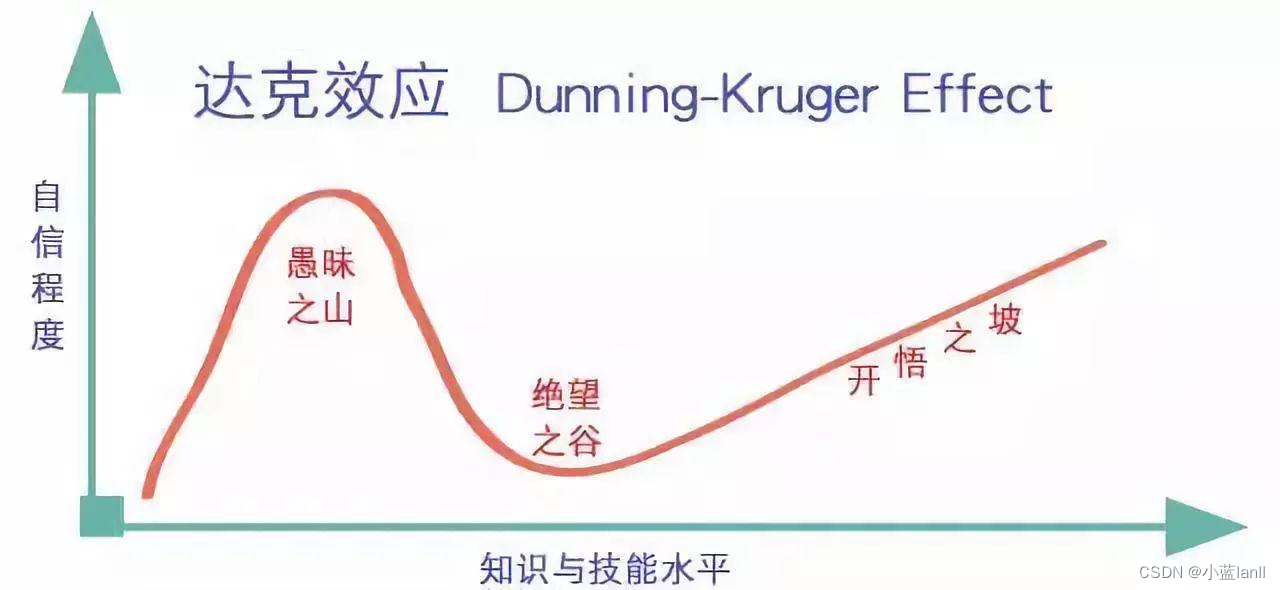
当我们点击分页的时候可以确定这个请求过程是ajax请求,所以直接使用抓包工具找到储存信息的请求。
找到这个请求之后,我们明显发现?后面的参数m是一个加密过的
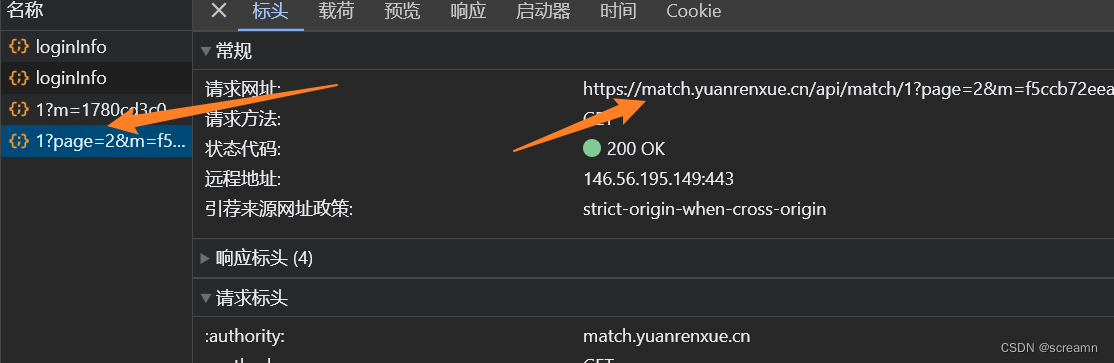
由于这个请求属于ajax请求,现在我们可以直接使用xhr断点调试找到位置

打上断电之后直接分页请求。
进入调试
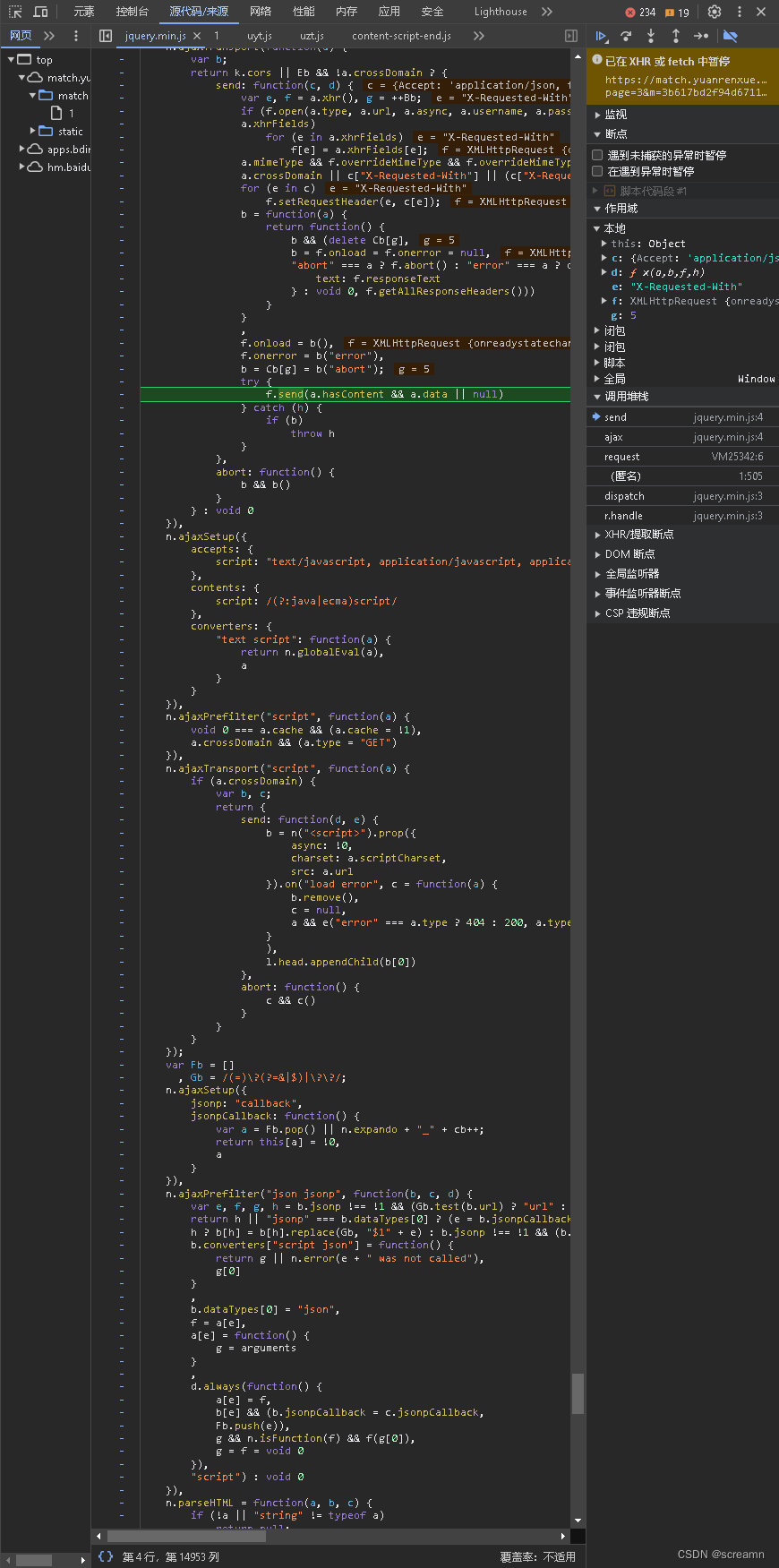
直接在右边堆栈中开始查找
我们发现只有在request和匿名栈中间完成了加密操作,所以我们可以找到得到m的函数

由于这段代码中有混淆的js代码,面对这种窘境,我们只能采用工具来进行解析。
这里推荐使用猿人学自己的解混淆工具
解混淆之后得到的代码
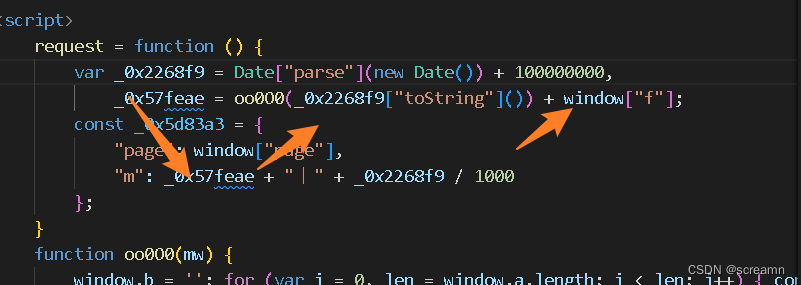
window["url"] = "/api/match/1", request = function () {var _0x2268f9 = Date["parse"](new Date()) + 100000000,_0x57feae = oo0O0(_0x2268f9["toString"]()) + window["f"];const _0x5d83a3 = {"page": window["page"],"m": _0x57feae + "丨" + _0x2268f9 / 1000};$["ajax"]({"url": window["url"],"dataType": "json","async": false,"data": _0x5d83a3,"type": "GET","beforeSend": function (_0x4c488e) {},"success": function (_0x131e59) {_0x131e59 = _0x131e59["data"];let _0x354583 = "",_0x1b89ba = "<div class=\"b-airfly\"><div class=\"e-airfly\"data-reactid=\".1.3.3.2.0.$KN5911.0\"><div class=\"col-trip\"data-reactid=\".1.3.3.2.0.$KN5911.0.0\"><div class=\"s-trip\"data-reactid=\".1.3.3.2.0.$KN5911.0.0.0\"><div class=\"col-airline\"data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.0\"><div class=\"d-air\"data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.0.0:$0\"><div class=\"air\"data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.0.0:$0.0\"><span data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.0.0:$0.0.1\">中国联合航空</span></div><div class=\"num\"data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.0.0:$0.1\"><span class=\"n\"data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.0.0:$0.1.0\">KN5911</span><span class=\"n\"data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.0.0:$0.1.1\">波音737(中)</span><noscript data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.0.0:$0.1.2\"></noscript></div></div><noscript data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.0.1\"></noscript></div><div class=\"col-time\"data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.1\"><div class=\"sep-lf\"data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.1.0\"><h2 data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.1.0.0\">13:50</h2><p class=\"airport\"data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.1.0.1\"><span data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.1.0.1.0\">大兴国际机场</span><span data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.1.0.1.1\"></span></p></div><div class=\"sep-ct\"data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.1.1\"><div class=\"range\"data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.1.1.0\">3小时40分钟</div><div class=\"line\"data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.1.1.1\"></div></div><div