1.MISC01
文件打开一堆01,差分曼彻斯特
python">from libnum import *
f = open("data","r",encoding="utf-8")
all_str = f.read()
f.close()
out = ""
n = (len(all_str) // 2) - 1
for i in range(0, n):tmp1 = all_str[i*2:i*2+2]tmp2 = all_str[i*2+2:i*2+4]if tmp1 == tmp2:out = out + '0'else:out = out + '1'
out = str(hex(int(out,2))[2::])
f = open("tmp.txt","w")
f.write(out)
f.close()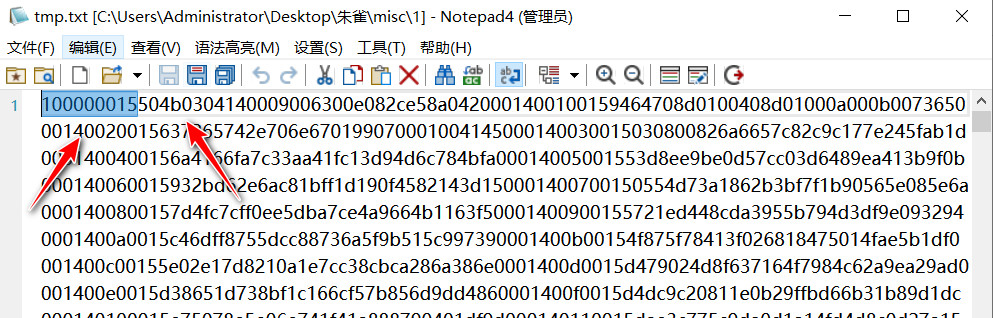
去除头部100000015后,转zip
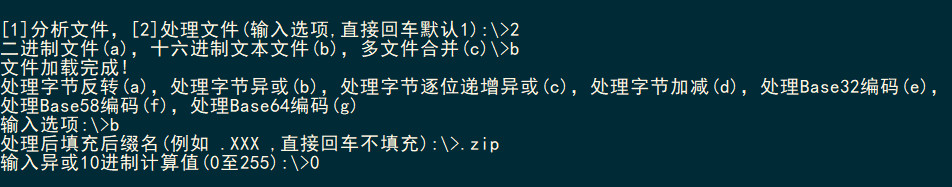
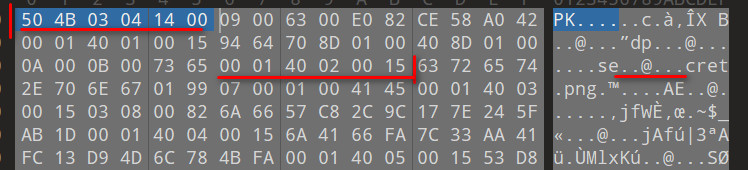
发现zip文件中夹杂多余字节,secret.png被分开,间隔为6个字节,估计是多余了6个字节。至于每取出多少字节后去除尾部6个字节,可以爆破。
