压缩包加密后门

You might have heard the term “encryption backdoor” in the news recently. We’ll explain what it is, why it’s one of the most hotly contested topics in the tech world, and how it could affect the devices you use every day.
您可能最近在新闻中听说过“加密后门”一词。 我们将解释它的含义,为什么它是技术界最受争议的主题之一,以及它如何影响您每天使用的设备。
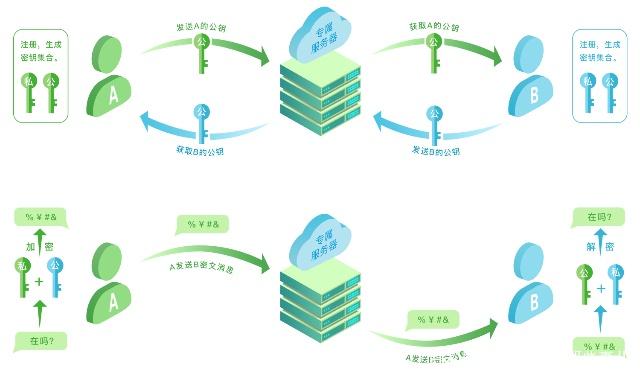
系统的访问密钥 (An Access Key into a System)
Most of the systems consumers use today have some form of encryption. To get past it, you have to provide some kind of authentication. For example, if your phone is locked, you have to use a password, your fingerprint, or facial recognition to access your apps and data.
如今,消费者使用的大多数系统都具有某种形式的加密 。 为了克服它,您必须提供某种身份验证。 例如,如果您的手机已锁定 ,则必须使用密码,指纹或面部识别才能访问您的应用程序和数据。
These systems generally do an excellent job of protecting your personal data. Even if someone takes your phone, he can’t gain access to your information unless he figures out your passcode. Plus, most phones can wipe their storage or become unusable for a time if someone tries to force them to unlock.
这些系统通常在保护您的个人数据方面做得很好。 即使有人拿走了您的电话,他也无法访问您的信息,除非他弄清楚了您的密码。 另外,如果有人试图强迫手机解锁,大多数手机会擦除其存储空间或暂时无法使用。
A backdoor is a built-in way of circumventing that type of encryption. It essentially allows a manufacturer to access all the data on any device it creates. And it’s nothing new—this reaches all the way back to the abandoned “Clipper chip” in the early ’90s.
后门是一种规避此类加密的内置方法。 实际上,它允许制造商访问其创建的任何设备上的所有数据。 它并不是什么新鲜事物,它可以一直追溯到90年代初废弃的“ Clipper芯片 ”。
Many things can serve as a backdoor. It can be a hidden aspect of the operating system, an external tool that acts as a key for every device, or a piece of code that creates a vulnerability in the software.
许多事情可以充当后门。 它可能是操作系统的一个隐藏方面,可能是每个设备的键的外部工具,也可能是在软件中造成漏洞的一段代码。
加密后门问题 (The Problem with Encryption Backdoors)
In 2015, encryption backdoors became the subject of a heated global debate when Apple and the FBI were embroiled in a legal battle. Through a series of court orders, the FBI compelled Apple to crack an iPhone that belonged to a deceased terrorist. Apple refused to create the necessary software and a hearing was scheduled. However, the FBI tapped a third-party (GrayKey), which used a security hole to bypass the encryption and the case was dropped.
2015年,当苹果和联邦调查局卷入一场法律大战时,加密后门成为全球激烈辩论的主题。 通过一系列法院命令,FBI迫使苹果破解了一个已故恐怖分子的iPhone。 苹果拒绝创建必要的软件,并安排了听证会。 但是,FBI窃听了第三方( GrayKey ),后者使用安全漏洞绕过了加密,因此案件被丢弃。
The debate has continued among technology firms and in the public sector. When the case first made headlines, nearly every major technology company in the U.S. (including Google, Facebook, and Amazon) supported Apple’s decision.
科技公司和公共部门之间的辩论仍在继续。 当案件首次成为头条新闻时,美国几乎所有主要技术公司(包括Google,Facebook和Amazon)都支持Apple的决定。
Most tech giants don’t want the government to compel them to create an encryption backdoor. They argue that a backdoor makes devices and systems significantly less secure because you’re designing the system with a vulnerability.
大多数科技巨头都不希望政府强迫他们创建加密后门。 他们认为,后门会使设备和系统的安全性大大降低,因为您正在设计带有漏洞的系统。
While only the manufacturer and the government would know how to access the backdoor at first, hackers and malicious actors would eventually discover it. Soon after, exploits would become available to many people. And if the U.S. government gets the backdoor method, would the governments of other countries get it, too?
虽然只有制造商和政府首先知道如何访问后门,但黑客和恶意行为者最终还是会发现它。 不久之后,许多人就可以使用攻击了。 如果美国政府采用后门方法,其他国家的政府也会采用这种方法吗?
This creates some frightening possibilities. Systems with backdoors would likely increase the number and scale of cybercrimes, from targeting state-owned devices and networks to creating a black market for illegal exploits. As Bruce Schneier wrote in The New York Times, it also potentially opens up critical infrastructure systems that manage major public utilities to foreign and domestic threats.
这创造了一些令人恐惧的可能性。 带有后门的系统可能会增加网络犯罪的数量和规模,从针对国有设备和网络的目标到为非法利用创造黑市。 正如布鲁斯·施耐尔(Bruce Schneier)在《纽约时报》上所写的那样,它还潜在地开放了关键的基础设施系统,该系统可以管理主要的公用事业设备,以应对国内外威胁。
Of course, it also comes at the cost of privacy. An encryption backdoor in the hands of the government allows them to look at any citizen’s personal data at any time without their consent.
当然,它也以牺牲隐私为代价。 政府手中的加密后门使他们无需征得其同意即可随时查看任何公民的个人数据。
关于后门的争论 (An Argument for a Backdoor)
Government and law enforcement agencies that want an encryption backdoor argue that the data shouldn’t be inaccessible to law enforcement and security agencies. Some murder and theft investigations have stalled because law enforcement was unable to access locked phones.
需要加密后门的政府和执法机构认为,执法人员和安全机构不应无法访问数据。 由于执法部门无法访问锁定的电话,一些谋杀和盗窃案的调查已停止。
The information stored in a smartphone, like calendars, contacts, messages, and call logs, are all things a police department might have the legal right to search with a warrant. The FBI said it faces a “Going Dark” challenge as more data and devices become inaccessible.
存储在智能手机中的信息,如日历,联系人,消息和通话记录,都是警察部门具有合法搜查令的合法权利。 FBI表示,随着越来越多的数据和设备无法访问,它面临着“ 走向黑暗 ”的挑战。
辩论仍在继续 (The Debate Continues)
Whether companies should create a backdoor in their systems remains a significant policy debate. Lawmakers and public officials frequently point out that what they really want is a “front door” that allows them to request decryption under specific circumstances.
公司是否应在其系统中创建后门仍然是一个重大的政策辩论。 议员和政府官员经常指出,他们真正想要的是一个“前门”,可以让他们在特定情况下请求解密。
However, a front door and encryption backdoor are largely the same. Both still involve creating an exploit to grant access to a device.
但是,前门和加密后门基本相同。 两者仍涉及创建漏洞以授予对设备的访问权限。
Until an official decision is rendered, this issue will likely continue to pop up in the headlines.
在做出正式决定之前,这个问题很可能会继续出现在头条新闻中。
翻译自: https://www.howtogeek.com/544727/what-is-an-encryption-backdoor/
压缩包加密后门