网络安全-01-VMware安装Kali&部署DVWA
- 🔻一、Kali简介&下载
- 📗 二、VMware安装Kali
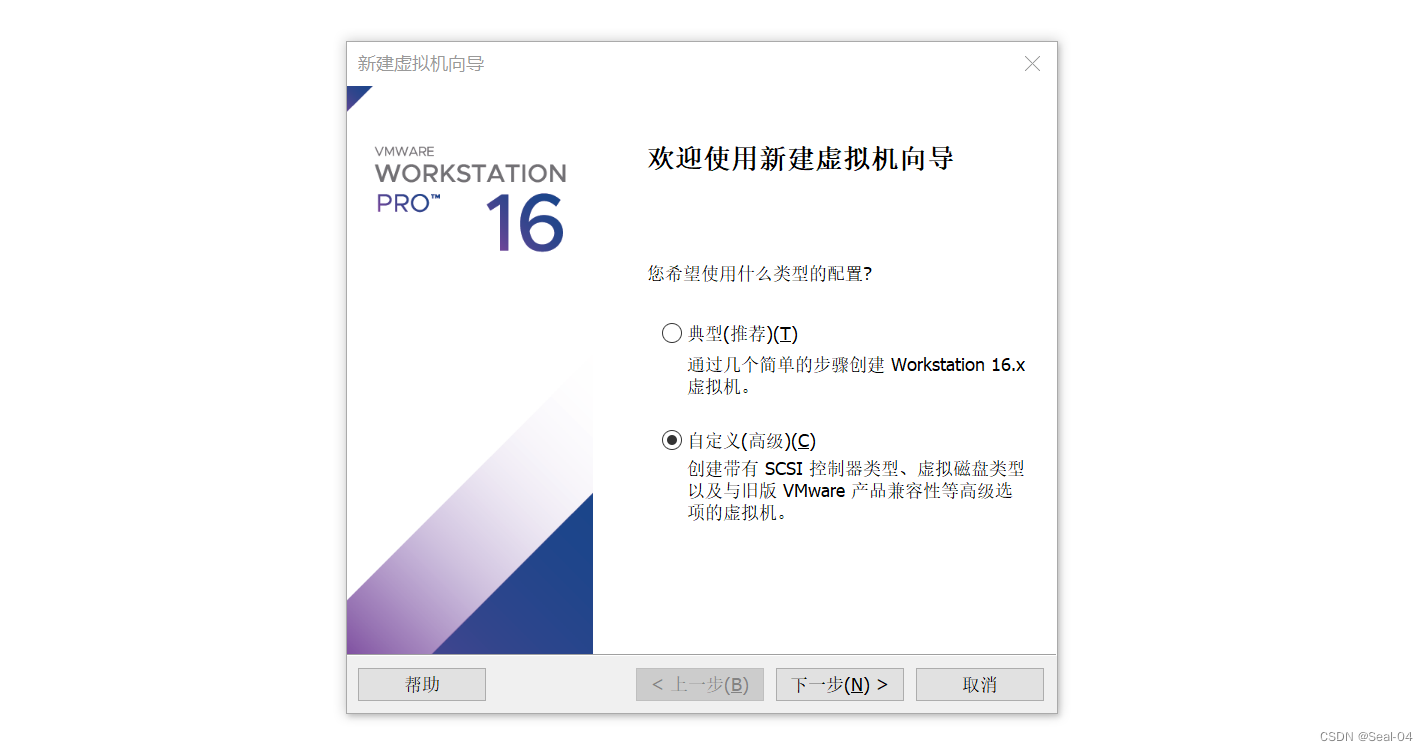
- 📰 2.1 新建虚拟机
- 📰 2.2 开始安装Kali
- 📰 2.3 更换apt源为国内源
- 📰 2.4 启动mysql-这里使用自带的maridb
- 📰 2.5 安装web服务器-apache2 & 启动
- 📰 2.6 LAMP安装DVWA漏洞靶场
- 📜 2.6.1 DVWA上传解压
- 📜 2.6.2 重命名config.inc.php.dist为config.inc.php
- 📜 2.6.3 根据红色报错做相应配置
- 📜 2.6.4 重启apache2 和mysql
- 📜 2.6.5 创建数据库
🔻一、Kali简介&下载
Kali linux是基于Debian的Linux的发行版,高级渗透测试及安全审核的工具。
kali linux:
1、包含600+渗透测试工具
2、完全免费
3、多语言
Kali linux镜像下载地址:
http://old.kali.org/kali-images/
📗 二、VMware安装Kali
📰 2.1 新建虚拟机
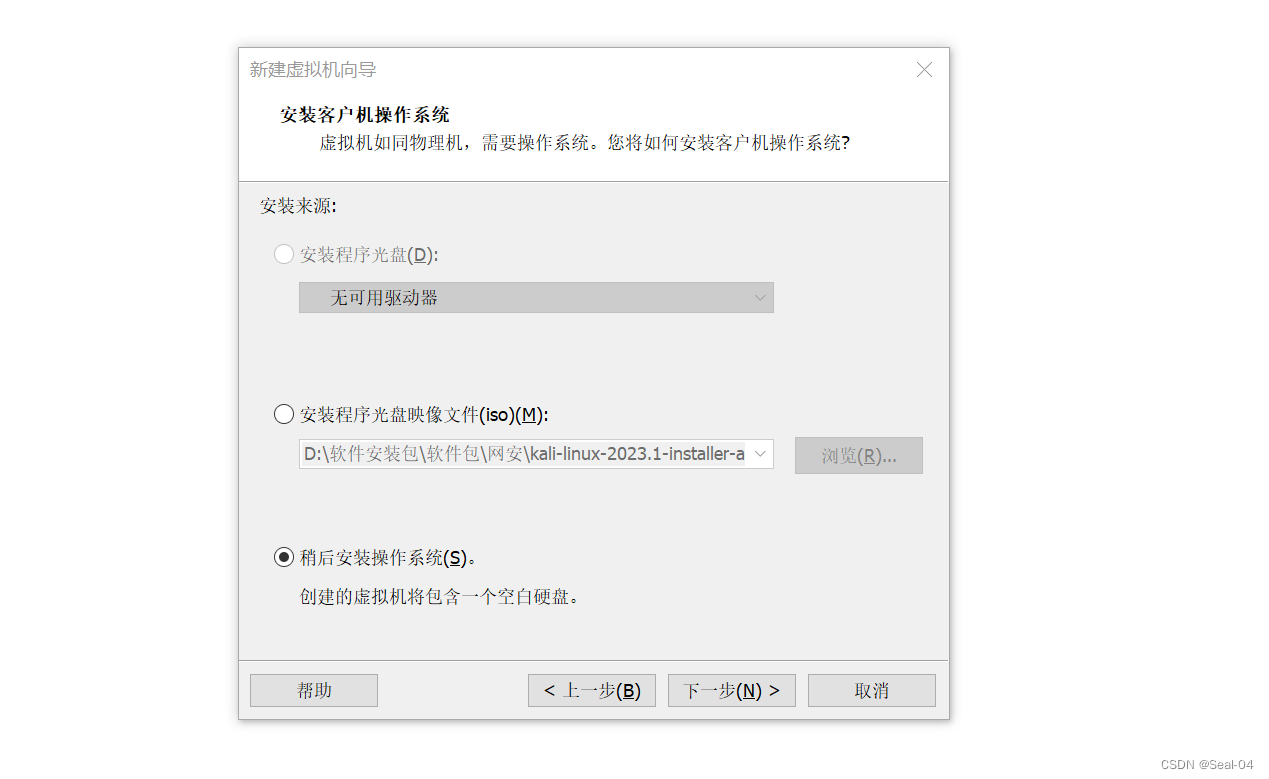
选择稍后安装操作系统,➡下一步
选择Linux, Debian 10.X 64位,➡下一步
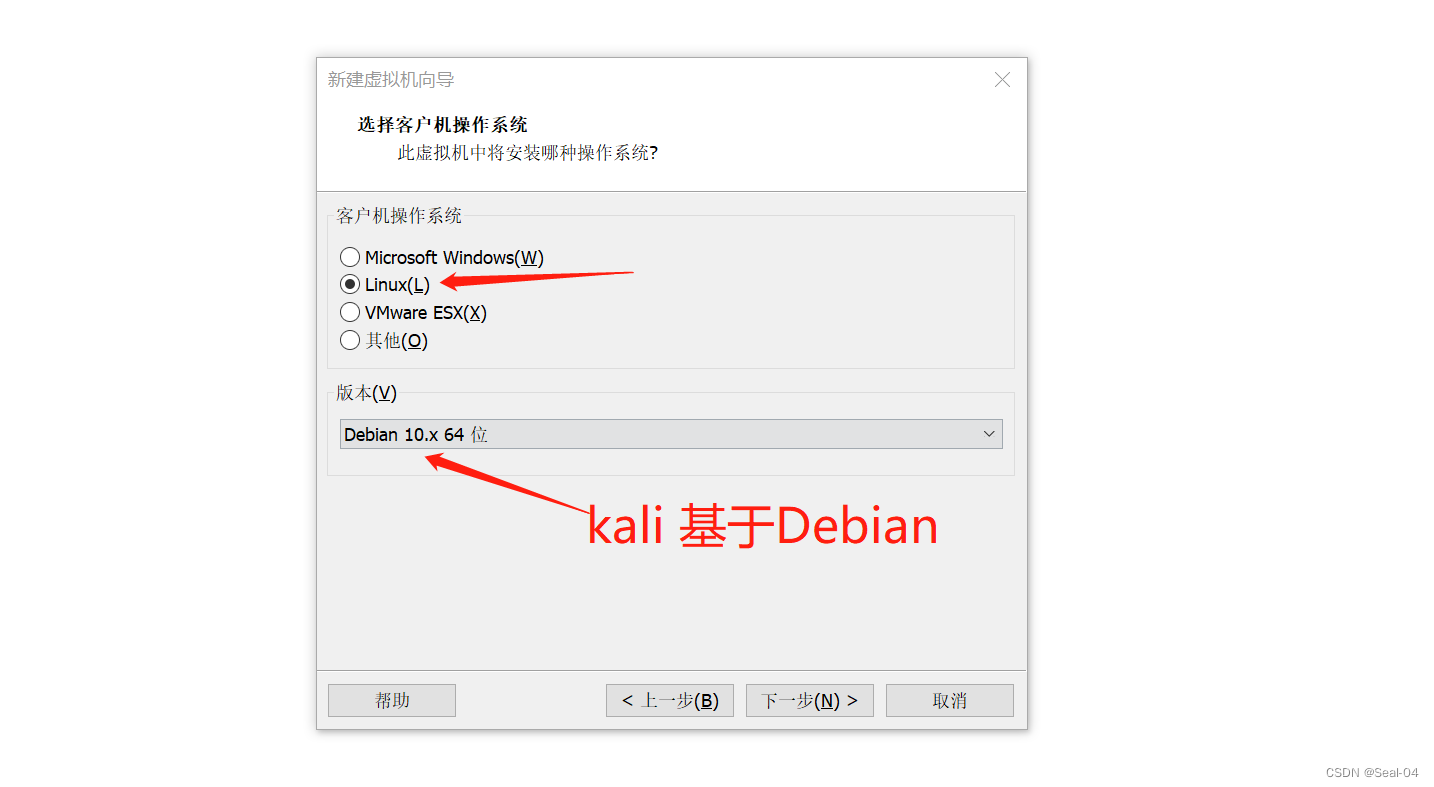
重命名虚拟机名称为Kali,➡下一步
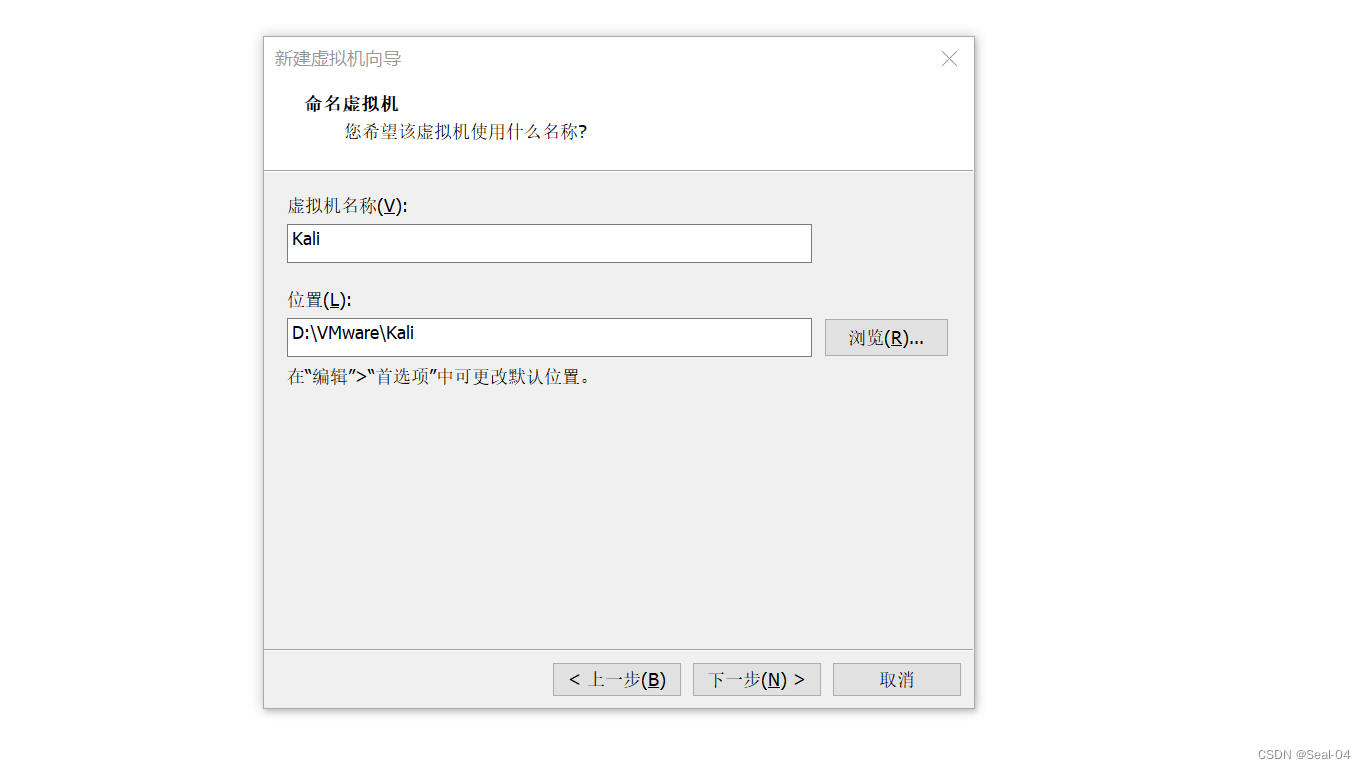
处理器配置,根据个人需求,➡下一步
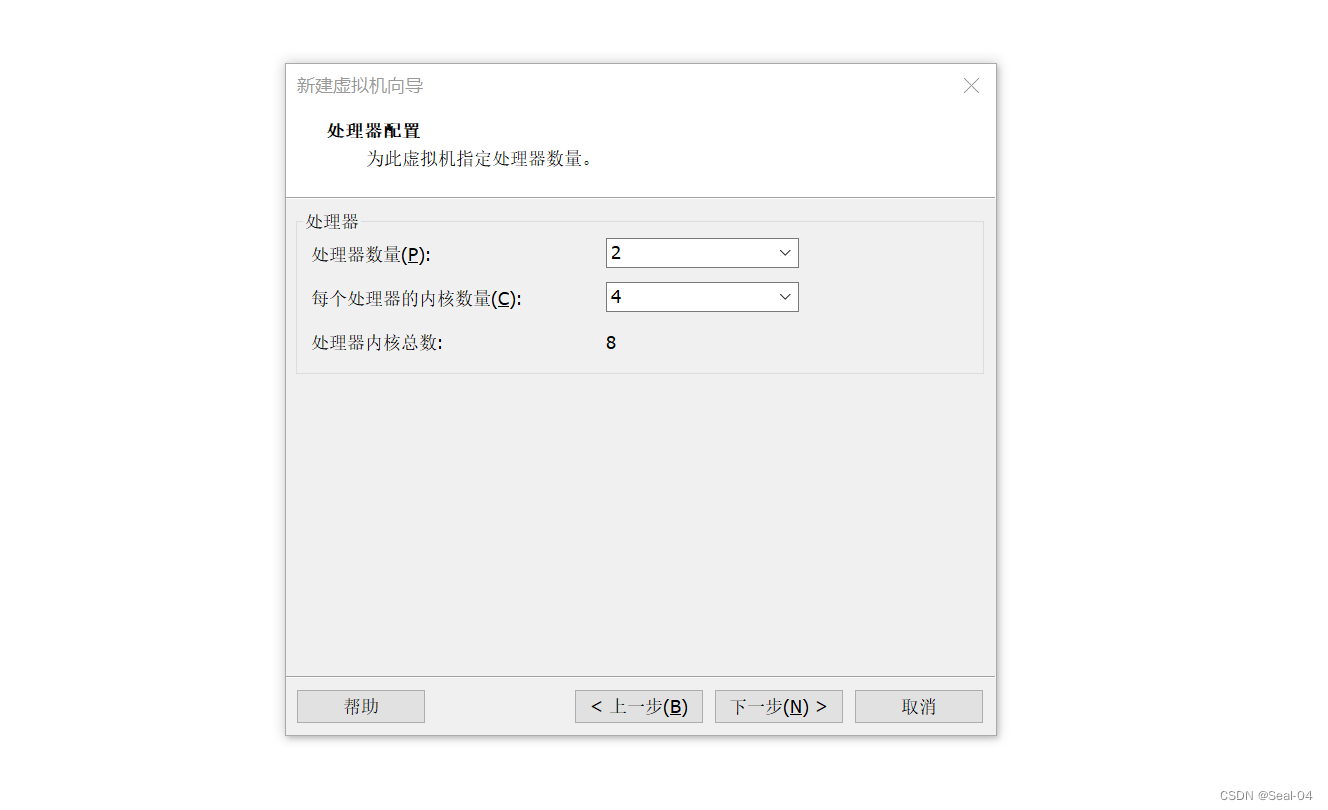
