8种机械键盘轴体对比
本人程序员,要买一个写代码的键盘,请问红轴和茶轴怎么选?
emmmmmm这次的Hackgame还是脑洞为主。。。我只做出来了6道题,这里结合官方wp总结一下,题目现在还是可以做的(https://hack2018.lug.ustc.edu.cn/)
签到题
打开页面后得到信息:

要求提交指定字符串。查看网页源码中表单名称:1
Key:
get上去:1http://202.38.95.46:12002/?key=hackergame2018
得到flag:flag{Hackergame2018_Have_Fun!}
猫咪问答
emmmmmm我不是中科大学生所以没做完这道。。不过也算是一个小社工吧,自己网上检索信息
flag:flag{G00G1E-is-always-YOUR-FRIEND}
游园会的集章卡片
这个题就不细说了。。。主要是给了一堆图片拼图,自行拼就行了
flag:flag{H4PPY_1M4GE_PR0CE551NG}
猫咪和键盘
打开后是一份乱的C++代码,需要还原。可以看出代码按列打乱了。
使用vim编辑器,列编辑模式还原后:1
2
3
4
5
6
7
8
9
10
11
12
13name: typed_printf.cpp
compile: g++ -std=c++17 typed_printf.cpp
title: type safe printf
author: nicekingwei
url: aHR0cHM6Ly96anUtbGFtYmRhLnRlY2gvY3BwZHQtcHJpbnRmLw==
related knowledge:
- value and type
value->value: function
type->value: parametric polymorphism
type->type: generic
value->type: dependent type
- auto
- if constexpr
编译运行后得到flag(待实验…)
Word文档
还真不知道docx文档结构是这样的
拖进winhex里:
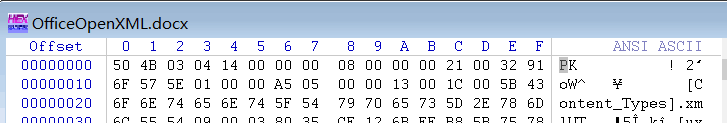
可以看出为zip文件,该后缀打开后里面就有flag文本文件了
flag:flag{xlsx,pptx,docx_are_just_zip_files}
猫咪银行
这道题开始以为要在js脚本上做文章,后来发现好像没用。。。然后买1/4的flag也没啥用。
后来存钱时,随便输了个很大的数字,发现结果不对劲,才反应过来是溢出问题。
输入一个大数,且收入不为负,时间在现在时间点前面就行(可以直接取出),多试几个数就可以了。

flag:flag{Evil_Integer._Evil_Overflow.}
黑曜石浏览器
这道题费了我好几天都没搞出来。。
抓包后是这样的:1
2
3
4
5
6
7
8
9
10GET / HTTP/1.1
Host: 202.38.95.46:12001
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:56.0) Gecko/20100101 Firefox/56.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=2e76eef44e3dd8842a479aa79f7f6396
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
返回提示说要使用最新的黑曜石浏览器(HEICORE),即我们需要知道最新的HEICORE浏览器的版本号,遂百度了一下,没东西。。试了各种手段没结果,于是懵逼了几天
肿么办呢?just google!google HEICORE会看到有一个HEICORE的官网(明显是中科大搭的。。。。)进去后什么都点不了。。下面有个v0.0.2以为是最新版本号,试了也没用。

后来查看了http://heicore.com的代码(不是index.php那个页面!),可以看到下载文件的名称,里面附带的有版本号49.1.2623.213,这才有结果了。。1
2
3
4
5
6
