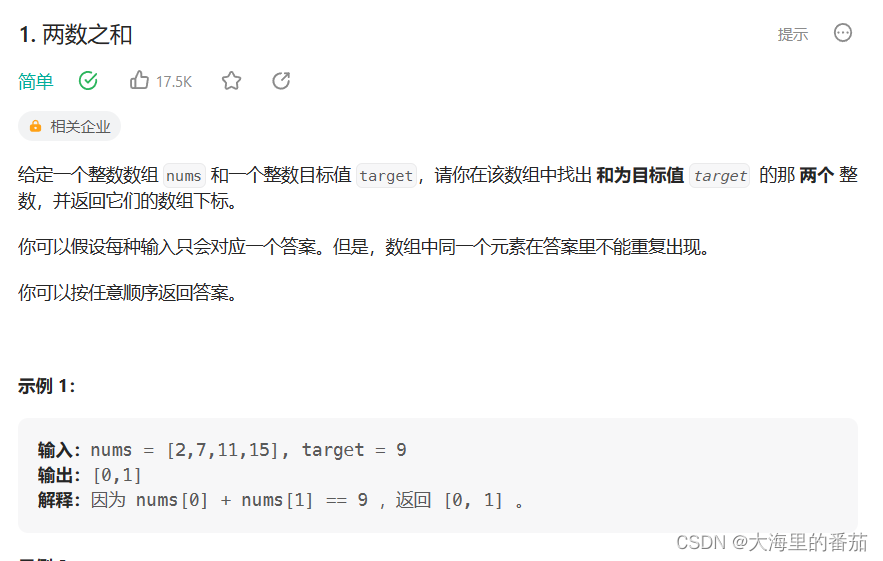
Filter表 是以kernel module形式加载的(insmod iptable_filter) 入口在net/ipv4/netfilter/iptable_filter.c中 Filter表主要在以下Hook点起作用: # define FILTER_VALID_HOOKS ( ( 1 << NF_INET_LOCAL_IN) | \ ( 1 << NF_INET_FORWARD) | \ ( 1 << NF_INET_LOCAL_OUT) ) static const struct xt_table packet_filter = { . name = "filter" , . valid_hooks = FILTER_VALID_HOOKS, . me = THIS_MODULE, . af = NFPROTO_IPV4, . priority = NF_IP_PRI_FILTER,
} ;
static struct pernet_operations iptable_filter_net_ops = { . init = iptable_filter_net_init, . exit = iptable_filter_net_exit,
} ; static int __init iptable_filter_init ( void )
{ int ret; ret = register_pernet_subsys ( & iptable_filter_net_ops) ; if ( ret < 0 ) return ret; filter_ops = xt_hook_link ( & packet_filter, iptable_filter_hook) ; if ( IS_ERR ( filter_ops) ) { ret = PTR_ERR ( filter_ops) ; unregister_pernet_subsys ( & iptable_filter_net_ops) ; } return ret;
}
static int __net_init iptable_filter_net_init ( struct net * net)
{ struct ipt_replace * repl; repl = ipt_alloc_initial_table ( & packet_filter) ; if ( repl == NULL ) return - ENOMEM; ( ( struct ipt_standard * ) repl-> entries) [ 1 ] . target. verdict = forward ? - NF_ACCEPT - 1 : - NF_DROP - 1 ; net-> ipv4. iptable_filter = ipt_register_table ( net, & packet_filter, repl) ; kfree ( repl) ; return PTR_ERR_OR_ZERO ( net-> ipv4. iptable_filter) ;
}
static unsigned int
iptable_filter_hook ( void * priv, struct sk_buff * skb, const struct nf_hook_state * state)
{ if ( state-> hook == NF_INET_LOCAL_OUT && ( skb-> len < sizeof ( struct iphdr ) || ip_hdrlen ( skb) < sizeof ( struct iphdr ) ) ) return NF_ACCEPT; return ipt_do_table ( skb, state, state-> net-> ipv4. iptable_filter) ;
}
入口在net\ipv4\netfilter\iptable_mangle.c中 mangle表主要在以下Hook点起作用: # define MANGLE_VALID_HOOKS ( ( 1 << NF_INET_PRE_ROUTING) | \ ( 1 << NF_INET_LOCAL_IN) | \ ( 1 << NF_INET_FORWARD) | \ ( 1 << NF_INET_LOCAL_OUT) | \ ( 1 << NF_INET_POST_ROUTING) ) static const struct xt_table packet_mangler = { . name = "mangle" , . valid_hooks = MANGLE_VALID_HOOKS, . me = THIS_MODULE, . af = NFPROTO_IPV4, . priority = NF_IP_PRI_MANGLE,
} ;
static struct pernet_operations iptable_mangle_net_ops = { . init = iptable_mangle_net_init, . exit = iptable_mangle_net_exit,
} ; static int __init iptable_mangle_init ( void )
{ int ret; ret = register_pernet_subsys ( & iptable_mangle_net_ops) ; if ( ret < 0 ) return ret; mangle_ops = xt_hook_link ( & packet_mangler, iptable_mangle_hook) ; if ( IS_ERR ( mangle_ops) ) { ret = PTR_ERR ( mangle_ops) ; unregister_pernet_subsys ( & iptable_mangle_net_ops) ; } return ret;
}
static int __net_init iptable_mangle_net_init ( struct net * net)
{ struct ipt_replace * repl; repl = ipt_alloc_initial_table ( & packet_mangler) ; if ( repl == NULL ) return - ENOMEM; net-> ipv4. iptable_mangle = ipt_register_table ( net, & packet_mangler, repl) ; kfree ( repl) ; return PTR_ERR_OR_ZERO ( net-> ipv4. iptable_mangle) ;
}
static unsigned int
iptable_mangle_hook ( void * priv, struct sk_buff * skb, const struct nf_hook_state * state)
