一 . 用netstat指令查看是端口占用情况
查看所有端口的占用情况
C:\Users\Administrator>netstat -ano
活动连接协议 本地地址 外部地址 状态 PIDTCP 0.0.0.0:21 0.0.0.0:0 LISTENING 2228TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 4TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 740TCP 0.0.0.0:389 0.0.0.0:0 LISTENING 3428TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4TCP 0.0.0.0:902 0.0.0.0:0 LISTENING 2496TCP 0.0.0.0:912 0.0.0.0:0 LISTENING 2496TCP 0.0.0.0:1689 0.0.0.0:0 LISTENING 3428TCP 0.0.0.0:3306 0.0.0.0:0 LISTENING 2612TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING 856TCP 0.0.0.0:4444 0.0.0.0:0 LISTENING 3428TCP 0.0.0.0:5985 0.0.0.0:0 LISTENING 4TCP 0.0.0.0:8085 0.0.0.0:0 LISTENING 8044TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING 4TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 476TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 1012TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 848TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 1688TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING 2004TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING 600TCP 0.0.0.0:49670 0.0.0.0:0 LISTENING 584TCP 0.0.0.0:54021 0.0.0.0:0 LISTENING 3428TCP 10.159.64.24:139 0.0.0.0:0 LISTENING 4TCP 10.159.64.24:3389 10.159.44.100:45306 ESTABLISHED 856TCP 10.159.64.24:54021 10.159.64.24:60248 ESTABLISHED 3428TCP 10.159.64.24:60248 10.159.64.24:54021 ESTABLISHED 3428TCP 127.0.0.1:7085 0.0.0.0:0 LISTENING 8044TCP 127.0.0.1:54008 127.0.0.1:54009 ESTABLISHED 3428TCP 127.0.0.1:54009 127.0.0.1:54008 ESTABLISHED 3428TCP 127.0.0.1:54011 127.0.0.1:54012 ESTABLISHED 3428TCP 127.0.0.1:54012 127.0.0.1:54011 ESTABLISHED 3428TCP 127.0.0.1:54013 127.0.0.1:54014 ESTABLISHED 3428TCP 127.0.0.1:54014 127.0.0.1:54013 ESTABLISHED 3428TCP 127.0.0.1:54016 127.0.0.1:54017 ESTABLISHED 3428TCP 127.0.0.1:54017 127.0.0.1:54016 ESTABLISHED 3428TCP 127.0.0.1:54018 127.0.0.1:54019 ESTABLISHED 