在网上看到很多文章写到l7是如何的强大。今天我决定试下。于是拿起笔记本,在XP下装了个双系统CentOS5.2最新的 在 [url]www.chinaunix.net[/url]下的。3G多。。。
l7作为应用层的防火墙可以对字符串进行过滤,这个我很喜欢。网上的文章也充分说明了它可以封堵讯雷和BT等P2P流量。真的很不错。
我的内核2.6.18-53.el5 iptables1.3.5
首先下载软件包
Download L7-filter kernel
[url]http://downloads.sourceforge.net/l7-filter/netfilter-layer7-v2.19.tar.gz[/url]
Download L7-filter userspace
[url]http://downloads.sourceforge.net/l7-filter/l7-filter-userspace-0.7.tar.gz[/url]
Download L7-filter Protocol definitions
[url]http://downloads.sourceforge.net/l7-filter/l7-protocols-2008-04-23.tar.gz[/url]
Download Linux Iptables 1.4.0
[url]http://www.netfilter.org/projects/iptables/files/iptables-1.4.0.tar.bz2[/url]
Download Linux Kernel 2.6.26
[url]http://www.kernel.org/pub/linux/kernel/v2.6/linux-2.6.26.tar.bz2[/url]
我比较保守 包先用XP下好 然后杀下毒 再用服务器的samba的功能对WINDOWS共享文件夹进行挂载
命令mount.cifs //IP/共享文件夹 /挂载地点 -o user=windows登陆名 回车
输入密码 ...................> ok
这里我要说下最重要的一点,关系到实验的结果。
首先停用系统中已有的iptables 比如我这里的iptables1.3.5
然后卸载rpm -e --nodeps 不考虑依赖关系直接卸载掉 这一步非常重要 这一步你没做就算你把下面操作无报错的全部完成,l7一样不能用。
把包都cp到 /usr/src里面
解压软件包 tar -vxf ............
解压好所有的包后
[root@test src]# cd /usr/src/l7-protocols-2008-04-23
[root@test l7-protocols-2008-04-23]# make install
mkdir -p /etc/l7-protocols
cp -R * /etc/l7-protocols
[root@test l7-protocols-2008-04-23]# make install
mkdir -p /etc/l7-protocols
cp -R * /etc/l7-protocols
[root@test src]# cd linux-2.6.26
[root@test linux-2.6.26]# patch -p1 < /usr/src/netfilter-layer7-v2.19/kernel-2.6.25-layer7-2.19.patch
[root@test linux-2.6.26]# make oldconfig 一路回车到底 (如果之前已经编译过 kernel source, 需先执行 make mrproper)
[root@test linux-2.6.26]# patch -p1 < /usr/src/netfilter-layer7-v2.19/kernel-2.6.25-layer7-2.19.patch
[root@test linux-2.6.26]# make oldconfig 一路回车到底 (如果之前已经编译过 kernel source, 需先执行 make mrproper)
[root@test linux-2.6.26]# make menuconfig
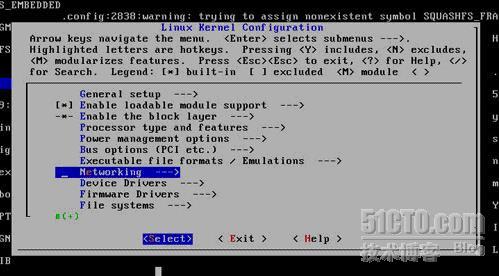
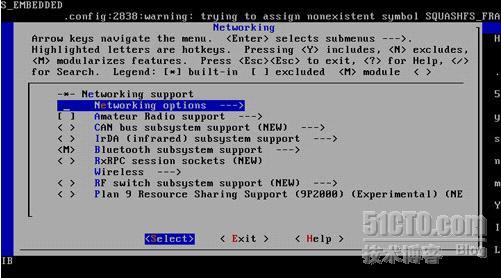
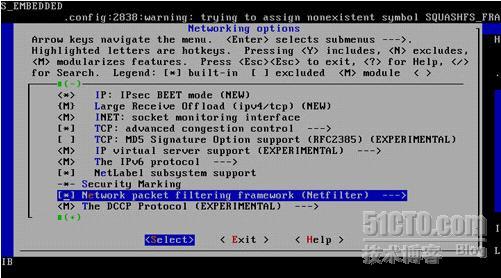
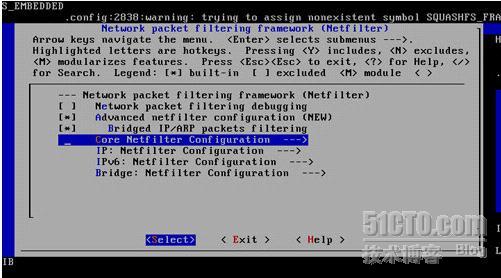
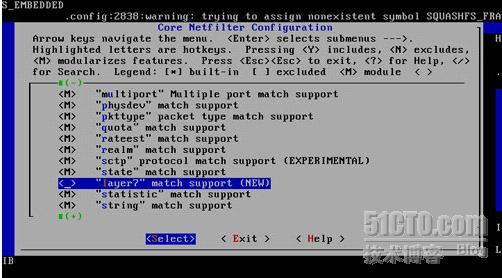
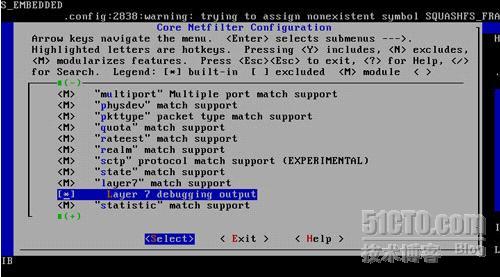
该M的地方就M *的地方就* Layer 7 match support一定要M上哈
