一、双机热备简介
1.1 VRRP概念
VRRP(Virtual Router Reduancy Protocol)是一种容错协议,它保证当主机的默认网关及下一跳路由器出现故障时,由备份路由器自动代替出现故障的路由器完成报文转发任务,从而保持网络通信的连续性和可靠性。
在FW上配置VRRP时,将两台FW上编号相同的接口加入一个VRRP备份组。一个VRRP备份组相当于一台虚拟路由设备,拥有虚拟IP地址和虚拟MAC地址。网络内的主机将网关设置为VRRP备份组的虚拟IP地址。
如下图所示R1和R2在接口下配置VRRP,选举出R1是主设备,R1发送224.0.0.18的组播报文通告自己存活,并发送免费ARP给接入交换机刷新MAC转发表上虚拟MAC对应的端口。当R1配置VRRP的接口故障后,R2因为定时器超时后仍未收到R1的组播报文将状态切换为主。
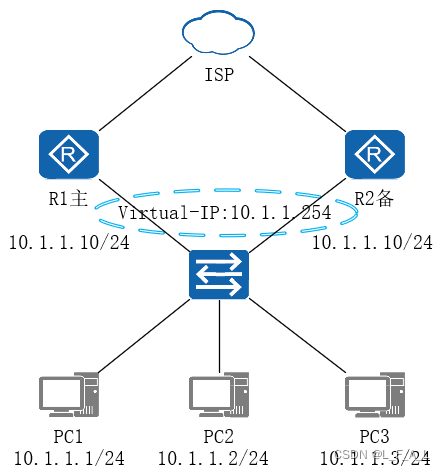
在华为交换机或路由器上,VRRP的状态是由可以配置的优先级大小决定的,同一个VRRP备份组中,优先级最大的设备状态为Master,其他设备的状态为Backup。但是在FW的VRRP备份组状态则不是由VRRP优先级大小决定的,并且是不可配置的固定为120。
1.2VGMP
为了解决单独配置VRRP可能遇到状态不一致问题,华为在VRRP的基础上开发了VGMP(VRRP Group Management Protocol),主要功能是集中管理和监控VRRP备份组。
在防火墙上接口无故障时,接口下的VRRP备份组状态由VGMP组的状态决定。
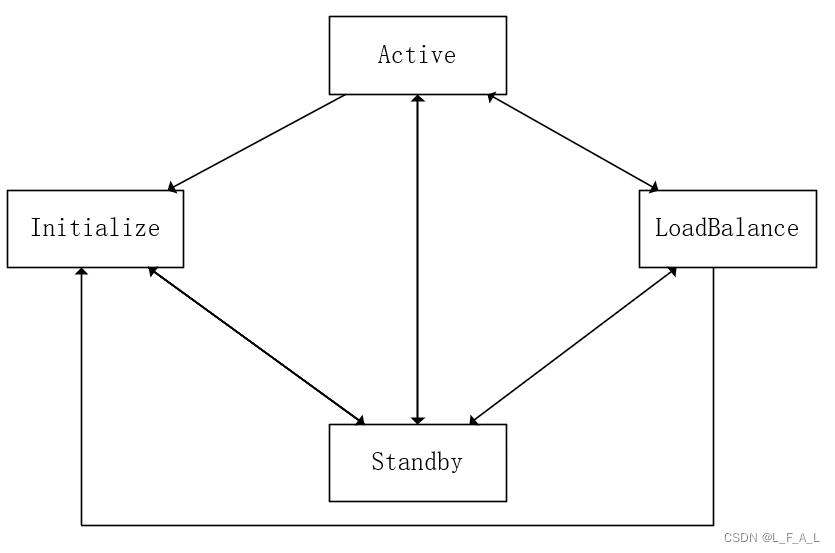
· 当VGMP组状态为active时,VRRP备份组的状态都是Master。
· 当VGMP组状态为standby时,VRRP备份组的状态都是Backup。
· 当VGMP组状态为load-balance时,VRRP备份组状态由VRRP备份组配置决定。
两台防火墙之间的VGMP状态主备切换的具体交互过程分以下三种情况:
①因接口或者链路故障引起的切换:
这一类故障发生时,主设备通过VGMP报文将状态信息和本端优先级立即发送到备设备,备设备比较报文的优先级和本机优先级,如果满足切换条件立即切换,瞬间完成业务流量的切换。
②因整机或心跳链路故障引起的切换:
这种故障发生时,由于设备无法发送状态通知备机,因此只能通过备机检测到心跳报文超时后才能发现故障,因此切换时间为5个心跳报文周期。
③抢占流程:
故障恢复后的切换流程,由于设备处于正常转发状态,等主机故障恢复后再切换回去,因此基本不会影响业务。
如下图所示组网FW上下行接口工作在三层,下行接口组成VRRP备份组,FW1为主设备,FW2为备设备。
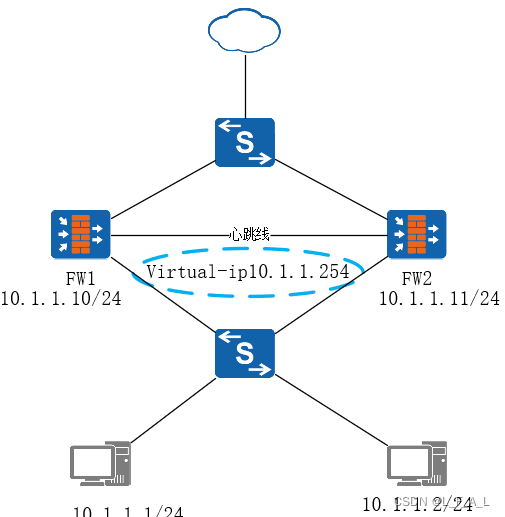
两台设备没有任何故障,所以VGMP组优先级相等,VGMP组状态都为load-balance。所以VRRP组的运行状态由配置决定,FW1为主设备则VRRP备份组状态为Master,FW2的VRRP备份组状态为Backup。日志如下:
[FW1]hrp enable
HRP_S[FW1]