7$("#download_link").click(function(){
if (!window.loggedIn) {
alert("仅差一步!请于登录后下载黑曜石浏览器。");
}
else {
window.location.href="HEICORE.49.1.2623.213_installer_latest.exe";
}
bp改User-Agent后:1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:56.0) Gecko/20100101 HEICORE/49.1.2623.213
返回结果:
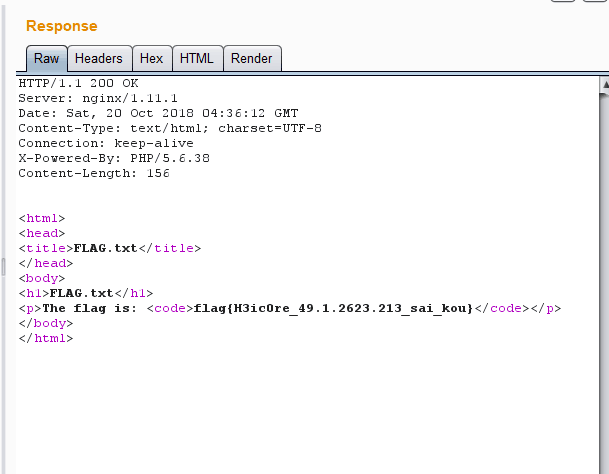
ps:官槽:除了百度以外的所有搜索引擎几乎都能找到该浏览器的官网:heicore.com
emmmmmmmmmmmmmmmmmmmmmmmmmm以后还是google吧
得到flag:flag{H3ic0re_49.1.2623.213_sai_kou}
回到过去
这道题只要熟悉unix/linux下的ed编辑器命令就好了。
题目也给出来了具体步骤,虚拟机里敲一遍即可。
flag:flag{t4a2b8c44039f93345a3d9b2}
我是谁
第一问:burp刷新了几次截包后,会在返回头里看到teapot,即关键字,得到flag:flag{i_canN0t_BReW_c0ffEE!}
打开链接来到第二问,提示需要换一种请求方式:
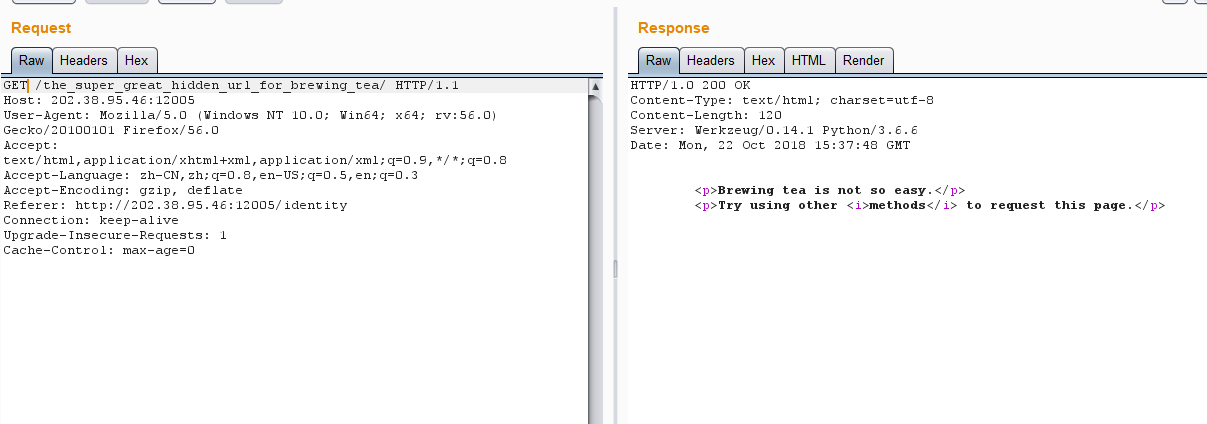
我们在burp换为POST形式:
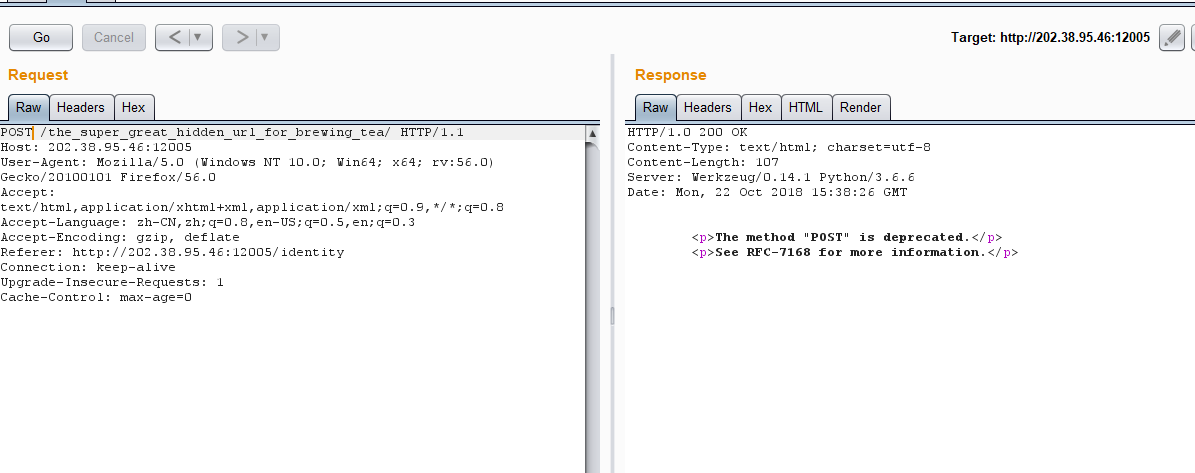
提示POST也不行,emmmmmmmmmm????当时做到这里就不会了,后面提到的BREW请求也没见过,所以没出来。。。
查看提示的文档
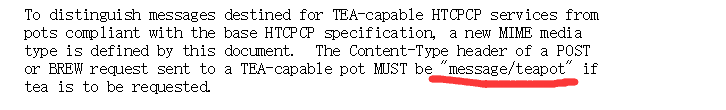
得知还有BREW这种请求。。。
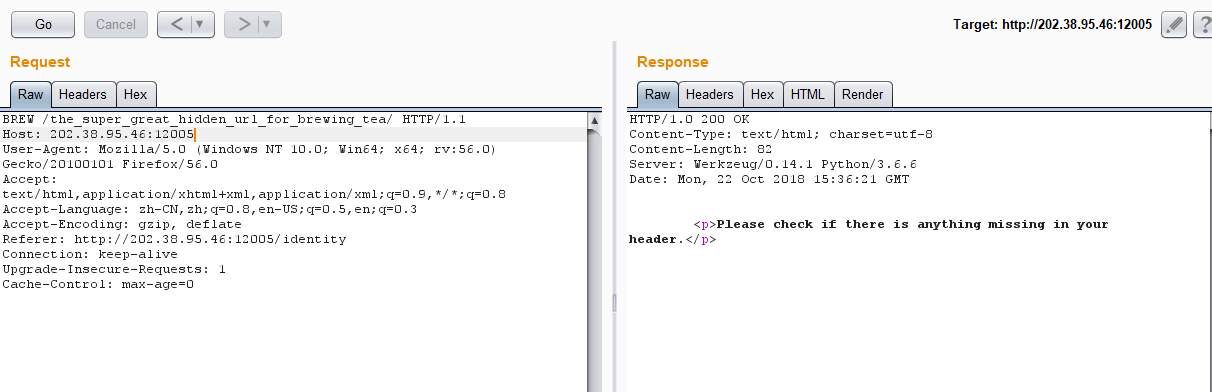
还要带上一个参数Content-Type: message/teapot',返回结果:

从返回头中看到下一个链接,同样的方式访问:

得到flag:flag{delivering_tea_to_DaLa0}`
家里有矿
秘籍残篇
猫咪遥控器
下载下来一个文本,内容全部为D、R、L、U的组合,可以联想到up,down,left,right四个方向。即这是是一个图片,可由这个步骤画出。
这里使用HTML中的canvas标签,该标签相当于一个图形容器,可以根据js脚本来绘制相应的图形。(当然pyhton的Turtle也是可以画出来的)下面是脚本:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
Cat Controller#path {
border: 1px solid #000000;
}
var seq = "DDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRDDDDDDDDDDDDDDDDDDDDLLLLLLLLLLLLLLLLLLDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDUUUUUUUUUUUUUUUUUUUUUUUUUULLLLLLLLLLLLRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRLLLLLLLLLLLLLLLLLLLLLLLLRRRRDDDDDDDDRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRUUUUUUUUUUUUUUUUUUUUDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDUUUUUUUUUUUUUUUUUUUURRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRUUUUUUUULLLLLLLLLLLLLLLLRRRRRRRRRRRRRRRRRRRRLLLLDDDDDDDDDDDDDDDDDDDDDDDDDDDDLLLLLLLLLLLLLLLLLLLLUUUUUUUUUUUUUUUURRRRRRRRRRRRRRRRRRRRUUUUUUUUUUUULLLLLLLLLLLLLLLLLLLLRRRRRRRRRRRRRRRRRRRRRRRRLLLLDDDDDDDDRRRRRRRRRRRRRRRRDDDDDDDDDDDDDDDDDDDDRRRRRRRRRRRRRRRRRRRRUUUUUUUUUUUUUUUUUUUUUUUUUUUULLLLLLLLLLLLLLLLLLLLDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDUUUURRRRRRRRRRRRRRRRRRRRRRRRLLLLDDDDDDDDDDDDLLLLLLLLLLLLLLLLLLLLLLLLRRRRRRRRRRRRRRRRRRRRRRRRRRRRLLLLUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUDDDDDDDDRRRRRRRRRRRRRRRRRRRRRRRRRRRRUUUUUUUUUUUUUUUUUUUURRRRRRRRLLLLLLLLDDDDDDDDDDDDDDDDDDDDDDDDLLLLLLLLDDDDRRRRRRRRDDDDDDDDDDDDDDDDDDDDDDDDRRRRRRRRLLLLLLLLUUUUUUUUUUUUUUUUUUUUUUUULLLLLLLLUUUURRRRRRRRUUUURRRRRRRRRRRRRRRRRRRRRRRRDDDDDDDDDDDDDDDDDDDDUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUURRRRDDDDRRRRDDDDRRRRDDDDDDDDDDDDDDDDUUUUUUUUUUUUUUUURRRRRRRRUUUUUUUURRRRDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDUUUUUUUUUUUUUUUUUUUURRRRRRRRRRRRUUUURRRRUUUURRRRRRRRRRRRRRRRDDDDRRRRDDDDRRRRDDDDDDDDLLLLLLLLLLLLLLLLLLLLLLLLLLLLLLLLUUUURRRRUUUUDDDDLLLLDDDDDDDDRRRRDDDDRRRRDDDDRRRRRRRRRRRRUUUURRRRRRRRUUUUDDDDLLLLLLLLDDDDLLLLLLLLLLLLUUUULLLLUUUULLLLUUUUUUUURRRRUUUURRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRDDDDDDDDDDDDDDDDDRRRRRRRRRRRRRRRRRRRRRRRRRRRRUUUUUUUUUUUUUUUUUUUUUUUULLLLLLLLLLLLLLLLLLLLLLLLLLLLDDDDDDDDDDDDDDDDDDDDDDDDRRRRRRRRRRRRRRRRRRRRRRRRRRRRUUUUUUUUUUUUUUUURRRRRRRRUUUULLLLUUUUDDDDRRRRDDDDRRRRDDDDDDDDDDDDDDDDDDDDRRRRUUUUUUUUUUUURRRRUUUUUUUUDDDDDDDDRRRRDDDDDDDDDDDDRRRRUUUUUUUUUUUUUUUUUUUURRRRUUUURRRRUUUUDDDDLLLLDDDDRRRRRRRRRRRRUUUUUUUUUUUUUUUUDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUURRRRDDDDRRRRDDDDRRRRDDDDDDDDDDDDDDDDUUUUUUUUUUUUUUUURRRRUUUURRRRUUUURRRRDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDUUUUUUUUUUUUUUUUUUUUDDDDUUUURRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRRLLLLLLLLLLLLLLLLUUUULLLLUUUULLLLLLLLDDDDLLLLDDDDLLLLDDDDDDDDDDDDRRRRDDDDRRRRDDDDRRRRRRRRUUUURRRRRRRRUUUUDDDDLLLLLLLLDDDDLLLLLLLLUUUULLLLUUUULLLLUUUUUUUURRRRRRRRRRRRRRRRRRRRRRRRUUUULLLLUUUUDDDDRRRRRRRRRRRRRRRRRRRRDDDDDDDDDDDDDDDDRRRRRRRRRRRRRRRRRRRRUUUUUUUUUUUUUUUUUUUULLLLLLLLLLLLLLLLLLLLDDDDDDDDUUUUUUUURRRRRRRRRRRRRRRRRRRRDDDDRRRRRRRRRRRRUUUULLLLUUUUDDDDRRRRDDDDRRRRDDDDDDDDDDDDDDDDDDDDRRRRUUUUUUUUUUUUUUUURRRRUUUUUUUUDDDDDDDDRRRRDDDDDDDDDDDDDDDDRRRRRRRRUUUUUUUUUUUUUUUURRRRUUUUUUUURRRRUUUUDDDDLLLLDDDDRRRRRRRRRRRRRRRRRRRRUUUUUUUUUUUUUUUULLLLLLLLRRRRRRRRDDDDDDDDDDDDDDDDDDDDRRRRRRRRDDDDLLLLLLLLDDDDDDDDDDDDDDDDDDDDLLLLLLLL";
var ctx = document.getElementById('path').getContext('2d');
var x = 0, y = 0;
function (type){
switch (type) {
case 'U': y -= 1; break;
case 'D': y += 1; break;
case 'L': x -= 1; break;
case 'R': x += 1; break;
}
ctx.fillRect(x, y, 1, 1);
}
for (var i = 0; i < seq.length; i++) {
move(seq[i]);
}
//
打开即可得到flag:flag{MeowMeow}
她的诗
下载附件,为一个文本和一个py文件。1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16#!/usr/bin/env python3
# This script helps you decode "her poem"
from codecs import decode
fin = open("poem.txt", "r")
fout = open("poem.out", "w")
for i in fin:
data = "begin 666 n" + i + " nendn"
decode_data = decode(data.encode("ascii"), "uu")
print(decode_data)
fout.write(decode_data.decode("ascii") + "n")
fin.close()
fout.close()
跑后将poem文本文件解析为了明文,但是文件中没有flag,说明有猫腻。。。
注意到py脚本中有一行begin 666,百度后:
得知加密方式为uuencode,在线解密后得结果:1---------There is something in this worldfthat no one has ever seen before.It is gentle and sweet.lMaybe if it could be seen,aeveryone would fight over it.gThat is why the world hid it,{so that no one could get their handson it so easily.STHowever, someday, someone will find it.The person who deserves it the mostewill definitely find it.