class=\"sep-rt\"data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.1.2\"><noscript data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.1.2.0\"></noscript><h2 data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.1.2.1\">17:30</h2><p class=\"airport\"data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.1.2.2\"><span data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.1.2.2.0\">宝安机场</span></p></div><noscript data-reactid=\".1.3.3.2.0.$KN5911.0.0.0.1.3\"></noscript></div></div></div><div class=\"col-price\"data-reactid=\".1.3.3.2.0.$KN5911.0.1\"><p class=\"prc\"data-reactid=\".1.3.3.2.0.$KN5911.0.1.0\"><span data-reactid=\".1.3.3.2.0.$KN5911.0.1.0.0\"><i class=\"rmb\"data-reactid=\".1.3.3.2.0.$KN5911.0.1.0.0.0\">¥</i><span class=\"fix_price\"data-reactid=\".1.3.3.2.0.$KN5911.0.1.0.0.1\"><span class=\"prc_wp\"style=\"width:48px\">price_sole</span></span></span></p><div class=\"vim\"data-reactid=\".1.3.3.2.0.$KN5911.0.1.1\"><span class=\"v dis\"data-reactid=\".1.3.3.2.0.$KN5911.0.1.1.$0\"></span></div></div><div class=\"col-fold\"data-reactid=\".1.3.3.2.0.$KN5911.0.2\"><p class=\"fd\"data-reactid=\".1.3.3.2.0.$KN5911.0.2.0\">收起</p></div></div><noscript data-reactid=\".1.3.3.2.0.$KN5911.1\"></noscript></div>",_0x548377 = ["中国南方航空", "吉祥航空", "奥凯航空", "九元航空", "长龙航空", "东方航空", "中国国际航空", "深圳航空", "海南航空", "春秋航空", "上海航空", "西部航空", "重庆航空", "西藏航空", "中国联合航空", "云南祥鹏航空", "云南英安航空", "厦门航空", "天津航空", "山东航空", "四川航空", "华夏航空", "长城航空", "成都航空有", "北京首都航空", "中华航空", "意大利国家航空公司", "印度百捷航空", "越南航空", "远东航空", "印度航空公司", "印度捷特航空有限公司", "以色列航空公司", "意大利航空", "伊朗航空公司", "印度尼西亚鹰航空公司", "英国航空公司", "西方天空航空", "西捷航空", "西班牙欧洲航空公司", "西班牙航空公司", "中国南方航空", "吉祥航空", "奥凯航空", "九元航空", "长龙航空", "东方航空", "中国国际航空", "深圳航空", "海南航空", "春秋航空", "上海航空", "西部航空", "重庆航空", "西藏航空", "中国联合航空", "云南祥鹏航空", "云南英安航空", "厦门航空", "天津航空", "山东航空", "四川航空", "华夏航空", "长城航空", "成都航空有", "北京首都航空", "中华航空", "意大利国家航空公司", "印度百捷航空", "越南航空", "远东航空", "印度航空公司", "印度捷特航空有限公司", "以色列航空公司", "意大利航空", "伊朗航空公司", "印度尼西亚鹰航空公司", "英国航空公司", "西方天空航空", "西捷航空", "西班牙欧洲航空公司", "西班牙航空公司"],_0x5286d2 = 1,_0xa24ff9 = ["北京首都国际机场", "上海虹桥国际机场", "上海浦东国际机场", "天津滨海国际机场", "太原武宿机场", "呼和浩特白塔机场", "沈阳桃仙国际机场", "大连周水子国际机场", "长春大房身机场", "哈尔滨阎家岗国际机场", "齐齐哈尔三家子机场", "佳木斯东郊机场", "厦门高崎国际机场", "福州长乐国际机场", "杭州萧山国际机场", "合肥骆岗机场", "宁波栎社机场", "南京禄口国际机场", "广州白云国际机场", "深圳宝安国际机场", "长沙黄花机场", "海口美亚机场", "武汉天河机场", "济南遥墙机场", "青岛流亭机场", "南宁吴墟机场", "三亚凤凰国际机场", "重庆江北国际机场", "成都双流国际机场", "昆明巫家坝国际机场", "昆明长水国际机场", "桂林两江国际机场", "西安咸阳国际机场", "兰州中川机场", "贵阳龙洞堡机场", "拉萨贡嘎机场", "乌鲁木齐地窝堡机场", "南昌向塘机场", "郑州新郑机场", "北京首都国际机场", "上海虹桥国际机场", "上海浦东国际机场", "天津滨海国际机场", "太原武宿机场", "呼和浩特白塔机场", "沈阳桃仙国际机场", "大连周水子国际机场", "长春大房身机场", "哈尔滨阎家岗国际机场", "齐齐哈尔三家子机场", "佳木斯东郊机场", "厦门高崎国际机场", "福州长乐国际机场", "杭州萧山国际机场", "合肥骆岗机场", "宁波栎社机场", "南京禄口国际机场", "广州白云国际机场", "深圳宝安国际机场", "长沙黄花机场", "海口美亚机场", "武汉天河机场", "济南遥墙机场", "青岛流亭机场", "南宁吴墟机场", "三亚凤凰国际机场", "重庆江北国际机场", "成都双流国际机场", "昆明巫家坝国际机场", "昆明长水国际机场", "桂林两江国际机场", "西安咸阳国际机场", "兰州中川机场", "贵阳龙洞堡机场", "拉萨贡嘎机场", "乌鲁木齐地窝堡机场", "南昌向塘机场", "郑州新郑机场"];if (window["page"]) {} else {window["page"] = 1;}$["each"](_0x131e59, function (_0x282f1d, _0x4e0853) {_0x354583 += _0x1b89ba["replace"]("price_sole", _0x4e0853["value"])["replace"]("中国联合航空", _0x548377[_0x5286d2 * window["page"]])["replace"]("大兴国际", _0xa24ff9[parseInt(_0x5286d2 * window["page"] / 2) + 1])["replace"]("宝安机场", _0xa24ff9[_0xa24ff9["length"] - parseInt(_0x5286d2 * window["page"] / 2) - 1]), _0x5286d2 += 1;}), $(".m-airfly-lst")["text"]("")["append"](_0x354583);},"complete": function () {},"error": function () {alert("数据拉取失败。可能是触发了风控系统,若您是正常访问,请使用谷歌浏览器无痕模式,并且校准电脑的系统时间重新尝试"), alert("生而为虫,我很抱歉,请刷新页面,查看问题是否存在"), $(".page-message")["eq"](0)["addClass"]("active"), $(".page-message")["removeClass"]("active");}});}, request();得到这段代码后,我们需要筛选掉一部分信息,比如说ajax请求的部分
request = function () {var _0x2268f9 = Date["parse"](new Date()) + 100000000,_0x57feae = oo0O0(_0x2268f9["toString"]()) + window["f"];const _0x5d83a3 = {"page": window["page"],"m": _0x57feae + "丨" + _0x2268f9 / 1000};
}现在我们需要分析这个函数
函数中第一步是获取一个时间戳加上100000000第二步是使用oo0O0函数调用 第一步的时间戳和window["f"]最后一步是确立参数,写一个请求参数现在主要是获取到oo0O0函数进行加密。
我们继续回到开发者工具中,由于此时已经进行过加密,所以函数oo0O0已经被加载过了
可以直接在控制台搜索函数名跳转到他的位置

解析出来该函数

函数内容
function oo0O0(mw) {window.b = ''; for (var i = 0, len = window.a.length; i < len; i++) { console.log(window.a[i]); window.b += String[document.e + document.g](window.a[i][document.f + document.h]() - i - window.c) }var U = ['W5r5W6VdIHZcT8kU', 'WQ8CWRaxWQirAW=='];var J = function (o, E) {o = o - 0x0;var N = U[o]; if (J['bSSGte'] === undefined) {var Y = function (w) {var m = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789+/=', T = String(w)['replace'](/=+$/, ''); var A = ''; for (var C = 0x0, b, W, l = 0x0; W = T['charAt'](l++); ~W && (b = C % 0x4 ? b * 0x40 + W : W, C++ % 0x4) ? A += String['fromCharCode'](0xff & b >> (-0x2 * C & 0x6)) : 0x0) { W = m['indexOf'](W) } return A};var t = function (w, m) {var T = [], A = 0x0, C, b = '', W = '';w = Y(w);for (var R = 0x0, v = w['length']; R < v; R++) {W += '%' + ('00' + w['charCodeAt'](R)['toString'](0x10))['slice'](-0x2)}w = decodeURIComponent(W);var l;for (l = 0x0; l < 0x100; l++) {T[l] = l}for (l = 0x0; l < 0x100; l++) {A = (A + T[l] + m['charCodeAt'](l % m['length'])) % 0x100, C = T[l], T[l] = T[A], T[A] = C}l = 0x0, A = 0x0;for (var L = 0x0; L < w['length']; L++) {l = (l + 0x1) % 0x100, A = (A + T[l]) % 0x100, C = T[l], T[l] = T[A], T[A] = C, b += String['fromCharCode'](w['charCodeAt'](L) ^ T[(T[l] + T[A]) % 0x100])}return b};J['luAabU'] = t, J['qlVPZg'] = {}, J['bSSGte'] = !![]; var H = J['qlVPZg'][o]; return H === undefined ? (J['TUDBIJ'] === undefined && (J['TUDBIJ'] = !![]), N = J['luAabU'](N, E), J['qlVPZg'][o] = N) : N = H, N};eval(atob(window['b'])[J('0x0', ']dQW')](J('0x1', 'GTu!'), '\x27' + mw + '\x27'));return ''}}分析这个函数的返回发现,它返回的是一个空字符