Feb 5 2023 17:03:26-08:00 FW1 HRPI/1/CORE_STATE:1.3.6.1.4.1.2011.6.122.51.2.2
.1 The HRP core state changed due to "Unknown".(old_state=initial,new_state=
abnormal(standby),local_priority=45000,peer_priority=unknown) # 状态从Initial变为standby,本端优先级正常,对端未知
Feb 5 2023 17:03:26-08:00 FW1 HRPI/1/CORE_STATE:1.3.6.1.4.1.2011.6.122.51.2.2.
1 The HRP core state changed due to "Unknown".(old_state=abnormal(standby),
new_state=normal,local_priority=45000,peer_priority=45000)
# 状态从standby变为normal及为load-balance,两端优先级正常且相同
然后查看VRRP备份组状态各为设置的状态
#FW1:
HRP_M[FW1]display vrrp brief
2023-02-05 17:14:28.450 -08:00
Total:2 Master:2 Backup:0 Non-active:0
VRID State Interface Type Virtual IP
----------------------------------------------------------------
1 Master GE0/0/1 Vgmp 10.1.1.254
2 Master GE0/0/2 Vgmp 202.100.1.254
#FW2:
HRP_S[FW2]display vrrp brief
2023-02-04 17:10:29.870 +08:00
Total:2 Master:0 Backup:2 Non-active:0
VRID State Interface Type Virtual IP
----------------------------------------------------------------
1 Backup GE0/0/1 Vgmp 10.1.1.254
2 Backup GE0/0/2 Vgmp 202.100.1.254 将上行接口模拟故障
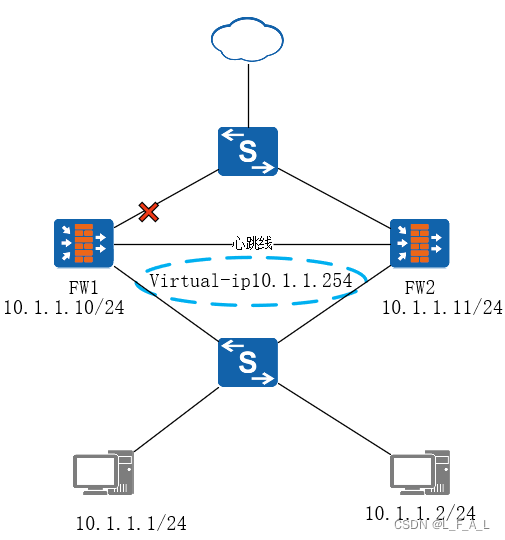
Feb 5 2023 17:17:09-08:00 FW1 %%01PHY/4/STATUSDOWN(l)[28]:GigabitEthernet0/0/1
changed status to down.
Feb 5 2023 17:17:09-08:00 FW1 %%01IFNET/4/LINK_STATE(l)[29]:The line protocolIP on the interface GigabitEthernet0/0/1 has entered the DOWN state.