因为头部504B03041400没有问题,从504B0304到42020015,长度44,可以从12爆破至44。
python">f = open("tmp.zip","rb")
all_b = f.read()
f.close()
n = len(all_b)for j in range(12,45):out = b""for i in range(0,n,j):out = out + all_b[i:i+(j-6)]f = open(f"out_{j}.zip","wb")f.write(out)f.close()多次尝试发现每22个字节去除6个多余字节,可以恢复正常文件
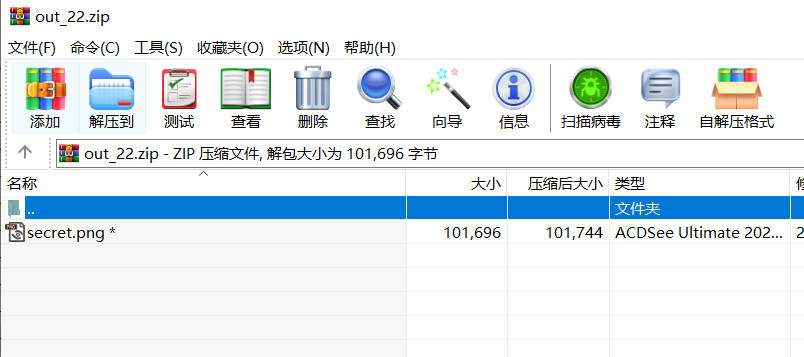
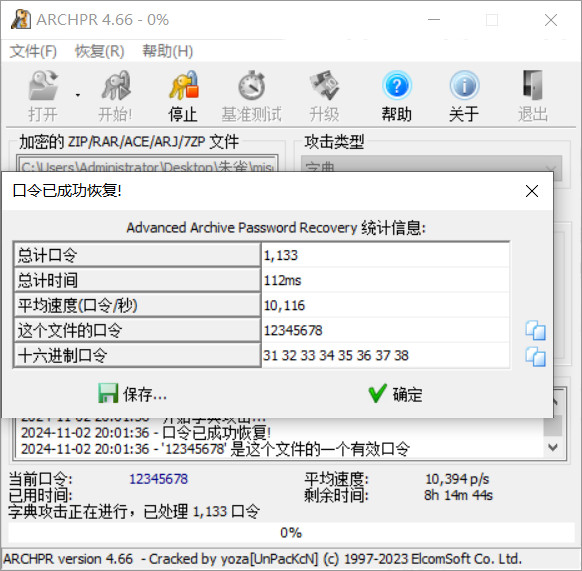
解压缩密码:12345678,解压缩得到图片
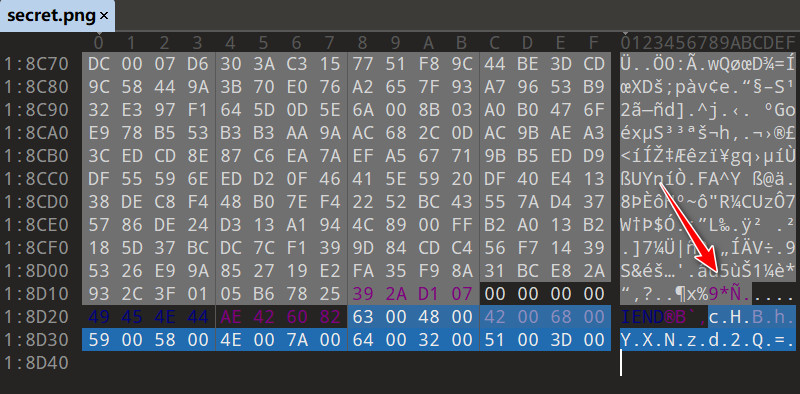
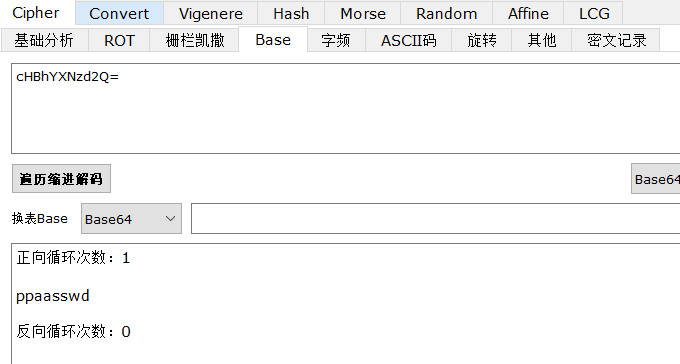
base64解码:ppaasswd