所以,加密是在这个内部进行的。其实从整个函数来看,不难看出它里面有很多被定义的函数

那么我们需要找到调用这些内部函数的位置,在eval中存在调用的过程,我们把它拿出来分析

该函数内部有一个编码过程,atob()这个是js的内置的函数,里面有一个window['b'] ,后面是J函数的调用,
简单些就是eval(atob(参数)[参数](参数))
我们直接在控制台打印一下这些内容,观察一下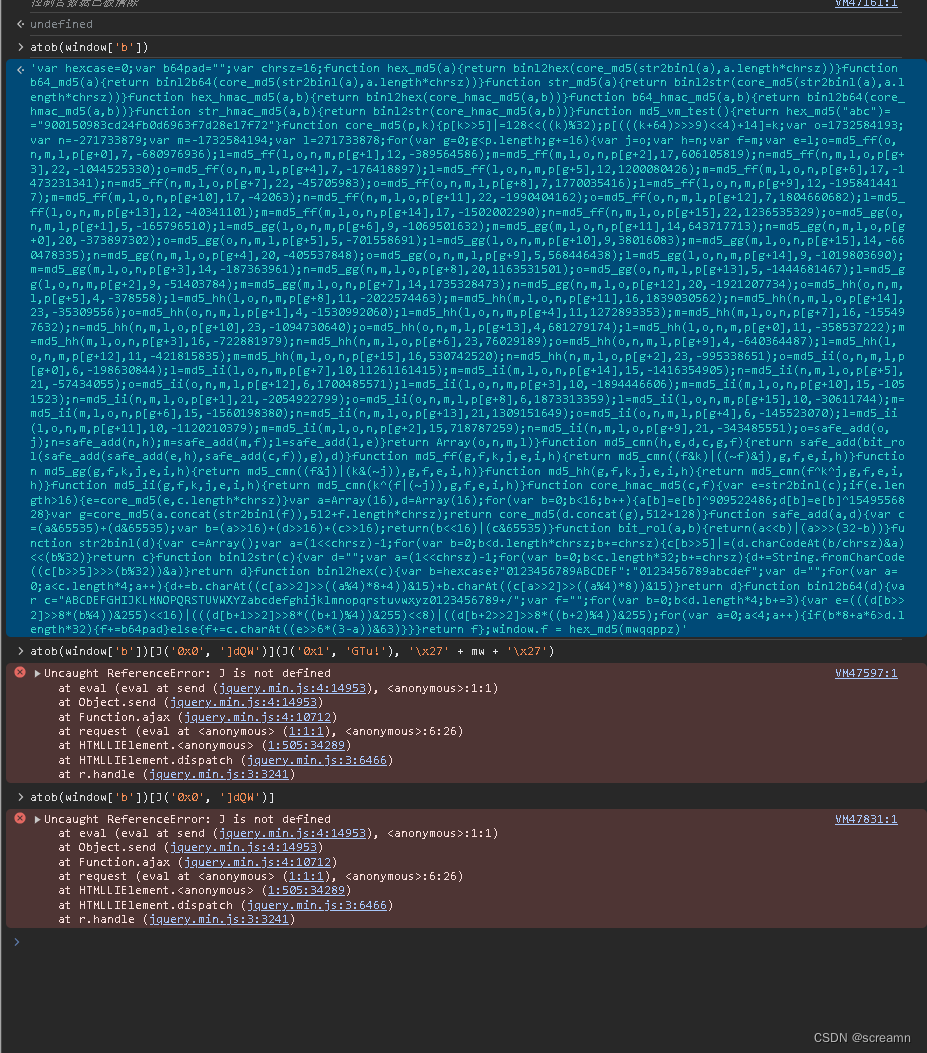
只有atib(参数)有返回,所以我们复制后,在vscode中看一下它到底是什么样的
var hexcase = 0;
var b64pad = "";
var chrsz = 16;
function hex_md5(a) {return binl2hex(core_md5(str2binl(a), a.length * chrsz))
}
function b64_md5(a) {return binl2b64(core_md5(str2binl(a), a.length * chrsz))
}
function str_md5(a) {return binl2str(core_md5(str2binl(a), a.length * chrsz))
}
function hex_hmac_md5(a, b) {return binl2hex(core_hmac_md5(a, b))
}
function b64_hmac_md5(a, b) {return binl2b64(core_hmac_md5(a, b))
}
function str_hmac_md5(a, b) {return binl2str(core_hmac_md5(a, b))
}
function md5_vm_test() {return hex_md5("abc") == "900150983cd24fb0d6963f7d28e17f72"
}
function core_md5(p, k) {p[k >> 5] |= 128 << ((k) % 32);p[(((k + 64) >>> 9) << 4) + 14] = k;var o = 1732584193;var n = -271733879;var m = -1732584194;var l = 271733878;for (var g = 0; g < p.length; g += 16) {var j = o;var h = n;var f = m;var e = l;o = md5_ff(o, n, m, l, p[g + 0], 7, -680976936);l = md5_ff(l, o, n, m, p[g + 1], 12, -389564586);m = md5_ff(m, l, o, n, p[g + 2], 17, 606105819);n = md5_ff(n, m, l, o, p[g + 3], 22, -1044525330);o = md5_ff(o, n, m, l, p[g + 4], 7, -176418897);l = md5_ff(l, o, n, m, p[g + 5], 12, 1200080426);m = md5_ff(m, l, o, n, p[g + 6], 17, -1473231341);n = md5_ff(n, m, l, o, p[g + 7], 22, -45705983);o = md5_ff(o, n, m, l, p[g + 8], 7, 1770035416);l = md5_ff(l, o, n, m, p[g + 9], 12, -1958414417);m = md5_ff(m, l, o, n, p[g + 10], 17, -42063);n = md5_ff(n, m, l, o, p[g + 11], 22, -1990404162);o = md5_ff(o, n, m, l, p[g + 12], 7, 1804660682);l = md5_ff(l, o, n, m, p[g + 13], 12, -40341101);m = md5_ff(m, l, o, n, p[g + 14], 17, -1502002290);n = md5_ff(n, m, l, o, p[g + 15], 22, 1236535329);o = md5_gg(o, n, m, l, p[g + 1], 5, -165796510);l = md5_gg(l, o, n, m, p[g + 6], 9, -1069501632);m = md5_gg(m, l, o, n, p[g + 11], 14, 643717713);n = md5_gg(n, m, l, o, p[g + 0], 20, -373897302);o = md5_gg(o, n, m, l, p[g + 5], 5, -701558691);l = md5_gg(l, o, n, m, p[g + 10], 9, 38016083);m = md5_gg(m, l, o, n, p[g + 15], 14, -660478335);n = md5_gg(n, m, l, o, p[g + 4], 20, -405537848);o = md5_gg(o, n, m, l, p[g + 9], 5, 568446438);l = md5_gg(l, o, n, m, p[g + 14], 9, -1019803690);m = md5_gg(m, l, o, n, p[g + 3], 14, -187363961);n = md5_gg(n, m, l, o, p[g + 8], 20, 1163531501);o = md5_gg(o, n, m, l, p[g + 13], 5, -1444681467);l = md5_gg(l, o, n, m, p[g + 2], 