# 接口变为Down
Feb 5 2023 17:17:09-08:00 FW1 %%01HRPI/4/VRRP_PEER_DOWN(l)[30]:The VRRP link
went down. (Interface=GigabitEthernet0/0/1, VrId=1, InetType=VRRP4).
Feb 5 2023 17:17:09-08:00 FW1 HRPI/1/CORE_STATE:1.3.6.1.4.1.2011.6.122.51.2.2.
1 The HRP core state changed due to "VRRP change to Down".(old_state=
normal,new_state=abnormal(standby),local_priority=44998,peer_priority=45000)
# 状态变从load-balance变为standby,优先级减少2
Feb 5 2023 17:17:09-08:00 FW1 %%01HRPI/4/PRIORITY_CHANGE(l)[31]:The priority of the local VGMP group changed.(change_reason="VRRP change to down.",local_old_priority=45000, local_new_priority=44998)
Feb 5 2023 17:17:09-08:00 FW1 %%01HRPI/4/CORE_STATE(l)[32]:The HRP core state changed due to "VRRP change to Down".(old_state=normal, new_state=abnormal(standby), local_priority=44998, peer_priority=45000)Feb 4 2023 17:11:44+08:00 FW2 HRPI/1/CORE_STATE:1.3.6.1.4.1.2011.6.122.51.2.2.1 The HRP core state changed due to "Unknown".(old_state=normal,new_state=abnormal(active),local_priority=45000,peer_priority=44998)
Feb 4 2023 17:11:44+08:00 FW2 %%01HRPI/4/CORE_STATE(l)[31]:The HRP core state changed due to "Unknown".(old_state=normal, new_state=abnormal(active), local_priority=45000, peer_priority=44998)
# 而FW2状态从loadbalance变为active1.3双机热备协议架构
VRRP负责对链路状态和流量的引导,VGMP负责统一监控管理VRRP的备份组。HRP负责对双机之间的关键配置命令和连接状态信息进行备份。
二、主备备份双机热备
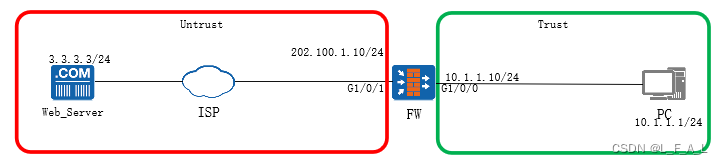
2.1拓扑
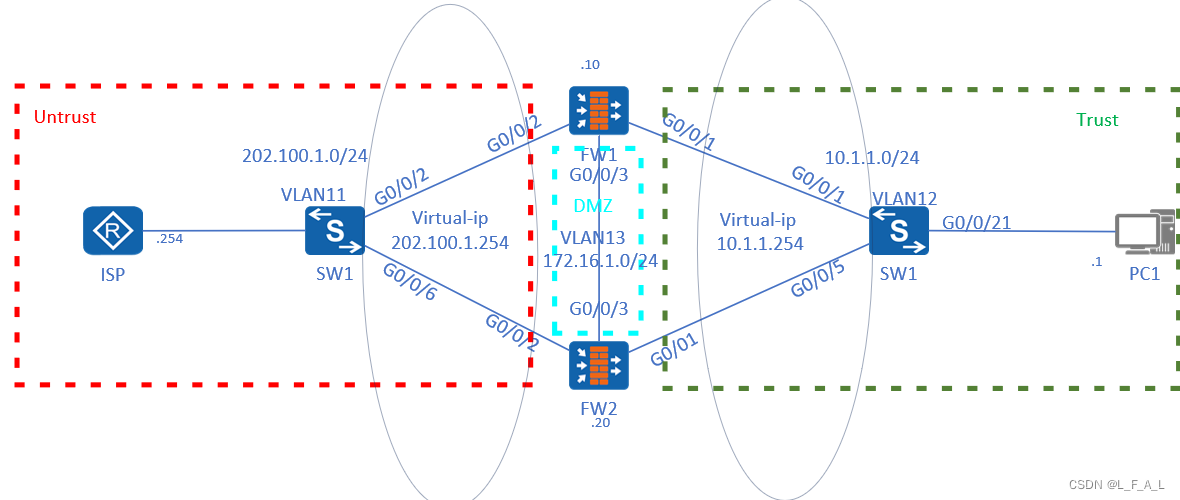
FW1和FW2配置双机热备形成基于VRRP的主备备份,FW1为主设备,FW2为备设备。当FW1发生故障时,FW2切换为主设备。
2.2 设备配置
SW1:
[SW1]vlan batch 10 to 20
[SW1]interface GigabitEthernet 0/0/1
[SW1-GigabitEthernet0/0/1]port link-type access
[SW1-GigabitEthernet0/0/1]port default vlan 12
[SW1-GigabitEthernet0/0/1]interface GigabitEthernet 0/0/5
[SW1-GigabitEthernet0/0/5]port link-type access
[SW1-GigabitEthernet0/0/5]port default vlan 12
[SW1-GigabitEthernet0/0/5]interface GigabitEthernet 0/0/9
[SW1-GigabitEthernet0/0/9]port link-type access
[SW1-GigabitEthernet0/0/9]port default vlan 12
[SW1-GigabitEthernet0/0/5]interface GigabitEthernet 0/0/2
[SW1-GigabitEthernet0/0/2]port link-type access
[SW1-GigabitEthernet0/0/2]port default vlan 11
[SW1-GigabitEthernet0/0/2]interface GigabitEthernet 0/0/6
[SW1-GigabitEthernet0/0/6]port link-type access
[SW1-GigabitEthernet0/0/6]port default vlan 11
[SW1-GigabitEthernet0/0/9]interface GigabitEthernet 0/0/16
[SW1-GigabitEthernet0/0/16]port link-type access