3428TCP 127.0.0.1:54019 127.0.0.1:54018 ESTABLISHED 3428TCP 127.0.0.1:54025 127.0.0.1:54026 ESTABLISHED 8044TCP 127.0.0.1:54026 127.0.0.1:54025 ESTABLISHED 8044TCP 192.168.58.1:139 0.0.0.0:0 LISTENING 4TCP 192.168.195.1:139 0.0.0.0:0 LISTENING 4TCP [::]:21 [::]:0 LISTENING 2228TCP [::]:80 [::]:0 LISTENING 4TCP [::]:135 [::]:0 LISTENING 740TCP [::]:389 [::]:0 LISTENING 3428TCP [::]:445 [::]:0 LISTENING 4TCP [::]:1689 [::]:0 LISTENING 3428TCP [::]:3306 [::]:0 LISTENING 2612TCP [::]:3389 [::]:0 LISTENING 856TCP [::]:4444 [::]:0 LISTENING 3428TCP [::]:5985 [::]:0 LISTENING 4TCP [::]:8085 [::]:0 LISTENING 8044TCP [::]:47001 [::]:0 LISTENING 4TCP [::]:49664 [::]:0 LISTENING 476TCP [::]:49665 [::]:0 LISTENING 1012TCP [::]:49666 [::]:0 LISTENING 848TCP [::]:49667 [::]:0 LISTENING 1688TCP [::]:49668 [::]:0 LISTENING 2004TCP [::]:49669 [::]:0 LISTENING 600TCP [::]:49670 [::]:0 LISTENING 584TCP [::]:54021 [::]:0 LISTENING 3428UDP 0.0.0.0:123 *:* 452UDP 0.0.0.0:500 *:* 848UDP 0.0.0.0:3389 *:* 856UDP 0.0.0.0:4500 *:* 848UDP 0.0.0.0:5050 *:* 452UDP 0.0.0.0:5353 *:* 1120UDP 0.0.0.0:5355 *:* 1120UDP 10.159.64.24:137 *:* 4UDP 10.159.64.24:138 *:* 4UDP 10.159.64.24:1900 *:* 716UDP 10.159.64.24:52841 *:* 716UDP 127.0.0.1:1900 *:* 716UDP 127.0.0.1:52844 *:* 716UDP 192.168.58.1:137 *:* 4UDP 192.168.58.1:138 *:* 4UDP 192.168.58.1:1900 *:* 716UDP 192.168.58.1:52843 *:* 716UDP 192.168.195.1:137 *:* 4UDP 192.168.195.1:138 *:* 4UDP 192.168.195.1:1900 *:* 716UDP 192.168.195.1:52842 *:* 716UDP [::]:123 *:* 452UDP [::]:500 *:* 848UDP [::]:3389 *:* 856UDP [::]:4500 *:* 848UDP [::]:5353 *:* 1120UDP [::]:5355 *:* 1120UDP [::1]:1900 *:* 716UDP [::1]:52840 *:* 716UDP [fe80::557e:e741:6082:9989%4]:546 *:* 1012UDP [fe80::557e:e741:6082:9989%4]:1900 *:* 716UDP [fe80::557e:e741:6082:9989%4]:52839 *:* 716UDP [fe80::e04c:f5c2:4a:3289%3]:1900 *:* 716UDP [fe80::e04c:f5c2:4a:3289%3]:52838 *:* 716
命令格式:netstat [options]