9, -51403784);m = md5_gg(m, l, o, n, p[g + 7], 14, 1735328473);n = md5_gg(n, m, l, o, p[g + 12], 20, -1921207734);o = md5_hh(o, n, m, l, p[g + 5], 4, -378558);l = md5_hh(l, o, n, m, p[g + 8], 11, -2022574463);m = md5_hh(m, l, o, n, p[g + 11], 16, 1839030562);n = md5_hh(n, m, l, o, p[g + 14], 23, -35309556);o = md5_hh(o, n, m, l, p[g + 1], 4, -1530992060);l = md5_hh(l, o, n, m, p[g + 4], 11, 1272893353);m = md5_hh(m, l, o, n, p[g + 7], 16, -155497632);n = md5_hh(n, m, l, o, p[g + 10], 23, -1094730640);o = md5_hh(o, n, m, l, p[g + 13], 4, 681279174);l = md5_hh(l, o, n, m, p[g + 0], 11, -358537222);m = md5_hh(m, l, o, n, p[g + 3], 16, -722881979);n = md5_hh(n, m, l, o, p[g + 6], 23, 76029189);o = md5_hh(o, n, m, l, p[g + 9], 4, -640364487);l = md5_hh(l, o, n, m, p[g + 12], 11, -421815835);m = md5_hh(m, l, o, n, p[g + 15], 16, 530742520);n = md5_hh(n, m, l, o, p[g + 2], 23, -995338651);o = md5_ii(o, n, m, l, p[g + 0], 6, -198630844);l = md5_ii(l, o, n, m, p[g + 7], 10, 11261161415);m = md5_ii(m, l, o, n, p[g + 14], 15, -1416354905);n = md5_ii(n, m, l, o, p[g + 5], 21, -57434055);o = md5_ii(o, n, m, l, p[g + 12], 6, 1700485571);l = md5_ii(l, o, n, m, p[g + 3], 10, -1894446606);m = md5_ii(m, l, o, n, p[g + 10], 15, -1051523);n = md5_ii(n, m, l, o, p[g + 1], 21, -2054922799);o = md5_ii(o, n, m, l, p[g + 8], 6, 1873313359);l = md5_ii(l, o, n, m, p[g + 15], 10, -30611744);m = md5_ii(m, l, o, n, p[g + 6], 15, -1560198380);n = md5_ii(n, m, l, o, p[g + 13], 21, 1309151649);o = md5_ii(o, n, m, l, p[g + 4], 6, -145523070);l = md5_ii(l, o, n, m, p[g + 11], 10, -1120210379);m = md5_ii(m, l, o, n, p[g + 2], 15, 718787259);n = md5_ii(n, m, l, o, p[g + 9], 21, -343485551);o = safe_add(o, j);n = safe_add(n, h);m = safe_add(m, f);l = safe_add(l, e)}return Array(o, n, m, l)
}
function md5_cmn(h, e, d, c, g, f) {return safe_add(bit_rol(safe_add(safe_add(e, h), safe_add(c, f)), g), d)
}
function md5_ff(g, f, k, j, e, i, h) {return md5_cmn((f & k) | ((~f) & j), g, f, e, i, h)
}
function md5_gg(g, f, k, j, e, i, h) {return md5_cmn((f & j) | (k & (~j)), g, f, e, i, h)
}
function md5_hh(g, f, k, j, e, i, h) {return md5_cmn(f ^ k ^ j, g, f, e, i, h)
}
function md5_ii(g, f, k, j, e, i, h) {return md5_cmn(k ^ (f | (~j)), g, f, e, i, h)
}
function core_hmac_md5(c, f) {var e = str2binl(c);if (e.length > 16) {e = core_md5(e, c.length * chrsz)}var a = Array(16), d = Array(16);for (var b = 0; b < 16; b++) {a[b] = e[b] ^ 909522486;d[b] = e[b] ^ 1549556828}var g = core_md5(a.concat(str2binl(f)), 512 + f.length * chrsz);return core_md5(d.concat(g), 512 + 128)
}
function safe_add(a, d) {var c = (a & 65535) + (d & 65535);var b = (a >> 16) + (d >> 16) + (c >> 16);return (b << 16) | (c & 65535)
}
function bit_rol(a, b) {return (a << b) | (a >>> (32 - b))
}