[SW1-GigabitEthernet0/0/16]port default vlan 11
[SW1-GigabitEthernet0/0/16]interface GigabitEthernet 0/0/3
[SW1-GigabitEthernet0/0/3]port link-type access
[SW1-GigabitEthernet0/0/3]port default vlan 13
[SW1-GigabitEthernet0/0/3]interface GigabitEthernet 0/0/7
[SW1-GigabitEthernet0/0/7]port link-type access
[SW1-GigabitEthernet0/0/7]port default vlan 13
ISP:
#配置IP地址
[IP-Rack01-ISP]int e0/0/1
[IP-Rack01-ISP-Ethernet0/0/1]undo portswitch
[IP-Rack01-ISP-Ethernet0/0/1]ip address 202.100.1.1 24
#配置ACL
[IP-Rack01-ISP]acl number 2000
[IP-Rack01-ISP-acl-basic-2000]rule 5 permit
#配置Easy-IP
[IP-Rack01-ISP-Ethernet0/0/3]nat outbound 2000
[IP-Rack01-ISP-Ethernet0/0/3]dis this
[V200R010C10SPC700]
#
interface Ethernet0/0/3undo portswitchip address 10.8.202.182 255.255.255.0nat outbound 2000
#
returnFW1:
#IP地址配置
[FW1]interface GigabitEthernet 0/0/1
[FW1-GigabitEthernet0/0/1]ip address 10.1.1.10 24
[FW1-GigabitEthernet0/0/1]service-manage ping permit
[FW1-GigabitEthernet0/0/1]interface GigabitEthernet 0/0/2
[FW1-GigabitEthernet0/0/2]ip address 202.100.1.10 24
[FW1-GigabitEthernet0/0/2]service-manage ping permit
[FW1-GigabitEthernet0/0/2]interface GigabitEthernet 0/0/3
[FW1-GigabitEthernet0/0/3]ip address 172.16.1.10 24
#安全区域划分
[FW1]firewall zone trust
[FW1-zone-trust]add interface g0/0/1
[FW1-zone-trust]firewall zone untrust
[FW1-zone-untrust]add interface g0/0/2
[FW1-zone-untrust]firewall zone dmz
[FW1-zone-dmz]add interface g0/0/3
#配置静态默认路由指向ISP
[FW1]ip route-static 0.0.0.0 0 202.100.1.1
#配置VRRP备份组
[FW1-GigabitEthernet0/0/1]vrrp vrid 1 virtual-ip 10.1.1.254 active
[FW1-GigabitEthernet0/0/1]vrrp virtual-mac enable
[FW1-GigabitEthernet0/0/2]vrrp vrid 2 virtual-ip 202.100.1.254 active
[FW1-GigabitEthernet0/0/2]vrrp virtual-mac enable
#配置心跳接口
[FW1]hrp interface GigabitEthernet 0/0/3 remote 172.16.1.20
#开启HRP
[FW1]hrp enable
FW2:
#IP地址配置
[FW2]interface g0/0/1
[FW2-GigabitEthernet0/0/1]ip address 10.1.1.20 24
[FW2-GigabitEthernet0/0/1]service-manage ping permit
[FW2-GigabitEthernet0/0/1]interface g0/0/2
[FW2-GigabitEthernet0/0/2]ip address 202.100.1.20 24
[FW2-GigabitEthernet0/0/2]service-manage ping permit
[FW2-GigabitEthernet0/0/2]interface g0/0/3
[FW2-GigabitEthernet0/0/3]ip address 172.16.1.20 24
#安全区域划分
[FW2-GigabitEthernet0/0/3]firewall zone trust
[FW2-zone-trust]add interface g0/0/1
[FW2-zone-trust]firewall zone untrust