➡➡➡下一步,创建新磁盘
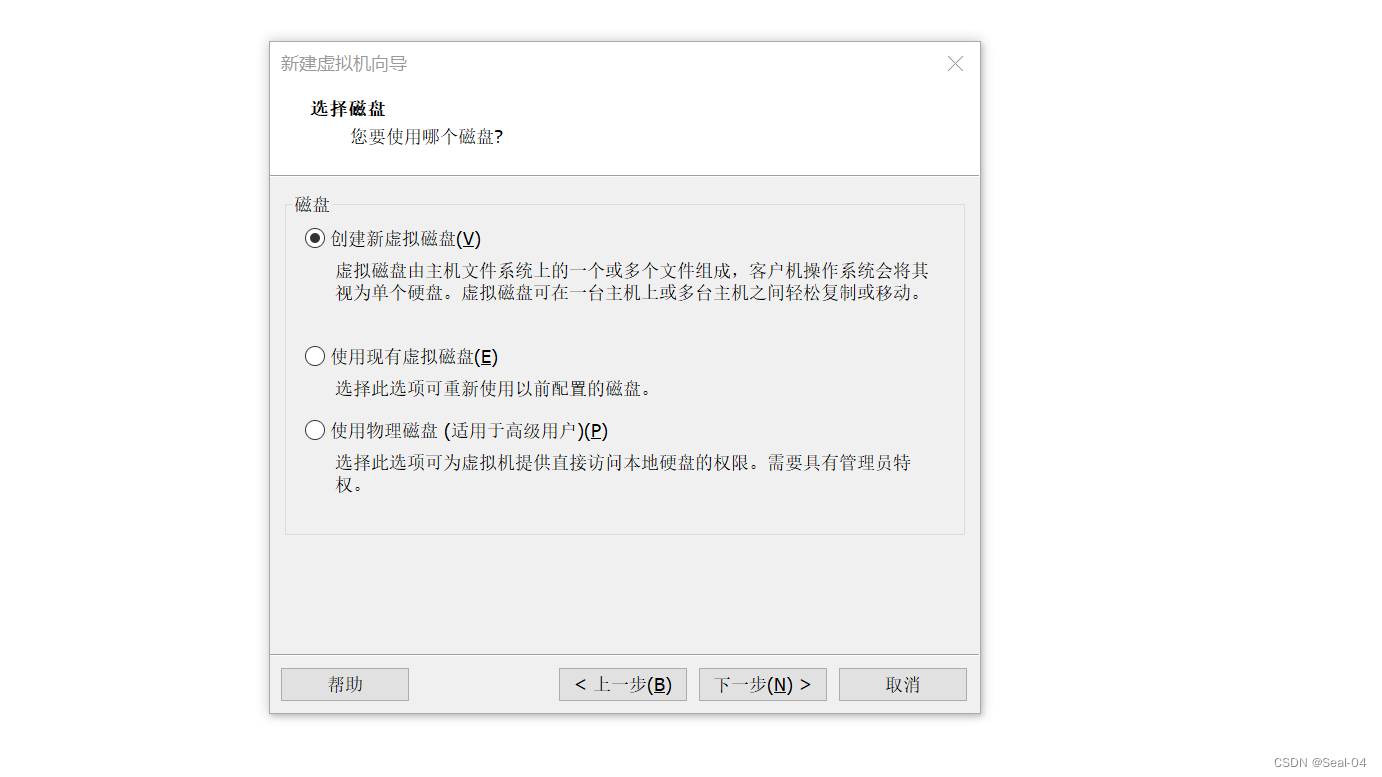
将虚拟磁盘存储为单个文件,➡下一步
➡➡下一步,完成创建
➡下一步,编辑虚拟机设置

➡下一步,选择Kali镜像文件
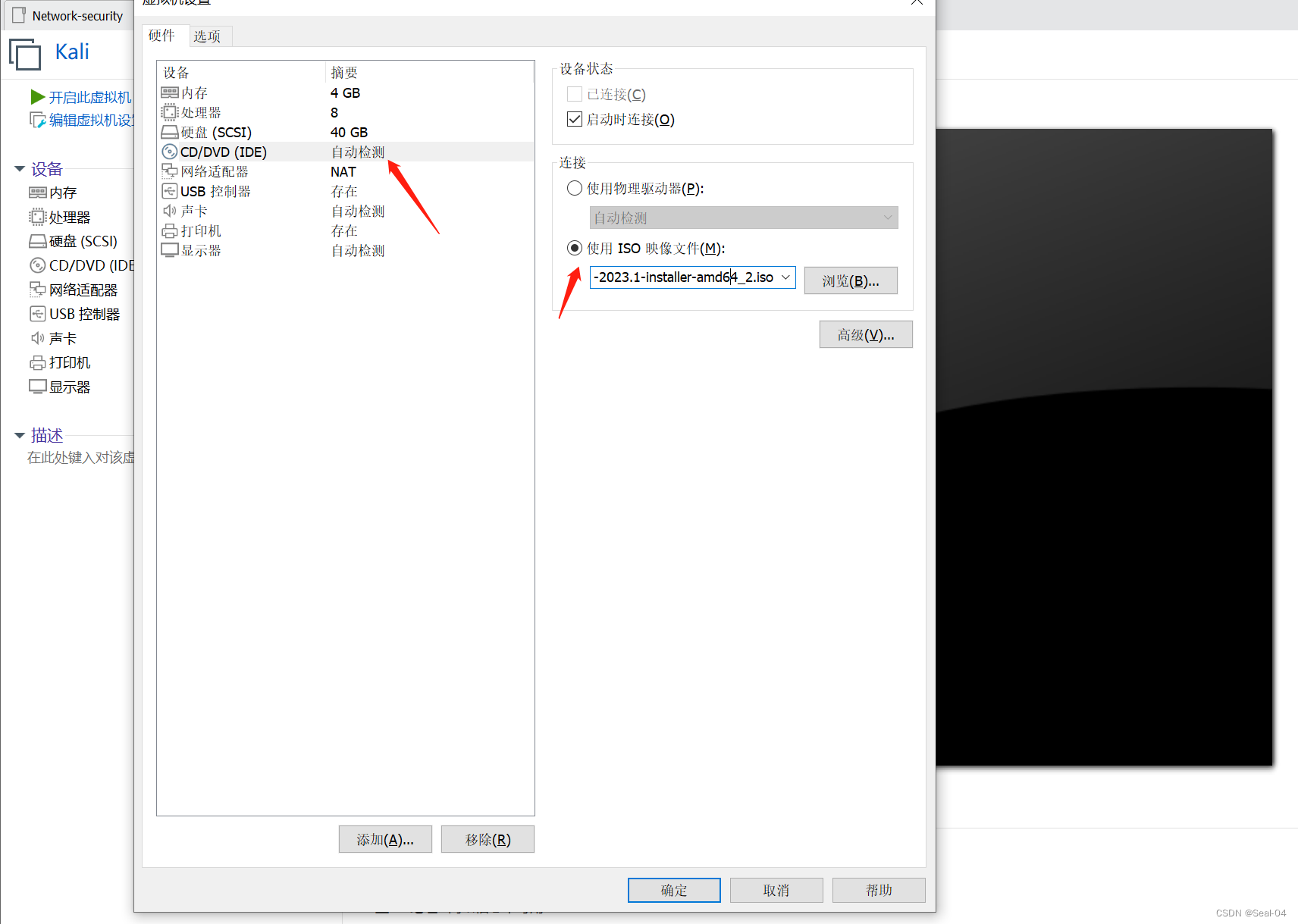
📰 2.2 开始安装Kali
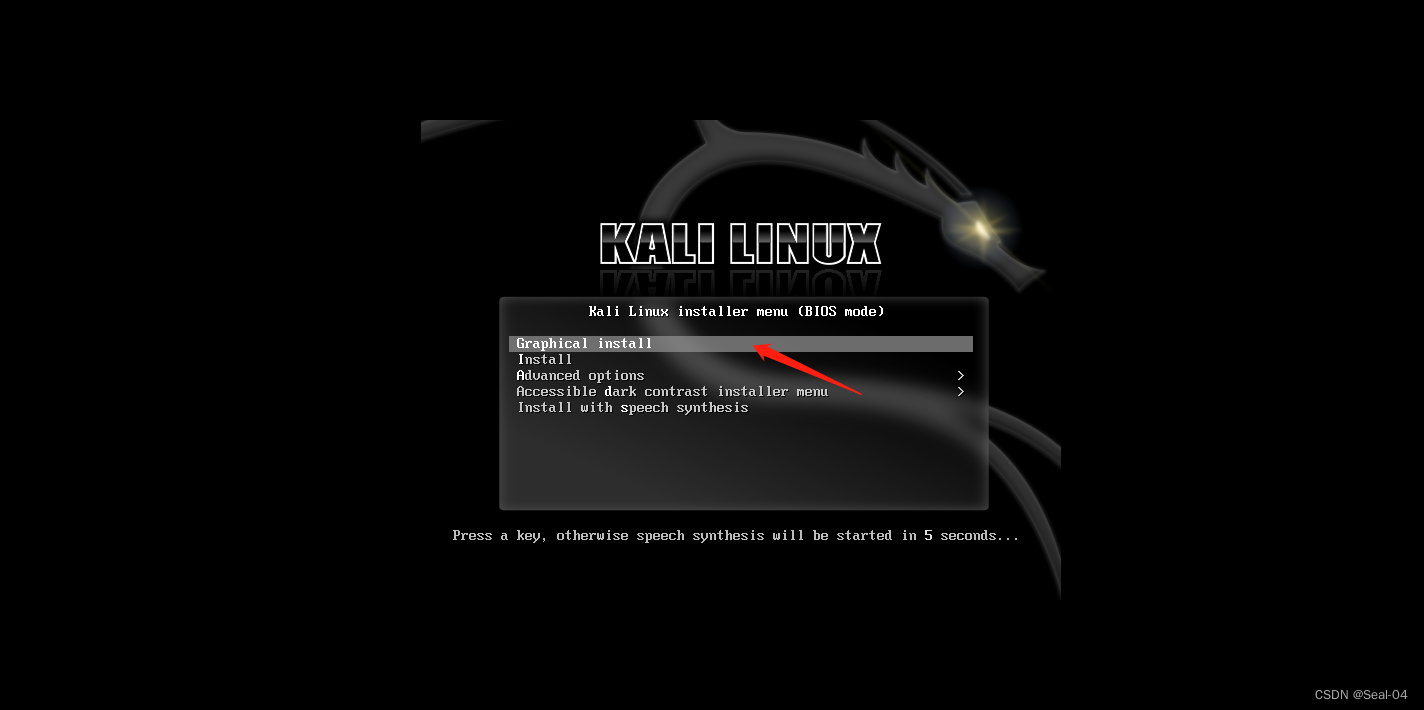
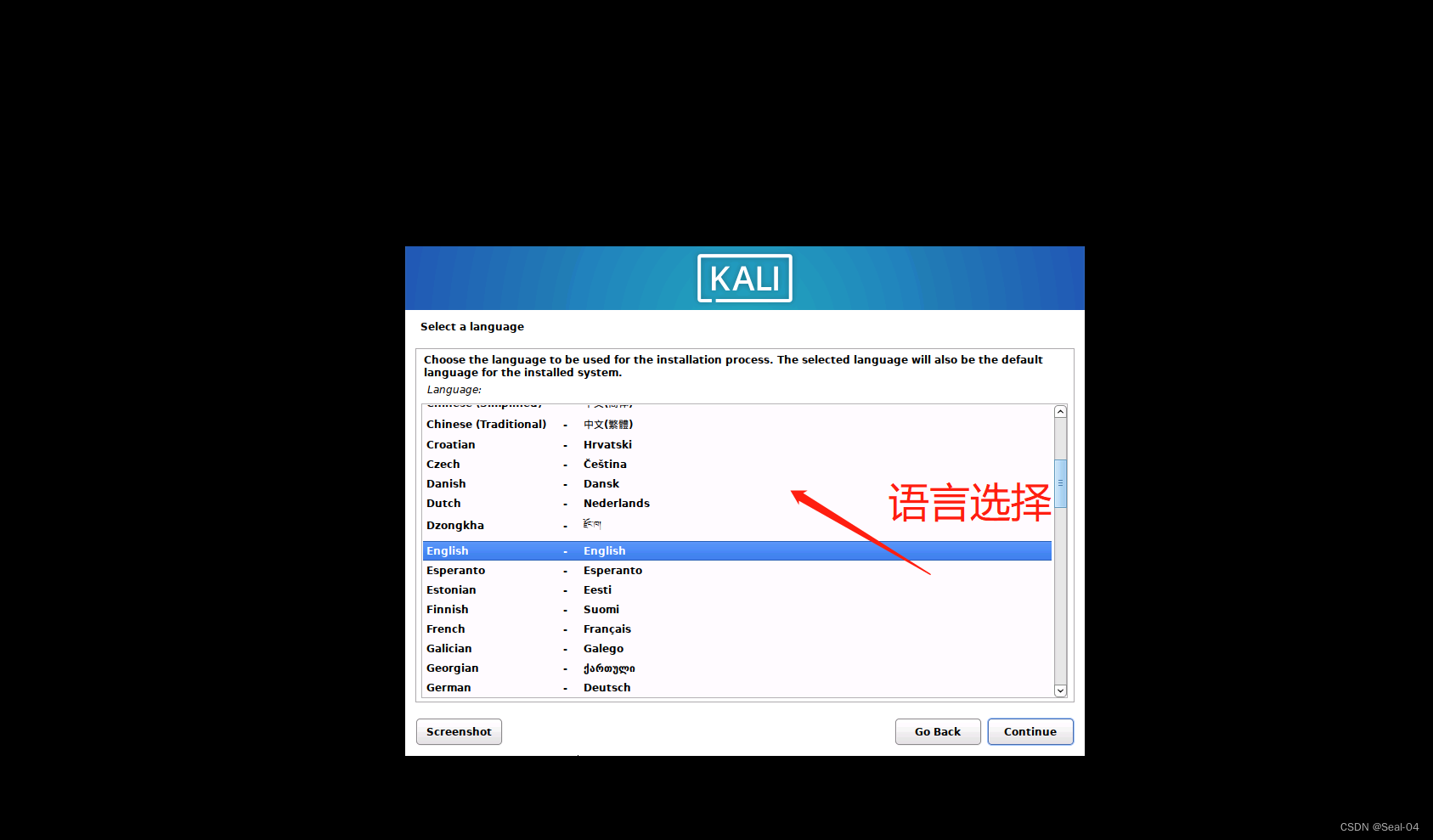
➡➡continue,至如下页面
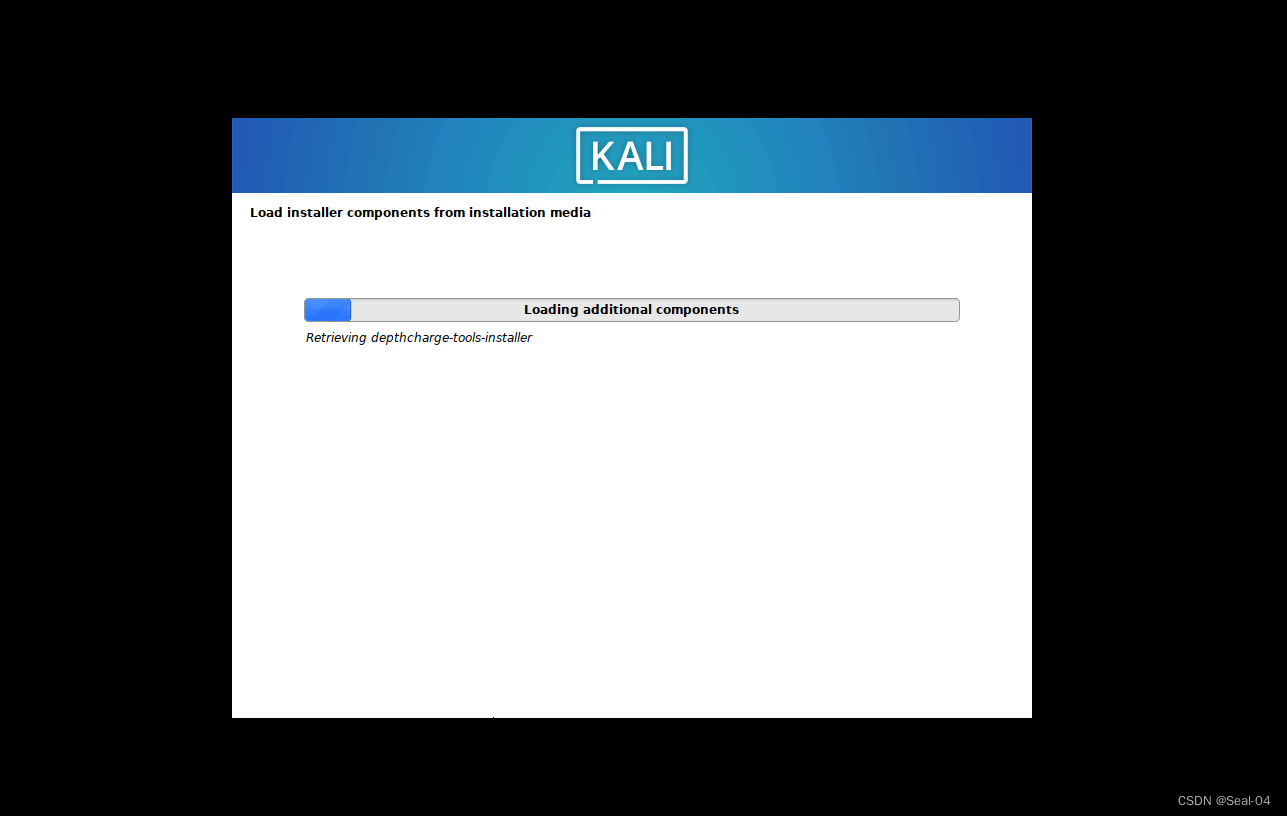
➡➡网络主机名
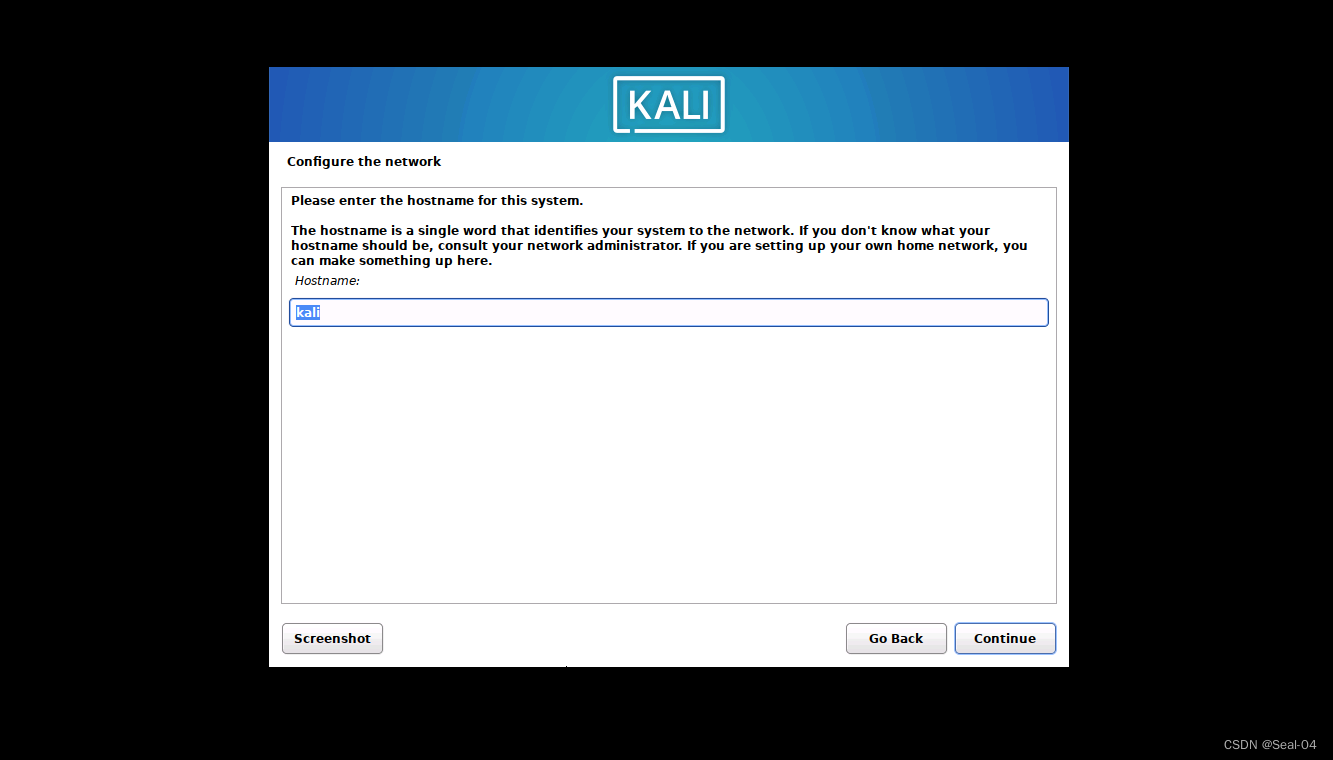
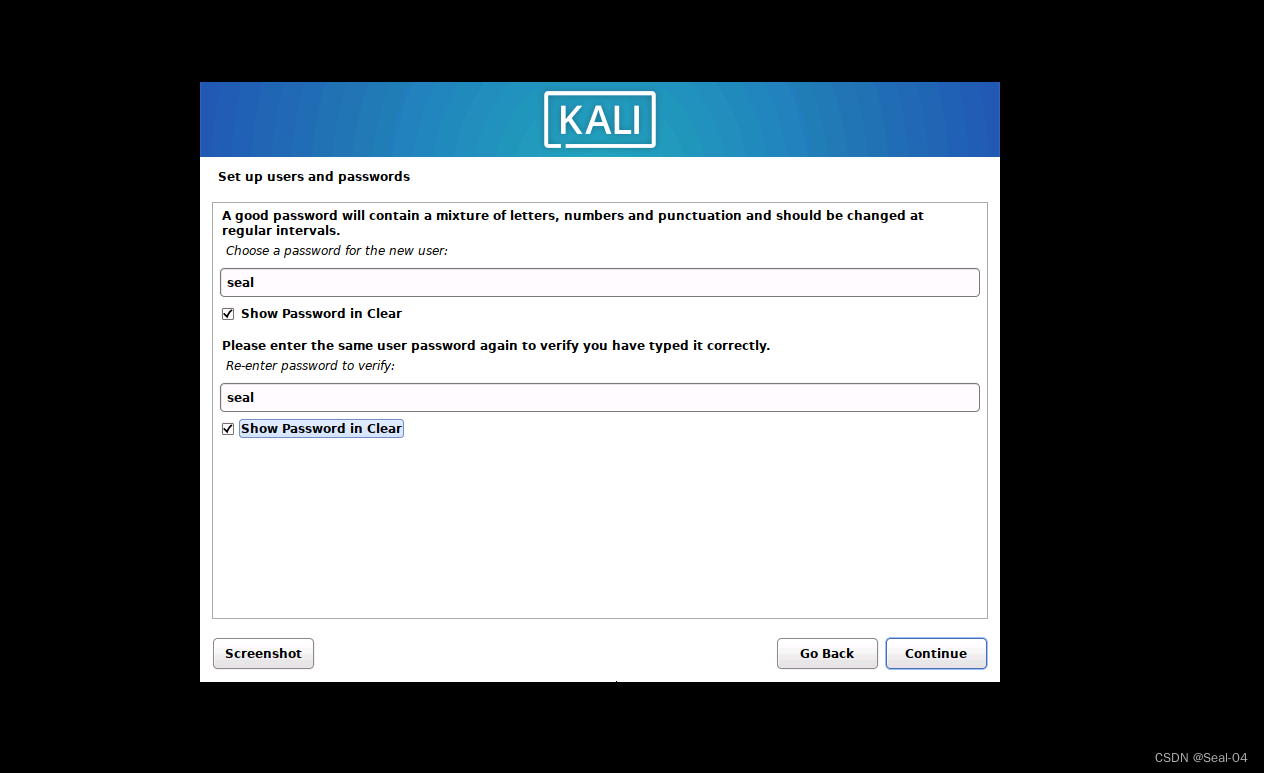
➡➡配置用户&密码
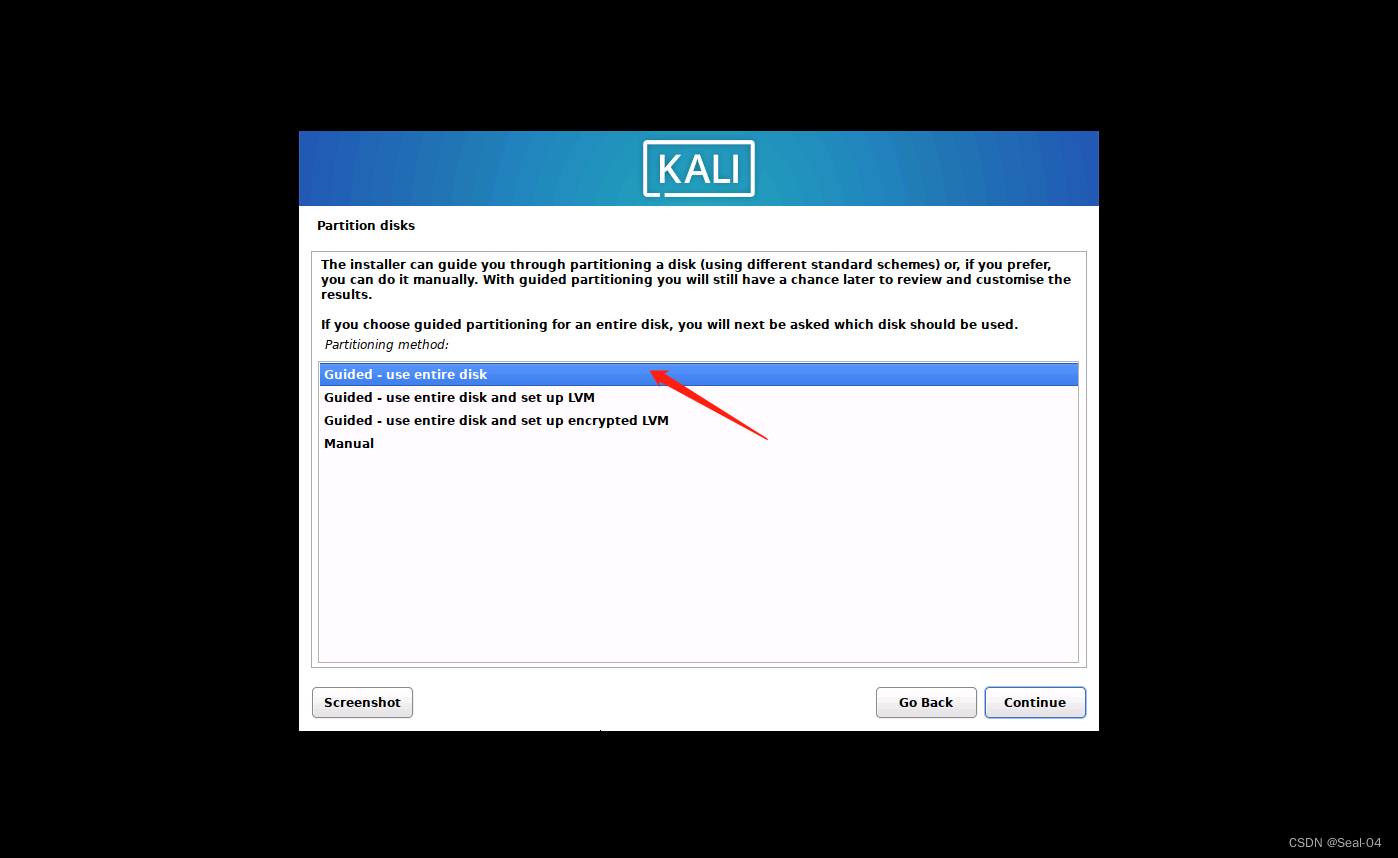
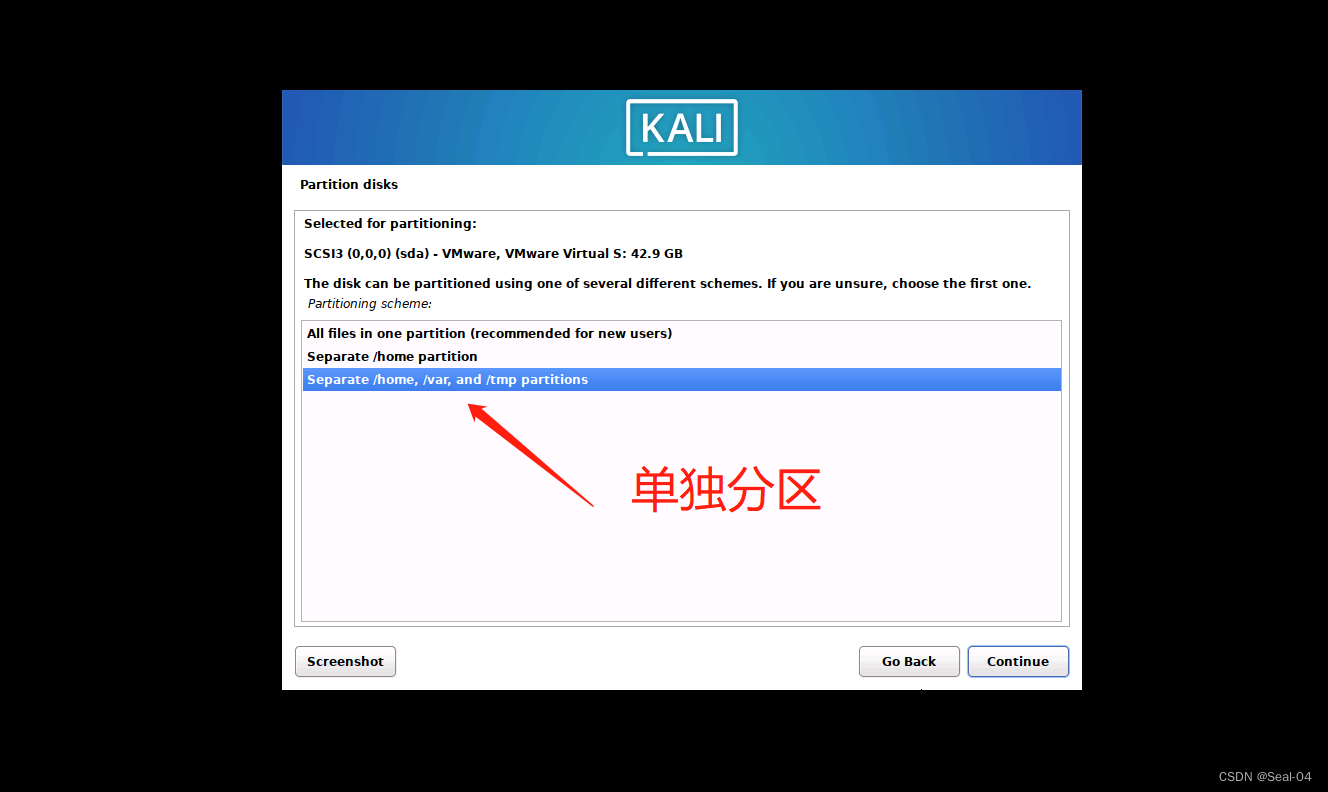
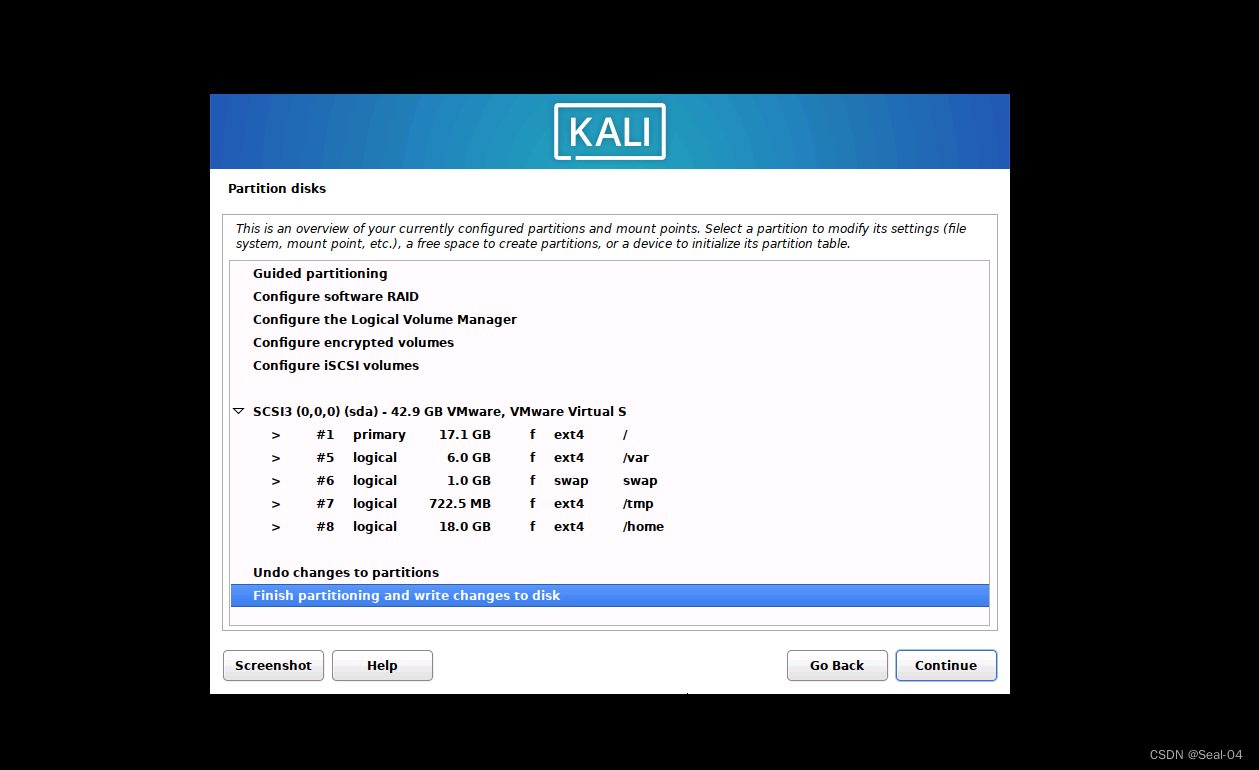
➡➡磁盘分区
➡➡软件选择
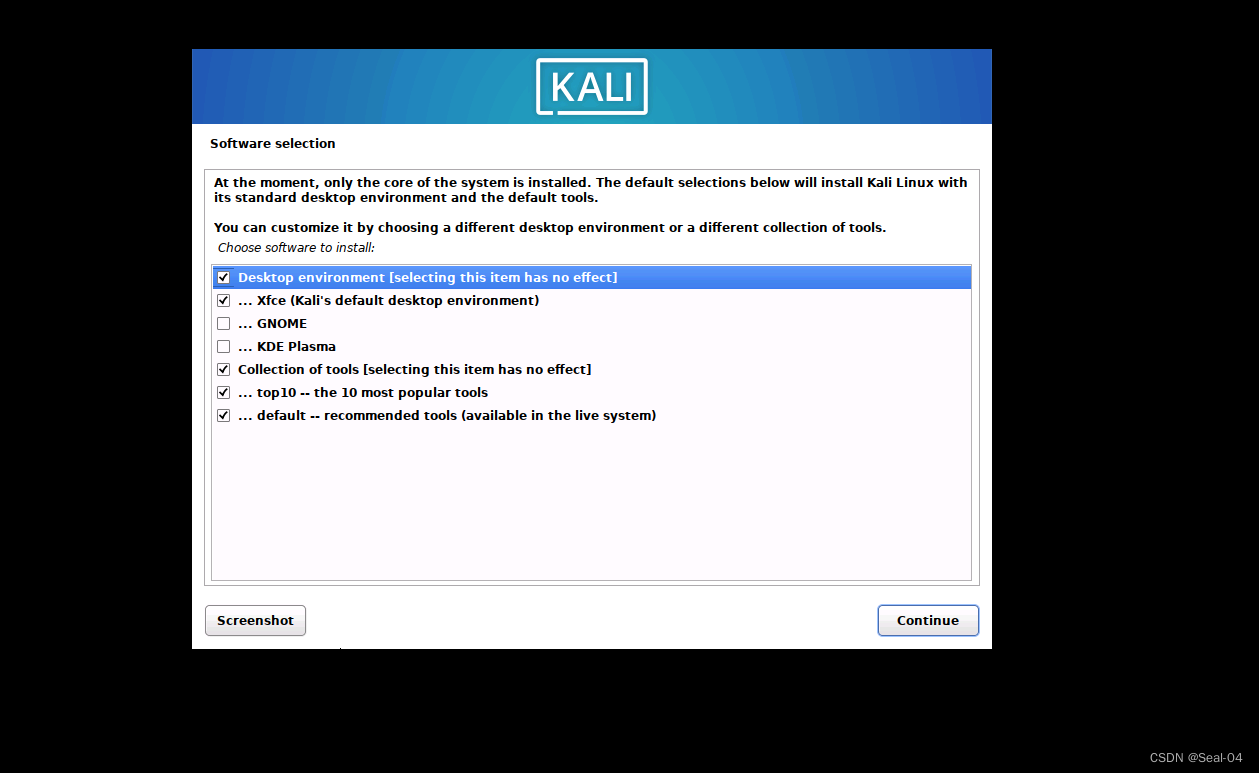
➡➡漫长的安装

📰 2.3 更换apt源为国内源
┌──(root㉿kali)-[/home/seal/Desktop]
└─# vi /etc/apt/sources.list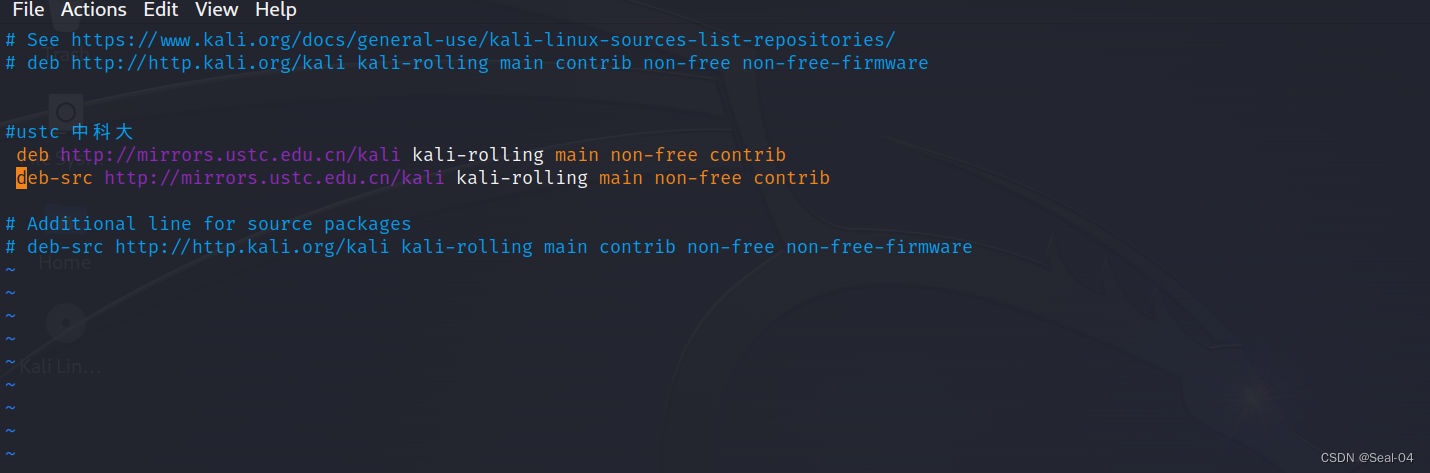