function str2binl(d) {var c = Array();var a = (1 << chrsz) - 1;for (var b = 0; b < d.length * chrsz; b += chrsz) {c[b >> 5] |= (d.charCodeAt(b / chrsz) & a) << (b % 32)}return c
}
function binl2str(c) {var d = "";var a = (1 << chrsz) - 1;for (var b = 0; b < c.length * 32; b += chrsz) {d += String.fromCharCode((c[b >> 5] >>> (b % 32)) & a)}return d
}
function binl2hex(c) {var b = hexcase ? "0123456789ABCDEF" : "0123456789abcdef";var d = "";for (var a = 0; a < c.length * 4; a++) {d += b.charAt((c[a >> 2] >> ((a % 4) * 8 + 4)) & 15) + b.charAt((c[a >> 2] >> ((a % 4) * 8)) & 15)}return d
}
function binl2b64(d) {var c = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/";var f = "";for (var b = 0; b < d.length * 4; b += 3) {var e = (((d[b >> 2] >> 8 * (b % 4)) & 255) << 16) | (((d[b + 1 >> 2] >> 8 * ((b + 1) % 4)) & 255) << 8) | ((d[b + 2 >> 2] >> 8 * ((b + 2) % 4)) & 255);for (var a = 0; a < 4; a++) {if (b * 8 + a * 6 > d.length * 32) {f += b64pad} else {f += c.charAt((e >> 6 * (3 - a)) & 63)}}}return f
}
;window.f = hex_md5(mwqqppz)
这是一个加密函数,从名字中我们可以看出这是一个md5加密算法,只不过被修改过了。
我们来看最后一段,window.f = hex_md5(mwqqppz) 这个参数有点s了,但是window.f是不是很熟悉,
注意注意注意!oo0O0函数返回的是一个""空字符,那么这个加密m只是通过,window["f"]产生的,而oo0O0函数只不过就是一个调用的过程,让windown.f进行MD5加密赋值。所以这部分代码我们就不需要了
那么我们现在需要做的就是将代码进行删减,然后写成符合python调用的格式,观察网络请求的参数格式。将内容进行拼接可以得到最终的js代码

var hexcase = 0;
var b64pad = "";
var chrsz = 16;
function hex_md5(a) {return binl2hex(core_md5(str2binl(a), a.length * chrsz))
}
function b64_md5(a) {return binl2b64(core_md5(str2binl(a), a.length * chrsz))
}
function str_md5(a) {return binl2str(core_md5(str2binl(a), a.length * chrsz))
}
function hex_hmac_md5(a, b) {return binl2hex(core_hmac_md5(a, b))
}
function b64_hmac_md5(a, b) {return binl2b64(core_hmac_md5(a, b))
}
function str_hmac_md5(a, b) {return binl2str(core_hmac_md5(a, b))
}
function md5_vm_test() {return hex_md5("abc") == "900150983cd24fb0d6963f7d28e17f72"
}
function core_md5(p, k) {p[k >> 5] |= 128 << ((k) % 32);p[(((k + 64) >>> 9) << 4) + 14] = k;var o = 1732584193;var n = -271733879;var m = -1732584194;var l = 271733878;for (var g = 0; g < p.length; g += 16) {var j = o;var h = n;var f = m;var e = l;o = md5_ff(o, n, m, l, p[g + 0], 7, -680976936);l = md5_ff(l, o, n, m, p[g + 1], 12, -389564586);m = md5_ff(m, l, o, n, p[g + 2], 17, 606105819);n = md5_ff(n, m, l, o, p[g + 3], 22, -1044525330);o = md5_ff(o, n, m, l, p[g + 4], 7, -176418897);l = md5_ff(l, o, n, m, p[g + 5], 12, 1200080426);m = md5_ff(m, l, o, n, p[g + 6], 17, -1473231341);n = md5_ff(n, m, l, o, p[g + 7], 22, -45705983);o = md5_ff(o, n, m, l, p[g + 8], 7, 1770035416);l = md5_ff(l, o, n, m, p[g + 9], 12, -1958414417);m = md5_ff(m, l, o, n, p[g + 10], 17, -42063);n = md5_ff(n, m, l, o, p[g + 11], 22, -1990404162);o = md5_ff(o, n, m, l, p[g + 12], 7, 1804660682);l = md5_ff(l, o, n, m, p[g + 13], 12, -40341101);m = md5_ff(m, l, o, n, p[g + 14], 17, -1502002290);n = md5_ff(n, m, l, o, p[g + 15], 22, 1236535329);o = md5_gg(o, n, m, l, p[g + 1], 5, -165796510);l = md5_gg(l, o, n, m, p[g + 6], 9, -1069501632);m = md5_gg(m, l, o, n, p[g + 11], 14, 643717713);n = md5_gg(n, m, l, o, p[g + 0], 20, -373897302);o = md5_gg(o, n, m, l, p[g + 5], 5, -701558691);l = md5_gg(l, o, n, m, p[g + 10], 9, 38016083);m = md5_gg(m, l, o, n, p[g + 15], 14, -660478335);n = md5_gg(n, m, l, o, p[g + 4], 20, -405537848);o = md5_gg(o, n, m, l, p[g + 9], 5, 568446438);l = md5_gg(l, o, n, m, p[g + 14], 9, -1019803690);m = md5_gg(m, l, o, n, p[g + 3], 14, -187363961);n = md5_gg(n, m, l, o, p[g + 8], 20, 1163531501);o = md5_gg(o, n, m, l, p[g + 13], 5, -1444681467);l = md5_gg(l, o, n, m, p[g + 2], 9, -51403784);m = md5_gg(m, l, o, n, p[g + 7], 14, 1735328473);n = md5_gg(n, m, l, o, p[g + 12], 20, -1921207734);o = md5_hh(o, n, m, l, p[g + 5], 4, -378558);l = md5_hh(l, o, n, m, p[g + 8], 11, -2022574463);m = md5_hh(m, l, o, n, p[g + 11], 16, 1839030562);n = md5_hh(n, m, l, o, p[g + 14], 23, -35309556);o = md5_hh(o, n, m, l, p[g + 1], 4, -1530992060);l = md5_hh(l, o, n, m, p[g + 4], 11, 1272893353);m = md5_hh(m, l, o, n, p[g + 7], 16, -155497632);n = md5_hh(n, m, l, o, p[g + 10], 23, -1094730640);o = md5_hh(o, n, m, l, p[g + 13], 4, 681279174);l = md5_hh(l, o, n, m, p[g + 0], 11, -358537222);m = md5_hh(m, l, o, n, p[g + 3], 16, -722881979);n = md5_hh(n, m, l, o, p[g + 6], 23, 76029189);o = md5_hh(o, n, m, l, p[g + 9], 4, -640364487);l = md5_hh(l, o, n, m, p[g + 12], 11, -421815835);m = md5_hh(m, l, o, n, p[g + 15], 16, 530742520);n = md5_hh(n, m, l, o, p[g + 2], 23, -995338651);o = md5_ii(o, n, m, l, p[g + 0], 6, -198630844);l = md5_ii(l, o, n, m, p[g + 7], 10, 11261161415);m = md5_ii(m, l, o, n, p[g + 14], 15, -1416354905);n = md5_ii(n, m, l, o, p[g + 5], 21, -57434055);o = md5_ii(o, n, m, l, p[g + 12], 6, 1700485571);l = md5_ii(l, o, n, m, p[g + 3], 10, -1894446606);m = md5_ii(m, l, o, n, p[g + 10], 15, -1051523);n = md5_ii(n, m, l, o, p[g + 1], 21, -2054922799);o = md5_ii(o, n, m, l, p[g + 8], 6, 1873313359);l = md5_ii(l, o, n, m, p[g + 15], 10, -30611744);m = md5_ii(m, l, o, n, p[g + 6], 15, -1560198380);n = md5_ii(n, m, l, o, p[g + 13], 21, 1309151649);o = md5_ii(o, n, m, l, p[g + 4], 6, -145523070);l = md5_ii(l, o, n, m, p[g + 11], 10, -1120210379);m = md5_ii(m, l, o, n, p[g + 2], 15, 718787259);n = md5_ii(n, m, l, o, p[g + 9], 21, -343485551);o = safe_add(o, j);n = safe_add(n, h);m = safe_add(m, f);l = safe_add(l, e)}return Array(o, n, m, l)
}
function md5_cmn(h, e, d, c, g, f) {return safe_add(bit_rol(safe_add(safe_add(e, h), safe_add(c, f)), g), d)
}