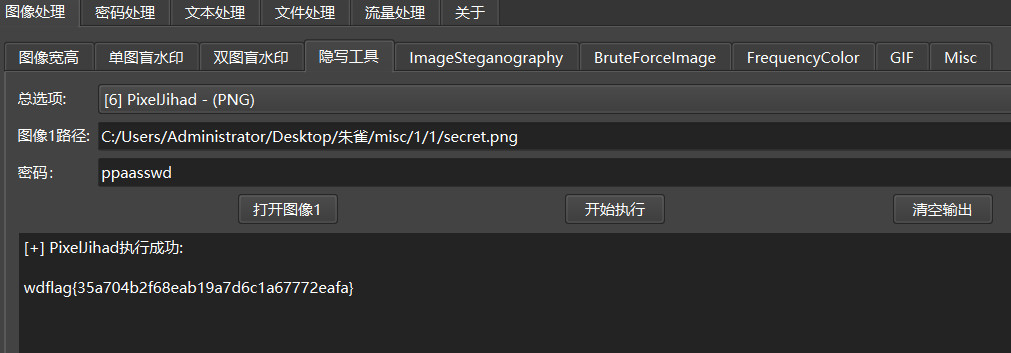
wdflag{35a704b2f68eab19a7d6c1a67772eafa}
2.MISC02
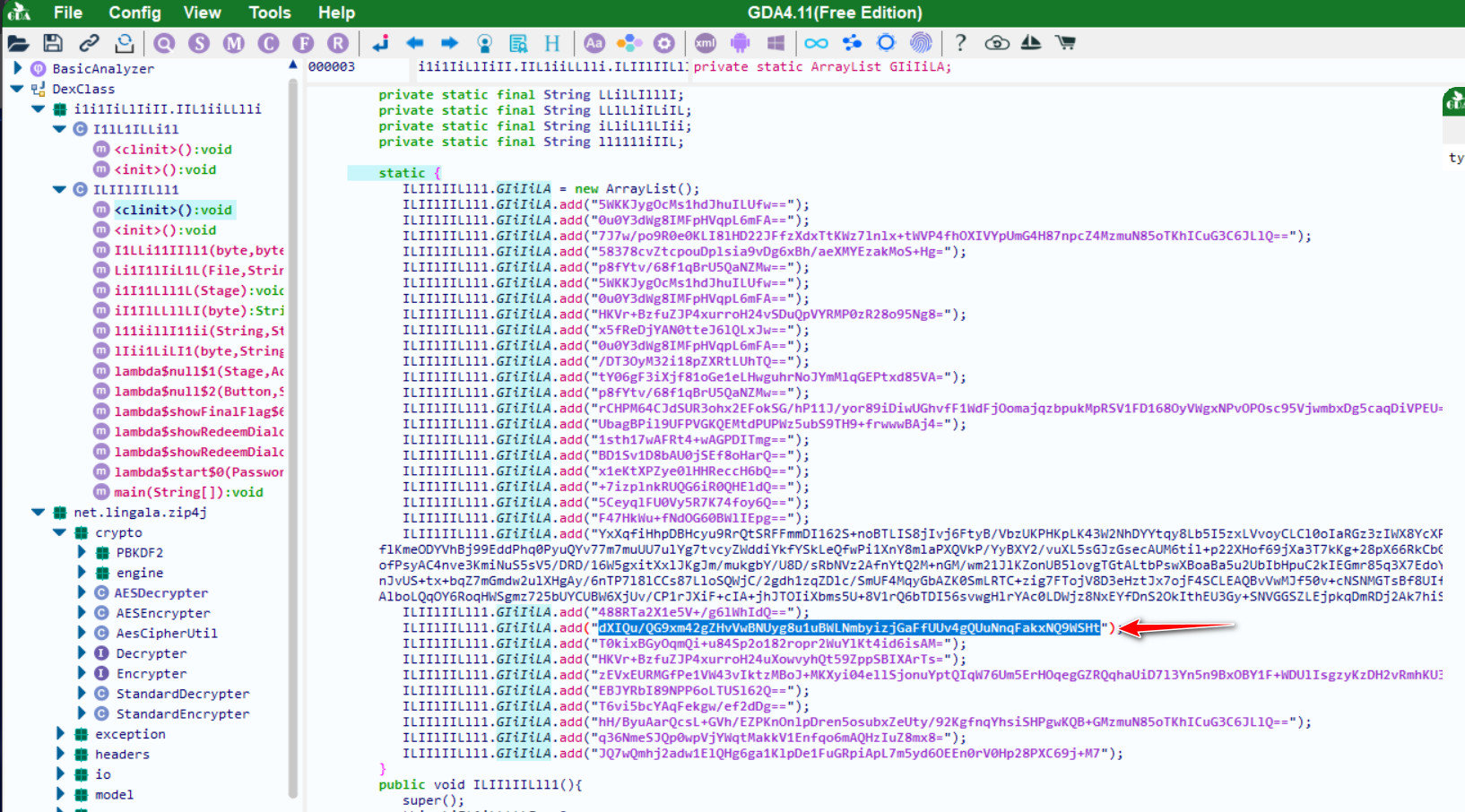
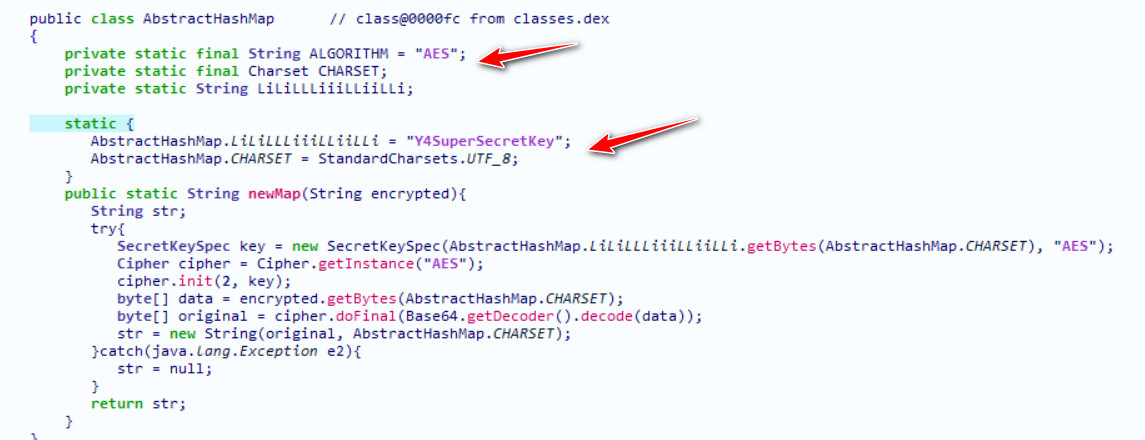
直接逆向读取信息,发现一堆Base64编码的信息和AES的key,逐个尝试
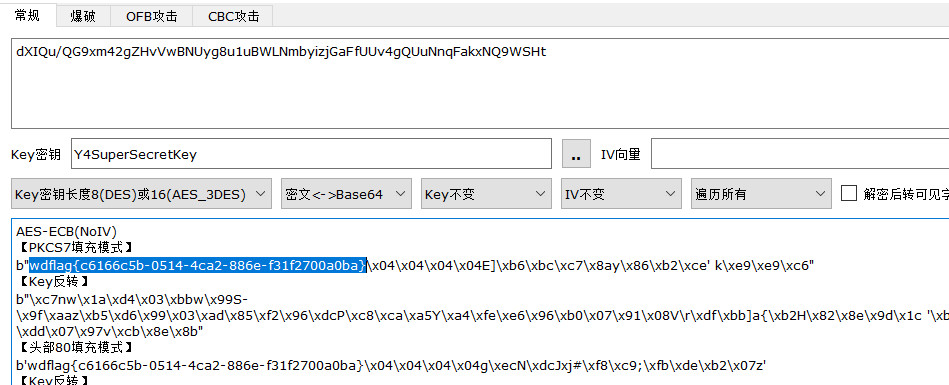
wdflag{c6166c5b-0514-4ca2-886e-f31f2700a0ba}
2.MISC03
尾部zip文件特征,提取
发现前后文件名不一致,修复
还有一个压缩文件,继续分离出来
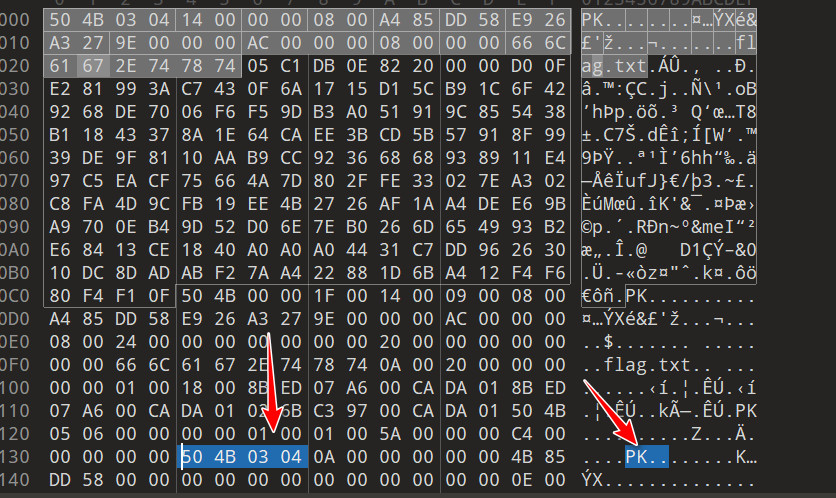
分离出两个文件,其中一个文件可以CRC爆破
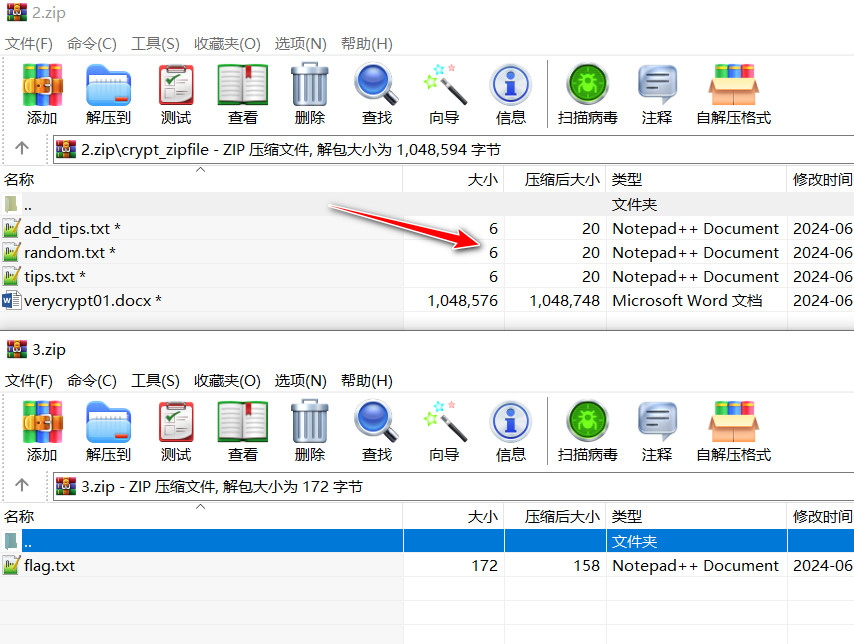
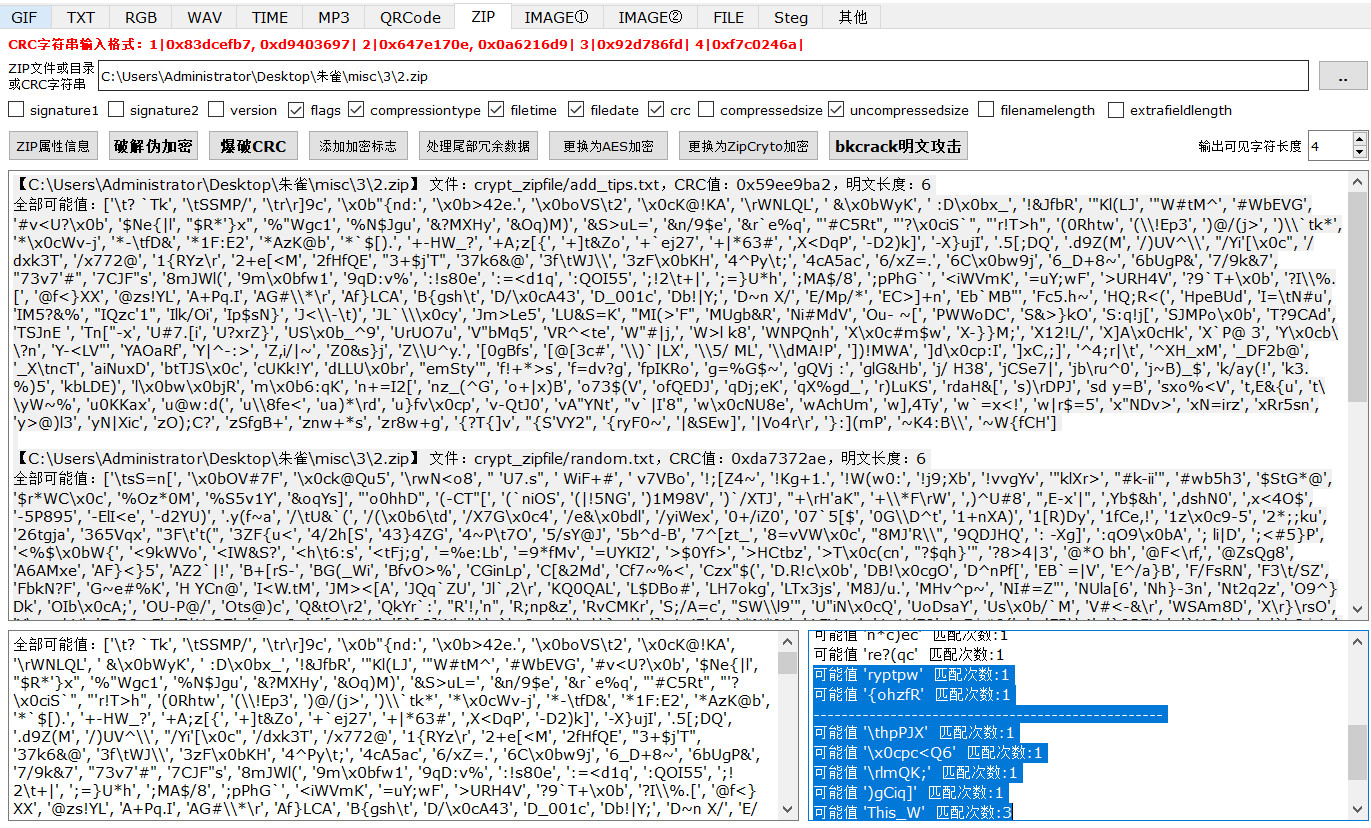
得到This_W和 ryptpw
第一组脚本筛选出字符