*********************源地址*****************************
#aliyun 阿里云deb http://mirrors.aliyun.com/kali kali-rolling main non-free contribdeb-src http://mirrors.aliyun.com/kali kali-rolling main non-free contrib#ustc 中科大deb http://mirrors.ustc.edu.cn/kali kali-rolling main non-free contribdeb-src http://mirrors.ustc.edu.cn/kali kali-rolling main non-free contrib#deb http://mirrors.ustc.edu.cn/kali-security kali-current/updates main contrib non-free#deb-src http://mirrors.ustc.edu.cn/kali-security kali-current/updates main contrib non-free#kali 官方源deb http://http.kali.org/kali kali-rolling main non-free contribdeb-src http://http.kali.org/kali kali-rolling main non-free contrib#deb http://security.kali.org/kali-security kali-rolling/updates main contrib non-free#deb-src http://security.kali.org/kali-security kali-rolling/updates main contrib non-free
更新软件列表
┌──(root㉿kali)-[/home/seal/Desktop]
└─# apt-get update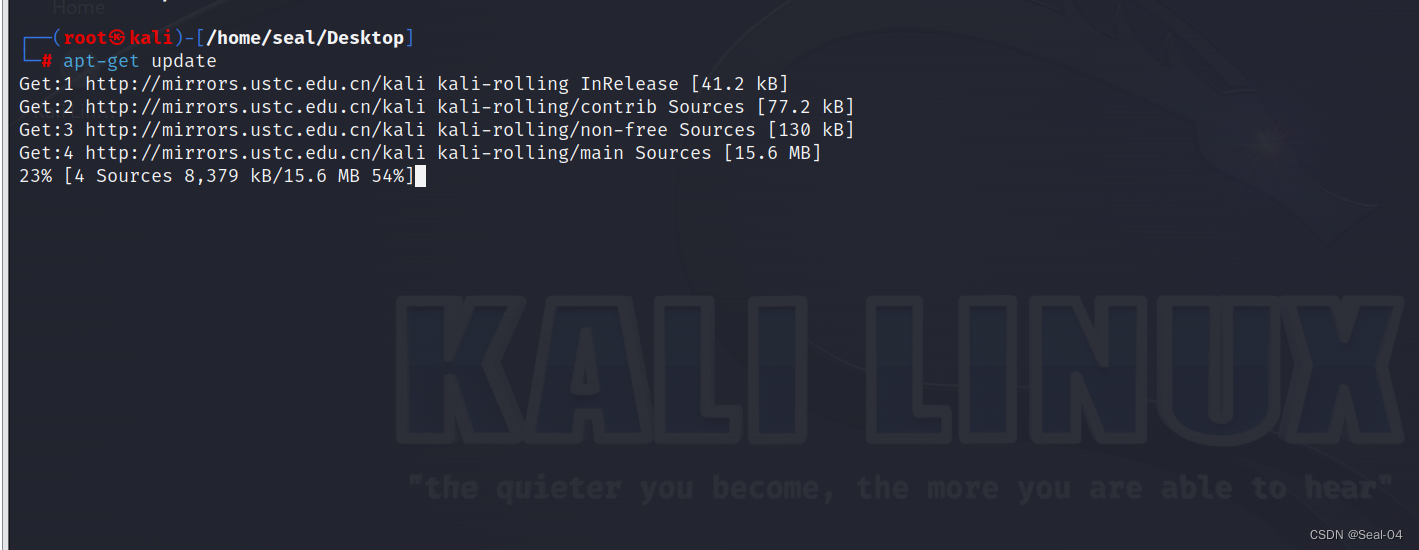
📰 2.4 启动mysql-这里使用自带的maridb
┌──(root㉿kali)-[/home/seal/Desktop]
└─# systemctl start mariadb┌──(root㉿kali)-[/home/seal/Desktop]
└─# systemctl status mariadb###开机自启####
┌──(root㉿kali)-[/home/seal/Desktop]
└─# systemctl enable mariadb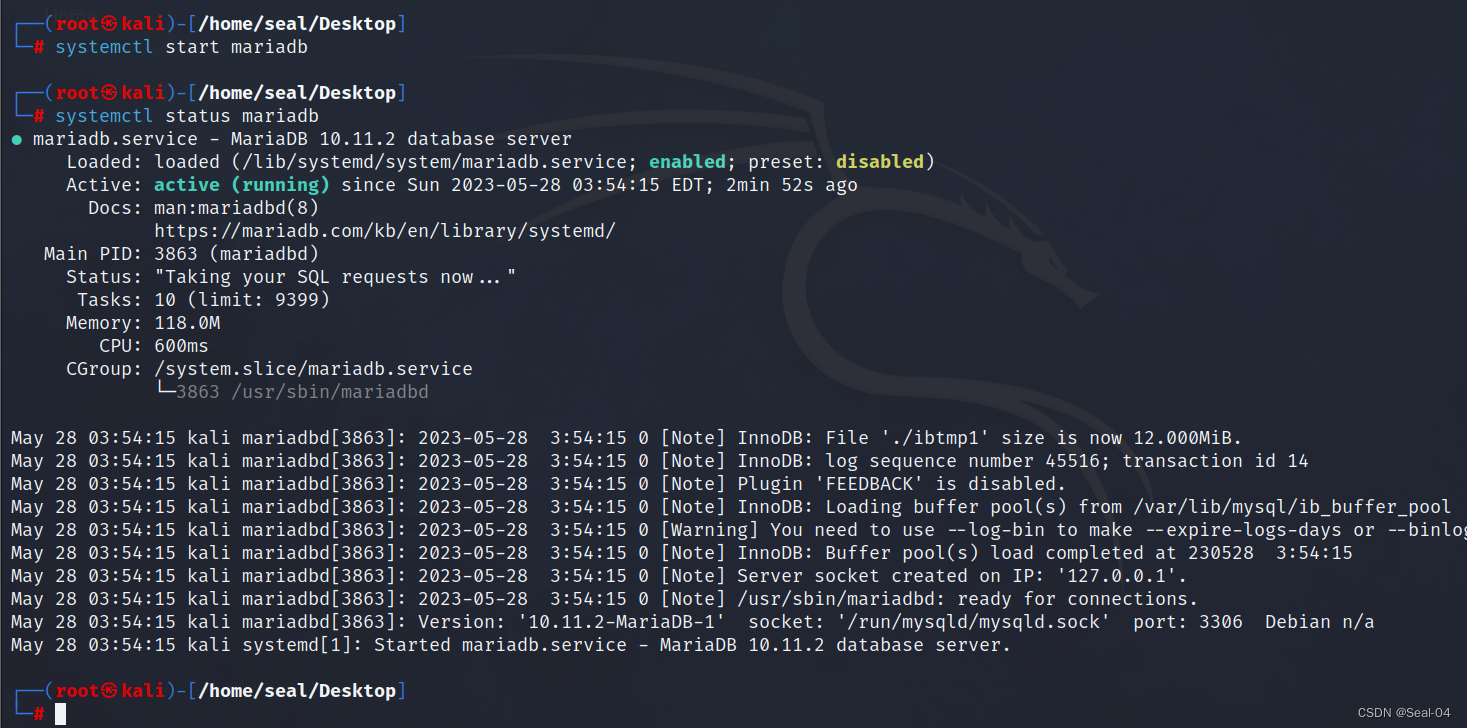
📰 2.5 安装web服务器-apache2 & 启动
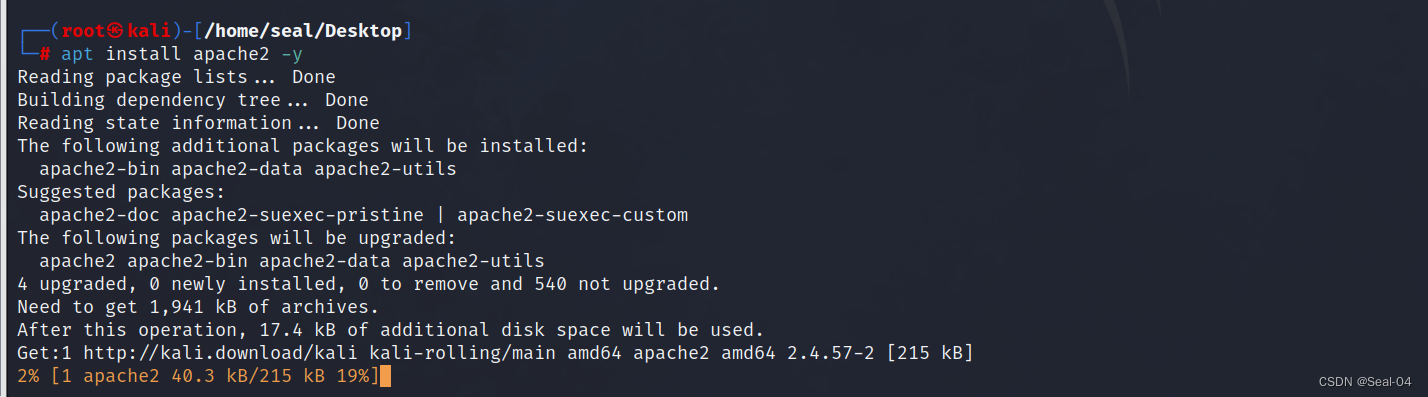
┌──(root㉿kali)-[/home/seal/Desktop]
└─# apt install apache2 -y
┌──(root㉿kali)-[/home/seal/Desktop]
└─# service apache2 status###开机自启####
┌──(root㉿kali)-[/home/seal/Desktop]
└─# systemctl enable apache2┌──(root㉿kali)-[/home/seal/Desktop]
└─# service apache2 restart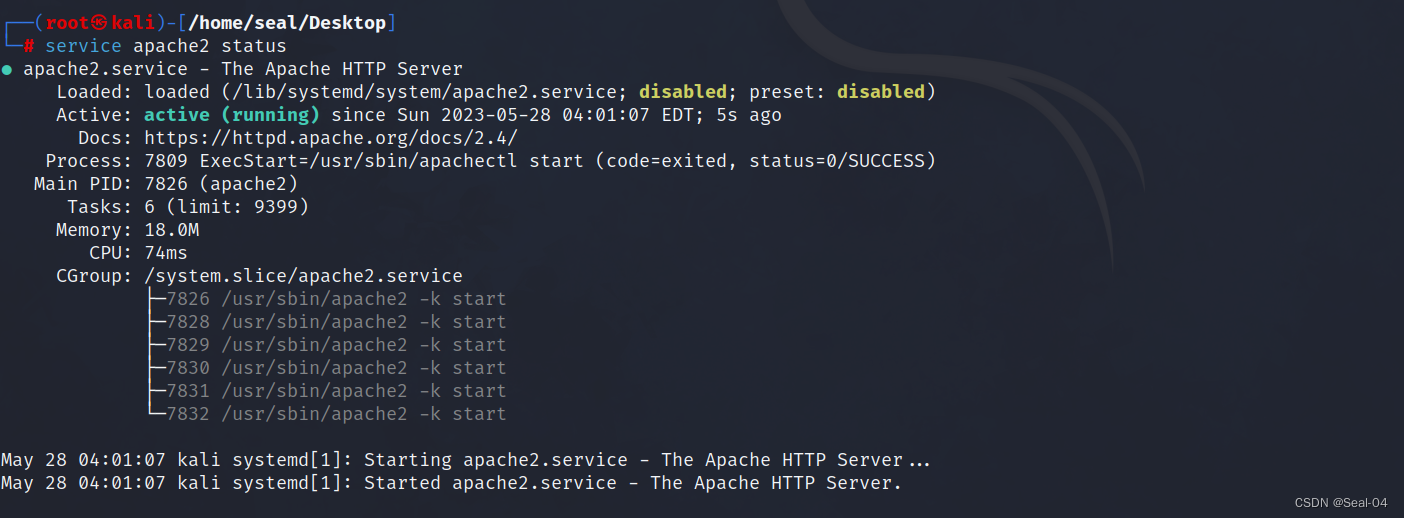