[root@test linux-2.6.26]# make 可以去午休下了 起码半个小时 我的是华硕的笔记本 如果你们在虚拟机上面做的话 慢慢等把
注释下
make menuconfig
make
make modules_install
make install -------> 2.6的内核直接用这几个命令就可以了
make
make modules_install
make install -------> 2.6的内核直接用这几个命令就可以了
2.4的内核需要下面这几个命令
make menuconfig
make dep
make bzp_w_picpath
make modules
make modules_install
make install
make dep
make bzp_w_picpath
make modules
make modules_install
make install
[root@test linux-2.6.26]# make modules_install
[root@test linux-2.6.26]# make install
[root@test linux-2.6.26]# reboot
OK了
OK了
[root@test ~]# uname -a
Linux test 2.6.26 #1 SMP Fri Sep 19 14:51:18 CST 2008 i686 athlon i386 GNU/Linux
Linux test 2.6.26 #1 SMP Fri Sep 19 14:51:18 CST 2008 i686 athlon i386 GNU/Linux
内核编译成功了!!!
现在回到原来的内核 如果你用新内核进行下一步操作是不会成功的
现在处理iptables了
[root@test ~]# cd /usr/src/iptables-1.4.0
[root@test iptables-1.4.0]# patch -p1 < /usr/src/netfilter-layer7-v2.19/iptables-1.4-for-kernel-2.6.20forward-layer7-2.19.patch
[root@test iptables-1.4.0]# patch -p1 < /usr/src/netfilter-layer7-v2.19/iptables-1.4-for-kernel-2.6.20forward-layer7-2.19.patch
[root@test iptables-1.4.0]# chmod +x extensions/.layer7-test
[root@test iptables-1.4.0]# make KERNEL_DIR=/usr/src/linux-2.6.26
[root@test iptables-1.4.0]# make install KERNEL_DIR=/usr/src/linux-2.6.26
[root@test iptables-1.4.0]# make install KERNEL_DIR=/usr/src/linux-2.6.26
OK了。。。。。。。 
reboot
启动2.6.26的内核
现在来测试下l7
[root@test ~]# iptables -m layer7 --help
iptables v1.4.0
iptables v1.4.0
Usage: iptables -[AD] chain rule-specification [options]
iptables -[RI] chain rulenum rule-specification [options]
iptables -D chain rulenum [options]
iptables -[LFZ] [chain] [options]
iptables -[NX] chain
iptables -E old-chain-name new-chain-name
iptables -P chain target [options]
iptables -h (print this help information)
iptables -[RI] chain rulenum rule-specification [options]
iptables -D chain rulenum [options]
iptables -[LFZ] [chain] [options]
iptables -[NX] chain
iptables -E old-chain-name new-chain-name
iptables -P chain target [options]
iptables -h (print this help information)
Commands:
Either long or short options are allowed.