python">a= ['\t? `Tk', '\tSSMP/', '\tr\r]9c', '\x0b"{nd:', '\x0b>42e.', '\x0boVS\t2', '\x0cK@!KA', '\rWNLQL', ' &\x0bWyK', ' :D\x0bx_', '!&JfbR', '"Kl(LJ', '"W#tM^', '#WbEVG', '#v<U?\x0b', '$Ne{|l', "$R*'}x", '%"Wgc1', '%N$Jgu', '&?MXHy', '&Oq)M)', '&S>uL=', '&n/9$e', '&r`e%q', "'#C5Rt", "'?\x0ciS`", "'r!T>h", '(0Rhtw', '(\\!Ep3', ')@/(j>', ')\\`tk*', '*\x0cWv-j', '*-\tfD&', '*1F:E2', '*AzK@b', '*`$[).', '+-HW_?', '+A;z[{', '+]t&Zo', '+`ej27', '+|*63#', ',X<DqP', '-D2)k]', '-X}ujI', '.5[;DQ', '.d9Z(M', '/)UV^\\', "/Yi'[\x0c", '/dxk3T', '/x772@', '1{RYz\r', '2+e[<M', '2fHfQE', "3+$j'T", '37k6&@', '3f\tWJ\\', '3zF\x0bKH', '4^Py\t;', '4cA5ac', '6/xZ=.', '6C\x0bw9j', '6_D+8~', '6bUgP&', '7/9k&7', "73v7'#", '7CJF"s', '8mJWl(', '9m\x0bfw1', '9qD:v%', ':!s80e', ':=<d1q', ':QOI55', ';!2\t+|', ';=}U*h', ';MA$/8', ';pPhG`', '<iWVmK', '=uY;wF', '>URH4V', '?9`T+\x0b', '?I\\%.[', '@f<}XX', '@zs!YL', 'A+Pq.I', 'AG#\\*\r', 'Af}LCA', 'B{gsh\t', 'D/\x0cA43', 'D_001c', 'Db!|Y;', 'D~n X/', 'E/Mp/*', 'EC>]+n', 'Eb`MB"', 'Fc5.h~', 'HQ;R<(', 'HpeBUd', 'I=\tN#u', 'IM5?