-a表示显示所有活动的TCP连接以及计算机监听的TCP和UDP端口。
-n表示只以数字形式显示所有活动的TCP连接的地址和端口号。
-o表示显示活动的TCP连接并包括每个连接的进程ID(PID)。
查看特定端口的占用情况(以80端口为例)
C:\Users\Administrator>netstat -aon|findstr 80TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 4TCP 0.0.0.0:8085 0.0.0.0:0 LISTENING 8044TCP 127.0.0.1:7085 0.0.0.0:0 LISTENING 8044TCP 127.0.0.1:54025 127.0.0.1:54026 ESTABLISHED 8044TCP 127.0.0.1:54026 127.0.0.1:54025 ESTABLISHED 8044TCP [::]:80 [::]:0 LISTENING 4TCP [::]:8085 [::]:0 LISTENING 8044UDP [fe80::557e:e741:6082:9989%4]:1900 *:* 716UDP [fe80::557e:e741:6082:9989%4]:52839 *:* 716UDP [fe80::e04c:f5c2:4a:3289%3]:1900 *:* 716UDP [fe80::e04c:f5c2:4a:3289%3]:52838 *:* 716
在第2列可以找到,占用80端口的进程号为4。
二. 用tasklist指令查找进程号对应的名称
查找所有进程号对应的名称
C:\Users\Administrator>tasklist
映像名称 PID 会话名 会话# 内存使用
========================= ======== ================ =========== ============
System Idle Process 0 Services 0 4 K
System 4 Services 0 140 K
smss.exe 260 Services 0 1,280 K
csrss.exe 368 Services 0 4,344 K
csrss.exe 456 Console 1 4,096 K
wininit.exe 476 Services 0 5,900 K
winlogon.exe 512 Console 1 8,456 K
services.exe 584 Services 0 13,848 K
lsass.exe 600 Services 0 16,572 K
svchost.exe 676 Services 0 26,880 K
svchost.exe 740 Services 0 24,716 K
svchost.exe 848 Services 0 140,064 K
svchost.exe 856 Services 0 50,948 K
svchost.exe 912 Services 0 32,872 K
dwm.exe 932 Console 1 29,708 K
LogonUI.exe 940 Console 1 41,764 K
svchost.exe 1012 Services 0 30,416 K
svchost.exe 452 Services 0 25,796 K
WUDFHost.exe 1032 Services 0 8,284 K
svchost.exe 1052 Services 0 18,176 K
svchost.exe 1120 Services 0 23,008 K
svchost.exe 1128 Services 0 7,252 K
svchost.exe 2004 Services 0 7,288 K
spoolsv.exe 1688 Services 0 16,612 K
svchost.exe 2144 Services 0 25,436 K
svchost.exe 2152 Services 0 10,592 K
svchost.exe 2184 Services 0 8,488 K
svchost.exe 2192 Services 0 19,312 K
svchost.exe 2228 Services 0 11,568 K
vmnat.exe 2252 Services 0 6,956 K