{ if ( state-> hook == NF_INET_LOCAL_OUT) return ipt_mangle_out ( skb, state) ; if ( state-> hook == NF_INET_POST_ROUTING) return ipt_do_table ( skb, state, state-> net-> ipv4. iptable_mangle) ; return ipt_do_table ( skb, state, state-> net-> ipv4. iptable_mangle) ;
}
入口在net\ipv4\netfilter\iptable_nat.c中 static const struct xt_table nf_nat_ipv4_table = { . name = "nat" , . valid_hooks = ( 1 << NF_INET_PRE_ROUTING) | ( 1 << NF_INET_POST_ROUTING) | ( 1 << NF_INET_LOCAL_OUT) | ( 1 << NF_INET_LOCAL_IN) , . me = THIS_MODULE, . af = NFPROTO_IPV4,
} ;
static int __init iptable_nat_init ( void )
{ int err; err = register_pernet_subsys ( & iptable_nat_net_ops) ; if ( err < 0 ) goto err1; err = nf_register_hooks ( nf_nat_ipv4_ops, ARRAY_SIZE ( nf_nat_ipv4_ops) ) ; if ( err < 0 ) goto err2; return 0 ; err2: unregister_pernet_subsys ( & iptable_nat_net_ops) ;
err1: return err;
}
static struct pernet_operations iptable_nat_net_ops = { . init = iptable_nat_net_init, . exit = iptable_nat_net_exit,
} ; static int __net_init iptable_nat_net_init ( struct net * net)
{ struct ipt_replace * repl; repl = ipt_alloc_initial_table ( & nf_nat_ipv4_table) ; if ( repl == NULL ) return - ENOMEM; net-> ipv4. nat_table = ipt_register_table ( net, & nf_nat_ipv4_table, repl) ; kfree ( repl) ; return PTR_ERR_OR_ZERO ( net-> ipv4. nat_table) ;
}
static struct nf_hook_ops nf_nat_ipv4_ops[ ] __read_mostly = { { . hook = iptable_nat_ipv4_in, . pf = NFPROTO_IPV4, . hooknum = NF_INET_PRE_ROUTING, . priority = NF_IP_PRI_NAT_DST, } , { . hook = iptable_nat_ipv4_out, . pf = NFPROTO_IPV4, . hooknum = NF_INET_POST_ROUTING, . priority = NF_IP_PRI_NAT_SRC, } , { . hook = iptable_nat_ipv4_local_fn, . pf = NFPROTO_IPV4, . hooknum = NF_INET_LOCAL_OUT, . priority = NF_IP_PRI_NAT_DST, } , { . hook = iptable_nat_ipv4_fn, . pf = NFPROTO_IPV4, . hooknum = NF_INET_LOCAL_IN, . priority = NF_IP_PRI_NAT_SRC, } ,
} ;
入口在net\ipv4\netfilter\iptable_raw.c中 raw表主要在以下Hook点起作用: # define RAW_VALID_HOOKS ( ( 1 << NF_INET_PRE_ROUTING) | ( 1 << NF_INET_LOCAL_OUT) ) static const struct xt_table packet_raw = { . name = "raw" , . valid_hooks = RAW_VALID_HOOKS, . me = THIS_MODULE, . af = NFPROTO_IPV4, . priority = NF_IP_PRI_RAW,
} ;
static struct pernet_operations iptable_raw_net_ops = { . init = iptable_raw_net_init, . exit = iptable_raw_net_exit,
} ; static int __init iptable_raw_init ( void )
{ int ret; ret = register_pernet_subsys ( & iptable_raw_net_ops) ; if ( ret < 0 ) return ret; rawtable_ops = xt_hook_link ( & packet_raw, iptable_raw_hook) ; if ( IS_ERR ( rawtable_ops) ) { ret = PTR_ERR ( rawtable_ops) ; unregister_pernet_subsys ( & iptable_raw_net_ops) ; } return ret;
}
static int __net_init iptable_raw_net_init ( struct net * net)
{ struct ipt_replace * repl; repl = ipt_alloc_initial_table ( & packet_raw) ; if ( repl == NULL ) return - ENOMEM; net-> ipv4. iptable_raw = ipt_register_table ( net, & packet_raw, repl) ; kfree ( repl) ; return PTR_ERR_OR_ZERO ( net-> ipv4. iptable_raw) ;
}
static unsigned int
iptable_raw_hook ( void * priv, struct sk_buff * skb, const struct nf_hook_state * state)
{ if ( state-> hook == NF_INET_LOCAL_OUT && ( skb-> len < sizeof ( struct iphdr ) || ip_hdrlen ( skb) < sizeof ( struct iphdr ) ) ) return NF_ACCEPT; return ipt_do_table ( skb, state, state-> net-> ipv4. iptable_raw) ;
}