&%', "IQzc'1", 'Ilk/Oi', 'Ip$sN}', 'J<\\-\t)', 'JL`\\\x0cy', 'Jm>Le5', 'LU&S=K', "MI(>'F", 'MUgb&R', 'Ni#MdV', 'Ou- ~[', 'PWWoDC', 'S&>}kO', 'S:q!j[', 'SJMPo\x0b', 'T?9CAd', 'TSJnE ', 'Tn["-x', 'U#7.[i', 'U?xrZ}', 'US\x0b_^9', 'UrUO7u', 'V"bMq5', 'VR^<te', 'W"#|j,', 'W>l k8', 'WNPQnh', 'X\x0c#m$w', 'X-}}M;', 'X12!L/', 'X]A\x0cHk', 'X`P@ 3', 'Y\x0cb\\?n', 'Y-<LV"', 'YAOaRf', 'Y|^-:>', 'Z,i/|~', 'Z0&s}j', 'Z\\U^y.', '[0gBfs', '[@[3c#', '\\)`|LX', '\\5/ ML', '\\dMA!P', '])!MWA', ']d\x0cp:I', ']xC,;]', '^4;r|\t', '^XH_xM', '_DF2b@', '_X\tncT', 'aiNuxD', 'btTJS\x0c', 'cUKk!Y', 'dLLU\x0br', "emSty'", 'f!