svchost.exe 2260 Services 0 11,440 K
MsMpEng.exe 2352 Services 0 154,116 K
vmnetdhcp.exe 2380 Services 0 11,216 K
vmware-usbarbitrator64.ex 2444 Services 0 10,000 K
vmware-authd.exe 2496 Services 0 13,440 K
mysqld.exe 2612 Services 0 26,688 K
csrss.exe 3864 RDP-Tcp#6 2 12,792 K
winlogon.exe 3924 RDP-Tcp#6 2 8,400 K
dwm.exe 3988 RDP-Tcp#6 2 128,360 K
rdpclip.exe 1220 RDP-Tcp#6 2 20,332 K
RuntimeBroker.exe 3612 RDP-Tcp#6 2 34,632 K
sihost.exe 3764 RDP-Tcp#6 2 22,676 K
svchost.exe 3080 RDP-Tcp#6 2 19,868 K
taskhostw.exe 1752 RDP-Tcp#6 2 20,804 K
explorer.exe 4024 RDP-Tcp#6 2 523,136 K
ChsIME.exe 1936 RDP-Tcp#6 2 9,064 K
ShellExperienceHost.exe 4308 RDP-Tcp#6 2 83,412 K
SearchUI.exe 4392 RDP-Tcp#6 2 47,184 K
ServerManager.exe 4700 RDP-Tcp#6 2 99,764 K
vmware-tray.exe 4936 RDP-Tcp#6 2 12,512 K
msdtc.exe 4792 Services 0 9,692 K
plmdeployer_prd_simple.ex 5008 RDP-Tcp#6 2 103,076 K
plmdeployer_prd_simple.ex 3776 RDP-Tcp#6 2 92,332 K
notepad.exe 1184 RDP-Tcp#6 2 14,124 K
dllhost.exe 3264 RDP-Tcp#6 2 9,140 K
plmdeployer_prd_simple.ex 2112 RDP-Tcp#6 2 93,160 K
svchost.exe 716 Services 0 6,892 K
mmc.exe 376 RDP-Tcp#6 2 11,144 K
mmc.exe 800 RDP-Tcp#6 2 17,328 K
taskhostw.exe 4352 RDP-Tcp#6 2 19,148 K
notepad.exe 724 RDP-Tcp#6 2 14,080 K
wordpad.exe 7576 RDP-Tcp#6 2 36,588 K
java.exe 3428 RDP-Tcp#6 2 372,520 K
cmd.exe 8088 RDP-Tcp#6 2 3,212 K
conhost.exe 3520 RDP-Tcp#6 2 15,196 K
java.exe 8044 RDP-Tcp#6 2 561,224 K
wordpad.exe 5724 RDP-Tcp#6 2 33,536 K
notepad.exe 5688 RDP-Tcp#6 2 15,676 K
git-bash.exe 4932 RDP-Tcp#6 2 5,164 K
mintty.exe 5348 RDP-Tcp#6 2 19,216 K
conhost.exe 8632 RDP-Tcp#6 2 11,716 K
bash.exe 9108 RDP-Tcp#6 2 9,644 K
git-bash.exe 5148 RDP-Tcp#6 2 5,104 K
mintty.exe 9084 RDP-Tcp#6 2 18,784 K
conhost.exe 8488 RDP-Tcp#6 2 11,724 K
bash.exe 4408 RDP-Tcp#6 2 9,588 K
git-bash.exe 756 RDP-Tcp#6 2 5,124 K
mintty.exe 2284 RDP-Tcp#6 2 18,220 K
conhost.exe 980 RDP-Tcp#6 2 11,676 K