📰 2.6 LAMP安装DVWA漏洞靶场
DVWA(Damn Vulnerable Web App)是用PHP+MySQL编写的一个用于常规Web漏洞教学的测试网站,包含了SQL注入、命令执行、文件上传等常见的一些安全漏洞。
📜 2.6.1 DVWA上传解压
DVWA下载地址:
链接:https://pan.baidu.com/s/1QT2HXBCMKUxkDpO0sLnf2w
提取码:dvwa
┌──(root㉿kali)-[/home/seal/Desktop]
└─# unzip DVWA-master.zip 
移动DVWA-master 至 /var/www/html/dvwa
┌──(root㉿kali)-[/home/seal/Desktop]
└─# mv DVWA-master /var/www/html/dvwa┌──(root㉿kali)-[/home/seal/Desktop]
└─# cd /var/www/html/dvwa 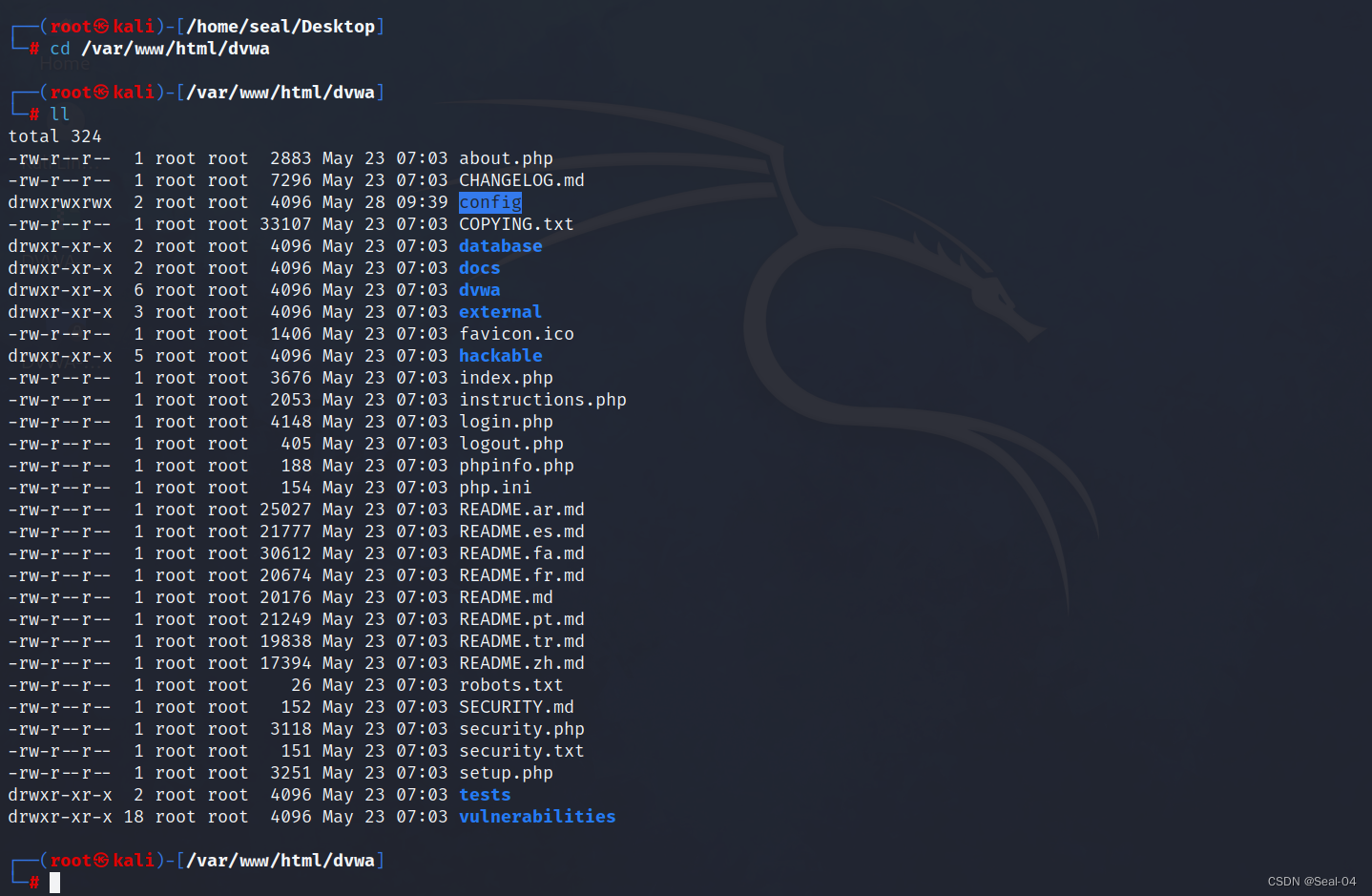
📜 2.6.2 重命名config.inc.php.dist为config.inc.php
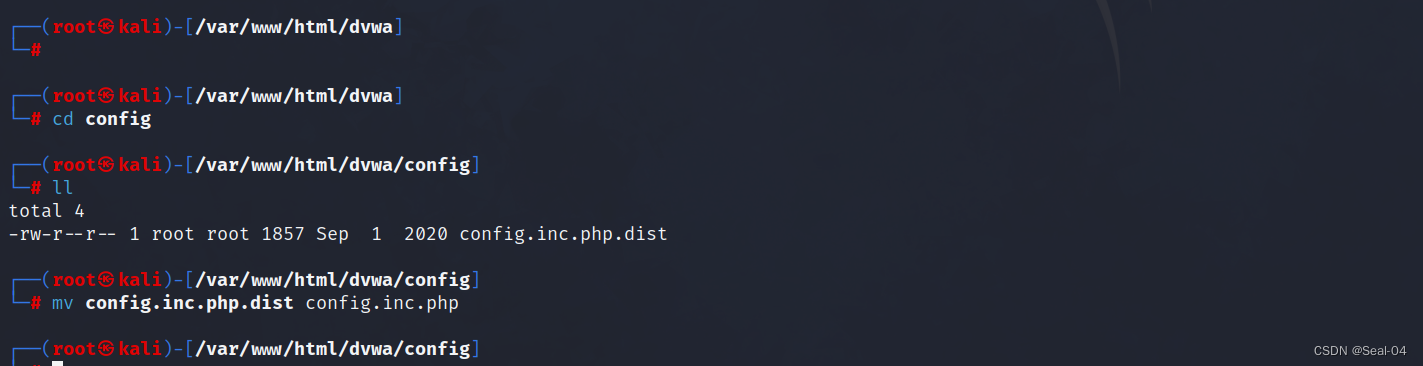
┌──(root㉿kali)-[/var/www/html/dvwa]
└─# cd config ┌──(root㉿kali)-[/var/www/html/dvwa/config]
└─# ll
total 4
-rw-r--r-- 1 root root 1857 Sep 1 2020 config.inc.php.dist┌──(root㉿kali)-[/var/www/html/dvwa/config]