+*>s', 'f=dv?g', 'fpIKRo', 'g=%G$~', 'gQVj :', 'glG&Hb', 'j/ H38', 'jCSe7|', 'jb\ru^0', 'j~B)_$', 'k/ay(!', 'k3.%)5', 'kbLDE)', 'l\x0bw\x0bjR', 'm\x0b6:qK', 'n+=I2[', 'nz_(^G', 'o+|x)B', 'o73$(V', 'ofQEDJ', 'qDj;eK', 'qX%gd_', 'r)LuKS', 'rdaH&[', 's)\rDPJ', 'sd y=B', 'sxo%<V', 't,E&{u', 't\\yW~%', 'u0KKax', 'u@w:d(', 'u\\8fe<', 'ua)*\rd', 'u}fv\x0cp', 'v-QtJ0', 'vA"YNt', "v`|I'8", 'w\x0cNU8e', 'wAchUm', 'w],4Ty', 'w`=x<!', 'w|r$=5', 'x"NDv>', 'xN=irz', 'xRr5sn', 'y>@)l3', 'yN|Xic', 'zO);C?', 'zSfgB+', 'znw+*s', 'zr8w+g', '{?T{]v', "{S'VY2", '{ryF0~', '|&SEw]', '|Vo4r\r', '}:](mP', '~K4:B\\', '~W{fCH']dic = "1234567890abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ_"
for i in a:pos = Truefor j in i:if j not in dic:pos = Falsebreakif pos == True:print(i)筛选出字符This_WD_001cryptpw,就是解压缩密码,解压缩出verycrypt01.docx
根据题意挂载,密码就是解压缩密码
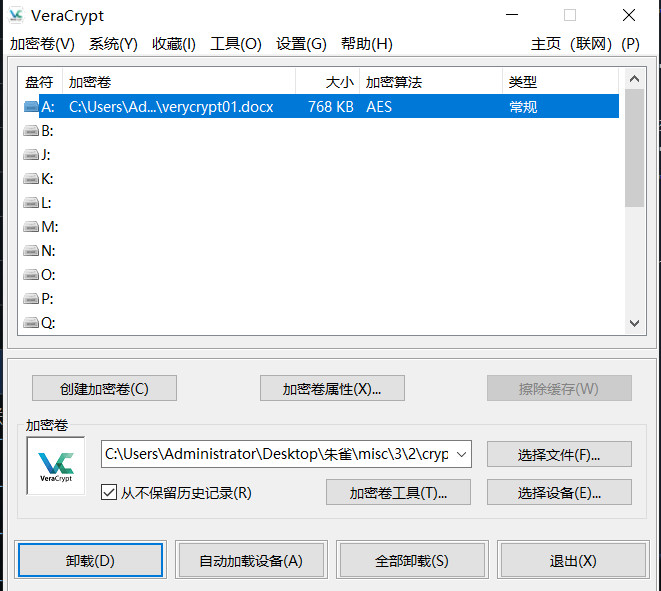
得到RSA私钥,用来解密flag.txt
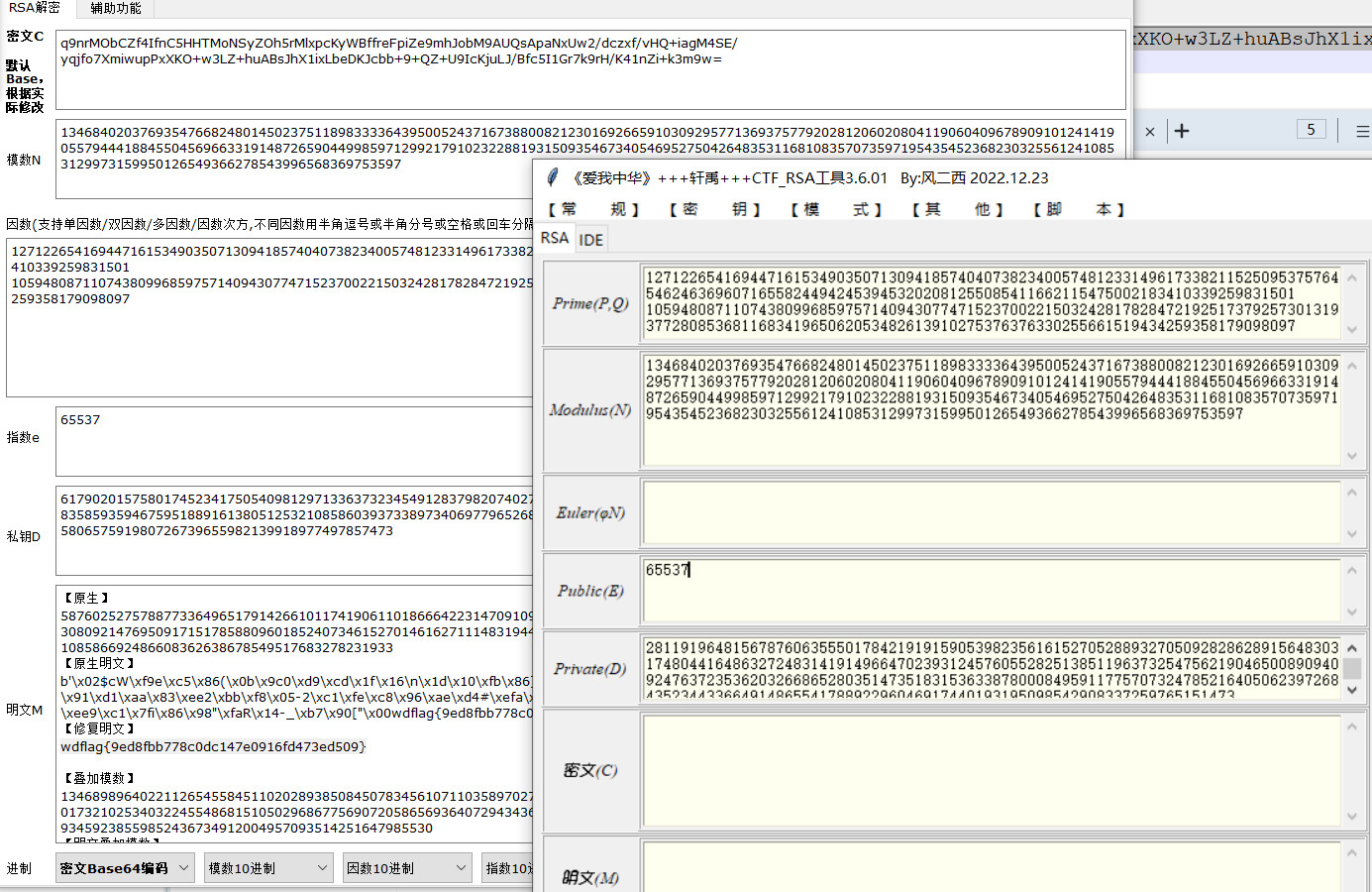
wdflag{9ed8fbb778c0dc147e0916fd473ed509}



![如何使用Google Search Console进行关键词研究[4 种简便方法]](https://img-blog.csdnimg.cn/img_convert/eef7fee1082f94ee5b1cb805810289e5.png)

