2022年第三届“网鼎杯”网络安全大赛(白虎组)部分题目附件
文章目录
- 【Misc】misc620
- 【Crypto】crypto582
- 【Crypto】crypto581
【Misc】misc620
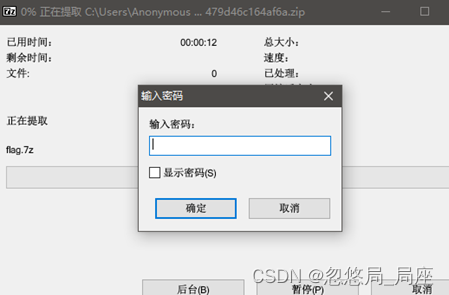
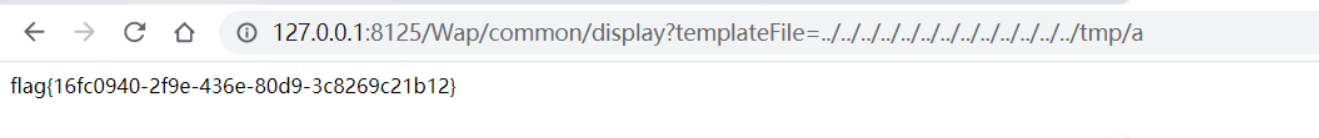
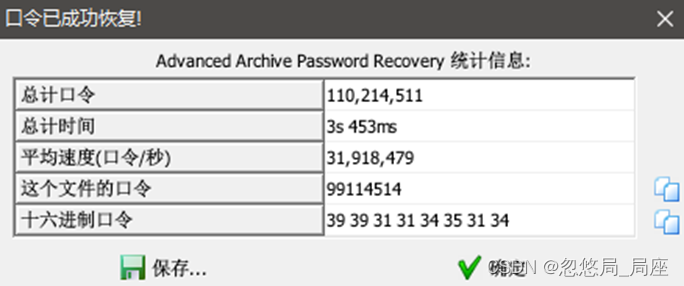
压缩包有密码,盲猜纯数字进行爆破,得到密码:
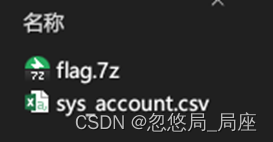
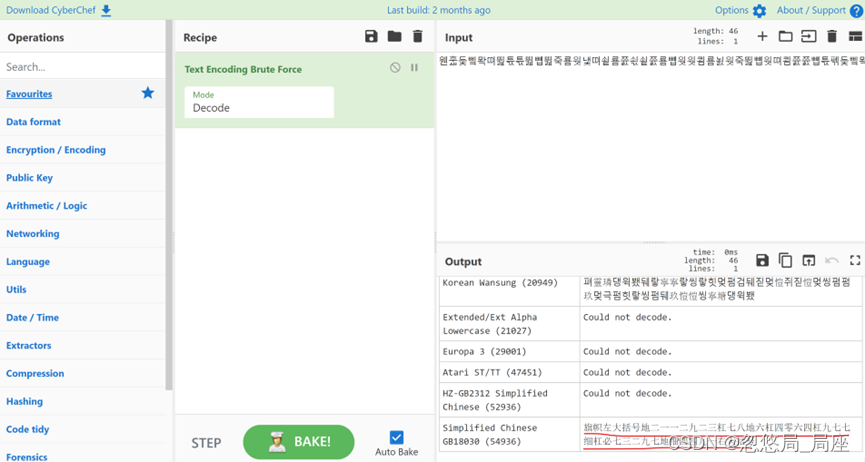
得到两个文件,flag.7z依然有密码,从csv文件中找
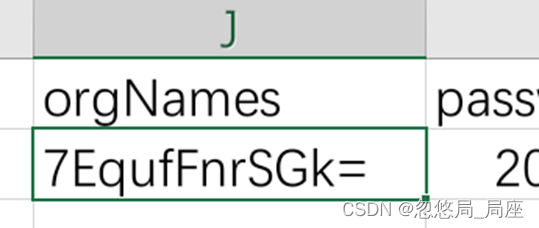
发现这有点像base编码后的
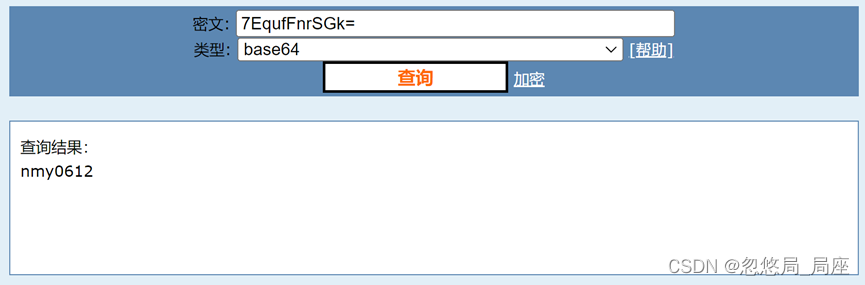
解码后得到,尝试解压缩
解压缩后得到
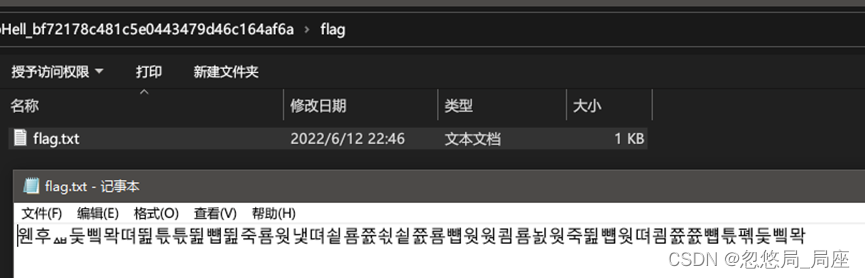
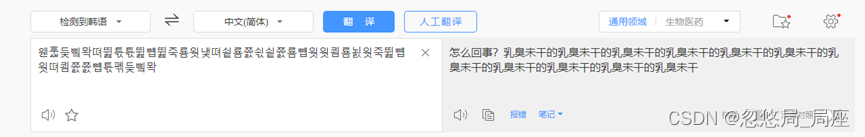
百度翻译没有结果,换工具。
flag{d2112923-78d6-4064-977c-b73297dc4491}
【Crypto】crypto582

c1 = 85139434329272123519094184286276070319638471046264384499440682030525456122476228324462769126167628121006213531153927884870307999106015430909361792093581895091445829379547633304737916675926004298753674268141399550405934376072486086468186907326396270307581239055199288888816051281495009808259009684332333344687
c2 = 104554808380721645840032269336579549039995977113982697194651690041676187039363703190743891658905715473980017457465221488358016284891528960913854895940235089108270134689312161783470000803482494370322574472422461483052403826282470850666418693908817591349159407595131136843764544166774390400827241213500917391144
c3 = 94771625845449128812081345291218973301979152577131568497740476123729158619324753128517222692750900524689049078606978317742545997482763600884362992468406577524708622046033409713416026145377740182233674890063333534646927601262333672233695863286637817471270314093720827409474178917969326556939942622112511819330
x = 78237329408351955465927092805995076909826011029371783256454322166600398149132623484679723362562600068961760410039241554232588011577854168402399895992331761353772415982560522912511879304977362225597552446397868843275129027248765252784503841114291392822052506837132093960290237335686354012448414804030938873765
y = 100442166633632319633494450595418167608036668647704883492068692098914206322465717138894302011092841820156560129280901426898815274744523998613724326647935591857728931946261379997352809249780159136988674034759483947949779535134522005905257436546335376141008113285692888482442131971935583298243412131571769294029