---------Do you like this school?I really, really love it.gABut nothing can stay unchanged.n0Fun things... Happy things...gThey can't all possibly stay unchanged.Even so,rcan you go on loving this place?A---------Sometimes I wonder,Phwhat if this town was alive?y_What if it had thoughts and feelingslike one of us?If it did,w1I think it would want to make the peopletHwho live here happy._---------Expectations are what you havewhen you have given up.uExpectations are born fromUa despairingly large difference in skill.e---------A joke only lasts for a moment,Ncif it leaves a misunderstanding,0it becomes a lie.D---------If someone didn't have any pride,wouldn't they also be lackingEin self-confidence?_IIf someone was free of greed,5wouldn't they have trouble_supporting their family?And if people didn't envy one another,5wouldn't they stop inventing new things?0_---------If I don't have to do it, I won't.fuIf I have to do it, I'll make it.---------/* Here is the end of my poem.
可以看出与脚本解出来的是有区别的,部分单词多出了几个字母,组合(最后补上显而易见的字符。。。)即可得到flag:flag{sSTegAn0grAPhy_w1tH_uUeNc0DE_I5_50_fun}
猫咪克星
这道题属于一道基础题,即使用py脚本进行简单的网络编程。
题目提示:nc 202.38.95.47 12009
先cmd试验一下:

要求:快速运算一个算术式并在30s内返回结果
打开IDE直接输入式子,并将结果写进cmd发送,你会发现你源源不断的得到新的式子,这样的话手工运算30s内是肯定算不完的。
![]()
这是我们想到了python的eval函数—-执行一个算数表达式。
下面是eval函数的解释:1
2
3
4
5
6
7
8
9
10Help on built-in function eval in module builtins:
eval(source, globals=None, locals=None, /)
Evaluate the given source in the context of globals and locals.
The source may be a string representing a Python expression
or a code object as returned by compile().
The globals must be a dictionary and locals can be any mapping,
defaulting to the current globals and locals.
If only globals is given, locals defaults to it.
如下脚本:1
2