--append -A chain Append to chain
--delete -D chain Delete matching rule from chain
--delete -D chain rulenum
Delete rule rulenum (1 = first) from chain
--insert -I chain [rulenum]
Insert in chain as rulenum (default 1=first)
--replace -R chain rulenum
Replace rule rulenum (1 = first) in chain
--list -L [chain] List the rules in a chain or all chains
--flush -F [chain] Delete all rules in chain or all chains
--zero -Z [chain] Zero counters in chain or all chains
--new -N chain Create a new user-defined chain
--delete-chain
-X [chain] Delete a user-defined chain
--policy -P chain target
Change policy on chain to target
--rename-chain
-E old-chain new-chain
Change chain name, (moving any references)
Options:
--proto -p [!] proto protocol: by number or name, eg. `tcp'
--source -s [!] address[/mask]
source specification
--destination -d [!] address[/mask]
destination specification
--in-interface -i [!] input name[+]
network interface name ([+] for wildcard)
--jump -j target
target for rule (may load target extension)
--goto -g chain
jump to chain with no return
--match -m match
extended match (may load extension)
--numeric -n numeric output of addresses and ports
--out-interface -o [!] output name[+]
network interface name ([+] for wildcard)
--table -t table table to manipulate (default: `filter')
--verbose -v verbose mode
--line-numbers print line numbers when listing
--exact -x expand numbers (display exact values)
[!] --fragment -f match second or further fragments only
--modprobe=<command> try to insert modules using this command
--set-counters PKTS BYTES set the counter during insert/append
[!] --version -V print package version.
Either long or short options are allowed.
--append -A chain Append to chain
--delete -D chain Delete matching rule from chain
--delete -D chain rulenum
Delete rule rulenum (1 = first) from chain
--insert -I chain [rulenum]
Insert in chain as rulenum (default 1=first)
--replace -R chain rulenum
Replace rule rulenum (1 = first) in chain
--list -L [chain] List the rules in a chain or all chains
--flush -F [chain] Delete all rules in chain or all chains
--zero -Z [chain] Zero counters in chain or all chains
--new -N chain Create a new user-defined chain
--delete-chain
-X [chain] Delete a user-defined chain
--policy -P chain target
Change policy on chain to target
--rename-chain
-E old-chain new-chain
Change chain name, (moving any references)
Options:
--proto -p [!] proto protocol: by number or name, eg. `tcp'
--source -s [!] address[/mask]
source specification
--destination -d [!] address[/mask]
destination specification
--in-interface -i [!] input name[+]
network interface name ([+] for wildcard)
--jump -j target
target for rule (may load target extension)
--goto -g chain
jump to chain with no return
--match -m match
extended match (may load extension)
--numeric -n numeric output of addresses and ports
--out-interface -o [!] output name[+]
network interface name ([+] for wildcard)
--table -t table table to manipulate (default: `filter')
--verbose -v verbose mode
--line-numbers print line numbers when listing
--exact -x expand numbers (display exact values)
[!] --fragment -f match second or further fragments only
--modprobe=<command> try to insert modules using this command
--set-counters PKTS BYTES set the counter during insert/append
[!] --version -V print package version.
LAYER7 match v1.4.0 options:
--l7dir <directory> : Look for patterns here instead of /etc/l7-protocols/
(--l7dir must be specified before --l7proto if used!)
--l7proto [!] <name> : Match the protocol defined in /etc/l7-protocols/name.pat
--l7dir <directory> : Look for patterns here instead of /etc/l7-protocols/
(--l7dir must be specified before --l7proto if used!)
--l7proto [!] <name> : Match the protocol defined in /etc/l7-protocols/name.pat
是不是???成功了 呵呵 


如何应用
iptables -t mangle -A POSTROUTING -m layer7 --l7proto xxx -j DROP
xxx那里就是你要封的东西。
l7支持的通讯软件或者协议课题参考 /etc/l7-protocols/protocols/ 下的文件
L7-filter 支持的通讯协议: L7-filter Supported Protocols
iptables 封包过滤图: [url]http://linux-ip.net/nf/nfk-traversal.png[/url]
可使用 -j MARK 参数 QoS 带宽管理, 参考地址: cbq.init 設定手札
转载于:https://blog.51cto.com/kevinleo/98197