bash.exe 5892 RDP-Tcp#6 2 9,580 K
notepad.exe 8272 RDP-Tcp#6 2 14,852 K
notepad.exe 3464 RDP-Tcp#6 2 14,436 K
cmd.exe 3636 RDP-Tcp#6 2 2,900 K
conhost.exe 8756 RDP-Tcp#6 2 14,972 K
notepad.exe 9036 RDP-Tcp#6 2 15,964 K
mmc.exe 7244 RDP-Tcp#6 2 13,036 K
ApplicationFrameHost.exe 5996 RDP-Tcp#6 2 24,204 K
SystemSettings.exe 6804 RDP-Tcp#6 2 57,788 K
MpCmdRun.exe 5948 Services 0 8,248 K
svchost.exe 5572 Services 0 6,228 K
tasklist.exe 6904 RDP-Tcp#6 2 8,080 K
WmiPrvSE.exe 3084 Services 0 8,688 K
查找所有特定进程号对应的名称(以进程4为例)
C:\Users\Administrator>tasklist|findstr 4
System Idle Process 0 Services 0 4 K
System 4 Services 0 140 K
csrss.exe 368 Services 0 4,340 K
csrss.exe 456 Console 1 4,096 K
wininit.exe 476 Services 0 5,900 K
winlogon.exe 512 Console 1 8,456 K
services.exe 584 Services 0 13,848 K
svchost.exe 740 Services 0 24,716 K
svchost.exe 848 Services 0 138,932 K
svchost.exe 856 Services 0 51,140 K
LogonUI.exe 940 Console 1 41,764 K
svchost.exe 1012 Services 0 30,456 K
svchost.exe 452 Services 0 25,796 K
WUDFHost.exe 1032 Services 0 8,284 K
svchost.exe 2004 Services 0 7,288 K
svchost.exe 2144 Services 0 25,432 K
svchost.exe 2184 Services 0 8,488 K
svchost.exe 2192 Services 0 19,304 K
svchost.exe 2260 Services 0 11,440 K
MsMpEng.exe 2352 Services 0 154,988 K
vmware-usbarbitrator64.ex 2444 Services 0 10,000 K
vmware-authd.exe 2496 Services 0 13,440 K
csrss.exe 3864 RDP-Tcp#6 2 12,840 K
winlogon.exe 3924 RDP-Tcp#6 2 8,400 K
dwm.exe 3988 RDP-Tcp#6 2 133,044 K
RuntimeBroker.exe 3612 RDP-Tcp#6 2 34,632 K
sihost.exe 3764 RDP-Tcp#6 2 22,676 K
explorer.exe 4024 RDP-Tcp#6 2 522,228 K
ChsIME.exe 1936 RDP-Tcp#6 2 9,064 K
ShellExperienceHost.exe 4308 RDP-Tcp#6 2 83,412 K
SearchUI.exe 4392 RDP-Tcp#6 2 47,184 K
ServerManager.exe 4700 RDP-Tcp#6 2 99,764 K
vmware-tray.exe 4936 RDP-Tcp#6 2 12,512 K
msdtc.exe 4792 Services 0 9,692 K
notepad.exe 1184 RDP-Tcp#6 2 14,124 K
dllhost.exe 3264 RDP-Tcp#6 2 9,140 K