z = 104712661985900115750011628727270934552698948001634201257337487373976943443738367683435788889160488319624447315127992641805597631347763038111352925925686965948545739394656951753648392926627442105629724634607023721715249914976189181389720790879720452348480924301370569461741945968322303130995996793764440204452
from gmpy2 import *
e=2022m=11323698514369171934509485270187482800747906221592420578818277215318591065610272211939730721658555842676447236708557849309772868815154841226050491067608493
print(m.bit_length())
m1=(x-2022)%m
m2=(y-2022)%m
m2=m2+mcc1 = pow(m+m1,e,m*m1)
cc2 = pow(m+m2,e,m*m2)
cc3 = pow(m1+m2,e,m1*m2)
assert cc1==c1
assert cc2==c2
assert cc3==c3
xx = pow(m1+2022,m,m*m1)
yy = pow(m2+2022,m,m*m2)
zz = pow(m+2022,m1,m*m1)
assert x==xx
assert y==yy
assert z==zz
import hashlib
flag = m + m1 + m2
flag = hashlib.md5(str(flag).encode('utf-8')).hexdigest()
print("flag{"+flag+"}")
flag{27979a70ef9152b759d9340779256dc8}
【Crypto】crypto581

from crypt import crypt
from gmpy2 import *
from functools import reducedef crack_unknown_increment(states, modulus, multiplier):increment = (states[1] - states[0]*multiplier) % modulusreturn modulus, multiplier, incrementdef crack_unknown_multiplier(states, modulus):multiplier = (states[2] - states[1]) * invert(states[1] - states[0], modulus) % modulusreturn crack_unknown_increment(states, modulus, multiplier)def crack_unknown_modulus(states):diffs = [s1 - s0 for s0, s1 in zip(states, states[1:])]zeroes = [t2*t0 - t1*t1 for t0, t1, t2 in zip(diffs, diffs[1:], diffs[2:])]modulus = abs(reduce(gcd, zeroes))return crack_unknown_multiplier(states, modulus)s=[150532854791355748039117763516755705063,
335246949167877025932432065299887980427,
186623163520020374273300614035532913241,
215621842477244010690624570814660992556,
220694532805562822940506614120520015819,
17868778653481346517880312348382129728,
160572327041397126918110376968541265339]
n,a,b=crack_unknown_modulus(s)
c = 114514
e = int(2e8)mod=10 ** 10000M=matrix(Zmod(mod),[[b,a*c,1],[0,c,0],[0,0,1]])
C=matrix(Zmod(mod),[[1,1,n]])
C=C.T
s=(M^e)*C
sol = str(s[0])[1:10001]
from hashlib import md5
enc=b'UUV\x04H\x01T\x01P\x03\t\x04\t\x1fW\x00T\x02LRSPT\x1d\x02\x02^\x01N[\\R\x02\tSV\x07\x06P\x01QK'
sol_md5 = md5(sol.encode()).hexdigest()
print(len(enc))
print(len(sol_md5))
from Crypto.Util.strxor import *
print(strxor((2*sol_md5.encode())[:42],enc))
flag{650e5058-6106-4a10-a2fc-b9110d54110d}