└─# mv config.inc.php.dist config.inc.php ┌──(root㉿kali)-[/var/www/html/dvwa/config]
└─#
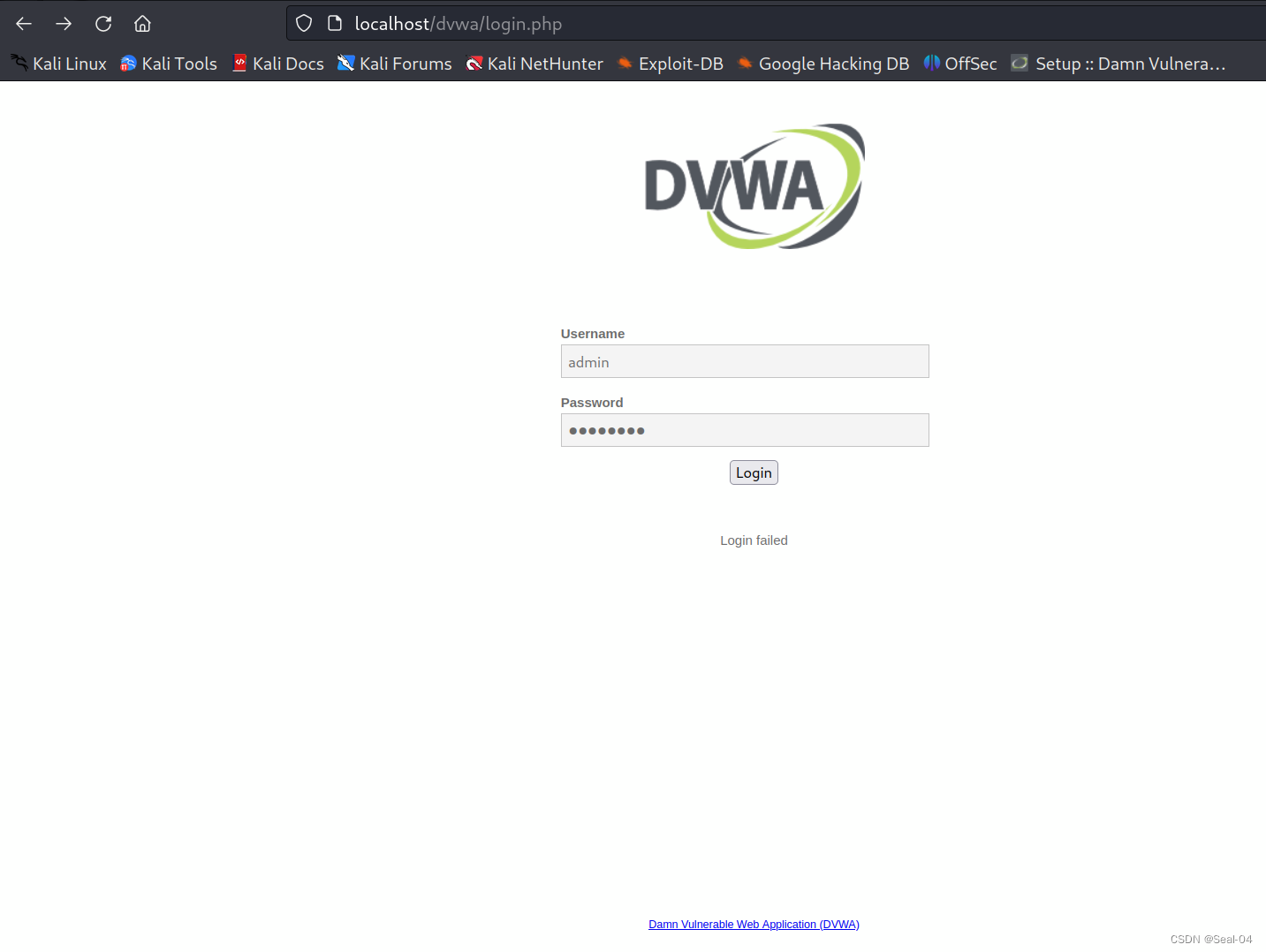
访问靶场:http://localhost/dvwa/setup.php
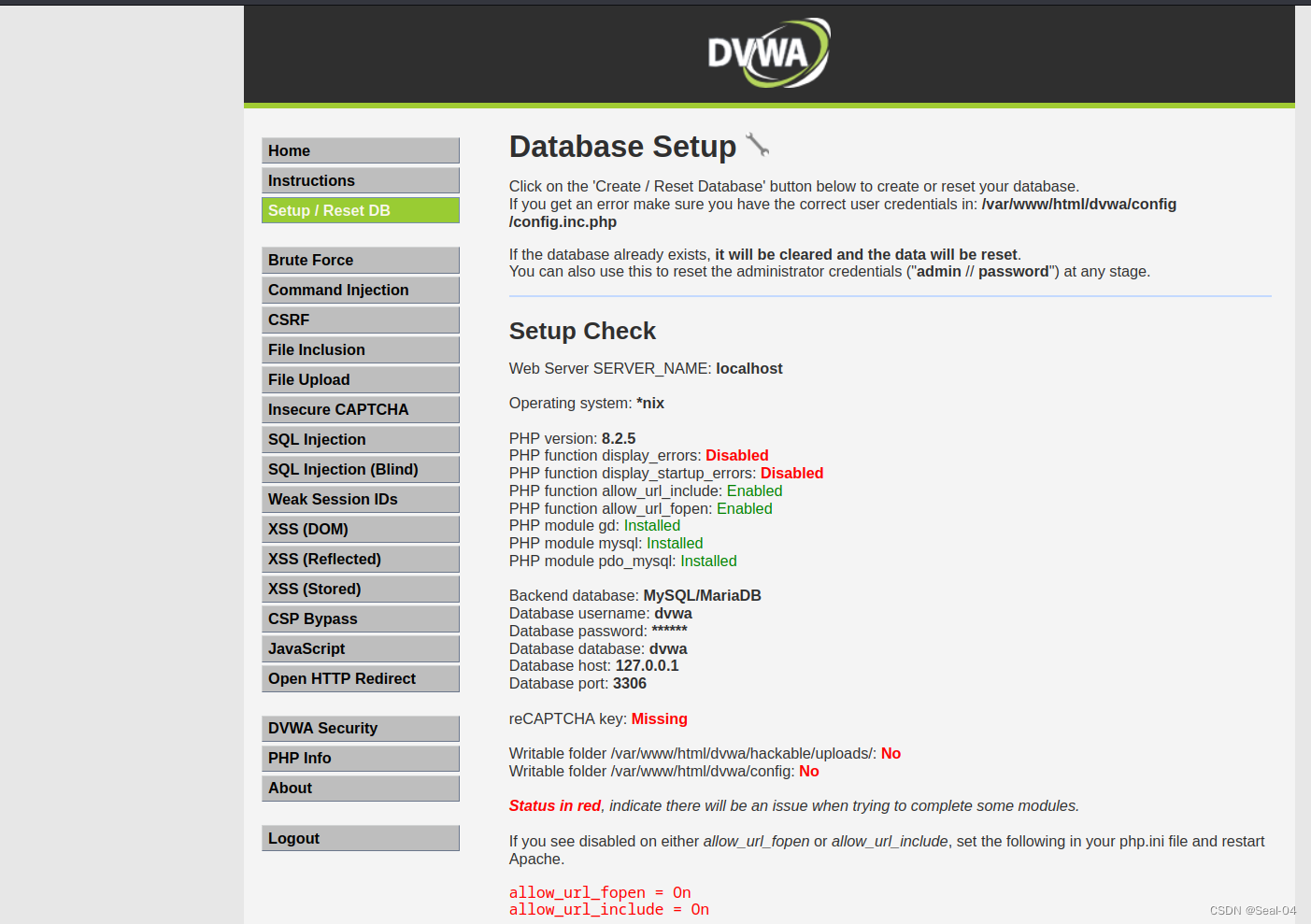
📜 2.6.3 根据红色报错做相应配置
PHP function display_errors: Disabled
PHP function display_startup_errors: Disabled
┌──(root㉿kali)-[/etc/php]
└─# vi /etc/php/8.2/apache2/php.ini
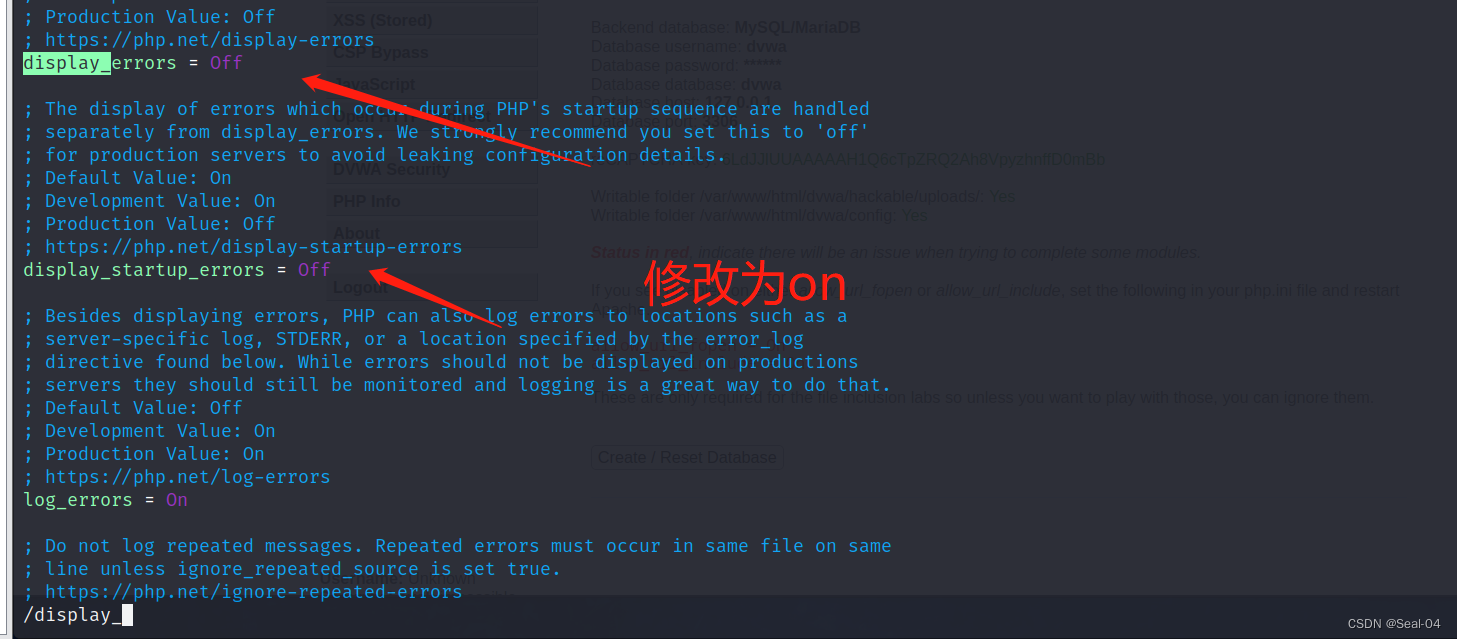
PHP module gd: Missing - Only an issue if you want to play with captchas
┌──(root㉿kali)-[/etc/php]
└─# apt install php-gd
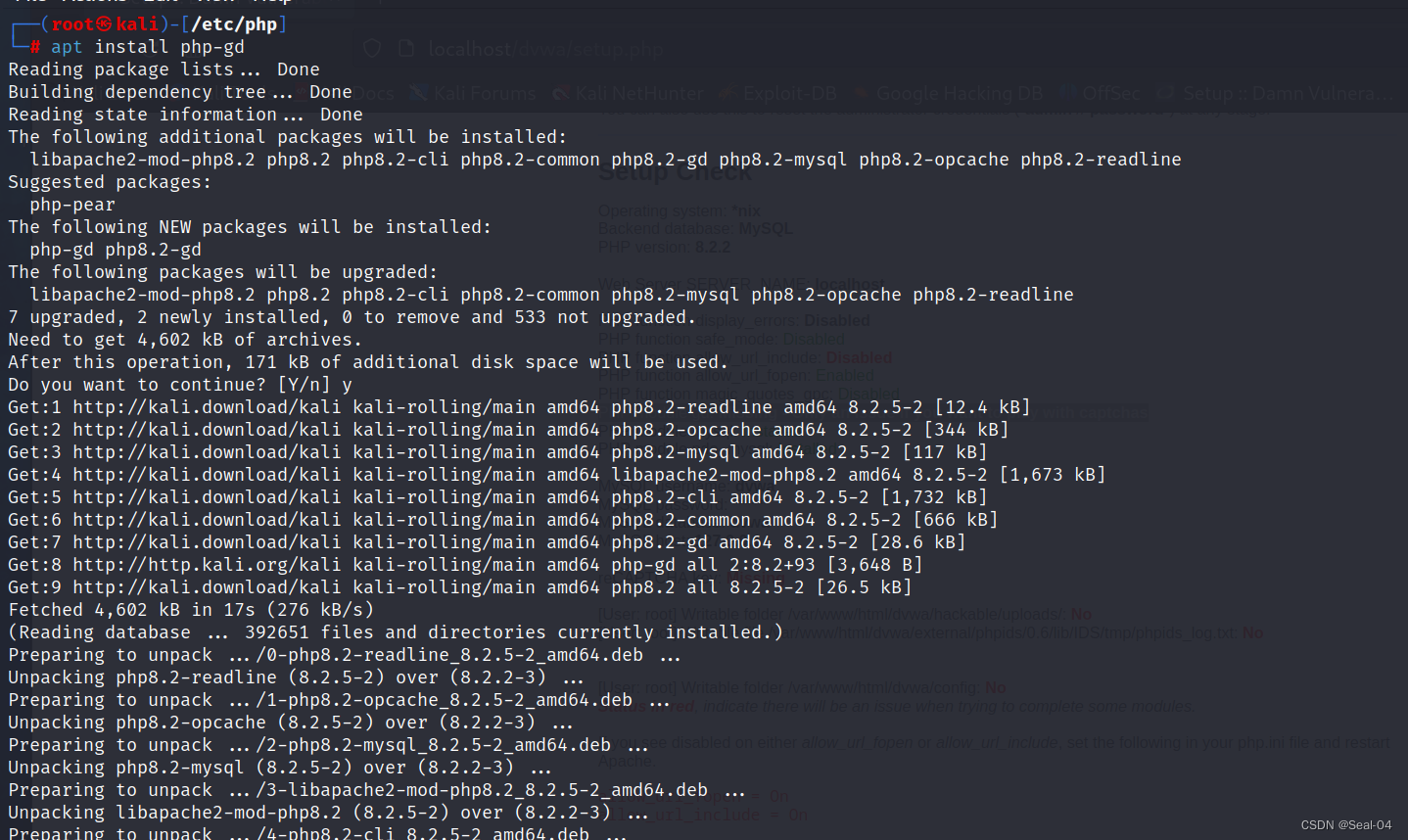
修改配置和安装 php-gd之后,重启apache2
t㉿kali)-[/etc/php]
└─# service apache2 restart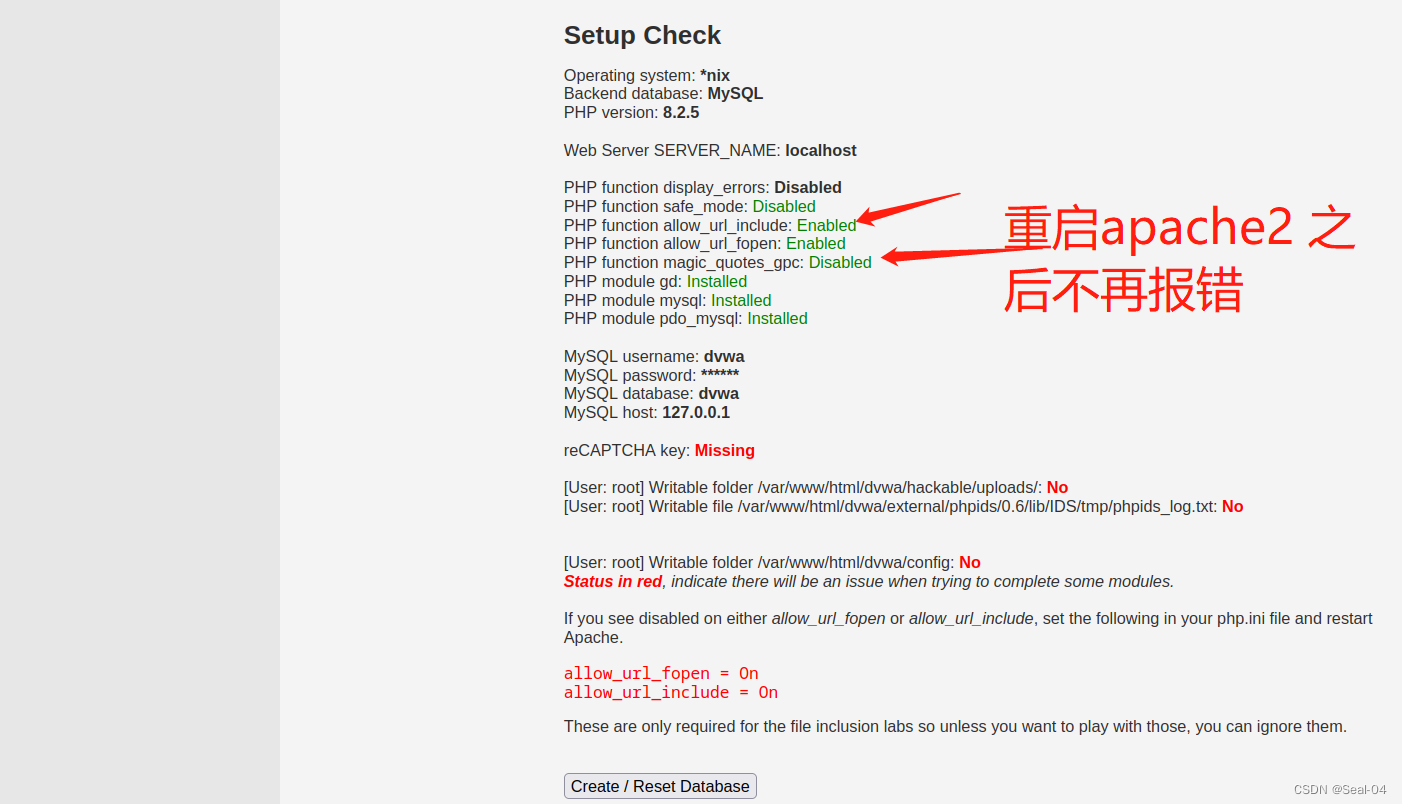
reCAPTCHA key: Missing
public:
6LdJJlUUAAAAAH1Q6cTpZRQ2Ah8VpyzhnffD0mBbprivate:
6LdJJlUUAAAAAM2a3HrgzLczqdYp4g05EqDs-W4K
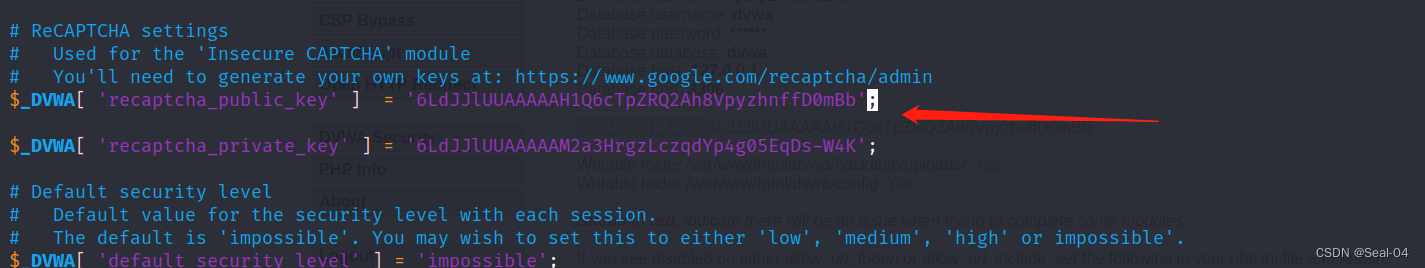
更改mysql配置信息,创建dvwa用户和密码,授权
MariaDB [(none)]> create user'dvwa'@'localhost'identified by 'dvwa';
Query OK, 0 rows affected (0.014 sec)MariaDB [(none)]> grant all privileges on *.* to 'dvwa'@'%' identified by 'dvwa';
Query OK, 0 rows affected (0.001 sec)MariaDB [(none)]> flush privileges;
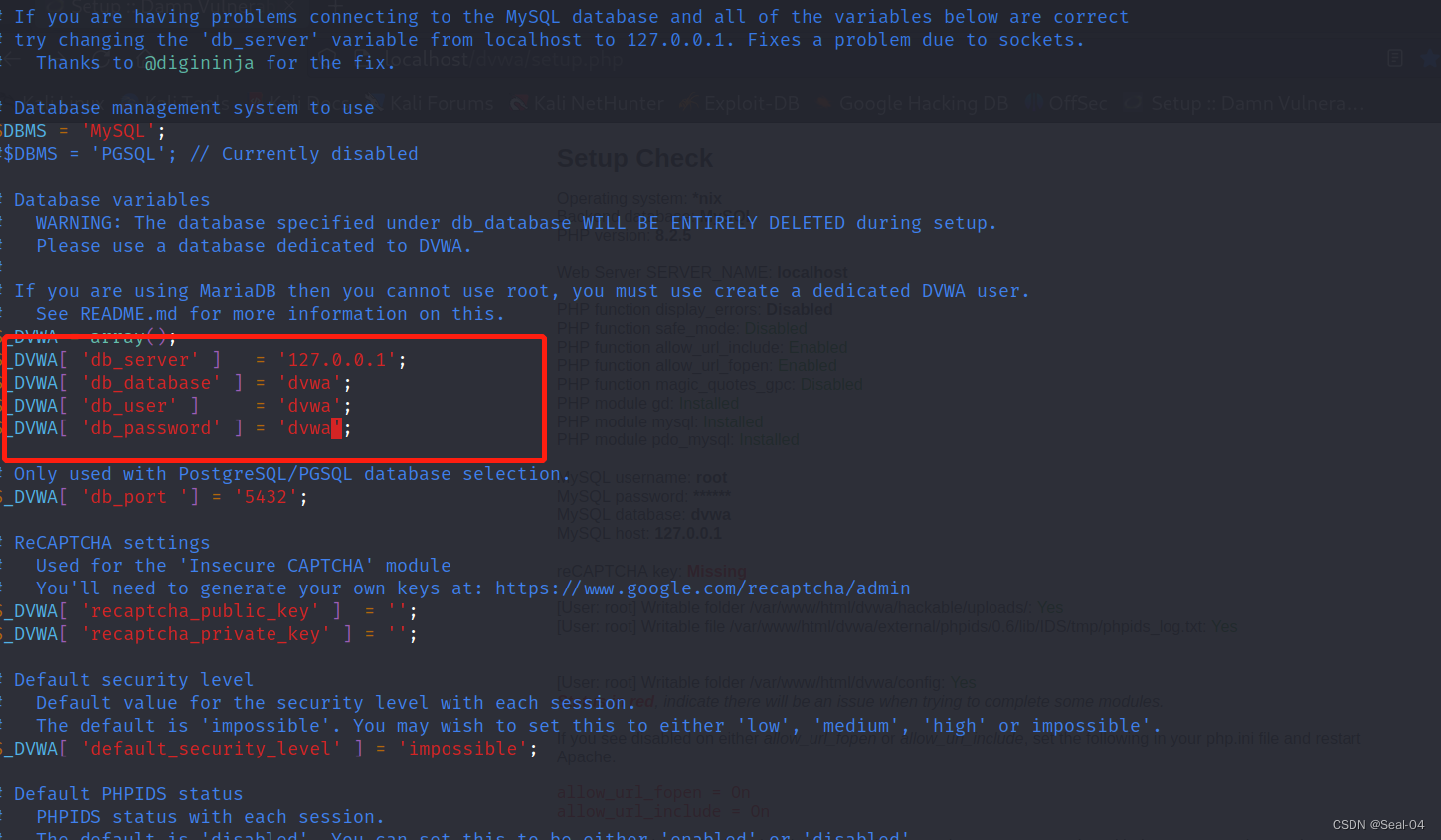
Query OK, 0 rows affected (0.001 sec)MariaDB [(none)]> 编辑config.inc.php 配置
┌──(root㉿kali)-[/var/www/html/dvwa/config]
└─# vi /var/www/html/dvwa/config/config.inc.php
uploads 文件夹 & config 文件夹赋权——chmod 777
[User: root] Writable folder /var/www/html/dvwa/hackable/uploads/: No
┌──(root㉿kali)-[/var/www/html/dvwa]
└─# cd hackable ┌──(root㉿kali)-[/var/www/html/dvwa/hackable]