[FW2-zone-untrust]add interface g0/0/2
[FW2-zone-untrust]firewall zone dmz
[FW2-zone-dmz]add interface g0/0/3
#配置静态默认路由指向ISP
[FW2]ip route-static 0.0.0.0 0 202.100.1.1
#配置VRRP备份组
[FW2-GigabitEthernet0/0/1]vrrp vrid 1 virtual-ip 10.1.1.254 standby
[FW2-GigabitEthernet0/0/1]vrrp virtual-mac enable
[FW2-GigabitEthernet0/0/2]vrrp vrid 2 virtual-ip 202.100.1.254 standby
[FW2-GigabitEthernet0/0/2]vrrp virtual-mac enable
#配置心跳接口
[FW2]hrp interface GigabitEthernet 0/0/3 remote 172.16.1.10
#启用HRP
[FW2]hrp enablePC1:
网关指向虚拟IP地址

FW1&FW2:
#安全策略放行内网PC访问外网
HRP_M[FW1]security-policy (+B)
HRP_M[FW1-policy-security]rule name PC1_Internet (+B)
HRP_M[FW1-policy-security-rule-PC1_Internet]source-zone trust (+B)
HRP_M[FW1-policy-security-rule-PC1_Internet]destination-zone untrust (+B)
HRP_M[FW1-policy-security-rule-PC1_Internet]source-address 10.1.1.0 24 (+B)
HRP_M[FW1-policy-security-rule-PC1_Internet]action permit
#配置源NAT
HRP_M[FW1]nat-policy (+B)
HRP_M[FW1-policy-nat]rule name Easy_Ip (+B)
HRP_M[FW1-policy-nat-rule-Easy_Ip]source-zone trust (+B)
HRP_M[FW1-policy-nat-rule-Easy_Ip]destination-zone untrust (+B)
HRP_M[FW1-policy-nat-rule-Easy_Ip]source-address 10.1.1.0 24 (+B)
HRP_M[FW1-policy-nat-rule-Easy_Ip]action source-nat easy-ip (+B)#FW1:
HRP_M[FW1]display vrrp
2023-02-01 09:19:20.560 +08:00GigabitEthernet0/0/1 | Virtual Router 1State : MasterVirtual IP : 10.1.1.254Master IP : 10.1.1.10PriorityRun : 120PriorityConfig : 100MasterPriority : 120Preempt : YES Delay Time : 0 sTimerRun : 60 sTimerConfig : 60 sAuth type : NONEVirtual MAC : 0000-5e00-0101Check TTL : YESConfig type : vgmp-vrrpBackup-forward : disabledCreate time : 2023-02-01 08:53:53 UTC+08:00Last change time : 2023-02-01 08:58:37 UTC+08:00GigabitEthernet0/0/2 | Virtual Router 2State : MasterVirtual IP : 202.100.1.254Master IP : 202.100.1.10PriorityRun : 120PriorityConfig : 100MasterPriority : 120 Preempt : YES Delay Time : 0 sTimerRun : 60 sTimerConfig : 60 sAuth type : NONEVirtual MAC : 0000-5e00-0102Check TTL : YESConfig type : vgmp-vrrpBackup-forward : disabledCreate time : 2023-02-01 08:58:22 UTC+08:00Last change time : 2023-02-01 08:58:37 UTC+08:00
#FW2:
HRP_S[FW2]display vrrp