mmc.exe 800 RDP-Tcp#6 2 17,524 K
taskhostw.exe 4352 RDP-Tcp#6 2 19,148 K
notepad.exe 724 RDP-Tcp#6 2 14,080 K
java.exe 3428 RDP-Tcp#6 2 372,520 K
java.exe 8044 RDP-Tcp#6 2 561,224 K
wordpad.exe 5724 RDP-Tcp#6 2 33,536 K
git-bash.exe 4932 RDP-Tcp#6 2 5,164 K
mintty.exe 5348 RDP-Tcp#6 2 19,216 K
bash.exe 9108 RDP-Tcp#6 2 9,644 K
git-bash.exe 5148 RDP-Tcp#6 2 5,104 K
mintty.exe 9084 RDP-Tcp#6 2 18,784 K
conhost.exe 8488 RDP-Tcp#6 2 11,724 K
bash.exe 4408 RDP-Tcp#6 2 9,588 K
git-bash.exe 756 RDP-Tcp#6 2 5,124 K
mintty.exe 2284 RDP-Tcp#6 2 18,220 K
notepad.exe 8272 RDP-Tcp#6 2 14,852 K
notepad.exe 3464 RDP-Tcp#6 2 14,436 K
conhost.exe 8756 RDP-Tcp#6 2 14,972 K
notepad.exe 9036 RDP-Tcp#6 2 15,964 K
mmc.exe 7244 RDP-Tcp#6 2 13,036 K
ApplicationFrameHost.exe 5996 RDP-Tcp#6 2 24,204 K
SystemSettings.exe 6804 RDP-Tcp#6 2 57,788 K
MpCmdRun.exe 5948 Services 0 8,160 K
tasklist.exe 4476 RDP-Tcp#6 2 8,092 K
从第2列找到进程号为4的,发现是System。
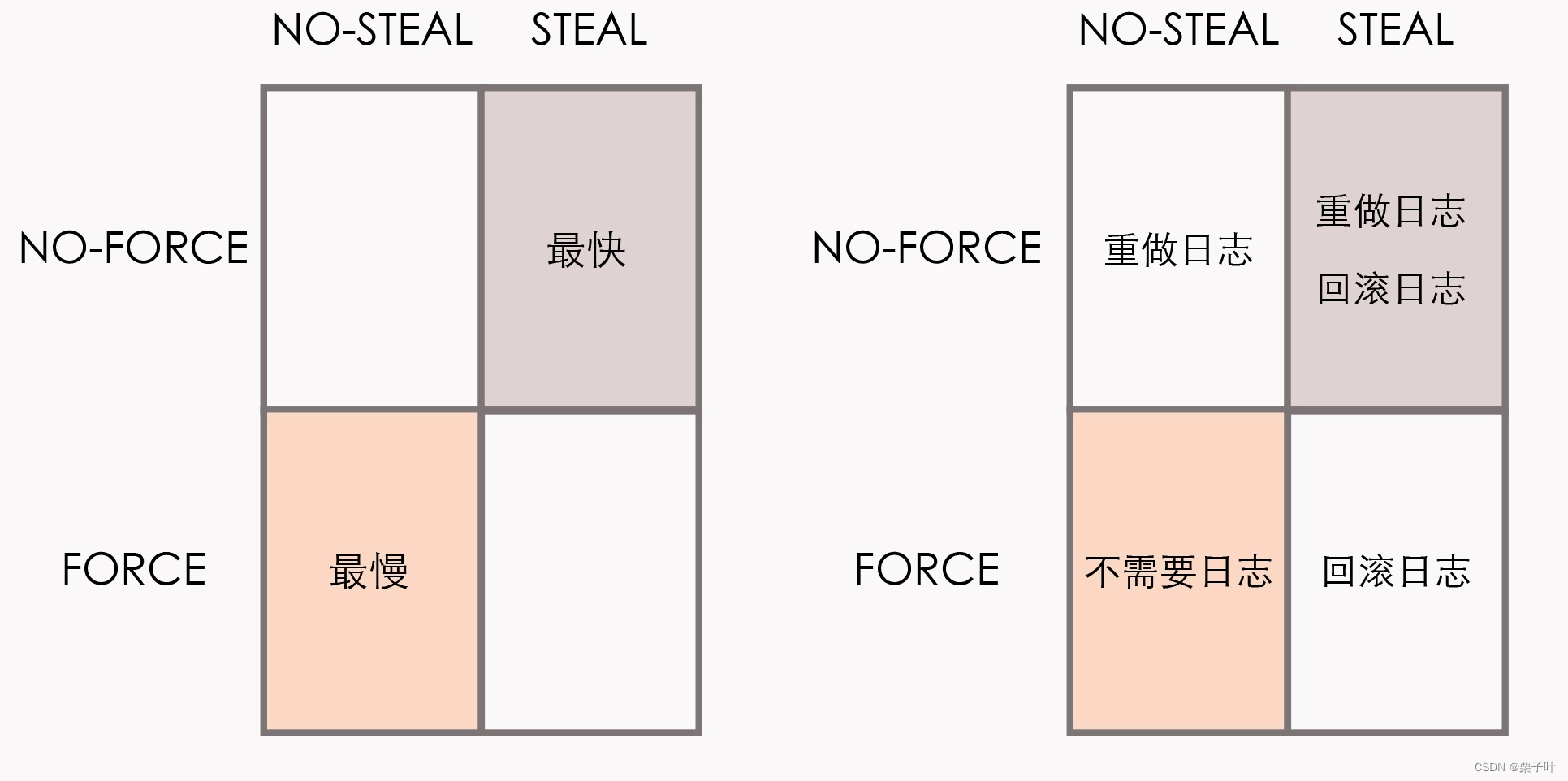
也可以在任务管理器查看进程对应的服务,发现pid=4的进程,其对应的进程描述是NT kernel & system。
三. 遇到了“80端口被System占用”,该如何解决呢?
这是什么进程?
系统的80端口是被W3SVC(万维网发布服务,World Wide Web Publishing Service)占用了,它是系统提供http服务的依赖项。哪些服务使用了这个端口呢?
- World Wide Web:发布服务
- SSDP Discovery:局域网共享所需服务
- Print Spooler:打印机交互服务
怎么处理呢?
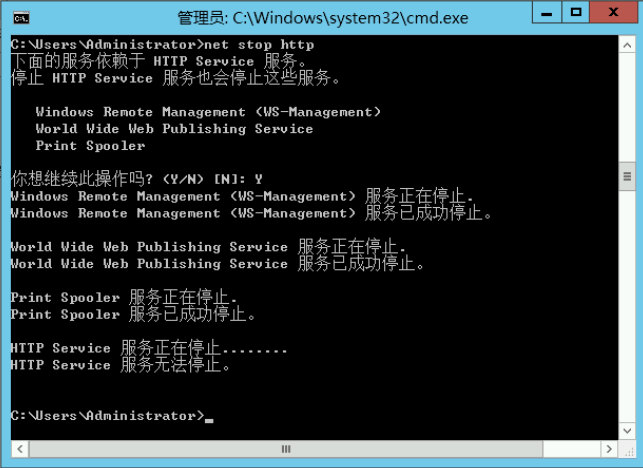
如果允许,可以直接不使用这个服务,这个进程显式停止是无法停止的,只有在cmd.exe里使用net stop http来停止。
(1) 关闭服务
C:\Users\Administrator>net stop http
下面的服务依赖于 HTTP Service 服务。
停止 HTTP Service 服务也会停止这些服务。World Wide Web 发布服务SSDP DiscoveryPrint Spooler
你想继续此操作吗? (Y/N) [N]: y
World Wide Web 发布服务 服务正在停止.
World Wide Web 发布服务 服务已成功停止。
SSDP Discovery 服务正在停止.
SSDP Discovery 服务已成功停止。
Print Spooler 服务正在停止.
Print Spooler 服务已成功停止。
HTTP Service 服务已成功停止。
或显示如下:
(2) 禁用服务
C:\Users\Administrator>sc config http start= disabled
[SC] ChangeServiceConfig 成功
此时查看可能发现80端口尚未释放,此时需重启服务器。
重启后,80单口端口就释放了。
参考文章:
Win10 | 查找占用特定端口的进程
遇到了“80端口被占用”的问题,该如何解决?
NT Kernel & System 占用80端口