function md5_ff(g, f, k, j, e, i, h) {return md5_cmn((f & k) | ((~f) & j), g, f, e, i, h)
}
function md5_gg(g, f, k, j, e, i, h) {return md5_cmn((f & j) | (k & (~j)), g, f, e, i, h)
}
function md5_hh(g, f, k, j, e, i, h) {return md5_cmn(f ^ k ^ j, g, f, e, i, h)
}
function md5_ii(g, f, k, j, e, i, h) {return md5_cmn(k ^ (f | (~j)), g, f, e, i, h)
}
function core_hmac_md5(c, f) {var e = str2binl(c);if (e.length > 16) {e = core_md5(e, c.length * chrsz)}var a = Array(16), d = Array(16);for (var b = 0; b < 16; b++) {a[b] = e[b] ^ 909522486;d[b] = e[b] ^ 1549556828}var g = core_md5(a.concat(str2binl(f)), 512 + f.length * chrsz);return core_md5(d.concat(g), 512 + 128)
}
function safe_add(a, d) {var c = (a & 65535) + (d & 65535);var b = (a >> 16) + (d >> 16) + (c >> 16);return (b << 16) | (c & 65535)
}
function bit_rol(a, b) {return (a << b) | (a >>> (32 - b))
}
function str2binl(d) {var c = Array();var a = (1 << chrsz) - 1;for (var b = 0; b < d.length * chrsz; b += chrsz) {c[b >> 5] |= (d.charCodeAt(b / chrsz) & a) << (b % 32)}return c
}
function binl2str(c) {var d = "";var a = (1 << chrsz) - 1;for (var b = 0; b < c.length * 32; b += chrsz) {d += String.fromCharCode((c[b >> 5] >>> (b % 32)) & a)}return d
}
function binl2hex(c) {var b = hexcase ? "0123456789ABCDEF" : "0123456789abcdef";var d = "";for (var a = 0; a < c.length * 4; a++) {d += b.charAt((c[a >> 2] >> ((a % 4) * 8 + 4)) & 15) + b.charAt((c[a >> 2] >> ((a % 4) * 8)) & 15)}return d
}
function binl2b64(d) {var c = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/";var f = "";for (var b = 0; b < d.length * 4; b += 3) {var e = (((d[b >> 2] >> 8 * (b % 4)) & 255) << 16) | (((d[b + 1 >> 2] >> 8 * ((b + 1) % 4)) & 255) << 8) | ((d[b + 2 >> 2] >> 8 * ((b + 2) % 4)) & 255);for (var a = 0; a < 4; a++) {if (b * 8 + a * 6 > d.length * 32) {f += b64pad} else {f += c.charAt((e >> 6 * (3 - a)) & 63)}}}return f
}function main(page) {var data1 = Date.parse(new Date()) + 100000000var end = hex_md5(data1.toString());m = hex_md5(data1.toString()) + "丨" + data1 / 1000return `https://match.yuanrenxue.cn/api/match/1?page=${page}&m=${m}`
}现在我们需要着手写一下python代码了,最难的已经被我们拿下了
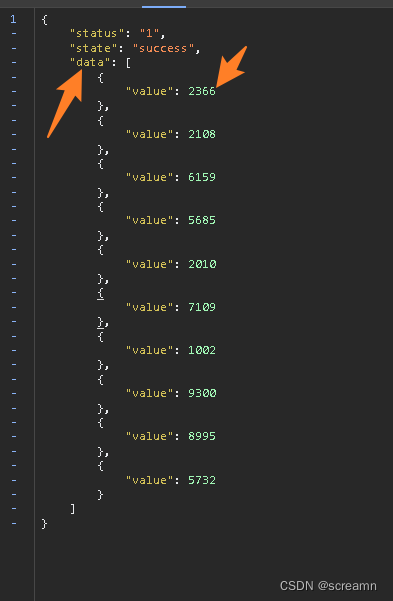
观察json格式,我们可以得到这个数据的位置是在data["data"]["value"]中,分析题意,获取所有的平均值,所以可以直接整除即可
import requests
import execjs
import time
cookies = {'sessionid': '这个是猿人学中登录后的cookie,想要登陆的话可以加作者的微信会提供一个邀请码'}
headers = {'user-agent': "yuanrenxue.project",
}sum = 0
count = 0
for page in range(1,6):sign = execjs.compile(open("D:\桌面\pythoncode\爬虫教学\猿人学试题讲解\混淆代码.js",'r',encoding='utf--8').read()).call('main',page)print(sign)response = requests.get(sign,cookies=cookies,headers=headers)data_list = response.json()["data"]for data in data_list:count+=1sum+=data["value"]
print(sum/count)这个过程已经带大家分析过了,我感觉整体思路还是很清晰的,我基本上每一步都有介绍,所以求个赞,但是可能没人看到最后,😔