目录
1.NSE介绍
2.NSE的使用
3.NSE分类使用
4.NSE调试功能使用
5.NSE参数的使用
6.NSE更新
7.NSE脚本分类
1.NSE介绍
NSE(Nmap Script Engine)是Nmap脚本引擎,内置了很多可以用来扫描的、针对特定任务的脚本。通过NSE可以不断拓展Nmap的扫描策略,加强Nmap的功能。
Nmap中使用 --script 参数来指定调用的脚本,并且脚本存储在Nmap安装路径下的script文件夹下,对于kali linux,存储在/usr/share/nmap/script/下面。

2.NSE的使用
使用Nmap探测web服务的title信息:nmap --script 脚本名称 目标
目前为止可以用的有589个脚本,每个脚本都有其独特的作用。
suye@ubuntu:~$ nmap --script http-title scanme.nmap.orgStarting Nmap 7.60 ( https://nmap.org ) at 2020-09-15 16:52 CST
Nmap scan report for scanme.nmap.org (45.33.32.156)
Host is up (0.19s latency).
Other addresses for scanme.nmap.org (not scanned): 2600:3c01::f03c:91ff:fe18:bb2f
Not shown: 979 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-title: Go ahead and ScanMe!
135/tcp filtered msrpc
139/tcp filtered netbios-ssn
445/tcp filtered microsoft-ds
593/tcp filtered http-rpc-epmap
1022/tcp filtered exp2
1023/tcp filtered netvenuechat
1025/tcp filtered NFS-or-IIS
1068/tcp filtered instl_bootc
1147/tcp filtered capioverlan
1433/tcp filtered ms-sql-s
4444/tcp filtered krb524
4899/tcp filtered radmin
5800/tcp filtered vnc-http
5900/tcp filtered vnc
5960/tcp filtered unknown
6129/tcp filtered unknown
6667/tcp filtered irc
9929/tcp open nping-echo
31337/tcp open EliteNmap done: 1 IP address (1 host up) scanned in 32.65 seconds
使用Nmap探测http服务的http头:nmap --script http-headers 目标
3.NSE分类使用
对于目标使用多个分类脚本进行探测,可以更快的找到目标的信息与弱点。
使用Nmap中漏洞分类脚本对目标进行探测,使用命令如下:nmap -sV --script vuln 目标
suye@ubuntu:~$ nmap -sV --script vuln 192.168.3.118Starting Nmap 7.60 ( https://nmap.org ) at 2020-09-15 17:53 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for ubuntu.lan (192.168.3.118)
Host is up (0.000087s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
Service Info: Host: UBUNTU; OS: Linux; CPE: cpe:/o:linux:linux_kernelHost script results:
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: false
| smb-vuln-regsvc-dos:
| VULNERABLE:
| Service regsvc in Microsoft Windows systems vulnerable to denial of service
| State: VULNERABLE
| The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference
| pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes
| while working on smb-enum-sessions.
|_ Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 50.91 seconds
使用Nmap中发现和版本信息分类进行探测,使用命令如下:nmap -sV --script=“version,disvcovery” 目标
使用Nmap除了exploit分类之外的其他分类进行探测,使用命令如下:nmap -sV --script=“not exploit” 目标
使用Nmap中http*的脚本,但是除了(http-brute和http-slowlors),使用命令如下:nmap -sV --script “(http*) and not (http-brute and http-slowlors)” 目标
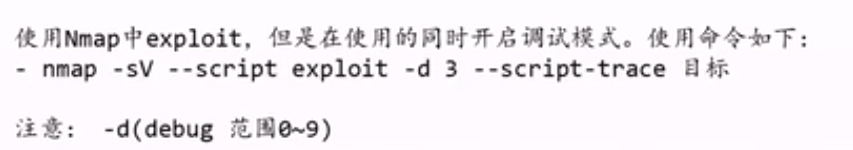
4.NSE调试功能使用
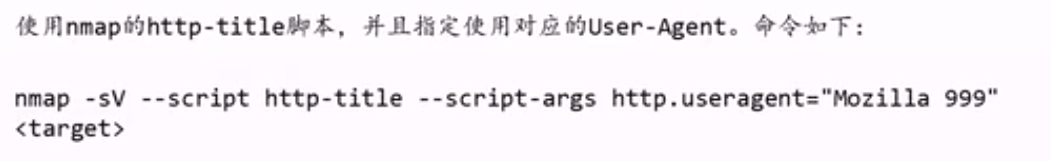
5.NSE参数的使用
6.NSE更新

7.NSE脚本分类