└─# ll
total 12
drwxr-xr-x 2 root root 4096 Sep 1 2020 flags
drwxr-xr-x 2 root root 4096 Sep 1 2020 uploads
drwxr-xr-x 2 root root 4096 Sep 1 2020 users┌──(root㉿kali)-[/var/www/html/dvwa/hackable]
└─# chmod 777 uploads ┌──(root㉿kali)-[/var/www/html/dvwa/hackable]
└─# [User: root] Writable folder /var/www/html/dvwa/config: No
┌──(root㉿kali)-[/var/www/html/dvwa]
└─# chmod 777 config ┌──(root㉿kali)-[/var/www/html/dvwa]
└─# 📜 2.6.4 重启apache2 和mysql
┌──(root㉿kali)-[/var/www/html/dvwa/config]
└─# service apache2 restart┌──(root㉿kali)-[/var/www/html/dvwa/config]
└─# systemctl restart mariadb┌──(root㉿kali)-[/var/www/html/dvwa/config]
└─# 📜 2.6.5 创建数据库
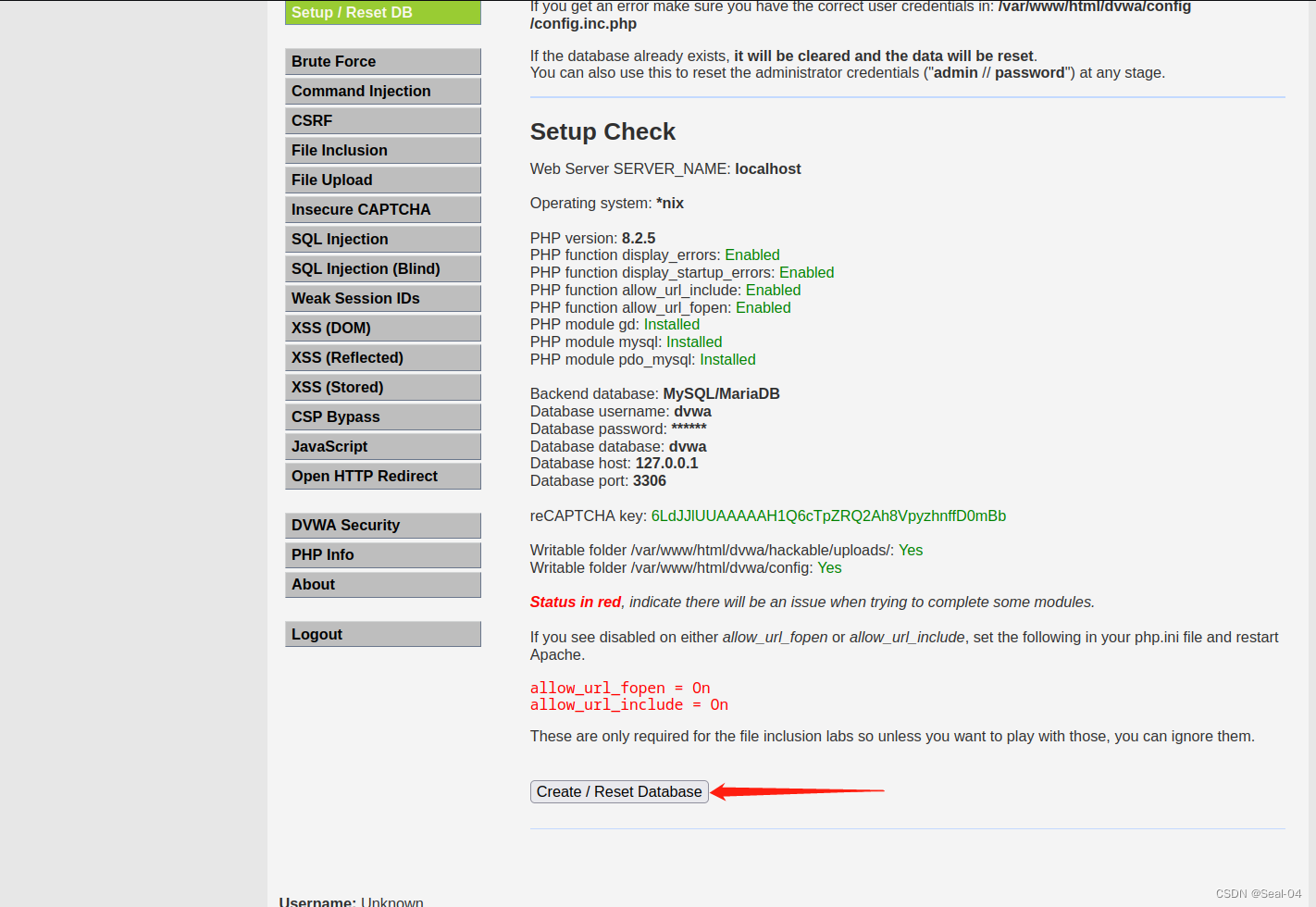
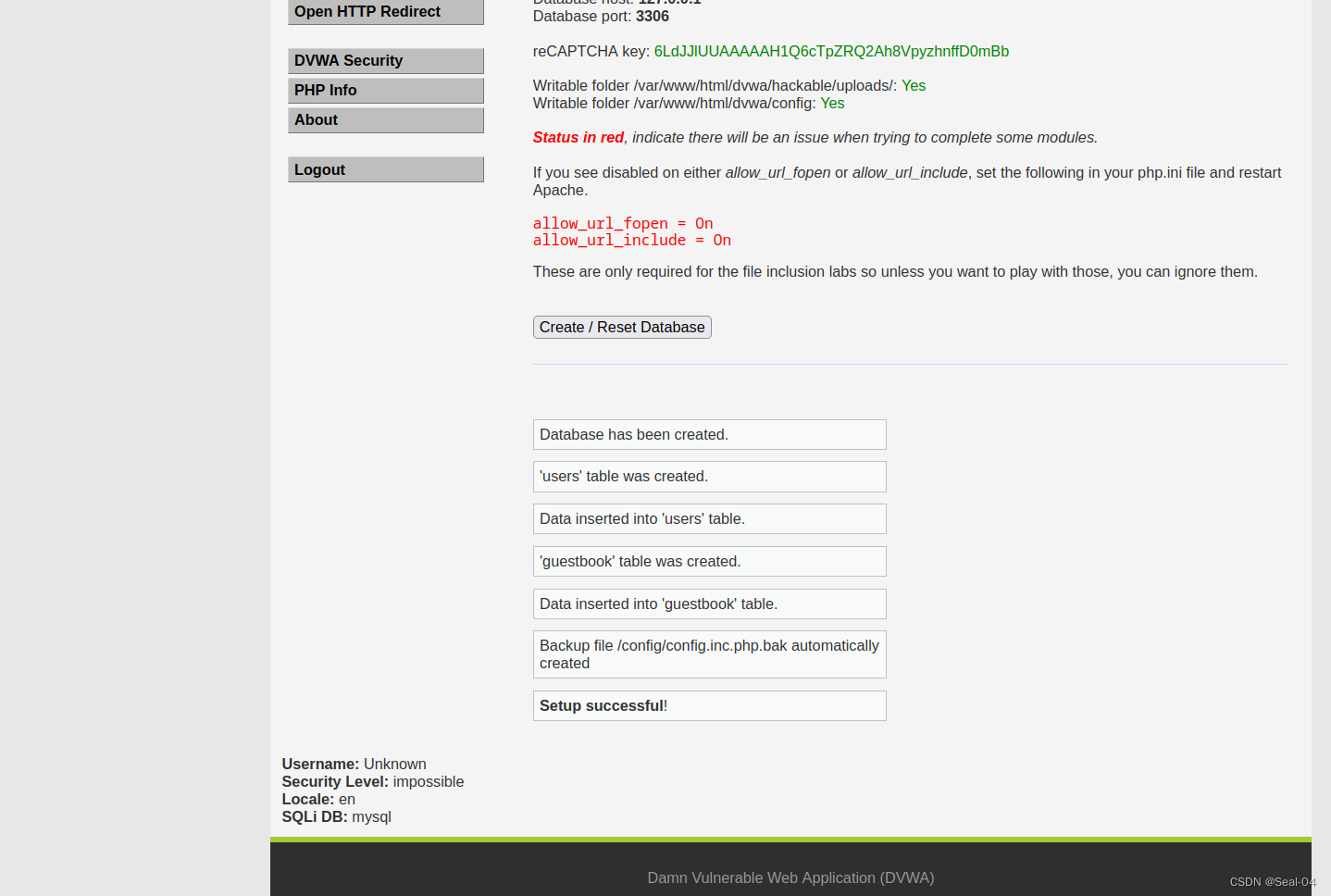
DVWA默认登陆的用户名:admin ,默认密码:password