2023-02-01 09:20:34.360 +08:00GigabitEthernet0/0/1 | Virtual Router 1State : BackupVirtual IP : 10.1.1.254Master IP : 10.1.1.10PriorityRun : 120PriorityConfig : 100MasterPriority : 120Preempt : YES Delay Time : 0 sTimerRun : 60 sTimerConfig : 60 sAuth type : NONEVirtual MAC : 0000-5e00-0101Check TTL : YESConfig type : vgmp-vrrpBackup-forward : disabledCreate time : 2023-02-01 08:55:35 UTC+08:00Last change time : 2023-02-01 08:55:35 UTC+08:00GigabitEthernet0/0/2 | Virtual Router 2State : BackupVirtual IP : 202.100.1.254Master IP : 202.100.1.10PriorityRun : 120PriorityConfig : 100MasterPriority : 120 Preempt : YES Delay Time : 0 sTimerRun : 60 sTimerConfig : 60 sAuth type : NONEVirtual MAC : 0000-5e00-0102Check TTL : YESConfig type : vgmp-vrrpBackup-forward : disabledCreate time : 2023-02-01 08:56:16 UTC+08:00Last change time : 2023-02-01 08:56:16 UTC+08:00查看HRP状态
#FW1:
HRP_M[FW1]display hrp state verbose
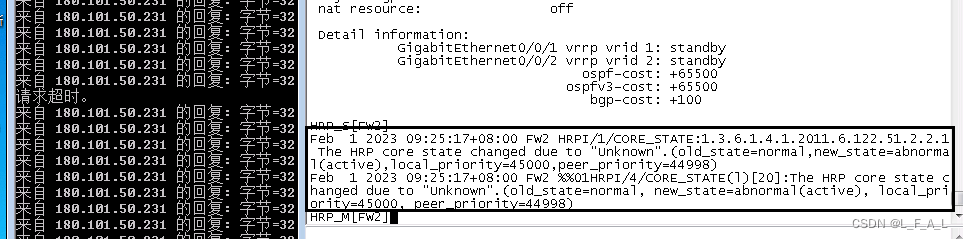
2023-02-01 09:21:41.940 +08:00Role: active, peer: standbyRunning priority: 45000, peer: 45000 Backup channel usage: 0.00%Stable time: 0 days, 0 hours, 23 minutesLast state change information: 2023-02-01 8:58:37 HRP core state changed, old_state = abnormal(standby), new_state = normal, local_priority = 45000, peer_priority = 45000.Configuration:hello interval: 1000mspreempt: 60smirror configuration: offmirror session: offtrack trunk member: onauto-sync configuration: onauto-sync connection-status: onadjust ospf-cost: onadjust ospfv3-cost: onadjust bgp-cost: onnat resource: offDetail information:GigabitEthernet0/0/1 vrrp vrid 1: activeGigabitEthernet0/0/2 vrrp vrid 2: activeospf-cost: +0ospfv3-cost: +0bgp-cost: +0#FW2:
HRP_S[FW2]display hrp state verbose
2023-02-01 09:22:28.440 +08:00Role: standby, peer: activeRunning priority: 45000, peer: 45000Backup channel usage: 0.00%Stable time: 0 days, 0 hours, 24 minutesLast state change information: 2023-02-01 8:58:22 HRP link changes to up.Configuration:hello interval: 1000mspreempt: 60smirror configuration: offmirror session: offtrack trunk member: onauto-sync configuration: onauto-sync connection-status: onadjust ospf-cost: onadjust ospfv3-cost: onadjust bgp-cost: onnat resource: offDetail information:GigabitEthernet0/0/1 vrrp vrid 1: standbyGigabitEthernet0/0/2 vrrp vrid 2: standbyospf-cost: +65500ospfv3-cost: +65500bgp-cost: +100
2.3 现象测试
主备切换测试:
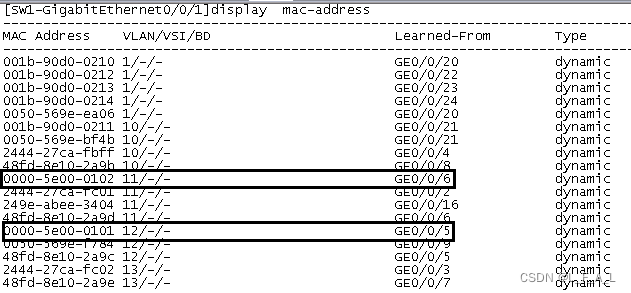
1.在PC1上执行"ping www.baidu.com -t",查看交换机的MAC地址表,虚拟MAC和主设备的接口绑定在一起。然后shut down交换机SW1的G0/0/1口。

[SW1-GigabitEthernet0/0/7]int g0/0/1
[SW1-GigabitEthernet0/0/1]shutdown 2.FW2备设备快速切换